DocuSign, a major provider of electronic signature technology, acknowledged today that a series of recent malware phishing attacks targeting its customers and users was the result of a data breach at one of its computer systems. The company stresses that the data stolen was limited to customer and user email addresses, but the incident is especially dangerous because it allows attackers to target users who may already be expecting to click on links in emails from DocuSign.
San Francisco-based DocuSign warned on May 9 that it was tracking a malicious email campaign where the subject line reads, “Completed: docusign.com – Wire Transfer Instructions for recipient-name Document Ready for Signature.” The missives contained a link to a downloadable Microsoft Word document that harbored malware.
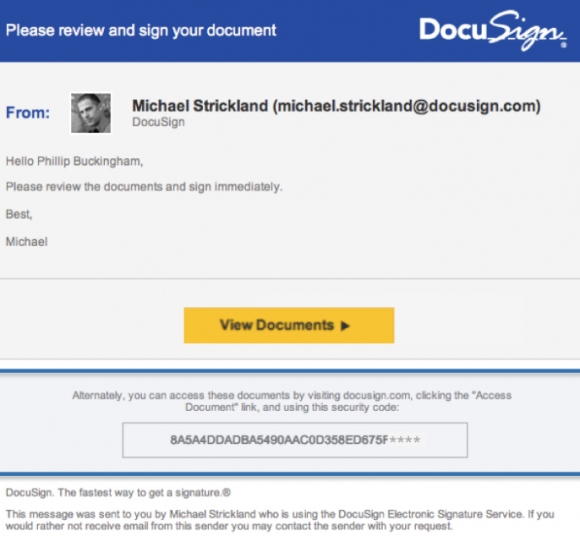
A typical DocuSign email. Image: DocuSign.
The company said at the time that the messages were not associated with DocuSign, and that they were sent from a malicious third-party using DocuSign branding in the headers and body of the email. But in an update late Monday, DocuSign confirmed that this malicious third party was able to send the messages to customers and users because it had broken in and stolen DocuSign’s list of customers and users.
“As part of our ongoing investigation, today we confirmed that a malicious third party had gained temporary access to a separate, non-core system that allows us to communicate service-related announcements to users via email,” DocuSign wrote in an alert posted to its site. “A complete forensic analysis has confirmed that only email addresses were accessed; no names, physical addresses, passwords, social security numbers, credit card data or other information was accessed. No content or any customer documents sent through DocuSign’s eSignature system was accessed; and DocuSign’s core eSignature service, envelopes and customer documents and data remain secure.”
The company is asking people to forward any suspicious emails related to DocuSign to spam@docusign.com, and then to delete the missives.
“They may appear suspicious because you don’t recognize the sender, weren’t expecting a document to sign, contain misspellings (like “docusgn.com” without an ‘i’ or @docus.com), contain an attachment, or direct you to a link that starts with anything other than https://www.docusign.com or https://www.docusign.net,” reads the advisory.
If you have reason to expect a DocuSign document via email, don’t respond to an email that looks like it’s from DocuSign by clicking a link in the message. When in doubt, access your documents directly by visiting docusign.com, and entering the unique security code included at the bottom of every legitimate DocuSign email. DocuSign says it will never ask recipients to open a PDF, Office document or ZIP file in an email.
DocuSign was already a perennial target for phishers and malware writers, but this incident is likely to intensify attacks against its users and customers. DocuSign says it has more than 100 million users, and it seems all but certain that the criminals who stole the company’s customer email list are going to be putting it to nefarious use for some time to come.




I have used DocuSign a few times to make long-distance real estate offers (that were rejected) and was dismayed at how little was required to use a site that might have committed me to pay hundreds of thousands of dollars.
It’s true that what you do with the site can have big consequences, but all it really allows you to do is sign a document; it serves the same function as a pen. I don’t think there’s any reason for requiring more from users of the site to sign things.
I received few mails, as per above information I tried to send same to spam@docusign.com. But this mail id id rejecting mails.
Please send this to me : loic dot houssier at docusign dot com
Thanks for your help
Loic
From what i heard from users, DocuSign do attach files to their emails.
Makes this statement kind of useless thou i know it is from a DocuSign statement from here https://trust.docusign.com/static/downloads/Combating_Phishing_WP_05082017.pdf
DocuSign says it will never ask recipients to open a PDF, Office document or ZIP file in an email.
DocuSign doesn’t require you to open any attachments. When signing a document, their emails provide a secure link to the encrypted .pdf that is housed in their cloud. When the document has been completed by all signers, the option to have a .pdf copy of the completed document(s) delivered via email is available. This is what the hack exploited. The emails were made to appear like the recipient had received a wire transfer, and the completed documentation was attached to the email for their review.
Yes! after the documents are signed the recipients received a copy to download.
This is a serious breach. I helped someone defend against the phishing attack described in the article.
It’s hard to train users to look at URLs for phishiness. The one I saw had a top-level domain of an African country.
This is especially bad when punycode URL can looks virtually identical to a “normal” URL. Some browsers will display this:
https://www.xn--80ak6aa92e.com/
as this:
https://www.apple.com/
See here for how it works:
https://www.xudongz.com/blog/2017/idn-phishing/
Any security system that relies on humans to do the right thing will fail.
Time to get rid of the use of email for good.
And do what instead? Go back to chisels and stone tablets, or snail mail and FedEx?
rofl… agreed.
End to end encrypted messaging systems.
Won’t happen. In the final analysis, most people want security nut they want convenience and features more. From there the it-can’t-happen-to-me delusion kicks in.
Some months ago, my employer wanted us to acknowledge receipt and reading of the employee handbook by using DocuSign.
After the initial shock from reading the documentation on their website, I did a little research and found that other people (some of them lawyers) also had concerns about DocuSign’s ‘digital signatures’.
I checked what the Canadian government considered to be acceptable digital signatures (hint: they’re bang on!). I referred the HR dept. (located in the ‘States) to the relevant Canadian government documentation, pointing out that what Docusign does has no legal standing in Canada. I refused to Docusign. They didn’t push it.
And, oh look!, I’m protected from this phishing attack.
This is not true. Digital signature are legal in Canada
I didn’t say digital signatures aren’t legal in Canada, I said “what Docusign does has no legal standing in Canada” .. because the signing key isn’t generated by the signor and under the full control of the signor, the document’s hash isn’t generated by the signor, and the hash isn’t signed/encrypted by the signor’s key, that is: the whole process isn’t under the full control of the signor.
http://laws.justice.gc.ca/eng/regulations/SOR-2005-30/page-1.html#h-2
I was very pleasantly surprised that the MPs in Ottawa got it right.
What are the concerns about Docusign’s digital signatures?
I just got a document to sign yesterday (had no experience with Docusign) and I didn’t have to set up a digital signature using PKI. So basically anybody with access to my e-mail could have signed. Is that what the concern is?
He didn’t say DocuSign isn’t a digital signature, simply that it doesn’t hold under the Canadian Federal legal system. Considering it’s prevalence in real estate in the US I doubt the same is true here (signed all docs related to my home purchase ~30 months ago via DocuSign).
Yeah, that’s pretty much it. In the ‘States, they do have legal standing.
There’s a discussion here (which includes some US lawyers):
https://security.stackexchange.com/questions/116896/are-documents-truly-signed-by-docusign
The delayed trickle of acknowledgements is enough to make me not want to trust this company.
There is already a proper way to digitally “sign” something: with a GPG key. When someone imitates a proven technology to dumb it down, that’s strike two.
Not securing your customers’ information, even on an marketing server? Strike three, thanks for playing.
PGP (i.e. Pretty Good Privacy)?
Well, that’s an option, too.
The open-source implementation is Gnu Privacy Guard, GPG. They have versions for Windows, OSX, Android, Linux, etc.
https://gnupg.org/
I saw several of these recently, but they linked to an Office365 login page, not a Word document.
If you live in the UK also submit a report to Action Fraud. This is set up by the City of London Police to handle cyber crime/phishing.
http://www.actionfraud.police.uk/report_fraud
In the USA you can use – https://www.ic3.gov/complaint/default.aspx
Matt
Our domain users are receiving targeted emails on this today. If anyone including Docusign has lingering Malware or gets infected from this point forward I’d suggest using Malwarebytes Breach Remediation Tool (MBBR). Works great and not expensive at all.
What I don’t understand is why this Docusign service ever exists?
It’s not a real crypto signature – all they do is allow you to tick a box saying that you are “signing” the document and then pass that info onto the sender of the document.
What’s the advantage compared to simply asking anyone to “sign” something by replying “I am signing this document” by email? None of those options will hold in court but at least with direct email you’re not involving an useless third-party in the process.
Oh, it’s so much more than that: you get to pick the typeface from a vast selection of three or four styles!
/sarcasm off
Well, yesterday’s phishing campaign posing as DocuSign that sent over 1,000 targeted emails against my company (have to run a report to get the actual number) now makes sense as to where they had obtained the email addresses from. Luckily, our email filter stopped all of the emails from reaching the recipient this time.
Can share what attribute you blocked Nik ?
It doesn’t help that Docusign sends out marketing emails, thus getting user complacent about getting email from Docusign. I finally unsubscribed to Docusign marketing emails.
I never want an unsolicited email from most companies. Especially companies dealing with financial transactions.
I am a docusign user. I was affected by this noticed the suspicious email and immediately tweeted them and forwarded the email to their abuse department.
I alerted docusign and arstechnica on the 8th of this bug, not sure docusign took it seriously at first.
Typo: “On San Francisco-based DocuSign warned on May 9”
Looks like it’s supposed to be either “On May 9th San Francisco…” or just “San Francisco-based…”
Once again, this seems to be a solid push for using DKIM and SPF. Identifying if the emails actually do come from DocuSign (or any other expected and semi-trusted party) would be a good step towards establishing the bona fides of the received email.
From there maybe we can move on to not sending attachments except when explicitly stated in a communication ahead of time from a trusted party.
Then the best fun, making sure that links actually go where they say they go and never trusting a shortened one.
Still loads of flaws in these approaches, but they do reduce some risk. That said, they also increase the communication barrier and historically we’ve never appreciated or approved of things that do that. DKIM and SPF are the best in that they don’t cause the user to have extra work, and their work can be done in the background silently.
For their one domain, docusign.net, they do have DMARC configured for 100% reject. For their other domain though, docusign.com, they only have DMARC configured for reporting.
“making sure that links actually go where they say they go”
Even if the links go where they should, this check does not always work. I’ve seen links in spam with domain or sub-domain names that make perfect sense for the legitimate company.
And I’ve seen I’ve seen links in legitimate company email. with domain or sub-domain names that look like spam links.
I hate Docusign, I really hope this prompts employers not to use this for employee offer letters and applications. I should not be forced to trust my personal info to some third party with little accountability just to accept a job offer.
One of our users here in the UK got hit on Thursday. NHS gets WannaCry on Friday. Wonder if anyone in the NHS uses DocuSign? Could explain how they hit patient zero.
Has DocuSign proactively notified customers of this breach?
I saw a few blocked on xeams server and nobody in my domain has ever had a docusign account.
since it was blocked before hitting actual mail server I didn’t dig into headers or anything
We have messages dating back to August/September 2016 that show they were breached as far back as then….
Users of Docusign lose all control over when documents with their private information will be removed from the website. The document is retained indefinitely.
My insurance agent sent me a form to sign. This came in the form of an email from Docusign to me. There was a link in the email to access the document which contained private information. There is no authentication required to view the document. I signed it, and my agent received it. The agent then deleted the form from their Docusign account, and I also deleted it from my Docusign account. However, if I click on the original email from Docusign, the document is still visible. I spent over two hours with three different agents in Docusign support and they say there is no way to remove access to documents with my private information from the Internet. This is an unacceptable policy. I have asked them to enhance their system to allow deletion if all parties involved want the document deleted, but they said they cannot promise anything.
Thank you Brian for helping us alert customers and users to the temporary unauthorized access to email addresses via one of our non-core systems, and how best to protect from phishing attacks. Following up for your readers, as noted in your article, we ask that readers forward any suspicious DocuSign emails to spam@docusign.com and then delete them from your system. Again, thank you.
I’ve never used DocuSign in my life….until yesterday. It was for legitimate purposes and everything went smoothly. I’ve never received a DDoS threat e-mail against one of my domains…..until today! Coincidence?
I have used DocuSign multiple times in the past and have not received any emails. In general, people are over reacting to the fact that their email address may have been comprised but under react (in my opinion) when their banks are potentially comprised.
If companies can identify child pornography and people’s faces with high degree of accuracy…
Why couldn’t spam filters identify images (like Docusign’s logo) not originating from the trademark holder’s authoritative email servers?
I realize there is a boatload of technical details to fill in and questions to answer like, “Well what if it is forwarded…” but I would think the basic idea is sound.
It would be so very, very slow to do image processing on every email with a logo.
I believe this breach may have been caused by the Hancitor campaign threat actors. In the visitor.txt files the threat actors use to track their campaign I found 105 different occurances in which docusign email accounts showed up. The visitor’s email is only added to this file after the email recipient clicks the link and visits the link to the malicious word document. This implies that on 105 different occasions a user attempted to download a Hancitor infected document and at least began the download process.
The fact the threat actors stole information regarding Docusign customers also implies they took manual interest in the systems that were most likely infected by this same campaign. Since this Hancitor campaign then apparently according to Docusign abused that information for some of its recent waves.
Krebs if you would like I can provide you with the visitor.txt files like I did with lutech so they could get a better history of the accounts and companies potentially affected. Let me know if you would like those files for your own research.
Try using PhishPro, to help protect and secure your phishing emails. PhishPro will validate if the email is a Phishing email or legitimate email so you do not get fooled.
Thank you so much for this update.