A new report proves the value of following the money in the fight against dodgy cybercrime services known as “booters” or “stressers” — virtual hired muscle that can be rented to knock nearly any website offline.
Last fall, two 18-year-old Israeli men were arrested for allegedly running vDOS, perhaps the most successful booter service of all time. The young men were detained within hours of being named in a story on this blog as the co-proprietors of the service (KrebsOnSecurity.com would later suffer a three-day outage as a result of an attack that was alleged to have been purchased in retribution for my reporting on vDOS).
The vDos home page.
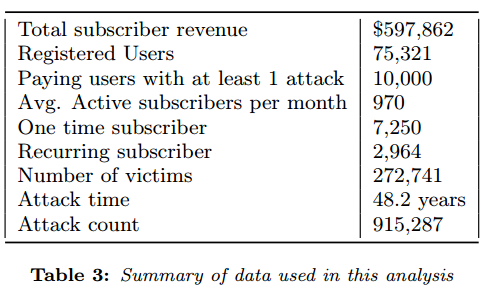
That initial vDOS story was based on data shared by an anonymous source who had hacked vDOS and obtained its private user and attack database. The story showed how the service made approximately $600,000 over just two of the four years it was in operation. Most of those profits came in the form of credit card payments via PayPal.
But prior to vDOS’s takedown in September 2016, the service was already under siege thanks to work done by a group of academic researchers who teamed up with PayPal to identify and close accounts that vDOS and other booter services were using to process customer payments. The researchers found that their interventions cut profits in half for the popular booter service, and helped reduce the number of attacks coming out of it by at least 40 percent.
At the height of vDOS’s profitability in mid-2015, the DDoS-for-hire service was earning its proprietors more than $42,000 a month in PayPal and Bitcoin payments from thousands of subscribers. That’s according to an analysis of the leaked vDOS database performed by researchers at New York University.
As detailed in August 2015’s “Stress-Testing the Booter Services, Financially,” the researchers posed as buyers of nearly two dozen booter services — including vDOS — in a bid to discover the PayPal accounts that booter services were using to accept payments. In response to their investigations, PayPal began seizing booter service PayPal accounts and balances, effectively launching their own preemptive denial-of-service attacks against the payment infrastructure for these services.
Those tactics worked, according to a paper the NYU researchers published today (PDF) at the Weis 2017 workshop at the University of California, San Diego.
“We find that VDoS’s revenue was increasing and peaked at over $42,000/month for the month before the start of PayPal’s payment intervention and then started declining to just over $20,000/month for the last full month of revenue,” the paper notes.
 The NYU researchers found that vDOS had extremely low costs, and virtually all of its business was profit. Customers would pay up front for a subscription to the service, which was sold in booter packages priced from $5 to $300. The prices were based partly on the overall number of seconds that an attack may last (e.g., an hour would be 3,600 worth of attack seconds).
The NYU researchers found that vDOS had extremely low costs, and virtually all of its business was profit. Customers would pay up front for a subscription to the service, which was sold in booter packages priced from $5 to $300. The prices were based partly on the overall number of seconds that an attack may last (e.g., an hour would be 3,600 worth of attack seconds).
In just two of its four year in operation vDOS was responsible for launching 915,000 DDoS attacks, the paper notes. In adding up all the attack seconds from those 915,000 DDoS attacks, the researchers found vDOS was responsible for 48 “attack years” — the total amount of DDoS time faced by the victims of vDOS.
“As VDoS’s revenue and active subscriber base dwindled, so did the amount of harmful DDoS attacks launched by VDoS,” the NYU researchers wrote. “The peak attack time we found was slightly under 100,000 attacks and 5 attack years per month when VDoS’s revenue was slightly over $30,000/month. This decreased to slightly under 60,000 attacks and 3 attack years during the last month for which we have attack data. Unfortunately, we have incomplete attack data and likely missed the peak of VDoS’s attack volume. However, the payment intervention correlates to a 40% decrease in attack volume, which equates to 40,000 fewer attacks and 2 fewer attack years per month.”
Although a small percentage of vDOS customers shifted paying for their monthly subscriptions to Bitcoin after their preferred PayPal methods were no longer available, the researchers found that most customers who relied on PayPal simply went away and never came back.
“Near the middle of August 2015, the payment intervention that limited vDOS’s ability to accept PayPal payments began to take its toll on vDOS,” the researchers wrote. “Disrupting vDOS’s PayPal payment channel had a noticeable effect on both recurring and new revenue. By August 2015, payments from the PayPal channel decreased by $12,458 (44%) from an average of $28,523 over the previous five months. The Bitcoin payment channel increased by $6,360 (71%), but did not fully compensate for lost revenue from PayPal.”
The next month, vDOS established a number of ad-hoc payment methods, such as other third-party payment processors that accept credit card payments. However, most of these methods were short lived, likely due to the payment processors learning about the nature of their illicit DDoS service and terminating their accounts, the researchers observed.
“The revenue from these other regulated payment channels dwindled over a ten month period from $18,167 in September 2015 to $1,700 during June 2016,” the NYU team wrote. “The last month of the database leak in July 2016 shows no other forms payments other than Bitcoin.”
Other developments since vDOS’s demise in September 2016 have conspired to deal a series of body blows to the booter service industry. In October 2016, Hackforums — until recently the most bustling marketplace on the Internet where people could compare and purchase booter services — announced it was permanently banning the sale and advertising of these services on the forum.
In December 2016, authorities in the United States and Europe arrested nearly three-dozen people suspected of patronizing booter services. The enforcement action was a stated attempt by authorities to communicate to the public that people can go to jail for hiring booter services.
In April 2017, a U.K. man who ran a booter service that delivered some 1.7 million denial-of-service attacks against victims worldwide was sentenced to two years in prison.
Prosecutors in Israel say they are preparing formal charges against the two young Israeli men arrested last year on suspicion of running vDOS.
Check out the full NYU paper here (PDF).




not much of a payoff considering the crime required to keep the service running.
The kids could have made another Talking Tom iOS/droid app and sold it to a Chinese soapbox company for $18 Billion instead. 🙂
That would have been the smart way to go – criminal minds aren’t much for activity that actually has a future. Whether crime pays or not, it still just ends in misfortune, darkness, and death.
One of the most difficult lessons in my life is that I can only grow the plants from the seeds I plant. If I plant weed seed in my life then I will harvest more weeds. It is hard work to remove them, so that I can plant good things. In fact many of the weeds I planted I couldn’t remove. I was stuck. I tried to cut them off, burn them out, and they would grow back from the root. I needed help. Only Jesus has been able to help me remove the junk that I planted in my life. The scars are deep from digging out some of those weeds. The peace of seeing the good crop of edibles is worth it. Good fruit growing in the place of weeds is always beautiful.
But don’t take my word for it. Google it.
bible.org/article/seven-laws-harvest
This was a great comment until you mentioned Jesus. Can we get him back to stop these cyber criminals?
When Jesus comes back it will all end.
Good Article
“In December 2016, authorities in the United States and Europe arrested nearly three-dozen people suspected of patronizing booter services.”
I don’t think this is the right approach. I mean, creating more criminals that will possibly be marked for life because of it making employment extremely hard and their lives miserable overall will only create another problem. A good, hard slap on the wrist that hurts but doesn’t ruin their lives should suffice. This obviously has to be proportional to the damage caused so it would be different if, say, the DDoS resulted in some death or something very severe.
I’d argue that even the people behind the service providing should get some sympathy. I mean, 18-year-old guys can be stupid and naive. It doesn’t help if we go around ruining lives forever at that stage. They are not dangerous criminals, they are just young fools after easy money with knowledge they have. The key here is punishment proportional to the severity of the crime. Sure DDoS can be very bad but we should be wise and punish accordingly not to create hardened criminals.
Here’s an idea – let them exchange their conviction for a couple of hours in a public stockade, so the victims can spit on them, throw tomatoes, and just generally harangue them with expletives. That was how it was in the old days, and it was very effective and reducing recidivism.
When a DDoS is launched against an e-commerce site for the purposes of extortion, it’s not an act that is ” stupid and naive”. It’s criminal. I have no problem with treating 18 year old criminals like criminals.
“I’d argue that even the people behind the service providing should get some sympathy.”
They deserve no sympathy at all. They literally cost businesses that their service DDoS’d thousands of dollars due to downtime & in server maintenance costs.
Throw the book at them.
Yes they caused real damage and they should be punished for it (contrary to what other comments think I’m advocating). If you really think we should throw the book at every crime ruining every life of every 1st-time criminal out there without giving them a chance to redeem and have a normal life then go ahead. It doesn’t work and it creates more people at the margins of society that frequently have no other means to get money to survive than turning to crime again when they are out of jail. OMG CRIMINALS, KILL THEM ALL has worked wonders in the US, no? Take a look in the justice/prison system of countries like Norway and you’ll see the stark contrast and how they aim to reinsert people into society, not just “throw the book”.
Or maybe Finland, home of the guy who grounded a plane with terroristic threats while the authorities looked on and did nothing except wait for his 18th birthday.
that poor dear. he needs sympathy not correction!
You think that simply arresting them is problematic? What kind of “good, hard, slap on the wrist” are you considering that would not involve law enforcement?
A stern talking to… From their father… *dreamily* when he gets home from the senate…
The real victims here are the criminals!
If the individual is not dangerous and cooperates why not direct him/her to community services and educational measures? There are other punishments aside from jailing people you know? By all means taking them into custody and putting some trackers to prevent them from running or even keep them locked up for a few days to let it sink into their heads. But law enforcement can punish with other less damaging alternatives aside from jail.
http://www.newyorker.com/business/currency/making-profits-on-the-captive-prison-market
I disagree, 18 year olds are young men and know exactly what they are doing. You say it yourself they are fools who think they can make easy money which it obviously was for a time by doing very little but why choose to make money off of others misfortune? They could have joined the youtube community uploading cute cat videos and made a living. These lads chose to be villains because they thought it was cool therefore they should be treated as such. Society is way to soft on criminals. It is partly why the world is in such a mess today.
Question is it even worted anymore.?
and if we punish…18 year old guy?? Why instead of punishing
we dont use his skills and talent for something else?
just think about it…we have so many unskilled people work as cybersecurity fields..my qyestion is why the skilled and talented people use their skills knowledge and for bad purpose?
So wait, let me get this straight, you want us to tolerate these criminals, and when they are finally caught you want to offer them a job? Would that not just encourage more technically minded individuals to commit crimes to land a Security in the event they are caught.
Dudes and dudetes, why all the anger? Sure they should suffer punishment and educational measures but why screw them permanently with prison and a criminal record when you can give them a chance and put their skills to good use in a honest job? I understand the impetus to punish, I’ve been victim to crimes before but if we can’t look past simple harsh punishment and into rehabilitation we will not solve the problem.
What anger?
I detect no anger in the comments.
As far as “community service” and “educational measures” go, they are useless.
There have to be adequate and sufficient consequences to a crime (or violation) to insure that the law (or rule) is obeyed.
” … why screw them permanently with prison and a criminal record when you can give them a chance and put their skills to good use in a honest job? ”
Successful reintegration of criminals into society is a different matter, and should be independent of the punishment imposed.
This practice is common in some eastern european nations, which kind of explains a lot about why those countries are the way they are. This is, as you noted, a form of reward, even encouragement, since legitimate jobs are often hard to come by (about which entire volumes have been written).
Even with income cut in half, that’s a lot of profit if their costs were small.
Go after the customers! They’re the ones that want the attacks to happen…
Is there a legitimate business use for these services?
There are some people that think a “booter” service could be legitimately used for web site load testing. That’s utterly false.
Valid web site load testing requires careful control of the number of virtual users. The target web site has to be monitored as the number of virtual users increases at a defined rate. And the web site performance logs have to be matched to the load testing activity to determine the system impact at each load level.
A “booter” or “stressor” service flings a load of crap at a web site. That’s not load testing.
What bugs me is Congress (US) is considering a “hack back” law. My first thought was people will hire jerks on the dark Web to do their hacking, including DDoS for hire.
When you’re under attack from a source investigating that source can sometimes lead to hacking charges, because probes and vulnerability scans can be considered forms of attack (depends on how outdated the laws are in your jurisdiction). If they can make those basic investigatory functions legal then the world would be a better place, even if it’s currently considered hacking.
Couldn’t happen to a nicer, more deserving set of “miscreants.”
Though it might be exceedingly difficult (maybe impossible), identification of recurring/dominant patterns (countries, firms, individuals, etc.) from whence those payments for vDOS services were being made — and whether there was any significant difference between the patterns of Bitcoin vs. PayPal payments — would be a mighty interesting research product for someone to produce.
Criminals are money success and profit hungry invidulas.
soft way of crimes are cybercrime,cybercrime will hold back violant crimes. If no more cybercrime…wolfs will be on the streeta with the knifes. simple is that.
Just a note: this and one other story on the homepage are dated June 17, eight days in the future. Precog?
The 17 is the year…not day. The larger number (In this case 06) Is the day, so it reads 6th of June 2017.
Seems like they are now getting some good treatment, the twitter account has not tweeted from last few hours.
now that’s like a real dox
Sorry, but this article is complete nonsense.
The following sums it up pretty well:
>“We find that VDoS’s revenue was increasing and peaked at over $42,000/month for the month before the start of PayPal’s payment intervention and then started declining to just over $20,000/month for the last full month of revenue,” the paper notes.
This shows how incredibly incompetent the authors of the paper were. vDos went from ~40k/month of mostly paypal payments to ~20k a month of only bitcoin payments. This is a significant increase in revenue, not a decline.
Paypal has been shutting down booter accounts for years, and vDos could lose several accounts a day. Generally less than half of the money would actually successfully make it’s way to the owners.
So, they were taken down due to illegally obtained evidence from someone hacking them
This shows how incredibly incompetent the authors of the paper were. vDos went from ~40k/month of mostly paypal payments to ~20k a month of only bitcoin payments. This is a significant increase in revenue, not a decline.