For several months I’ve been poking at a decent-sized spam botnet that appears to be used mainly for promoting adult dating sites. Having hit a wall in my research, I decided it might be good to publish what I’ve unearthed so far to see if this dovetails with any other research out there.
In late October 2016, an anonymous source shared with KrebsOnSecurity.com a list of nearly 100 URLs that — when loaded into a Firefox browser — each displayed what appeared to be a crude but otherwise effective text-based panel designed to report in real time how many “bots” were reporting in for duty.
Here’s a set of archived screenshots of those counters illustrating how these various botnet controllers keep a running tab of how many “activebots” — hacked servers set up to relay spam — are sitting idly by and waiting for instructions.
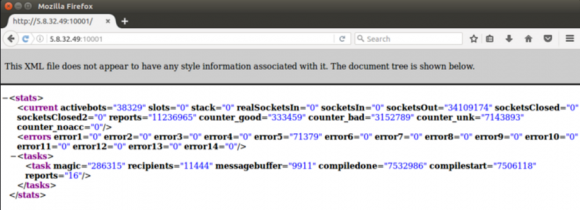
One of the more than 100 panels linked to the same porn spamming operation. In October 2016, these 100 panels reported a total of 1.2 million active bots operating simultaneously.
At the time, it was unclear to me how this apparent botnet was being used, and since then the total number of bots reporting in each day has shrunk considerably. During the week the above-linked screen shots were taken, this botnet had more than 1.2 million zombie machines or servers reporting each day (that screen shot archive includes roughly half of the panels found). These days, the total number of servers reporting in to this spam network fluctuates between 50,000 and 100,000.
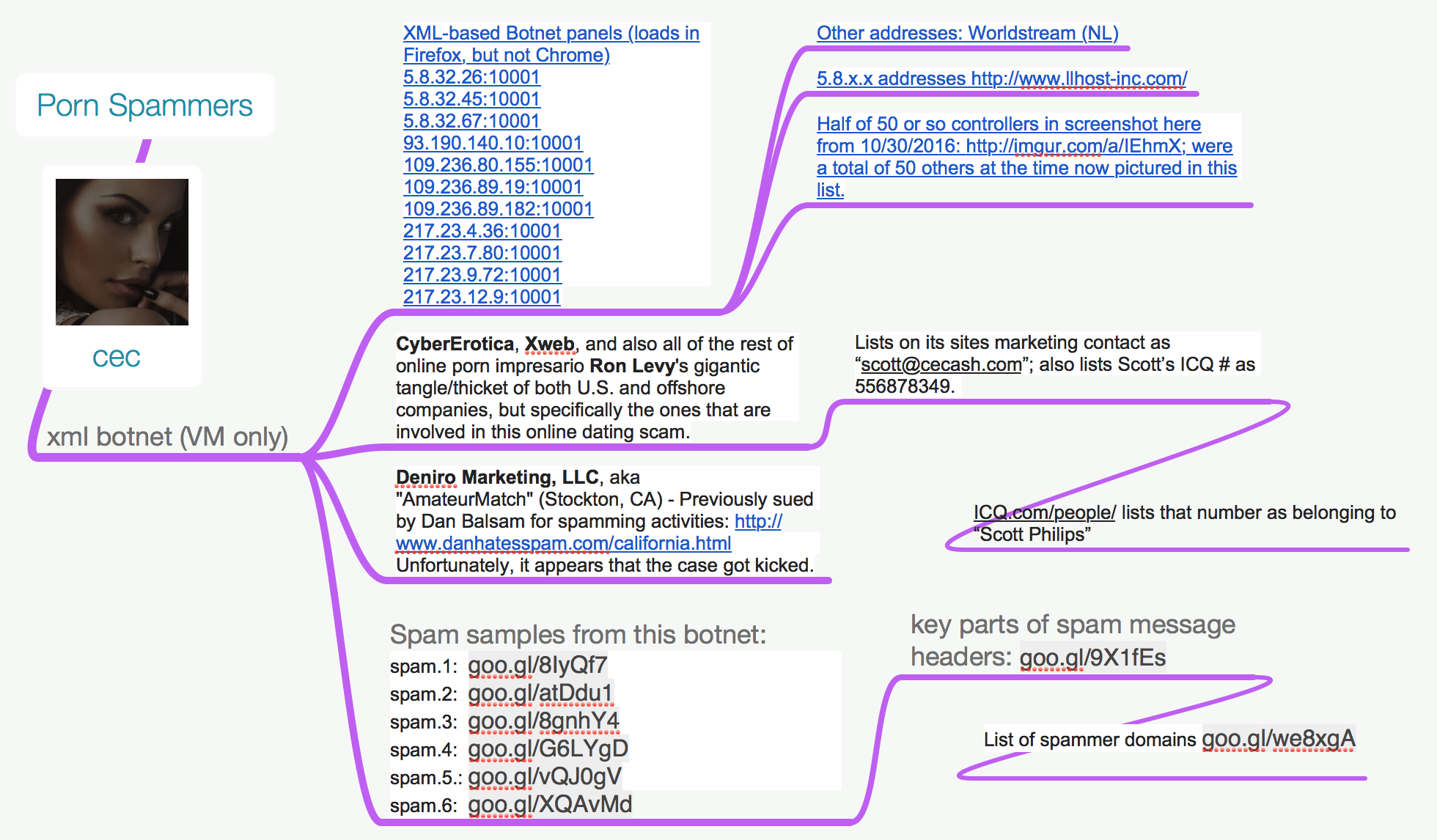
Thanks to a tip from an anti-spam activist who asked not to be named, I was able to see that the botnet appears to be busy promoting a seemingly endless network of adult dating Web sites connected to just two companies: CyberErotica, and Deniro Marketing LLC (a.k.a. AmateurMatch).
As affiliate marketing programs go, CyberErotica stretches way back — perhaps to the beginning. According to TechCrunch, CyberErotica is said to have launched the first online affiliate marketing firm in 1994.
In 2001, CyberErotica’s parent firm Voice Media settled a lawsuit with the U.S. Federal Trade Commission, which alleged that the adult affiliate program was misrepresenting its service as free while it dinged subscribers for monthly charges and made it difficult for them to cancel.
In 2010, Deniro Marketing found itself the subject of a class-action lawsuit that alleged the company employed spammers to promote an online dating service that was overrun with automated, fake profiles of young women. Those allegations ended in an undisclosed settlement after the judge in the case tossed out the spamming claim because the statute of limitations on those charges had expired.
What’s unusual (and somewhat lame) about this botnet is that — through a variety of botnet reporting panels that are still displaying data — we can get live, real-time updates about the size and status of this crime machine. No authentication or credentials needed. So much for operational security!
The “mind map” pictured below contains enough information for nearly anyone to duplicate this research, and includes the full Web address of the botnet reporting panels that are currently online and responding with live updates. I was unable to load these panels in a Google Chrome browser (perhaps the XML data on the page is missing some key components), but they loaded fine in Mozilla Firefox.
But a note of caution: I’d strongly encourage anyone interested in following my research to take care before visiting these panels, preferably doing so from a disposable “virtual” machine that runs something other than Microsoft Windows.
That’s because spammers are usually involved in the distribution of malicious software, and spammers who maintain vast networks of apparently compromised systems are almost always involved in creating or at least commissioning the creation of said malware. Worse, porn spammers are some of the lowest of the low, so it’s only prudent to behave as if any and all of their online assets are actively hostile or malicious.
FOLLOW THE HONEY
So how did KrebsOnSecurity tie the spam that was sent to promote these two adult dating schemes to the network of spam botnet panels that I mentioned at the outset of this post? I should say it helped immensely that one anti-spam source maintains a comprehensive, historic collection of spam samples, and that this source shared more than a half dozen related spam samples. Here’s one of them.
All of those spams had similar information included in their “headers” — the metadata that accompanies all email messages.
Received: from minitanth.info-88.top (037008194168.suwalki.vectranet.pl [37.8.194.168])
Received: from exundancyc.megabulkmessage225.com (109241011223.slupsk.vectranet.pl [109.241.11.223])
Received: from disfrockinga.message-49.top (unknown [78.88.215.251])
Received: from offenders.megabulkmessage223.com (088156021226.olsztyn.vectranet.pl [88.156.21.226])
Received: from snaileaterl.inboxmsg-228.top (109241018033.lask.vectranet.pl [109.241.18.33])
Received: from soapberryl.inboxmsg-242.top (037008209142.suwalki.vectranet.pl [37.8.209.142])
Received: from dicrostonyxc.inboxmsg-230.top (088156042129.olsztyn.vectranet.pl [88.156.42.129])
To learn more about what information you can glean from email headers, see this post. But for now, here’s a crash course for our purposes. The so-called “fully qualified domain names” or FQDNs in the list above can be found just to the right of the open parentheses in each line.
When this information is present in the headers (and not simply listed as “unknown”) it is the fully-verified, real name of the machine that sent the message (at least as far as the domain name system is concerned). The dotted address to the right in brackets on each line is the numeric Internet address of the actual machine that sent the message.
The information to the left of the open parentheses is called the “HELO/EHLO string,” and an email server administrator can set this information to display whatever he wants: It could be set to bush[dot]whitehouse[dot]gov. Happily, in this case the spammer seems to have been consistent in the naming convention used to identify the sending domains and subdomains.
Back in October 2016 (when these spam messages were sent) the FQDN “minitanth.info-88[dot]top” resolved to a specific IP address: 37.8.194.168. Using passive DNS tools from Farsight Security — which keeps a historic record of which domain names map to which IP addresses — I was able to find that the spammer who set up the domain info-88[dot]top had associated the domain with hundreds of third-level subdomains (e.g. minithanth.info-88[dot]top, achoretsq.info-88[dot]top, etc.).
It was also clear that this spammer controlled a great many top-level domain names, and that he had countless third-level subdomains assigned to every domain name. This type of spamming is known as “snowshoe” spamming.
Like a snowshoe spreads the load of a traveler across a wide area of snow, snowshoe spamming is a technique used by spammers to spread spam output across many IPs and domains, in order to dilute reputation metrics and evade filters,” writes anti-spam group Spamhaus in its useful spam glossary.
WORKING BACKWARDS
So, armed with all of that information, it took just one or two short steps to locate the IP addresses of the corresponding botnet reporting panels. Quite simply, one does DNS lookups to find the names of the name servers that were providing DNS service for each of this spammer’s second-level domains.
Once one has all of the name server names, one simply does yet more DNS lookups — one for each of the name server names — in order to get the corresponding IP address for each one.
With that list of IP addresses in hand, a trusted source volunteered to perform a series of scans on the addresses using “Nmap,” a powerful and free tool that can map out any individual virtual doorways or “ports” that are open on targeted systems. In this case, an Nmap scan against that list of IPs showed they were all listening for incoming connections on Port 10001.
From there, I took the IP address list and plugged each address individually into the URL field of a browser window in Mozilla Firefox, and then added “:10001” to the end of the address. After that, each address happily loaded a Web page displaying the number of bots connecting to each IP address at any given time.
Here’s the output of one controller that’s currently getting pinged by more than 12,000 systems configured to relay porn spam (the relevant part is the first bit on the second line below — “current activebots=”). Currently, the entire botnet (counting the active bots from all working bot panels) seems to hover around 80,000 systems.
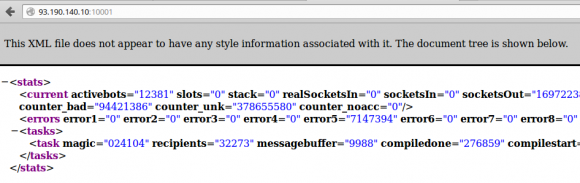
At the time, the spam being relayed through these systems was advertising sites that tried to get visitors to sign up for online chat and dating sites apparently affiliated with Deniro Marketing and CyberErotica.
Seeking more information, I began searching the Web for information about CyberErotica’s affiliate offerings and I found that the affiliate program’s marketing division is run by a guy who uses the email address scott@cecash.com.
A Google search quickly reveals that scott@cecash.com also advertises he can be reached using the ICQ instant messenger address of 55687349. I checked icq.com’s member lookup page, and found the name attached to ICQ# 55687349 is “Scott Philips.”
Mr. Philips didn’t return messages seeking comment. But I couldn’t help wonder about the similarity between that name and a convicted Australian porn spammer named Scott Phillips (NB: two “l’s in Phillips).
In 2010, Scott Gregory Phillips was fined AUD $2 million for running a business that employed people to create fake profiles on dating websites in a bid to obtain the mobile phone numbers of dating website users. Phillips’ operation then sent SMS texts such as “get laid, text your number to…”, and then charged $5 on the mobile accounts of people who replied.
Phillips’ Facebook page and Quora profile would have us believe he has turned his life around and is now making a living through day trading. Reached via email, Phillips said he is a loyal reader who long ago quit the spam business.
“I haven’t been in the spam business since 2002 or so,” Phillips said. “I did some SMS spam in 2005, got about 18 million bucks worth of fines for it, and went straight.”
Phillips says he builds “automated commodity trading systems” now, and that virtually all modern spam is botnet-based.
“As far as I know the spam industry is 100% botnet these days, and not a viable proposition for adult sites,” he told KrebsOnSecurity.
Well, it’s certainly a viable proposition for some spammer. The most frustrating aspect of this research is that — in spite of the virtually non-existent operational security employed by whoever built this particular crime machine, I still have no real data on how the botnet is being built, what type of malicious software may be involved, or who’s responsible.
If anyone has additional research or information on this botnet, please don’t hesitate to leave a comment below or get in touch with me directly.




LMAO .. Those polish domains come from my home town in Poland … I guess I’m in the wrong business lol
Best business is bank transfers.
best profit
now canada and usa run good.
Ha ha ha spamerzy z Suwałk nakryci przez Briana Krebsa! Podlasie RULEZ!
@Brian as usually great research. Regards from Poland!
Spammers are lower then pond scum,
Some RBLs look at the age of the FQDN as part of their reputation. This article makes the reason obvious.
Email servers take a good afternoon of work for me to set up. I suppose these spammers have the process automated, but my gut feeling is these dime a dozen domains just have a very basic relay on them.
What’s so spectacularly stunning about this is that the spammer/botnet operator has been able to be so careless and/or so inept… leaving the real-time monitoring port (10001) on all of the C&C servers for his botnet naked and open, for all the world to see.
Does it really matter? What is “the world” going to do about it?
For me the most spectacularly stunning thing was seeing the letters I-C-Q next to each other for the first time in 15 years. Does he also have a Friendster account?
Icq is much more common than you realize apparently…with OTR these miscreants feel safe communicating and doing business over icq regardless of how old the software is. Look at any of Krebs posts with ads from underground marketplaces and you’ll see ICQ listed on probably 95% of them or more.
LosPollos.com dating program used AS202023 for their landers.
adam@cestaff.com runs CEcash.
Their dating site is citysexcash.com
Been known scammers since day 1
Luke Ford knows more about Scot Phillips porn exploits than anyone. https://en.wikipedia.org/wiki/Luke_Ford_(blogger)
Brian, might try checking some of the IPs/URLs etc on Threatcrowd.org. It is a nice place to get visualizations and you might be able to put together some more information.
80000 bots down from 1.2 million is a work in progress, we need to sort this out to put these people out of business
Does it really matter? What is “the world” going to do about it?
I too was surprised to see ICQ was still around. So I tried logging in with an old account I had last used in 2000, and was successful.
However, when I tried to change my PW, it said my OLD PW was “not secure enough”, (the new one was very secure), so I could not change it. Also, although I added an SMS auth, I could not add an email address. I suspect that my old PW was being checked again for complexity, since it was required when adding an email address. So, I conclude their website has significant problems, if you are trying to use an old account.
I was also surprised to learn that they are now owned by a company, headquartered in Moscow. I wrote to the ICQ partners email address, (icq_partners[AT@AT]corp.mail.ru) asking what their plans are for the ICQ, since it still has all its old user database.
Although my old PW wasn’t secure, at least I had the presence of mind to never use the same PW twice on another site, since presumably ANY PW you had from your old account, this company now has, as well as all your old contacts.
Dan Balsam, of danhatesspam.com, has four small claims court judgements in his favor against Deniro Marketing Llc. A California-level court dismissed a fifth case between the two.
danhatesspam.com/cases/deniro_4ac.pdf January 2015.
The reason you can see XML in Firefox is that there’s a special handler for raw XML in Firefox.
If you prefixed the URL with view-source: in Chrome, you’d see similar content. Alternative, you could open the debug tools view of chrome and get something similar.
The reason the feature exists in Firefox is that otherwise, a reason XML document (one without an attached CSS stylesheet) would have no presentation, which is really unhelpful to web developers.
Excuse me but how does this relate to the porn industry??? You keep saying it’s dating and chat sites but that’s not in any way related to adult models or their careers, calling us the lowest of the low is just crazy offensive. Stop trying to ruin the things we do!! No shame in porn!
Guess reading comprehension is a challenge. The story is about porn spammers, not pornographers.