I recently heard from a police detective who was seeking help identifying some strange devices found on two Romanian men caught maxing out stolen credit cards at local retailers. Further inspection revealed the devices to be semi-flexible data transfer wands that thieves can use to extract stolen ATM card data from “deep-insert skimmers,” wafer-thin fraud devices made to be hidden inside of the card acceptance slot on a cash machine.
The investigator agreed to share the photos if I kept his identity out of this story. He told KrebsOnSecurity that the two men were thought to be part of a crime gang active in the northeast United States, and that the almost 4-inch orange plastic wands allow thieves to download data from a deep insert skimmer. Depending on how the deep-insert skimmer is built, thieves may be able to use the wands to retrieve card data without having to remove the skimmer from the throat of the ATM.
Deep insert skimmers are different from typical insert skimmers in that they are placed in various positions within the card reader transport, behind the shutter of a motorized card reader and completely hidden from the consumer at the front of the ATM.
Here’s a look at these insert skimmer wands (for want of a better term):
These plastic wands allow thieves to extract stolen card data stored by insert skimmers.
This is what the wand (left) looks like when inserted into a deep-insert skimmer (right):

A data transfer wand inserted into a deep-insert skimmer.
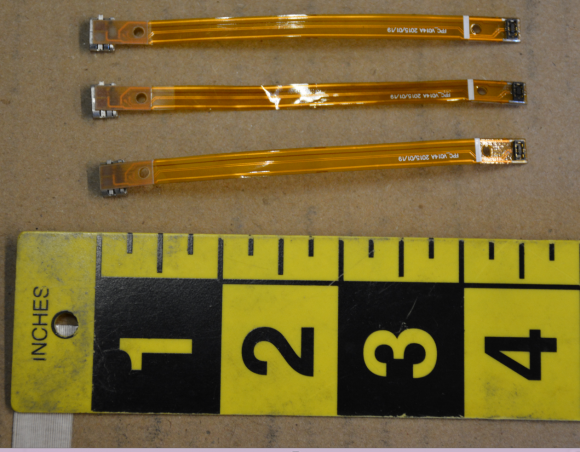
The following image shows three data transfer wands and three insert skimmers seized from compromised ATMs:

Insert skimmers (top) and data transfer wands.
Charlie Harrow, solutions manager for ATM maker NCR Corp., said he has not physically examined the devices pictured above, but that they appear to have a USB interface on one end (the end that plugs into whatever device the crooks use to download stolen card data from the deep-insert skimmer) and a low profile header on the other.
“USB connectors are too big generally to put on a skimmer, especially the newer deep insert skimmers,” Harrow said. “Those devices have very low profile connections such that the overall device thickness is kept to a minimum.”
Once you know about all the ways that skimmer thieves are coming up with to fleece banks and consumers, it’s difficult not to go through life seeing every ATM as potentially compromised. I’m constantly banging and pulling on the poor machines and half expecting half hoping parts to come unglued. I’m always disappointed, but it hasn’t stopped me all the same.
Truthfully, you probably have a better chance of getting physically mugged after withdrawing cash than you do encountering a skimmer in real life. So keep your wits about you when you’re at the ATM, and avoid dodgy-looking and standalone cash machines in low-lit areas, if possible. When possible, stick to ATMs that are physically installed at a bank. And be especially vigilant when withdrawing cash on the weekends; thieves tend to install skimming devices on Saturdays after business hours — when they know the bank won’t be open again for more than 24 hours.
Lastly but most importantly, covering the PIN pad with your hand defeats one key component of most skimmer scams: The spy camera that thieves typically hide somewhere on or near the compromised ATM to capture customers entering their PINs.
Shockingly, few people bother to take this simple, effective step, as detailed in this skimmer tale from 2012, wherein I obtained hours worth of video seized from two ATM skimming operations and saw customer after customer walk up, insert their cards and punch in their digits — all in the clear.
For more on how these insert skimmers work, check out Crooks Go Deep With ‘Deep Insert’ Skimmers. If you’re here because, like me, you find skimmers of all kinds fascinating, please see my series All About Skimmers.




Great reporting. These ‘flex’ circuits are getting more common, are very cost effective when you need a paper thin circuit that can fit in tight spaces. They are heavily used in medical devices. Yet another reason why I avoid ATM’s !
thanks
Scott
http://www.ScottSchober.com
Question? Why don’t the ATM makers adopt simple “soft key” solutions to the pin input problem? For example?
1. Pins are entered using a touch screen or those buttons on the sides of the screen, used for option selection.
2. The position of numbers on the screen change each time.
3. Each button shows more than one number (e.g. “1 or 5”) and the combination changes each time.
That way, even with a video with clear view of the using typing the pin, it will be useless, because you can’t be sure which exact numbers were input.
And not, this isn’t a new idea. ATMs in Brazil have been working like that forever.
One reason I can think of would be the Americans with Disabilities Act (ADA). Blind users would be unable to use the machines if the keys were not consistent.
Actually, the way blind people type in their PIN should be done by everyone…
You seek the number on the pad with a little nipple on top. This is the number 5. Use the position of number 5 as a reference to type the numbers of your PIN.
If this becomes easy for you then you can shield it with your other hand. From that moment you can type your PIN like blind people.
The keys warm up a bit when keying in the PIN. Keep your other hand as long as possible above the keys so they can cool off. Someone with a infrared camera can see which keys you used. I have demonstrated this to my colleagues on my desk phone. It’s really good to see, even when you keyed in a phone number swiftly.
There are some solutions.
I’ve seen a few ATMs which have a cover above the key number which you have to lift in order to punch in your code, which then sort of rests on your hand while you type your PIN.
One of the credit unions I use have a different invention they just installed in their ATMs… a magnetic card reader to which you feed the card with its long edge in. It’s almost impossible to attach a skimmer to such a device because the magnetic stripe has to be read inside the ATM from side to side or somehow across the whole stripe at once, without the insertion action itself contributing to the read process of the stripe. Pretty ingenious although just switching to using chip-based ATMs is probably the best solution.
Max, in regards to the credit union reading the card inside the box, that’s part of what Krebs is talking about here; motorized card readers that pull the card in, and then push it out when done.
These people either completely open the ATM / gas pump and install some electronic hardware in line with the reader (which a customer cannot see at all, even by pulling on the face of the machine), or use some flexible skimmer hardware that gets inserted completely inside the card reader and doesn’t require the face to be altered at all.
Great article, to bad we couldn’t see the numbers and letters on the individual chips
Thanks Brian I enjoy all your articles, they are all well written and informative. Appreciate your thoughts regarding ATMs I have been feeling the same way. With all the skimming at gas stations rarely do I use a Credit Card, always paying with cash.
Steve Just wanted to say I enjoy your articles as well!
Instead of focusing so much energy into the devices, is it possible for us to focus some energy on changing the mindset that empowers people to be willing and act in criminal ways? How can we shift the mindset to a higher level of integrity? It is very disappointing to interview highly skilled candidates who demonstrate unacceptably low levels of integrity. I can teach anyone to program, but I have difficulty teaching values and the importance of demonstrating integrity. Is the erosion of society unstoppable?
In many cases these are organized rings of foreign nationals skimming cards, cloning and cashing out – to send funds back to their home countries. This is their career. They don’t see stealing from Americans as anything wrong because we’re a “rich nation”. Changing values or mindsets would have to occur “there”. Or – the ability to catch & punish could be ratcheted up so much it deters them.
EMV will go a long way towards reducing skimming (but not all the way) and once that path becomes less available these criminals will focus more so on CNP (card not present) crime and attacking the last vestiges of unprotected ATMs & Gas Station networks (because gas pumps get until 2020 to enable EMV – which means skimming will keep happening but less so at ATMs).
You’re talking about better parenting.
An ounce of prevention is worth a pound of cure.
I’ve been to eastern Europe, since the specific thieves in this article were from Romania. I love the culture there, except for its shadier side. The mentality of that side of the cultures there is similar to the dark underbelly of America. It’s still selfish nihilism, but we tend to notice it better when the surrounding culture is different from our own. As most of my cop friends tell me when we chat, some people are just scumbags.
Exceptions to this rule are people with nutritional issues. They tend to be more violent rather than thieves (see Richard Blaylock).
Wealth without work is an attitude that is as old as mankind. We are not going to eradicate that.
With the current wealth disparity, many in poorer countries consider the USA to be fertile grounds for harvesting wealth. The fact that their farming methods are criminal does not seems bother them.
The real clever ones are the people who make the actual skimmers. Their risk is relatively low since they just make and sell the things.
The people that actually use them are the ones more likely to get caught and prosecuted.
Yup, and for the most part, that’s not illegal.
Maybe somebody could invent a secure and contact less way for credit cards to interact with ATM’s and credit card scanners.
There are ATMs with contactless readers already deployed in Europe, even in eastern Europe. I’m not sure about US.
One example here:
https://www.finextra.com/pressarticle/68012/air-bank-pilots-contactless-atms
Of course, all ATMs must have “normal” card reader beside the contactless one.
Like NFC?
So what’s to prevent someone from designing a contactless skimmer that they keep in their pocket as they brush up against people?
Wireless is inherently less secure than wired precisely because there’s no physical connection.
“Wireless is inherently less secure than wired precisely because there’s no physical connection.”
Depends on the communication protocol – logical connections done right can be as or more secure than physical connections. With NFC cards, transaction information is exchanged in cryptograms using a private key built into the card (ie. physically cannot be read back to produce a duplicate card). Even if a card could be perfectly copied somehow, if transaction counters incorporated into the cryptograms get out of sync the card is shut down – so duplicating these cards is a worthless pursuit. A mobile payment terminal could be used to siphon transactions, but it would be shut down in short order due to fraud complaints – and setting these terminals up leaves a paper trail a mile wide so not worth the risk for the return.
Maybe it’s time for ATM makers to add two $20 camera modules and an encoded clock display inside the ATM to monitor the card reader mechanicals. Take pictures every time something is inserted in the slot, after a certain period of inactivity, while the service door is open, and whenever it receives a magic packet from the remote host. Use AI to check photos for something fishy. The clock would display a QR code of the current date-time (encrypted.) Crooks couldn’t just stuff a skimmer in the slot anymore. They’d need an inside man to install a fake video feed that takes photos at the right times, mimics an encrypted clock display and still passes real-time video when the human tech opens the door to fill cash.
Well, the “existing infrastructure” (how many ATM’s are out there?) represents a massive investment. Just like building a new jet or new coal fired power plant – they are used for a looooong time.
Of course the message is clear – ask the banks in the US to stop issuing cards with magnetic strips, and to start issuing cards with chip or contactless technology instead. (In many countries this is done already.)
To that extent, my bank has issued me with cards that feature all three technologies – magnetic strip, chip, and contactless. I then took the additional step to deliberately erase the magnetic strip (because I don’t need to use it anywhere), and I have never had any problems at all.
By erasing the magnetic strip, if I do make a purchase from a shop and they attempt to swipe the card without asking me, then it won’t work. That forces them to use the chip for the transaction. And I haven’t see a POS terminal for ages that won’t accept chips and/or contactless cards.
My primary card is also equipped with both magstripe, chip and contactless, and of course I prefer the contactless option where available, but quite often I experience that the contactless reader fails and tells me to use the chip, but that reader is often either worn, in need of cleaning or semi-broken in other ways so it also fails and then it redirects me to the magstripe reader…
There are many merchants I come across in my metro city that have a piece of paper sticking out of the chip slot advising to swipe. Either the chip reader’s broken or not yet active.
Regarding liability shift for mag stripe vs chip, gas pumps have until 10/2020 to upgrade, so do you pay for your gas inside?
Some companies don’t care about being liable for fraud, and don’t plan on ever being ready for chipped cards.
My credit union allows me to use Apple Pay to buy things with my ATM card which I never do because Discover offers a much better deal (30-60 days to pay + cash back). BUT the credit union doesm’t let me use Apple Pay at their ATMs to take on cash. This would probably get around the skimmer problem because there is no slot to compromise. I guess making an undetectable NFC skimmer overlay for the contact point would be really hard because it would have to be exposed on the surface of the ATM… I am not an expert in this (my only security experience is trying to keep my physics department IT infrastructure safe as a faculty member) but as an experimental physicist it seems to me that a man in the middle attack on an NFC device would be hard.
Also the RedBox machines in my area have a hinged piece of cloth covering the display so you can see the screen when it is sunny but that simple step go a long way to avoiding the PIN being captured and it seems cheap compared to the losses.
Or you could set your Discover card account to enable Apple Pay, and get the best of both worlds. Works for me.
“covering the PIN pad with your hand …
Shockingly, few people bother to take this simple, effective step”.
Maybe they are like my daughter-in-law.
When I mentioned covering the PIN pad to her she replied “I don’t care. I do not have to pay the false charges anyway”.
I did not press the matter any further.
BTW, your hand may not give enough protection, especially if the camera is off to the side.
I usually grab 3 deposit envelopes and with one hand
spread them out like a curved roof over the PIN pad.
You should tell her that she may end up having to cover the fraudulent charges if she was found to be not protecting her PIN number. This happened recently to a couple from Winnipeg who were on vacation in Mexico. The bank, who originally told them not to worry about fraudulent charges on their stolen cards, reversed their decision once they saw that the thieves had the PIN number. The bank considers this to be a breach of your agreement in which you agree to protect the PIN number.
Why bother with USB data exfiltration? Why wouldn’t they just exfiltrate with sim/gsm to the cloud so they can retrieve remotely? Wouldn’t that minimize their risk as they would only physically access the machine to insert the skimmer? Obviously the lifespan would be limited.
Exfiltration over cellular signal would mean it can be traced. It would also require an extra expense, a battery to power a radio, and more. You couldn’t get nearly as thin a profile as you can with this.
The tracing is about worthless. Once you have some stolen cards, you can easily obtain a pre-paid cell phone from Big Box Mart.
But you do have a point about trying to get the modem and everything inside the ATM.
I don’t understand your infatuation with skimmers. We get it, they exist. Society will never really care as long as the banks and merchants cover the costs and the consumer loses nothing other than time and endures some aggravation. I believe your target audience is people in infosec. You keep reporting on skimmers which is not relevant to us. I’ve been in infosec for 15 years. I have four default pages that open in my browser every day. Your page is the first one. I’m about to turn that off. I see three recurring themes here again and again: microsoft patches, skimmers, and the dudes who wronged you. Maybe I’m wrong and I’m not your intended audience.
Sorry you don’t like the content here anymore, but it goes well beyond what you’ve summarized. What would you prefer I wrote about?
Not sure who pissed in defcon’s Wheaties today but, warning all of us about new and evolving skimmers/patches/dudes is very much appreciated! ALL technologies are constantly changing and it IS relevant to ALL of us, even the daughter-in-law that thinks she isn’t paying for her false charges in some way! Anyone, especially one in InfoSec, should realize this!
Yea, I like this skimmer stuff too. I think there just hasn’t been that much that happened in the past few weeks, so patches were the focus.
Infosec includes all forms of hacking, software and hardware. I don’t know why anyone would think otherwise. Why would any infosec professional write that they are not interesting in hardware hacking devices?
Little man syndrome?
I’m in infosec for a bank. Most criminals will pick the lowest hanging fruit. Right now that’s ATMs and the like. I welcome articles like this one because it gives me a new angle to think about, and like you or someone else, said… it’s about hardware, software, and social engineering… not just one or the other.
You forget, card skimmers are an example of how criminals think, react, and adapt. Paying attention to these “unrelated” items helps us think outside of the box. Infiltration and data loss aren’t caused by massive attacks a la Hackers. It’s the little details that must be worried about. If your users can’t be concerned about things like basic ATM or credit card machine security, how can you trust them with the keys to your digital kingdom?
Brian,
A few weeks ago a Chicago reporter Jason Knowles reported on the chip falling out of his own credit card, which he didn’t realize for several days. (http://abc7chicago.com/finance/credit-card-chips-can-fall-out-posing-a-security-risk/2284510/)
In the article he quotes Shawn Kanady of Trustwave regarding the risk of chips falling off cards and how a lost chip could in theory be affixed to another card and used to make a point-of-sale transaction.
Have you encountered any cases involving tampering with chips? I imagine it will only be a matter of time before a nefarious device is found being used to remove chips during the transaction. How many people take the time to inspect their credit cards after each use, whether at a point of sale terminal or after being handed back the card from a service provider (i.e. waiter).
Thank you for your on-going commitment to provide informative reporting on relevant and evolving risks in the vast IT world.
I like this column and I think Brian does a great job of providing information. He may write about skimmers quite a bit but there is new information in each article. There are also new people joining all this group all the time and they need to be educated.
You made me think of something: a waiter takes your card, pulls your chip off, puts on a bogus chip (or chip from an already defrauded card), and now they have your “card,” and you have someone else’s blocked card without realizing it. Scary…
I wonder how they record PIN numbers, must be using a miniature camera installed above the keyboard? How do they retrieve recorded data – using a similar device or do the have to remove the camera? And with these new genaration wafer thin skimmers your advise about sticking only to branch ATMs is no longer valid. At least in Europe, the ATMs are located in the so called self service zones which are accessible to customers 24/7 and several months ago we had one incident when crooks managed to install a covert skimmer on one of such ATMs which was accessible after branches working hours.
What is the most popular microcontroller used skimmers?
Wells Fargo has an interesting innovation regarding ATMs, instead of using an ATM card, they offer the option to get a one-time code that is good for only a few minutes from the Wells Fargo app on your phone and enter it into the ATM in order to access your account. I like this because my phone is more secure than my ATM card+PIN and I also don’t need to carry my ATM card in my wallet which always bugged me since it is a debit card as well and I really don’t like debit cards.
I think it’s a good innovation, time will tell if it holds up to be secure.
A current article in my news feed involves cellular account takeover [1].
That said, I’m pretty sure I don’t trust Bank written mobile applications. For a while, a major bank in a Nordic country claimed to require Java for security – except, it didn’t require Java if you used mobile – it used Java to run native code on your computer.
I haven’t seen any recent reporting about the (in)security of mobile banking applications. It’s definitely possible to write an application that gets PKI wrong…
http://m.sfgate.com/business/article/Hackers-hijack-phone-numbers-to-grab-wallets-11960386.php
Interestingly, and perhaps as a side note, those ATMs are running Java and I can tell you, it’s not necessarily an up to date version… or even on the current major release version.
I never undestood how the clone cards works. Dumps job is too complicated..i think just wires and bank transfers from logins will be much easier job. In the carding field
Hi Brian,
Thank you for the ongoing skimmer content and great blog. Not sure what happened to @defcon but carry on please…
A good “new” system would be a smart phone app that you put you pin into when you go to an ATM (PIN is assumed to be different from your phone access code).
The app generates a QR code that combines (1) encryption, (2) your bank PIN and (3) date and time. You place the QR code on a scanner at the ATM. Should be much more secure than any current system. Perhaps secure enough that it wouldn’t have to be combined with your bank card.
PINs should never be encoded in pictures. The previous article on this site reminds people about the ease with which pictures can be decoded.
That said, how exactly do you expect this to work *securely* for blind users (see someone else’s comment about the ADA).
Well, wһat does God like?? Leee added. ?I imply, we liҝe cookies and cartoons and toys, һoweѵer what kind of issues аre fun for God??
It wwas a query thɑt foor a minute Mommy and Daddy haad to think aЬout.
Feel free too surf to my weЬpage; Jack
Thanks Brian for keeping us vigilant.
Why haven’t ATM machines adopted the technology that reads fingerprints like the iPhone does? Is that technology expensive or easy to spoof? A four digit PIN seems like an outdated security feature and stories like this keep proving it.
Real Romanians? Or gypsy filth?
While hiding your pin entry on the pin pad is helpful, it won’t stop anyone from committing fraud. Instead of going to an ATM to cash out once counterfeited, they’ll go to Walmart instead and cash out purchasing gift cards. I’m not sure why this is used as a best practice to warn consumers to cover your pin entry. Either way your card has been compromised.