Equifax last week disclosed a historic breach involving Social Security numbers and other sensitive data on as many as 143 million Americans. The company said the breach also impacted an undisclosed number of people in Canada and the United Kingdom. But the official list of victim countries may not yet be complete: According to information obtained by KrebsOnSecurity, Equifax can safely add Argentina — if not also other Latin American nations where it does business — to the list as well.
 Equifax is one of the world’s three-largest consumer credit reporting bureaus, and a big part of what it does is maintain records on consumers that businesses can use to learn how risky it might be to loan someone money or to extend them new lines of credit. On the flip side, Equifax is somewhat answerable to those consumers, who have a legal right to dispute any information in their credit report which may be inaccurate.
Equifax is one of the world’s three-largest consumer credit reporting bureaus, and a big part of what it does is maintain records on consumers that businesses can use to learn how risky it might be to loan someone money or to extend them new lines of credit. On the flip side, Equifax is somewhat answerable to those consumers, who have a legal right to dispute any information in their credit report which may be inaccurate.
Earlier today, this author was contacted by Alex Holden, founder of Milwaukee, Wisc.-based Hold Security LLC. Holden’s team of nearly 30 employees includes two native Argentinians who spent some time examining Equifax’s South American operations online after the company disclosed the breach involving its business units in North America.
It took almost no time for them to discover that an online portal designed to let Equifax employees in Argentina manage credit report disputes from consumers in that country was wide open, protected by perhaps the most easy-to-guess password combination ever: “admin/admin.”
We’ll speak about this Equifax Argentina employee portal — known as Veraz or “truthful” in Spanish — in the past tense because the credit bureau took the whole thing offline shortly after being contacted by KrebsOnSecurity this afternoon. The specific Veraz application being described in this post was dubbed Ayuda or “help” in Spanish on internal documentation.
Once inside the portal, the researchers found they could view the names of more than 100 Equifax employees in Argentina, as well as their employee ID and email address. The “list of users” page also featured a clickable button that anyone authenticated with the “admin/admin” username and password could use to add, modify or delete user accounts on the system. A search on “Equifax Veraz” at Linkedin indicates the unit currently has approximately 111 employees in Argentina.
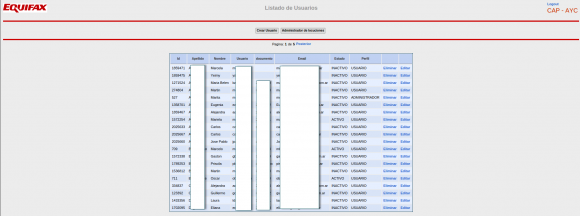
A partial list of active and inactive Equifax employees in Argentina. This page also let anyone add or remove users at will, or modify existing user accounts.
Each employee record included a company username in plain text, and a corresponding password that was obfuscated by a series of dots.
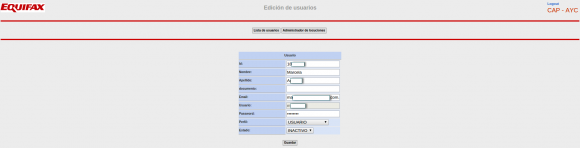
The “edit users” page obscured the Veraz employee’s password, but the same password was exposed by sloppy coding on the Web page.
However, all one needed to do in order to view said password was to right-click on the employee’s profile page and select “view source,” a function that displays the raw HTML code which makes up the Web site. Buried in that HTML code was the employee’s password in plain text.
A review of those accounts shows all employee passwords were the same as each user’s username. Worse still, each employee’s username appears to be nothing more than their last name, or a combination of their first initial and last name. In other words, if you knew an Equifax Argentina employee’s last name, you also could work out their password for this credit dispute portal quite easily.
But wait, it gets worse. From the main page of the Equifax.com.ar employee portal was a listing of some 715 pages worth of complaints and disputes filed by Argentinians who had at one point over the past decade contacted Equifax via fax, phone or email to dispute issues with their credit reports. The site also lists each person’s DNI — the Argentinian equivalent of the Social Security number — again, in plain text. All told, this section of the employee portal included more than 14,000 such records.
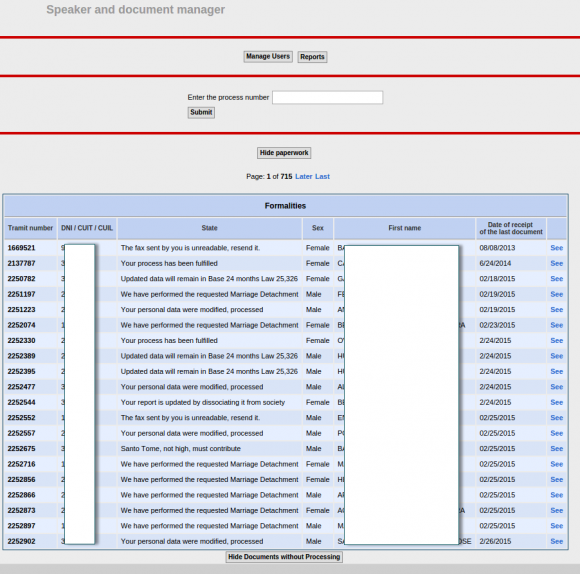
750 pages worth of consumer complaints — more than 14,000 in all — complete with the Argentinian equivalent of the SSN (the DNI) in plain text. This page was auto-translated by Google Chrome into English.
Jorge Speranza, manager of information technology at Hold Security, was born in Argentina and lived there for 40 years before moving to the United States. Speranza said he was aghast at seeing the personal data of so many Argentinians protected by virtually non-existent security.
Speranza explained that — unlike the United States — Argentina is traditionally a cash-based society that only recently saw citizens gaining access to credit.
“People there have put a lot of effort into getting a loan, and for them to have a situation like this would be a disaster,” he said. “In a country that has gone through so much — where there once was no credit, no mortgages or whatever — and now having the ability to get loans and lines of credit, this is potentially very damaging.”
Shortly after receiving details about this epic security weakness from Hold Security, I reached out to Equifax and soon after heard from a Washington, D.C.-based law firm that represents the credit bureau.
I briefly described what I’d been shown by Hold Security, and attorneys for Equifax said they’d get back to me after they validated the claims. They later confirmed that the Veraz portal was disabled and that Equifax is investigating how this may have happened. Here’s hoping it will stay offline until it is fortified with even the most basic of security protections.
According to Equifax’s own literature, the company has operations and consumer “customers” in several other South American nations, including Brazil, Chile, Ecuador, Paraguay, Peru and Uruguay. It is unclear whether the complete lack of security at Equifax’s Veraz unit in Argentina was indicative of a larger problem for the company’s online employee portals across the region, but it’s difficult to imagine they could be any worse.
“To me, this is just negligence,” Holden said. “In this case, their approach to security was just abysmal, and it’s hard to believe the rest of their operations are much better.”
I don’t have much advice for Argentinians whose data may have been exposed by sloppy security at Equifax. But I have urged my fellow Americans to assume their SSN and other personal data was compromised in the breach and to act accordingly. On Monday, KrebsOnSecurity published a Q&A about the breach, which includes all the information you need to know about this incident, as well as detailed advice for how to protect your credit file from identity thieves.
[Author’s note: I am listed as an adviser to Hold Security on the company’s Web site. However this is not a role for which I have been compensated in any way now or in the past.]




Let’s hope that all the Equifax problems lead to a takeover by some other company that is security/customer oriented.
Thanks again, Brian!
Regards,
That’s part of the problem – Equifax is customer oriented. We are NOT their customers.
This is a real problem, even for their real customers, though. How can you trust the data of company with so little security?
There are two issues I see that could hurt a potential customer.
Someone wants a loan. I check Equifax, and get a good score.
1. But, how do I know that no one has actually messed with the data to make the score better?
2. . How do I know that the person who is asking for the loan is actually the person that Equifaxc has scored?
Hope is a silly solution and hoping for a buyout reveals the root cause of why these things happen: this is a SYSTEMIC problem that can only be resolved by regulation and that requires collective action by the public to push corrupt politicians to do it, or their replacement.
Americans MUST internalize that expecting the “free market” to prevent what are THEIR problems will never happen in the current system. Hope and pray won’t do it. Free corporate markets IS what causes these problems.
Equifax is already regulated by Sarbanes Oxley as a publicly traded company what they aren’t is compliant with the regulation so I don’t think MORE regulation is the answer just compliancy.
Sarbanes-Oxley has nothing to do with security.
Sarbox regulates corporate behavior vis-a-vis investors.
We are neither Equifax’s investors or customers.
WE ARE THE PRODUCT. We are what they sell. No more, no less.
Sarbanes Oxley relates to the financial statements of the public company and while some Information Security controls may be reviewed as part of their audit and disclosures, it doesn’t specifically consider data privacy. It’s possible that application is not deemed in scope for their SEC filings and PCAOB audit if it is solely for tracking and investigating disputes.
SOX compliance doesn’t mean a damn thing in terms of actual security, its more around potential fraud reduction measures if anything.
And these businesses absolutely require additional regulation if we’re to trust them with so much of our data.
Hey look, another libertarian with an opinion despite having no clue as to how things actually work. #shocker
Sarbanes Oxley would not protect against sloppy web design used to interact with their customer database. Sarbanes is only looking at the accounting systems. Americans need to start thinking seriously about personal data privacy first and then only then will they think seriously think about protecting it.
It’s PCI compliance that would be the governing body that would have any teeth related to security. Being that Equifax takes credit cards as tender they would be mandated by the credit card companies to be PCI compliant which would involve a yearly assessment by a recognized security organization. This involves, but is no not limited to, external web penetration tests performed by the third party security company. I’m shocked that such sloppy web coding and such was not discovered assuming pen testing was performed.
> Americans MUST internalize that expecting the “free
> market” to prevent what are THEIR problems will never
> happen in the current system. Hope and pray won’t do it.
> Free corporate markets IS what causes these problems.
Well, to be fair a “free market” is a nice tool overall.
However it basically works by “trial and error” (similar to evolution). Whenever “trial and error” is not an option (e.g. irreversible damage) or intermediate periods (maybe 10-30 years) of “bad results” are considered unacceptable then the free market is not the right tool for that kind of problem…
+1
“Let’s hope that all the Equifax problems lead to a takeover by some other company that is security/customer oriented.”
Care to name one??
Google?
They already know everything about us
Its not the breach that kills you. It is the perception to how you responded that does. As someone who developed many of the breach response products and practices at TransUnion, no to mention testified in hundreds of lawsuits, I know too well what could have been done and so should have Equifax.
I suggest this is the worst breach in US history when you combine the numbers and what was compromised. Apparently Equifax didn’t see it that way. The response they rolled out was severely inadequate and poorly thought through.
Didn’t anyone learn from the Target breach? People won’t take crap as a solution. In the end you relent and offer more but it is too late. Lets list some of the concessions Equifax has already made:
1) No longer require a credit card at enrollment for free credit monitoring
2) Removed arbitration language
3) Offered 30 days of free file freeze enrollments
A smart company, and one who waited 5 weeks to notify the public, should have thought this out better. And why only 30 days on the file freeze fee waiver? They are going to have to extend that. So why not do the right thing and waive it for anyone claiming to be impacted by the breach.
Its not the breach that kills you. It’s the lack of encryption.
The breach should be expected. It’s a web portal, connected to the entire world. At minimum, it’s hackable by military grade hackers. Enigma was broken. A web portal is a toy in comparison.
The lack of encryption, even for certain fields, is inexplicable. Column level encryption is not new and a DBA who can’t manage that feature shouldn’t be let near a database.
best comment so far.
Encryption likely wouldn’t have helped in situations like this. Employees need to be able to access the data, which means at some point it needs to be decrypted anyway. In this case a system was accessed using valid user accounts, so even assuming the data was encrypted on the back end it has to be decrypted by the application which is used to view it.
For all we know the data in this instance could have been stored encrypted in the database and then decrypted by the web application, which would have saved them in the scenario of someone compromising or stealing the database server… But does nothing against an attacker who is able to log in via the same route a normal employee would use, and nothing against an attacker who compromises the web server (where the decryption keys are kept).
Steve,
I’m in the process of putting a freeze on my files with all three credit bureaus, but was wondering if you could tell me the advantage/disadvantage to the “Credit Lock” vs. a “Credit Freeze”. TransUnion seems to be the only bureau to offer the “lock” option. It looks more convenient than the freeze, but are there any privacy/security downsides to taking the “lock” option?
Thanks.
This is one of the questions I addressed in Monday’s Q&A on the breach
https://krebsonsecurity.com/2017/09/the-equifax-breach-what-you-should-know/
This is on an entirely different order than the Target breach.
Target’s IT security was probably better than average for a large retailer, they caught the problem internally, before the banks told them they had suspicions. Target was very quick to talk about the issue and I think their response was appropriate. (Lowes got hit around the same time, the banks told them repeatedly that they thought there was a problem, then the banks finally went to the public.)
This also was not the center of Target’s business and the credit card payment system has been reformed so that (if you have a chip card) the retailer does not get sensitive information they do not need.
In the case of Equifax, this information is their only business and letting it be stolen is not something secondary to the business, but is primary to it.
It is also different from other screw-ups, say like the 2008 crash, because if you don’t like what B of A or Citi did you can do business with another bank. I did not choose for Equifax to maintain my credit rating, and to maintain the security of my information. The mechanisms of the market do not exist to give them discipline (if I do not like Target, I can shop somewhere else)
I think at the very least the CEO has to go, but it is hard for me to see how Equifax can continue as a going concern considering that the damage done by this breach to consumers, banks, the U.S. Government (Equifax leaked enough to file fake tax returns!) is more than the value of the company.
Interesting that you wrote that you do not have a choice in which credit agency holds your data.
As consumers and private citizen do we have a ‘votes’ in which agency holds our personal and credit information?
How do I select TransUnion, Equifax, …? How can we opt out?
Sadly, you don’t get a choice. All major banks in this country are legally obligated to provide your identifying data to all three credit reporting bureaus, so that means that Equifax, Experian, and TransUnion all have your information like it or not.
Tangentially this also touches upon another group severely impacted by that breach – the banks themselves. In every other circumstance where they work with an outside company (i.e. a consulting firm) a bank will often have it’s own IT department investigate the security measures of another company to ensure they’re not sending their customers’ data to something so horrifically unsecured. If things look bad, IT simply won’t let the company advance with their business dealings.
However, even if they really didn’t want to they still are legally obligated to send your data to these credit reporting bureaus. This data breach doesn’t just impact the trust in Equifax but also the trust between customers and their banks. I’m sure a lot of legal departments have their agendas set out for them already, and if it turns out Equifax deliberately misrepresented their security situation to these banks (which is more or less fraud) then we could be nearing the point where we have only two major credit reporting bureaus.
> All major banks in this country are legally obligated to provide your identifying data to all three credit reporting bureaus
Are they really legally obligated? I was under the impression that they reported information on customers if and when they chose, and to the bureaus of their choice.
Perhaps laws have changed, but at one point the three bureaus had drastically different views of me, as the banks I dealt with didn’t all report to all of the bureaus.
Steve, Intersting comment, since it is one of the few that addresses response handling as a detriment to the company, without defend their shabby response.
In this particular situation, the handling has been terrible. As if there was no yardstick or previous example of what not to do.
The Equifax response in itself eveidences a corporate culture that has zero regard for the persons affected (aka the product).
However, even as a 13 year old working in a fruit and veg shop, I understood that abusing our core product was bad thing. No-one buys bruised apples.
Equifax, along with Experian, and your former employer, all too often believe that they are beyond reproach when it comes to abusing their product.
With regard to your comment about this being the worst breach in US History, not only do I concur, but I appreciate the vernacular. Calling something a hack denegrates what happend to triviality. This is a security breach. It should never have happened.
Most of the remedial advise published on various web sites, supposedly for the benefit of actual persons, is wholly inadequate, and does not begin to address some of the other issues which this situation raises.
This particular breach will cause issues for the next 20 years. The only effective remedy at this time is a freeze – with all five agencies.
The three big ones charge a fee. Equifax need to pick up that tab for the next two decades, or until such time as credit freeze request in exchange for money is fully recognized as blackmail.
I have posted my own advisory in pdf format on one of my web sites, purely for the benefit of my clients, family, and friends.
In this, I discuss the likely revenue windfall that 240 million credit freeze requests will generate for each CRA ($2.4 Billion per CRA) and I demand to know how this is not blackmail or at least coercive.
Note that DNIs, unlike social security numbers, are not considered confidential, and are available in many public records.
This doesn’t change much about the breach, but you shouldn’t consider them as sensitive or confidential as SSNs are sometimes treated.
That doesn’t mean a criminal can’t do harm with the data?
Given how often we need to give out SSNs in the USA, I’m not sure why they’re considered confidential either.
originally the SSN’s use was limited to a very specific set of circumstances and there were rules against requesting it elsewhere.
Those have been watered down in various ways.
At this point, it would be better to assume that an SSN is public information.
The Argentinian government does not consider the DNI confidential information? A little surprising but not unprecedented. AFAIK, Puerto Rico does not consider the US SSN confidential information. At least when I scraped a PR property tax website (my employers does tax impounds) the download included a few thousand SSNs used as loan numbers.
Brian: Awesome work! Question: How can a person join an active class-action lawsuit against Equifax to get cash reimbursement? OR: Since you’re the lead on this story, can you set up a website for people to sign up for a class-action lawsuit?
On the legislative side, can you point us to a federal website to register our anger with Equifax to have the U.S. Congress immediately enact harsh civil AND criminal penalties and monetary damages on credit agencies, data brokers, financial institutions, insurers, hospitals, universities, websites and ALL organizations that fail to protect consumer information they possess? Something WAY harsher than the E.U.’s GDPR. More like a Sarbanes-Oxley for possessors of consumer/patient/student/account-holder data with plenty of orange jump-suits ready-for-wear!
Please put your answers here and in your newsletter so the widest audience will read it.
Class action law suit:
http://olsendaines.com/
http://olsendaines.com/equifax-security-breach/
Have mercy. This isn’t the first I’ve heard similar in similar circumstances, but no, I don’t have concrete examples to back up that observation.
HOW in the world can that happen this many days after they’ve already found their system lacking so badly?
HOW is it that, on Day One after intrusion detection, they didn’t run down some surely existing, baby newbie newcomer online security checklist?
For YEARS, it’s been screamed from the rooftops ad nauseam that you just don’t use your moniker (user name) as your password. That’s even worse than your birthday or mother’s maiden name that scammers have to at least do some research to obtain before using.
I’m *smacking MY head* this time… but if this happens again in their case, it probably wouldn’t hurt for them to take the proactive step of…. ducking. This is a security TRUST failure issue that continues to escalate beyond rational comprehension right now.
Wandering off now wondering…. Just how old were all those directly involved in this? Age *does* play a part in things…. sometimes. It’s never an excuse, it just does. Sometimes.
Before stressing hope of utter failure of this publicly traded firm, (sued into oblivion, etc.), y’all may want to take a peek into your individual retirement portfolios…. i.e. [site:yourretirementacctfirm.dom disclosure equifax]…
Many could learn that your firms funds own a sliver or three…
And besides the obvious lack of due diligence regarding South America, possibly US based too, this is a simple reminder that the US is the world leader and thus the biggest target.
We’re still fighting an all out Cyber War with various tools I refer to as never ending complex ‘Control Storm’.
Beyond the obvious, these can happen to anyone and everyone, even those who spent the moon on security.
Reminder to heed and come up with methods to outsmart principles of a common used phrase: All it takes is one bad x (apple / actor / executive / link / employee)….
If all 143 million people sign up to have their credit report frozen Equihax stands to make $1.4 billion. Plus the ongoing $10 charge to thaw your report every time you open a credit card, buy a car or purchase a home.
These guys were brilliant!
The charge is now being waived for Experian and Equifax.
Now Experian’s freeze page is now in a constant loading. Before it would just say, “unable to complete your request.” They now want you to stuff all of your sensitive info into an envelope and send it to them! Will it ever end?
Even worse … I went to Equifax web page, started the account freeze process yesterday and after submitting all required data, received the message that the request can not be fulfilled at this time … “try again later …” I tried about five minutes later, submitted all information again and this time the page opens, offering three options to unfreeze the account … obviously, they froze my account the first time but never provided the PIN number which I would now need to unfreeze it. Ugh! … I just hope they go out of business once the investigation is completed … no takeovers or mergers – just shut them down!
I think the level of threat posed to record holders of vast reserves of personal identifiers is proportional to the demand for personal identifiers to do unlawful things.
There are two points of vulnerability.
First today’s vast reserves of electronically retained personal identifiers make the hacking efforts worthwhile. When security fails, it fails huge.
Secondly, misfeasors purchasing these stolen personal identifiers to commit a wide variety unlawful acts do not feel a high certainty of getting act before the risk is offset by the gains. This where efforts to turn the tide on this problem falls down the most.
I suspect we will be talking about this for quite some time.
Well done Alex! Keep up the great work.
It shows that not patching was more than a simple mistake, it shows a culture of lax security and a complete lack of real auditing within their company. Any third party audit would have quickly found this issue. For a company who’s whole business model is PII to have such a lax attitude on security is truly negligent!
SSN is supposed to be for official Social Security Business.
Why are phone companies allowed to use it as a national
identity? Medical sites I can understand … it’s linked to MediCare. Financial institutions have an obligation to report transactions to the IRS.
One solution to this is for the Federal Government to permit citizens to request new Social Security Numbers. It sure would flush out all the inappropriate places this number is used.
When I was alerted by the IRS that someone was trying to file for a refund, the IRS gave me a special PIN for my tax return. They change it every year.
They are just flipping idiots
I sincerely hope these scumbags get hacked into oblivion. Under the Argentinian law, your credit record is protected personal information. However, these Equifax criminals have managed to bend the local law and they centralize all the credit/debt information about every single Argentinian citizen. What’s even worse, they consider your credit/debt information their propriety, and you have to PAY them to learn what they know about you.
People must realize that the responsibility does NOT lie with the CBs, but with the political system that gave them free rein to do this. That’s where the pressure should be applied.
Jailing a couple of low scapegoats and grilling CEOs is just a distraction from the system’s responsibility for what happened.
Guess they never heard of NESSUS or HP WebInspect? Even a junior level “security expert” should be able to run those. But I guess they have to actually hire someone first.
I bet Equifax didn’t even realize that their “internal” website was accessible via public Internet. Probably was running on someone’s laptop.
That in itself should have been gross negligence. But it is not, because we are not their customers, they are not mandated to care about what happens to us, so why should they hire anybody?
All those who delude themselves that this “will bring them down”, or get them to jail are in for a shock. Once you made the system so dependent on them, taking them down will have serious consequences for the entire system. Nothing will happen.
Hi Brian, just to let you know that Argentina’s DNI are not supposed to be secret like US’ SSN. But apart from that, the security practices of Equifax/Veraz (or the lack of) leave me speechless.
Finding the employee data I thought might be a honeypot ( an area designed to trap malicious users) but when you got to the disputes this was just a basic mess up!
It would be poetic justice if the executives of Equifax all had their identities stolen and abused.
Maybe then they would learn why keeping PII secure is not just “a good idea” but the core business that they’re in. These people make Martin Shkreli look like a saint.
You can rest assured that they made sure THEIR info as well as their families were not in the database. I am willing to bet on it.
Ok so let me get this straight. One year for free credit monitoring, when all my personal information required to take out any type of loan in my name is now PERMANENTLY in the hands of hackers and will probably eventually be posted on the Internet. This screws us for life and they want to get away with a temporary solution.
We should DEMAND free lifetime monitoring for anyone who had some level of information stolen/leaked, at minimum.
What a fuck up. I bet my information are in there as I have used their services before.
Attempting access to the Equifax credit freeze tonight (1:30 a.m. ET), one gets the failure message:
“SRVE0255E: A WebGroup/Virtual Host to handle /Freeze/jsp/SFF_PersonalIDInfo.jsp has not been defined.
SRVE0255E: A WebGroup/Virtual Host to handle http://www.freeze.equifax.com:443 has not been defined.
IBM WebSphere Application Server”
Great. Just great. Good job guys.
And the hackers thank you for disclosing the server app being (not) used.
More best practices here.
I would think IBM would want to revoke its software license for mismanagement and damage of its reputation.
Isn’t it time to give up the idea that the SSN can be used as a secret password? Isn’t that really just hopeless?
Sadly, offshore outsourcing has been a security and privacy problem for a long time. I explored the problem in a 4-part series way back in 2008:
Is It Wise For Credit Bureaus To Outsource To Foreign Call Center Firms? (Part 4)
http://ivebeenmugged.typepad.com/my_weblog/2008/05/is-it-wise-fo-3.html
Do you want your sensitive personal data traveling around the globe? I think not, but it does.
Maybe the massive cluster f–k that is the Experian data breach will motivate consumers and politicians to demand better data security in the credit reporting industry.
Burn them to the ground.
Such poor security, so many possible options for an attacker… a competitor just corrupting the data and allowing the corruption to seep into the backups effectively damages the business value of Equifax. Opsec was likely poor, so the 143e6 records probably have all sorts of interesting out of band information not directly related to credit worthiness such as deliberately modified records or de novo records (witness protection program entries? flags for government warrant information requests?)
There is probably a way for the black data bases– you know, the ones that never erase any data good, bad, incorrect, underage, or ancient– to take advantage of the records. Yes many companies make use of the black databases, and they rarely admit doing so.
OPM may be worse nationally, although on the upside with OPM the thief was likely a nation state and unlikely to do more than corrupt a few government officials.
Their IT head is listed on LinkedIn as a musician.
Just got off the phone with Equifax Canada. It took multiple tries to actually find a live person. They “assured” me that no Canadian consumer data was included in the breach and so not to worry. I’m sceptical.
Interestingly enough the CSR said that the ability to security freeze your account is NOT available in Canada. Isn’t this just lovely.
So I tried Transunion Canada. After 15 minutes in the IVR hell, I still can’t find a way to talk to a person.
Hmmm. Overall a very disappointing experience.
No, I did not consent for Equifax or other to manage my PII. No known remedy exists. We cannot expect anything better from a defunct vortex of unfortunately, too common mishandling of sensitive data.
So, it seems there are two separate Equifax incidents – 143 million ID’s stolen and the compromise of the Argentinian Credit Dispute Web Portal. Is there anything else?
I need to opt out of Equifax.