Tag Archives: Equifax
Experian, You Have Some Explaining to Do
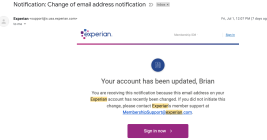
Twice in the past month KrebsOnSecurity has heard from readers who’ve had their accounts at big-three credit bureau Experian hacked and updated with a new email address that wasn’t theirs. In both cases the readers used password managers to select strong, unique passwords for their Experian accounts. Research suggests identity thieves were able to hijack the accounts simply by signing up for new accounts at Experian using the victim’s personal information and a different email address.
IRS Will Soon Require Selfies for Online Access
If you created an online account to manage your tax records with the U.S. Internal Revenue Service (IRS), those login credentials will cease to work later this year. The agency says that by the summer of 2022, the only way to log in to irs.gov will be through ID.me, an online identity verification service that requires applicants to submit copies of bills and identity documents, as well as a live video feed of their faces via a mobile device.
Intuit to Share Payroll Data from 1.4M Small Businesses With Equifax
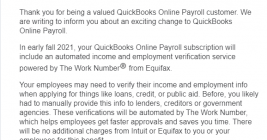
Financial services giant Intuit this week informed 1.4 million small businesses using its QuickBooks Online Payroll and Intuit Online Payroll products that their payroll information will be shared with big-three consumer credit bureau Equifax starting later this year unless customers opt out by the end of this month.
Intuit says the change is tied to an “exciting” and “free” new service that will let millions of small business employees get easy access to employment and income verification services when they wish to apply for a loan or line of credit.
Fintech Startup Offers $500 for Payroll Passwords
How much is your payroll data worth? Probably a lot more than you think. One financial startup that’s targeting the gig worker market is offering up to $500 to anyone willing to hand over the payroll account username and password given to them by their employer, plus a regular payment for each month afterwards in which those credentials still work.
Experian’s Credit Freeze Security is Still a Joke
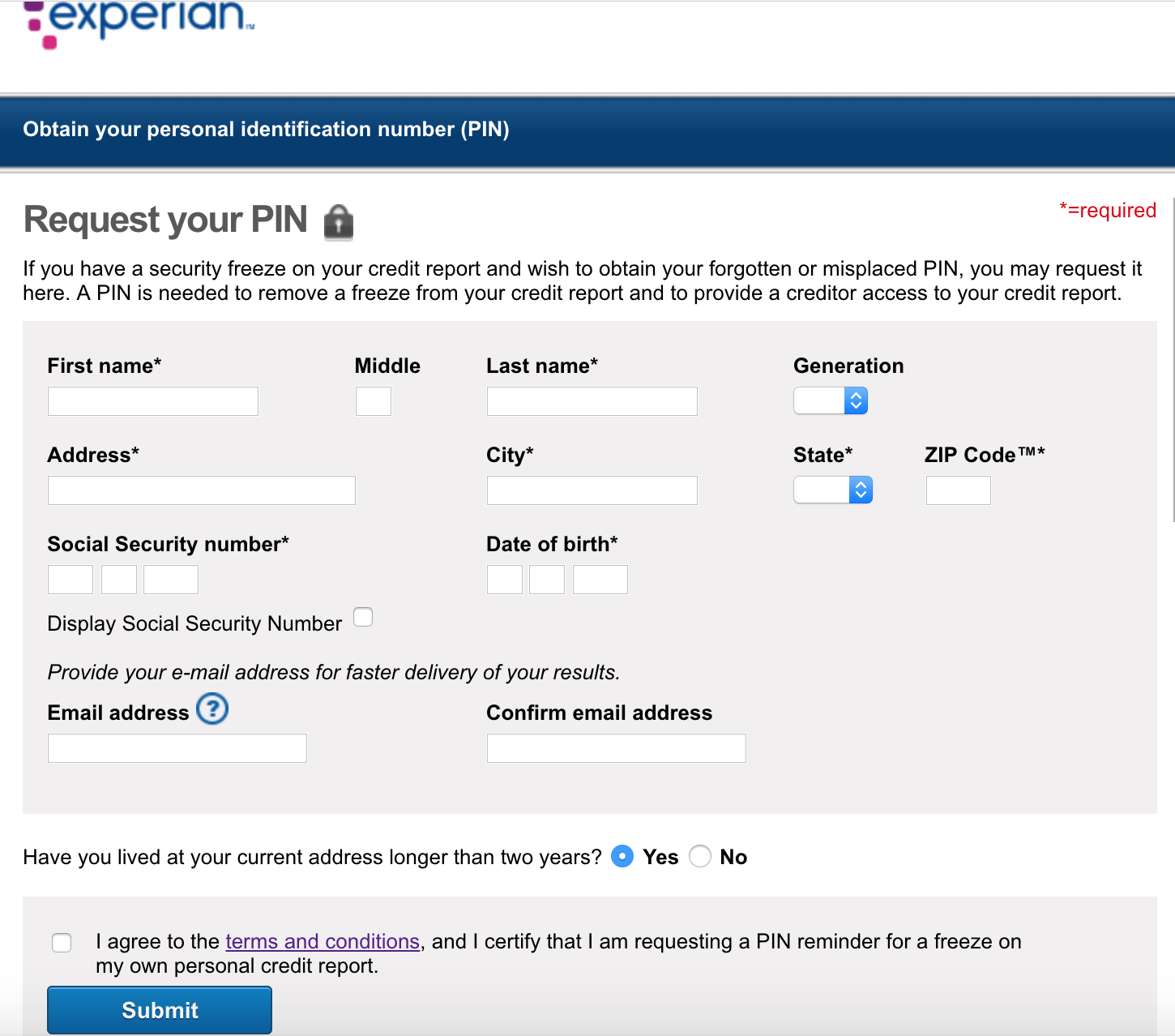
In 2017, KrebsOnSecurity showed how easy it is for identity thieves to undo a consumer’s request to freeze their credit file at Experian, one of the big three consumer credit bureaus in the United States. Last week, KrebsOnSecurity heard from a reader who had his freeze thawed without authorization through Experian’s website, and it reminded me of how truly broken authentication and security remains in the credit bureau space.
Why & Where You Should Plant Your Flag
Credit Freezes are Free: Let the Ice Age Begin
It is now free in every U.S. state to freeze and unfreeze your credit file and that of your dependents, a process that blocks identity thieves and others from looking at private details in your consumer credit history. If you’ve been holding out because you’re not particularly worried about ID theft, here’s another reason to reconsider: The credit bureaus profit from selling copies of your file to others, so freezing your file also lets you deny these dinosaurs a valuable revenue stream.
In a Few Days, Credit Freezes Will Be Fee-Free
Later this month, all of the three major consumer credit bureaus will be required to offer free credit freezes to all Americans and their dependents. Maybe you’ve been holding off freezing your credit file because your home state currently charges a fee for placing or thawing a credit freeze, or because you believe it’s just not worth the hassle. If that accurately describes your views on the matter, this post may well change your mind.
Credit Card Issuer TCM Bank Leaked Applicant Data for 16 Months
TCM Bank, a company that helps more than 750 small and community U.S. banks issue credit cards to their account holders, said a Web site misconfiguration exposed the names, addresses, dates of birth and Social Security numbers of thousands of people who applied for cards between early March 2017 and mid-July 2018.
TCM is a subsidiary of Washington, D.C.-based ICBA Bancard Inc., which helps community banks provide a credit card option to their customers using bank-branded cards.