How much is your payroll data worth? Probably a lot more than you think. One financial startup that’s targeting the gig worker market is offering up to $500 to anyone willing to hand over the payroll account username and password given to them by their employer, plus a regular payment for each month afterwards in which those credentials still work.
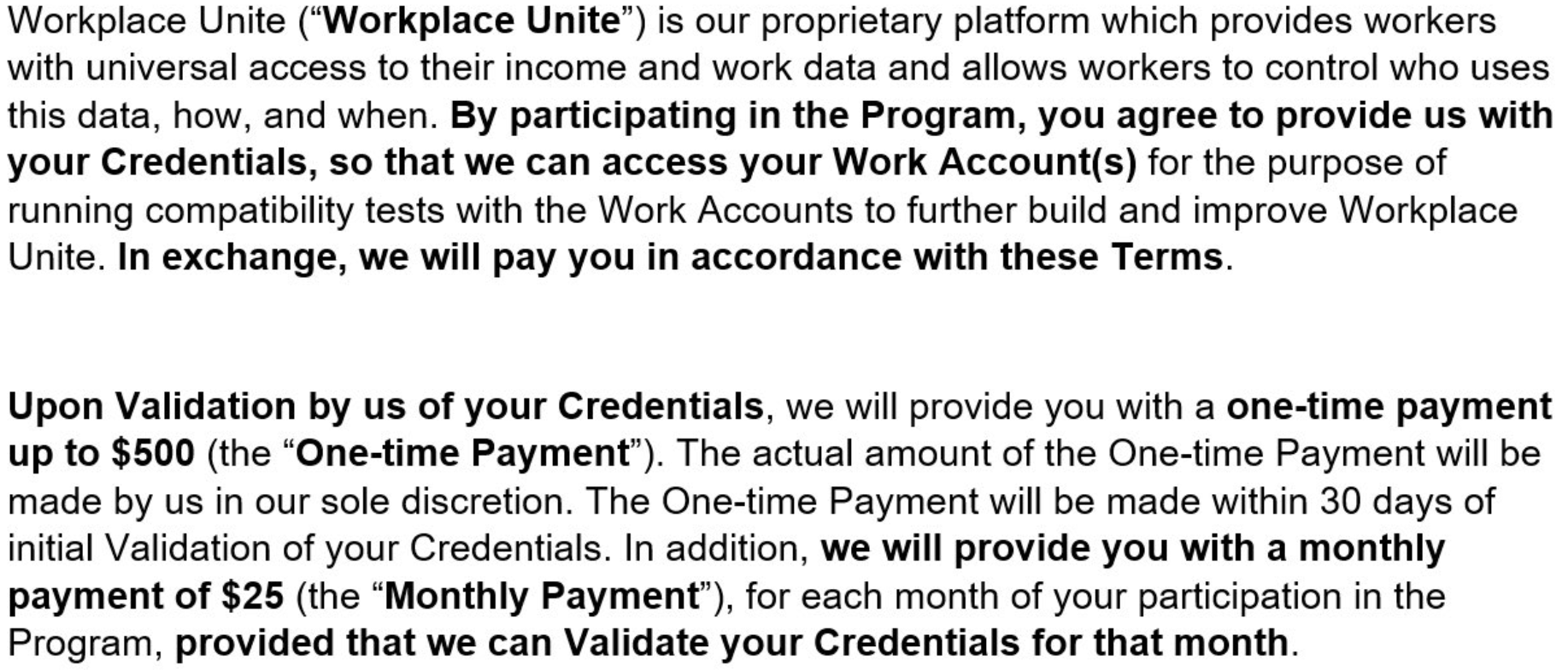
This ad, from workplaceunited[.]com, promised up to $500 for people who provided their payroll passwords, plus $25 a month for each month those credentials kept working.
“Consumers’ access to financial security and upward mobility is dependent on their access to and control over their own employment records and how easily they can share those records with financial institutions,” Argyle explained in a May 3 blog post. “We enable access to a dataset that, for too long, has gone unstandardized, unregulated, and controlled by corporations instead of consumers, contributing to system-wide inequalities.”
In that sense, Argyle is making a play for a discrete chunk of a much larger employment data market dominated by the major credit bureaus, which have been hoovering up and selling access to employment data for years.
The 800-lb. gorilla there is Equifax, whose The Work Number product has for years purchased employment data flows from some of the world’s largest companies (employees consent to this sharing as part of their employment contract, and The Work Number makes it fairly easy for anyone to learn how much you earn).
The Work Number is designed to provide automated employment and income verification for prospective employers, and tens of thousands of companies report employee salary data to it. It also allows anyone whose employer uses the service to provide proof of their income when purchasing a home or applying for a loan.
On its blog, Argyle imagines a world in which companies choose to integrate its application platform interface (API) and share their employee payroll data. At the same time, the company appears to be part of an effort in which non-salaried workers are prompted to repay their erstwhile employers’ trust by selling payroll credentials.
If Argyle is worried these two goals might somehow conflict, that is not obvious by looking at some of its direct-to-consumer efforts.
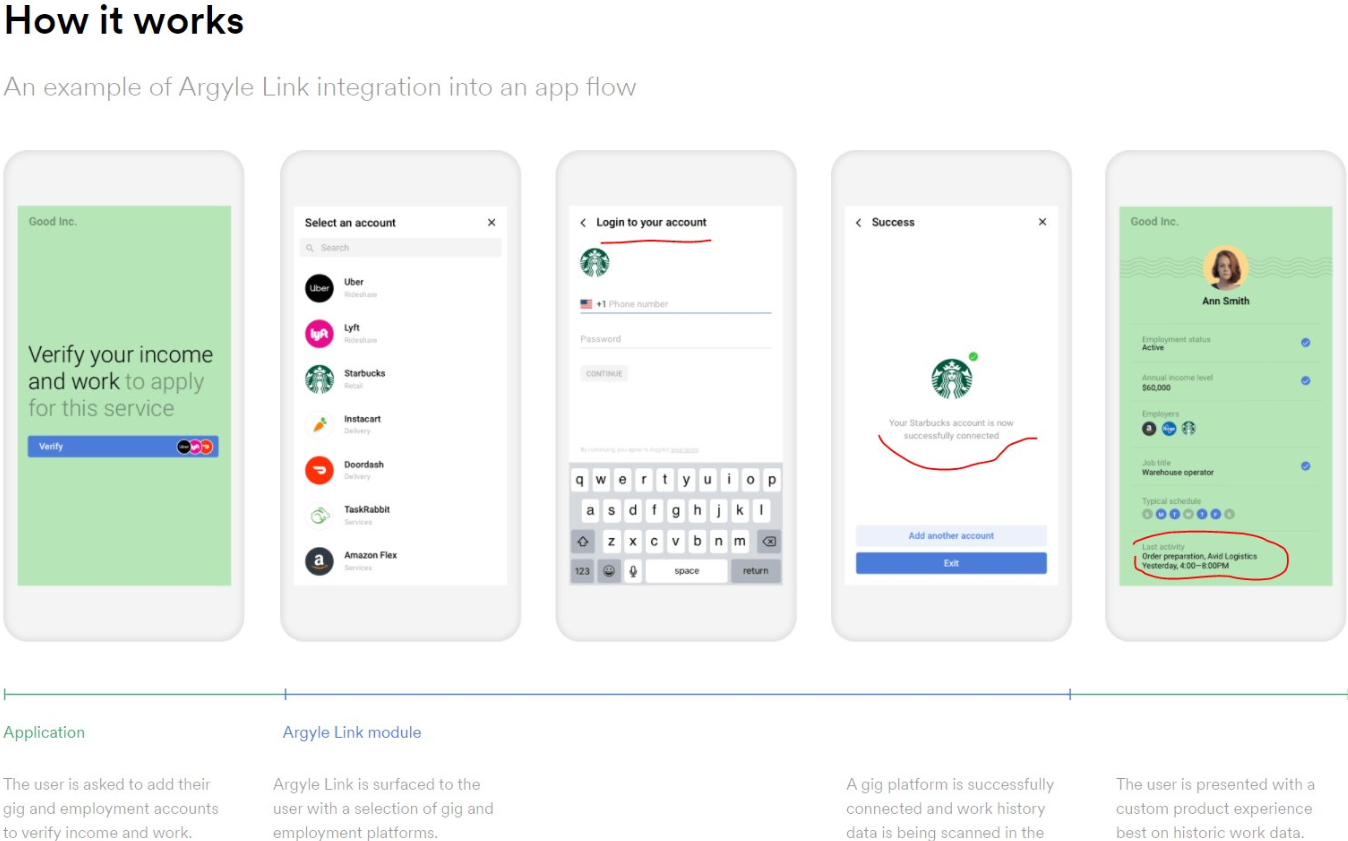
The website pictured below prompts visitors to “connect payroll,” and those who proceed agree to have their payroll data shared with a company called Earnin, a mobile payday loan app that lets users get an advance on their upcoming paycheck.

Clicking “Connect Payroll” brings up a list of payroll login pages for brand name companies, including Walmart, Starbucks, Amazon, Uber, Chipotle, etc., with a search feature that reveals login pages for everyone from the Federal Bureau of Investigation (FBI) to the Federal Reserve and Federal Trade Commission (FTC).

The default Argyle list of payroll login pages for major companies.
Here’s what comes up when you search by “Department of” at this site:
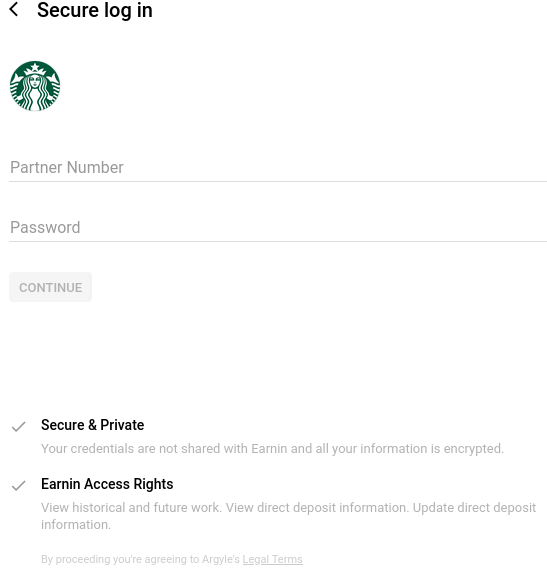
Drilling down into individual companies listed here produces a username and password form that in some cases is modified to request an employee identifier other than a username, such as a employee ID, associate or partner number instead. Here’s the login page for Starbucks employees:
The site pictured above actively checks if any submitted credentials are working, by submitting them directly to the employer in question. This Argyle status page indicates the system’s “data connection status” to countless employers.
Some of you may be thinking, “How many of us actually know or have our payroll passwords?” According to Argyle, plenty of people do.
“At Argyle, we are intimately familiar with how likely someone is to know the password for their employment account or payroll system, because we’ve seen hundreds of thousands of users successfully (and unsuccessfully) provide their credentials,” Argyle’s Billy Mardsen wrote on Apr. 1. “We closely monitor their success rate—what we call conversion—because it drives the performance of the products and applications that our clients build on top of Argyle.”
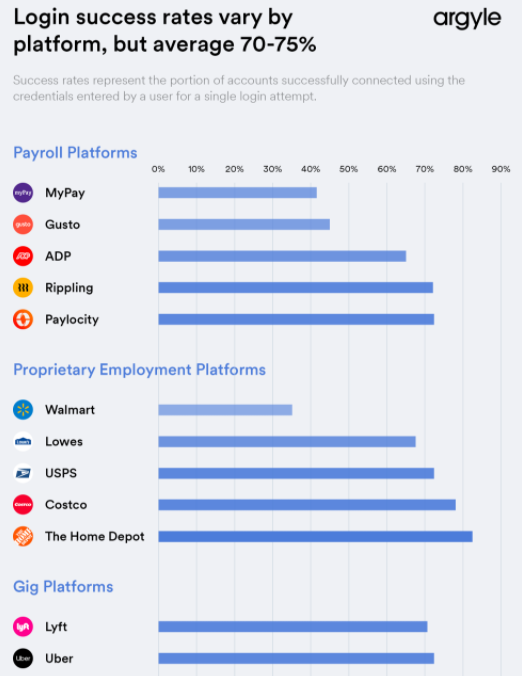
Argyle’s “conversion” numbers by employer. Image: Argyle.com
UNCOMMON GROUNDS
KrebsOnSecurity first heard about this company via Twitter from security researcher Kevin Beaumont, who pointed to a nest of domains associated with Argyle’s API — nearly all of which are offline now. At the time, Beaumont and others digging into this suspected the sites were part of an elaborate phishing scam.
These sites, which seemed to be grouped around a recent recruitment effort variously called “Workers United,” “UniteAtWork,” “WageCompete” and “CommonGrounds,” indicate that Argyle’s platform has been pivotal in a slew of campaigns paying employees at specific companies up to $100 for their payroll account passwords. Here’s one seeking T-Mobile employees:
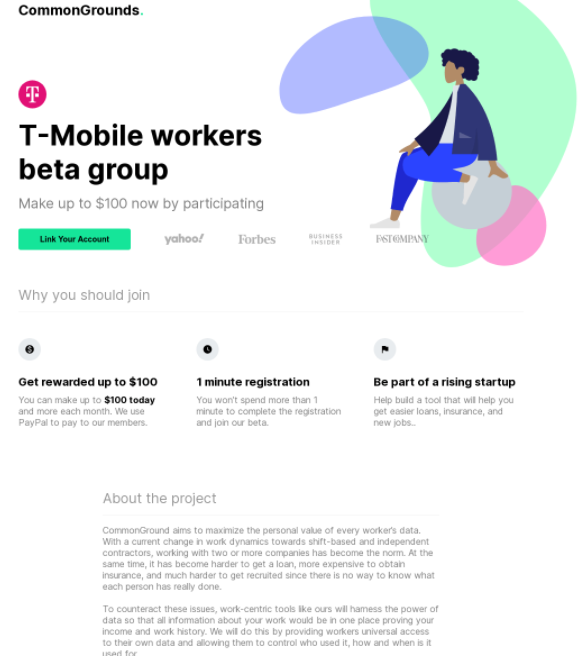
A promotion offering T-Mobile employees $100 to give up their T-Mobile payroll account passwords.
Another recent promotion targeted employees at J.P. Morgan Chase, the largest financial institution in the United States:
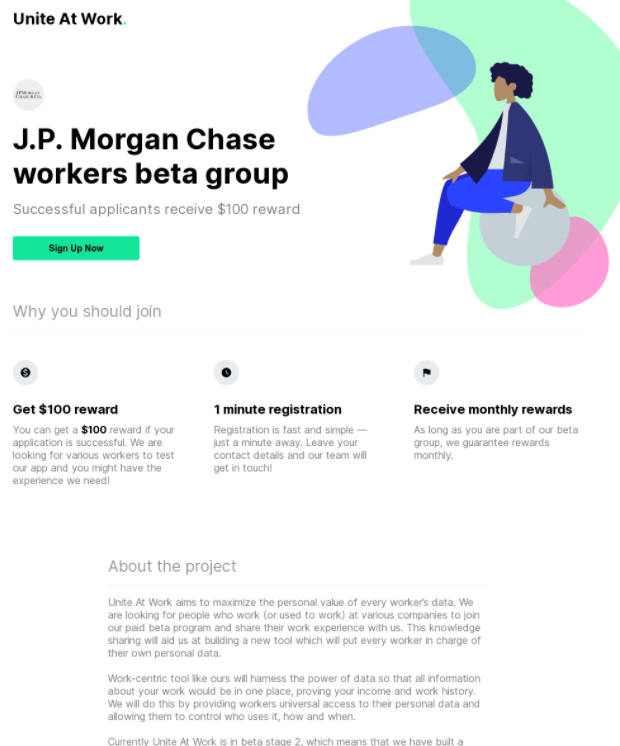
Argyle declined multiple interview requests for this story, so it’s not clear how much of a role — if any — the company may have played in these various sites. But code prebuilds and instructions published in the company’s name on Github strongly suggest Argyle was instrumental in the WageCompete initiative.
Also, this page over at Scopeinc.com says the WageCompete program is provided by Argyle Expert Services.
Here’s a graphical look at the various websites mentioned here and their ties to Argyle’s API (click to enlarge):
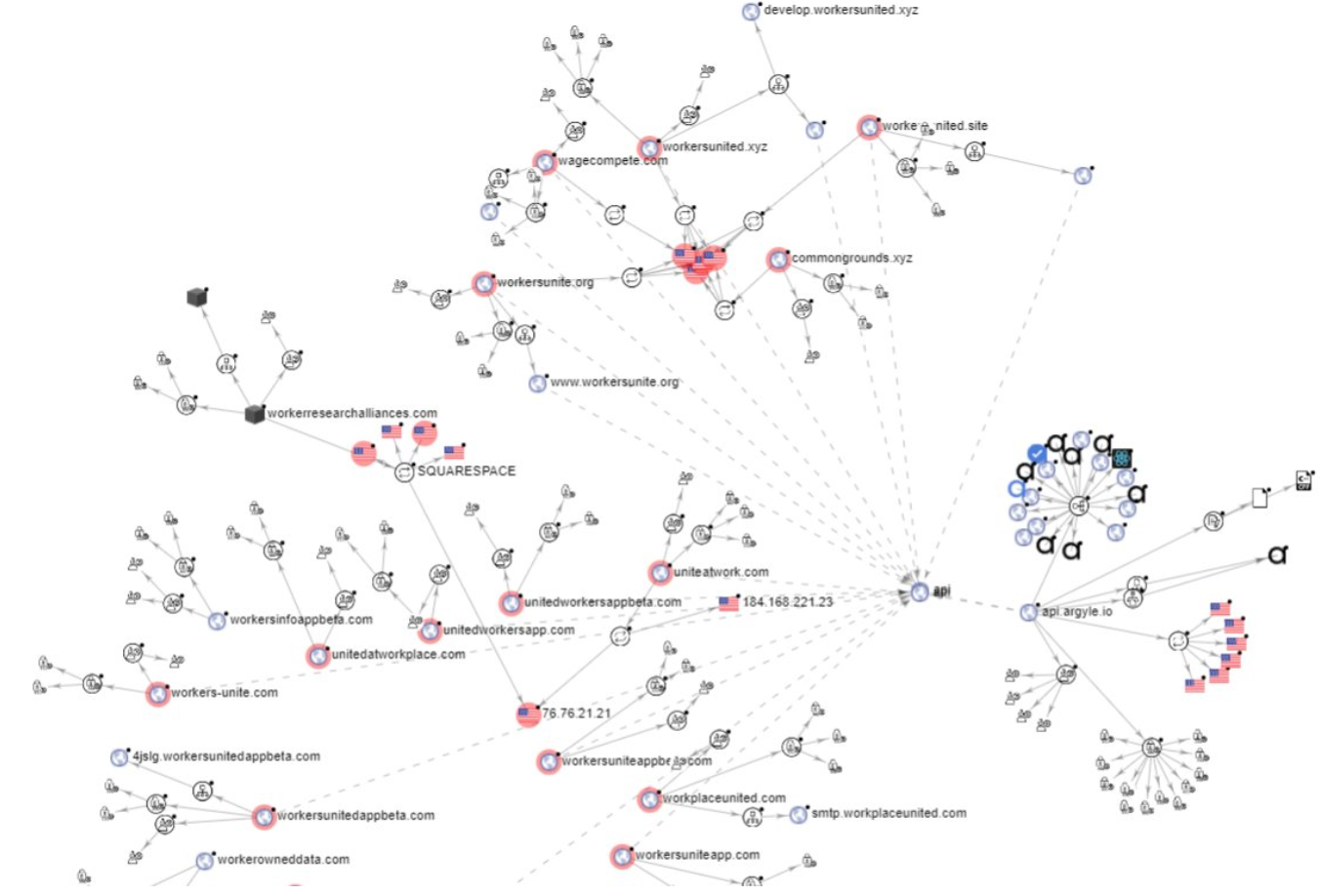
The network of sites paying people for payroll passwords and their connections to Argyle’s API. Click to enlarge. Image: Virustotal
One of the sites in that graphic above that’s connected to Argyle’s API — workerresearchalliances[.]com — is currently live and includes the same verbiage about participants getting paid for their payroll credentials. The terms and conditions of the “WorkersApp beta program” were set by a company called Workers Research Alliances LLC, incorporated in February. The address for Workers Research Alliances is just a few blocks from Argyle’s office in New York City.
‘WE DO THINGS OTHERS DARE NOT DO’
Steve Friedl, an IT consultant in the payroll service bureau industry, said it appears Argyle has been paying people to help them refine their API and data scraping technology.
“They are not paying this money just to be able to sell people services, they are doing so to maintain their screen-scraping software API,” Friedl said. “This is essentially paying employees to help Argyle hack their payroll provider.”
Last fall Argyle announced it had landed a $20 million investment from Bain Capital, among others. The company’s co-founder, Shmulik Fishman, is described as a “disruptor” who says he wants to make credit scores obsolete.
“We’re fearless,” Fishman told Authority Magazine. “We do things other people dare not do.”
That much is clear. Hey, I can get behind almost anything that disintermediates the creaky old credit bureaus in a straightforward and consumer-friendly way. And the last time I checked, it’s not against the law to give someone your password, or to induce someone to do so willingly in exchange for something else (unless maybe you work for a federal agency).
But I wonder how many of the companies listed on all these payroll connect sites will respond to knowing their brands and logos are associated with a site that asks their employees to give away passwords.
KrebsOnSecurity contacted multiple high-level sources at major companies whose login pages are shown in these payroll connect programs running on Argyle’s platform. None of those sources were authorized to talk to the media, but all seemed fairly horrified at what they were seeing, and each said their employer’s legal departments were launching their own investigations.
Beaumont said he’s worried that in some companies, an employee’s payroll credentials may work to gain access to other parts of the organization — meaning some employees may be giving away more than they realize.
“My concern is some companies use single sign-on for payroll,” Beaumont said. “That’s a lot of access for a data harvesting company.”
Update, Aug. 16, 10:47 a.m. ET: Earnin said it had a two-month payroll integration test Earnin with Argyle, but that it terminated that test in December 2020 and that Argyle did the Earnin promotion on its own. “Earnin was not part of this promotion and we never sell customer information – in fact, our agreements with vendors explicitly forbid monetization of user data,” the company said in a written statement.




Is Argyle a play on Plaid ( https://en.wikipedia.org/wiki/Plaid_(company) )? They provide the back end integration and login service for all those personal finance aggregators.
Yes, that is what the company’s founders have said: That they want to be the Plaid or Mint of employment data.
It wouldn’t be worth it to me at any price to do this to my employer. The second you get found out, you would lose your job, potentially have your name blasted all over social media, potentially face criminal charges and risk being blackballed for life to ever work in that industry again.
This happens on a daily basis across tons of platforms. The way SaaS has been engineered is to provide transparent methods for one platform to integrate with the next. If you look at O365 and its out of the box experience it is designed for employees to provide their data to third parties.
Is payroll more sensitive? Maybe, hard to say it depends on the person’s role and access (much like other platforms). Assuming the person only has access to their payroll statements I’m not sure this would be significant, for a payroll employee with more global access this certainly would be a different story.
As far as credentials (again assuming as I’m not about to try this out) it should be fairly safe if standard authentication best practices are followed (e.g. Argyle doesn’t receive the credentials but is getting an auth token).
Maybe I’m looking at this wrong but in most cases I don’t see this as much of an issue (again with a number of assumptions being made on my part).
If it’s anything like banking, they probably intentionally make it hard to integrate since integrations (from a service provider perspective) generally add risk with little upside. On top of which, they reduce vendor lock-in esp if the company is looking to enter the space the integration is in
There’s almost no chance they’re doing properly with any kind of auth token access (which requires cooperation with the payroll entity); I bet a dollar and a donut that they are just doing industrial strength screen scraping and that the payroll people don’t know anything about it.
As evidence, I just got off the phone with one of my customers who is listed on their site, and he knew nothing about it.
Another reason to deploy MFA, especially when SSO is in play.
I read that graph above as Paylocity/Rippling/ADP having MFA enabled on less than 30% of the users who attempt to sign-up. That is CRAZY.
Without purpose built APIs with delegated auth, they are giving over creds that have full access to Direct Deposit and W2 details.
Properly implemented MFA should at least provide a control on this. If nothing else, that would help track login attempts, and provide a way to get alerted and notify users when a prompt does get generated.
Regardless, this is a horrid business model. It’s enticing employees to risk reprimand or outright termination for violating corporate policy. Which business out there does *NOT* have a policy against sharing login credentials?
I’m not sure how MFA helps at all here. In this scenario, an employee decides they want to sell or share their payroll credentials, they do so, and then they approve the 2FA prompt. Argyle says their platform works fine with 10 different types of payroll MFA. They’ll even let you reset your payroll credentials if you don’t remember them:
https://argyle.com/blog/payroll-passwords
Multi-factor authentication and single sign-on
Argyle supports up to 10 different authentication methods depending on what our customers’ platform requires, including SMS and email one-time passcodes, security questions, confirmation SMS and emails (i.e. magic links), and time-based one-time-passcodes (e.g. Google Authenticator). Argyle also supports authentication via single sign on (e.g. Okta, OneID, Microsoft SSO).
Embedded password-reset flows
Some users don’t know their passwords. Argyle makes it easy for these users to reset their passwords directly within Argyle Link.
You can’t make “credit scores obsolete” they are so ingrained into American society that your success in life depends on that three digit numbers to obtain worthiness for financial backing , housing or even employment.
Scary to think another country could purchase employment data on government workers. Imagine if that site was hacked.
Inputting your credentials to a domain ending in .xyz is a good idea, said no one ever.
BTW, the Maltego app (last graph) is the best tool teasing out interesting connections between domains, emails, ip addresses and phone numbers ever, IMHO!
‘WE DO THINGS OTHERS DARE NOT DO’
Consultant: Somebody who borrows your watch and tells you the time and keeps the watch*.
* The watch in this, excuse the expression, case is a Rolex(tm) but good luck buying one anywhere else for $500 bucks, or even getting it cleaned (the database) once a month for a monthly recurring charge of that magnitude since this must be done by an Authorized Service Dealer (an anonymous Fintech Startup). This monthly recurring charge is said to be (DuckDuckGo) to be in the range of $600-$1000 depending on the model (of either the watch or the database).
Put away your Financial Calculator. There are no transcendental functions to solve by iteration. Assume instead that “Real Names” are randomly distributed beginning with either a number (incl. Elon’s kid, Prince, etc.) or a Letter [A-Z]. The average wages have to be reported anyway … U.S. Department of Labor: Fair Labor Standards Act (FLSA) and the “gig economy” can be correlated against national averages for Industry and Geography: https://www.dol.gov/general/topic/statistics/wagesearnings
Let the (Private Sector/gig economy) Games begin. It is rather pointless to be “discovering” the Public Sector database triples (Real Name, User Name, Payroll) because the profile can be simulated (https://www.federalpay.org/gs/2021)
I can easily see people signing up for this, regardless of the money offer. Because, as the “Social Engineering: because there’s no patch for human stupidity” slogan says, people are stupid.
I work in an academic library, a small university branch campus. Last week I was helping a public patron sign on to Gmail and I was shocked to see how many remembered logins there were for Gmail in a browser. He asked me to help him clean his off of the computer, and I told him I’d take care of it. While digging into the computer, I found someone had linked their Gmail to auto-login. Now, this next part is probably obvious to a lot of you, but I only use Gmail for it’s basic email function function, so I’m not familiar with this, plus it’s not my primary email system. This person had also downloaded 20+ web site login passwords onto this public computer’s browser. We’re talking Social Security, Netflix, U.S. Military, VPN. All of these credentials just sitting there for the taking. And the passwords were completely visible by clicking on the little Show icon.
I looked at some of the passwords to see if he was maintaining good password security, and he wasn’t. While he had two or three different passwords, mostly used one password across all accounts. It wasn’t seriously strong, I’m sure a rainbow table would take it down quickly enough.
I can easily see people selling out their employer for “up to $250”.
The worst part was that we only have three public computers right now – normally have six – and the third computer also had someone perma-logged in to Gmail.
*sigh*
I have no faith in humanity. Criminals or non. And the browsers now flush all cookies and cache on close.
Shouldn´t you set up your public PCs to auto-reset to a safe (and password free) state after each patron´s session?
The IT dept should have. They didn’t. I had limited access to what I could do on the public PCs until recently, and I still don’t know what level of access that I have. The IT director was pretty worthless. When I worked for him I found things like Cisco wireless routers with their antennas horizontal. Aside from the fact that I was Cisco certified and an amateur radio operator and explaining to him about antenna propagation patterns, he said “that was how main campus told him it should be” it stayed that way for ages, and half the building had lousy WiFi coverage.
It’s a tricky situation. I can’t do anything on the student computers at all as they’re on a completely isolated network, which makes it impossible for me to check if their printer works. We recently received a bunch of passwords from an IT guy who took an early retirement offer when we were hit with budget cuts, and he said one of them should work. I haven’t had a chance to work with any of them yet.
Ahhh my ADP portal login also contains my direct deposit account info, which can be modified, so if I sell my credentials how long before my paycheck ends up in some overseas bank account?
That’s kicker, Mike, if one is needed!
In fact, one of the captured images (that explains what you are agreeing to…) explicitly states that they can “Update direct deposit information” (it’s under the “Earnin Access Rights” section)!!!!!
Hmm, I’m trying to search the name of my employer and “maximize the personal value of every worker’s data” but not getting any results. Does anyone know if they’ve changed their standard marketing wording?
What could possibly go wrong? thought absolutely no one to whom $500 and $25 a month is a significant incentive.
I currently make $11.75 an hour for 20 hours a week working in a library. My paycheck is around $330 twice a month. If I had no scruples and didn’t know what that offer could lead to, yeah, it could be quite an attractive offer.
Not unlike those work from home offers where you’re just buying gift cards but actually working as a money mule for scammers.
I’d bet one of my paychecks not a single board member or employee is willing to personally sign up.
There are 2 issues with some of the comments:
1) The users are NOT selling out their employers! They are selling their own payroll data – they are not being asked to provide logins to payrol as admin, where other user’s data can be seen, but only their own. In theory this is how it should be. Each of us controls the data and the employers should not be able to sell on our behalf. This is what would disrupt the credit industry.
2) The existing payroll portals do not allow “read only/reporting” access. As pointed above, the login can change the direct deposit, see SSN etc. If we could all create read only logins, we would have more people being comfortable sharing and giving the data to the highest bidder – or nobody, depending on the level of trust.
I would imagine that each company imposes an AUP on its employees. Any AUP that does not require employees to keep passwords/credentials private should be all that is needed to get the creator of said AUP fired. Thus, each employee is subject to being fired (rightly so!) By procuring a breach of the employee’s agreement to the AUP, Argyle is interfering with contracts. While this might not be per se illegal, there are enough names on this list that have well-funded legal teams that I would not want to be responsible for Argyle’s defense or legal bills!
Hard or software tokens would stop this.
Every employer I know of has a policy that basically says if you share your payroll data or any kind of account login information with anyone that’s grounds for immediate dismissal.
I can easily picture scenarios where folks are thinking they don’t have an individual payroll code but rather a link off the internal website using just their network ID and password. There goes corporate security when those folks provide this outfit with their network ID and password. Can we say swing the door wide open to everyone and anyone?
“Up to” means “no more than”. So 1 cent is still “up to 500$”…
If a company doesn’t have these sites IP restricted (can only be accessed by company egress points) then it’s still on the companies (near and or far side) for lax security.
Example; We access XXX.com for processing PII. I could give out my username and password, and unless they are on our network, they aren’t getting access. Options for account lockout and logging.
Sometimes there is a $5 solution to a $50B problem.
What if you use a SAAS provider for payroll? Or want your tens of thousands of Starbucks employees across the world to access their pay cheque without requiring VPN?
Sometimes a $5 solution isn’t feasible.
As much as you might love to IP restrict, you’ll have employees hitting your payroll app pre and post employment. Requiring VPN is really not an option.
Oh my. The article does not nearly go far enough with the possible consequences here. Besides sharing your password being an obvious reason to be fired with cause, you just allude to it in the last sentence: “My concern is some companies use single sign-on for payroll,”.
Now follow this thought a little further. To facilitate monthly updates to the payroll data, Argyle must store the passwords they’ve been given in a reversible format, not a hash. This immediately makes it a prime target for every major hacking group or nation state actor who didn’t know about their existence yet. How many of those passwords will provide SSO access to other systems in those companies, starting with webmail, from which the attacker can then move laterally?
Or look at the financial side – EVERY company would want to buy that user database asap at pretty much any price, so they can lock out the affected accounts before someone else uses them.
Plaid also stores credentials to enable persistent access – yet about 30% of US consumer bank accounts have been accessed via Plaid at some point in time.
getpinwheel, another employment and Income data aggregator. It also allows direct deposit switching across multiple payroll provider. They must be storing credentials as well. So is Plaid and Mint as financial data aggregator.
Forrest Gump: “Stupid is as stupid does”.
Wow, WOW!!!!. People are willingly doing this for up to $500 (or 1 cent as pointed out above)?
Seriously?
Besides all of the comments about how it affects employers and getting blacklisted etc. What’s to stop this company from changing the bank account your pay is deposited in? Notice you get “paid” within 30 days of supplying your credentials, so how many pay cycles can you potentially lose before you notice? 1, 2, 4?
This a known phishing attack method/strategy. Get your payroll credentials and change the bank account.
These people are screwed. Their business model is seriously illegal and now that a bunch of legal departments are involved it’s likely they’ll be sued and/or raided within days.
Former employees have a continuing obligation to protect their former employer’s confidential information. Bribing a former employee to violate that obligation is illegal. In this case, the bribery is designed to allow unauthorized access to confidential payroll data that every one of these companies is going to identify as valuable trade secrets. Bribing former employees in order to steal their former employer’s trade secrets is a criminal offense. Not to mention a slam dunk trade secret TRO in any court in this country.
I’d be surprised if they’re still in business a month from now.
The interesting question is what happens to the people who took the bribes? My guess is their former employers are going to be seriously pissed. And they’re definitely going to find out.
Hmmm…Argyle used the address associated with Workers Research Alliances LLC in their trademark registration:
https://uspto.report/TM/90298832