Tag Archives: Experian
ID Theft Service Resold Access to USInfoSearch Data
It’s Still Easy for Anyone to Become You at Experian
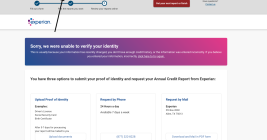
In the summer of 2022, KrebsOnSecurity documented the plight of several readers who had their accounts at big-three consumer credit reporting bureau Experian hijacked after identity thieves simply re-registered the accounts using a different email address. Sixteen months later, Experian clearly has not addressed this gaping lack of security. I know that because my account at Experian was recently hijacked, and the only way I could recover access was by recreating the account.
Experian Glitch Exposing Credit Files Lasted 47 Days
On Dec. 23, 2022, KrebsOnSecurity alerted big-three consumer credit reporting bureau Experian that identity thieves had worked out how to bypass its security and access any consumer’s full credit report — armed with nothing more than a person’s name, address, date of birth, and Social Security number. Experian fixed the glitch, but remained silent about the incident for a month. This week, however, Experian acknowledged that the security failure persisted for nearly seven weeks, between Nov. 9, 2022 and Dec. 26, 2022.
Identity Thieves Bypassed Experian Security to View Credit Reports
Identity thieves have been exploiting a glaring security weakness in the website of Experian, one of the big three consumer credit reporting bureaus. Normally, Experian requires that those seeking a copy of their credit report successfully answer several multiple choice questions about their financial history. But until the end of 2022, Experian’s website allowed anyone to bypass these questions and go straight to the consumer’s report. All that was needed was the person’s name, address, birthday and Social Security number.
Experian, You Have Some Explaining to Do
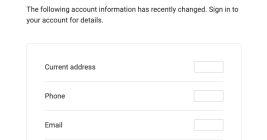
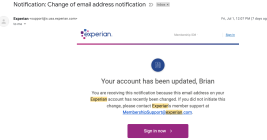
Twice in the past month KrebsOnSecurity has heard from readers who’ve had their accounts at big-three credit bureau Experian hacked and updated with a new email address that wasn’t theirs. In both cases the readers used password managers to select strong, unique passwords for their Experian accounts. Research suggests identity thieves were able to hijack the accounts simply by signing up for new accounts at Experian using the victim’s personal information and a different email address.
Experian API Exposed Credit Scores of Most Americans
Big-three consumer credit bureau Experian just fixed a weakness with a partner website that let anyone look up the credit score of tens of millions of Americans just by supplying their name and mailing address, KrebsOnSecurity has learned. Experian says it has plugged the data leak, but the researcher who reported the finding says he fears the same weakness may be present at countless other lending websites that work with the credit bureau.
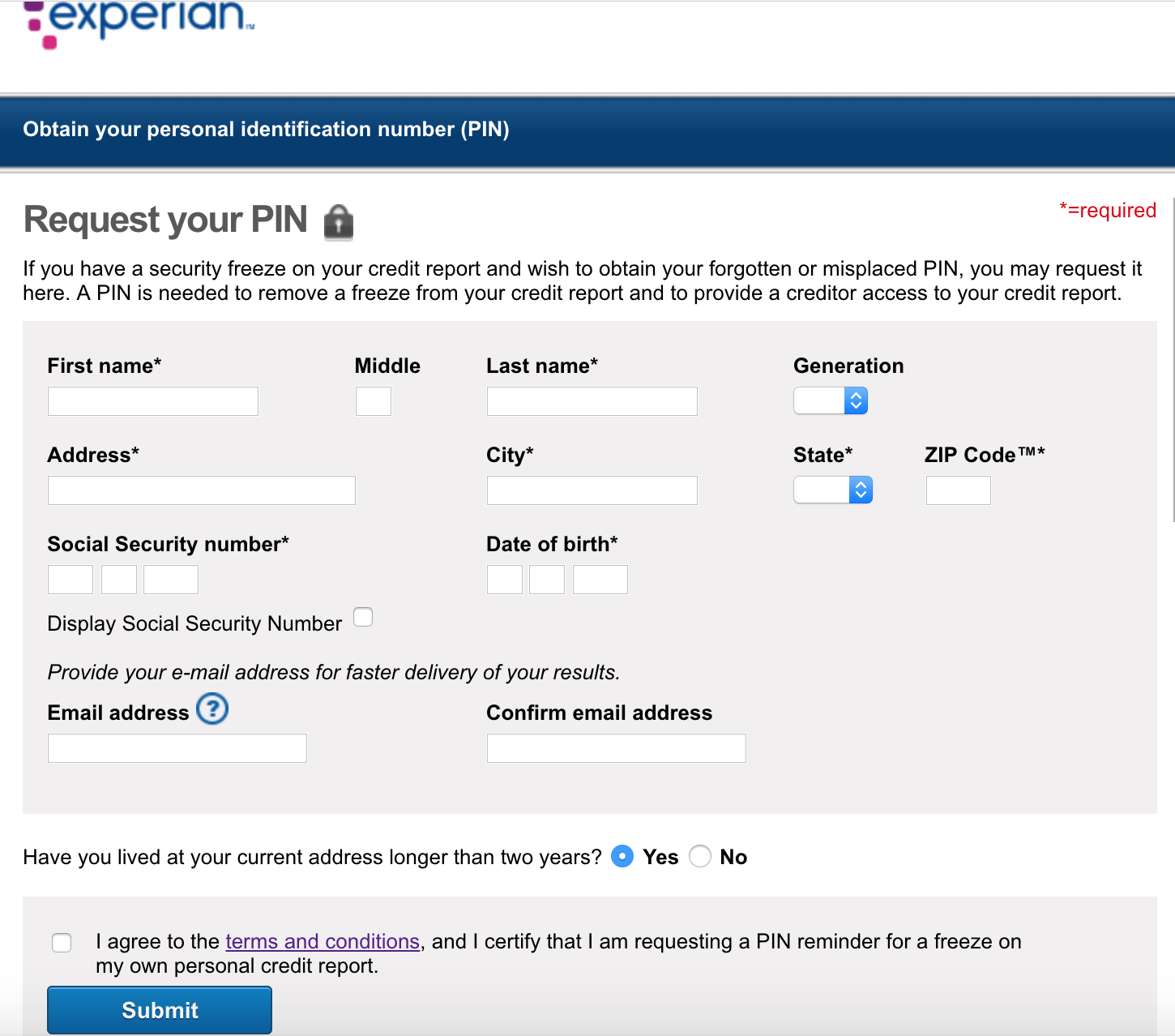
Experian’s Credit Freeze Security is Still a Joke
In 2017, KrebsOnSecurity showed how easy it is for identity thieves to undo a consumer’s request to freeze their credit file at Experian, one of the big three consumer credit bureaus in the United States. Last week, KrebsOnSecurity heard from a reader who had his freeze thawed without authorization through Experian’s website, and it reminded me of how truly broken authentication and security remains in the credit bureau space.
Confessions of an ID Theft Kingpin, Part I
At the height of his cybercriminal career, the hacker known as “Hieupc” was earning $125,000 a month running a bustling identity theft service that siphoned consumer dossiers from some of the world’s top data brokers. That is, until his greed and ambition played straight into an elaborate snare set by the U.S. Secret Service. Now, after more than seven years in prison Hieupc is back in his home country and hoping to convince other would-be cybercrooks to use their computer skills for good.