Sonic Drive-In, a fast-food chain with nearly 3,600 locations across 45 U.S. states, has acknowledged a breach affecting an unknown number of store payment systems. The ongoing breach may have led to a fire sale on millions of stolen credit and debit card accounts that are now being peddled in shadowy underground cybercrime stores, KrebsOnSecurity has learned.

The first hints of a breach at Oklahoma City-based Sonic came last week when I began hearing from sources at multiple financial institutions who noticed a recent pattern of fraudulent transactions on cards that had all previously been used at Sonic.
I directed several of these banking industry sources to have a look at a brand new batch of some five million credit and debit card accounts that were first put up for sale on Sept. 18 in a credit card theft bazaar previously featured here called Joker’s Stash:
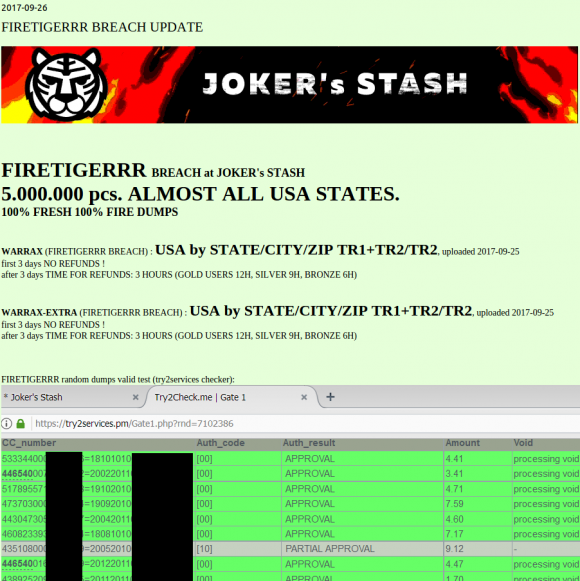
This batch of some five million cards put up for sale today (Sept. 26, 2017) on the popular carding site Joker’s Stash has been tied to a breach at Sonic Drive-In. The first batch of these cards appear to have been uploaded for sale on Sept. 15.
Sure enough, two sources who agreed to purchase a handful of cards from that batch of accounts on sale at Joker’s discovered they all had been recently used at Sonic locations.
Armed with this information, I phoned Sonic, which responded within an hour that it was indeed investigating “a potential incident” at some Sonic locations.
“Our credit card processor informed us last week of unusual activity regarding credit cards used at SONIC,” reads a statement the company issued to KrebsOnSecurity. “The security of our guests’ information is very important to SONIC. We are working to understand the nature and scope of this issue, as we know how important this is to our guests. We immediately engaged third-party forensic experts and law enforcement when we heard from our processor. While law enforcement limits the information we can share, we will communicate additional information as we are able.”
Christi Woodworth, vice president of public relations at Sonic, said the investigation is still in its early stages, and the company does not yet know how many or which of its stores may be impacted.
The accounts apparently stolen from Sonic are part of a batch of cards that Joker’s Stash is calling “Firetigerrr,” and they are indexed by city, state and ZIP code. This geographic specificity allows potential buyers to purchase only cards that were stolen from Sonic customers who live near them, thus avoiding a common anti-fraud defense in which a financial institution might block out-of-state transactions from a known compromised card.
Malicious hackers typically steal credit card data from organizations that accept cards by hacking into point-of-sale systems remotely and seeding those systems with malicious software that can copy account data stored on a card’s magnetic stripe. Thieves can use that data to clone the cards and then use the counterfeits to buy high-priced merchandise from electronics stores and big box retailers.
Prices for the cards advertised in the Firetigerr batch are somewhat higher than for cards stolen in other breaches, likely because this batch is extremely fresh and unlikely to have been canceled by card-issuing banks yet.
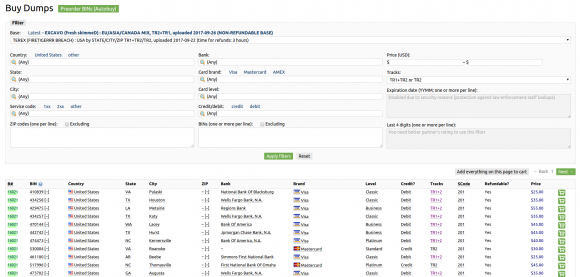
Dumps available for sale on Joker’s Stash from the “FireTigerrr” base, which has been linked to a breach at Sonic Drive-In. Click image to enlarge.
Most of the cards range in price from $25 to $50, and the price is influenced by a number of factors, including: the type of card issued (Amex, Visa, MasterCard, etc); the card’s level (classic, standard, signature, platinum, etc.); whether the card is debit or credit; and the issuing bank.
I should note that it remains unclear whether Sonic is the only company whose customers’ cards are being sold in this particular batch of five million cards at Joker’s Stash. There are some (as yet unconfirmed) indications that perhaps Sonic customer cards are being mixed in with those stolen from other eatery brands that may be compromised by the same attackers.
The last known major card breach involving a large nationwide fast-food chain impacted more than a thousand Wendy’s locations and persisted for almost nine months after it was first disclosed here. The Wendy’s breach was extremely costly for card-issuing banks and credit unions, which were forced to continuously re-issue customer cards that kept getting re-compromised every time their customers went back to eat at another Wendy’s.
Part of the reason Wendy’s corporate offices had trouble getting a handle on the situation was that most of the breached locations were not corporate-owned but instead independently-owned franchises whose payment card systems were managed by third-party point-of-sale vendors.
According to Sonic’s Wikipedia page, roughly 90 percent of Sonic locations across America are franchised.
Dan Berger, president and CEO of the National Association of Federally Insured Credit Unions, said he’s not looking forward to the prospect of another Wendy’s-like fiasco.
“It’s going to be the financial institution that makes them whole, that pays off the charges or replaces money in the customer’s checking account, or reissues the cards, and all those costs fall back on the financial institutions,” Berger said. “These big card breaches are going to continue until there’s a national standard that holds retailers and merchants accountable.”
Financial institutions also bear some of the blame for the current state of affairs. The United States is embarrassingly the last of the G20 nations to make the shift to more secure chip-based cards, which are far more expensive and difficult for criminals to counterfeit. But many financial institutions still haven’t gotten around to replacing traditional magnetic stripe cards with chip-based cards. According to Visa, 58 percent of the more than 421 million Visa cards issued by U.S. financial institutions were chip-based as of March 2017.
Likewise, retailers that accept chip cards may present a less attractive target to hackers than those that don’t. In March 2017, Visa said the number of chip-enabled merchant locations in the country reached two million, representing 44 percent of stores that accept Visa.




“We are working to understand the nature and scope of this issue, as we know how important this is to our guests. We immediately engaged third-party forensic experts and law enforcement when we heard from our processor”
Same statement more or less in each and every breach.
Except no free credit-monitoring!
Whadda you mean? Course they will give you 1 free year of Experian Credit Monitoring…..
What? Crap no, they will be too expensive. Equifax is likely to have a firesale on that stuff, so it will be Equifax monitoring.
Having worked several breaches, this is often the case and most likely accurate. Depending on what is known, the company might not have a handle on what’s happened, what a compromised and if the threat actor is still active. The 1st step is containment and then investigation. The details of an investigation can change in the initial phases as more information and scope of the incident comes to light. Depending on if there are other related incidents, the company may be limited to what it can share.
the first thing to do is to be proactive instead of reactive and then there is no need for these statements….
Of course! Everyone just needs perfect security! It’s so simple!
At least he managed to avoid saying “this hurts us more than it hurts you”, as in the Equifax breach.
Does Sonic say who their credit card processor is?
“The accounts apparently stolen from Sonic are part of a batch of cards that Joker’s Stash is calling “Firetigerrr,” and they are indexed by city, state and ZIP code. This geographic specificity allows potential buyers to purchase only cards that were stolen from Sonic customers who live near them, thus avoiding a common anti-fraud defense in which a financial institution might block out-of-state transactions from a known compromised card.”
Well that’s damn convenient
The local level C/C sales are what made the Target breach so bad.
Which point of sale (POS) system are they using?
Up until late last year, if I remember right, many sites were using OrderMatic out of Oklahoma City. They moved to Micros prior to the Oracle purchase. Around here, I’m not certain how many of the sites have moved to Micros though. I have seen Micros at a few Sonic locations that were in mall food courts.
Source – I’m a Point-of-Sale tech. NOT Micros though.
There are roughly 180-250 Ordermatic Stores left. The rest are Micros.
The POS system they used should be a mute point as the POS shouldn’t have anything to do with credit card information. If it does that is a problem.
Sonic had a mixed bag of POS solutions not only ordermatic. Many have switched to Micros but several others deployed Infor.
Brian, the problem isn’t the issuing of EMV cards it’s the fallback to Mag at the merchant.
Agreeing with Jonah. My FI is close to 100% EMV – but until the merchants switch over *cleanly* to EMV acceptance, the FIs are in a tough spot. If we deny all fallback transactions, our cardholders get upset and say that we’re not providing good service – but if we accept a “bad” fallback transaction, we’re on the hook.
If this is as bad as it’s looking, we’ll hopefully see Visa or MC alert listings soon that will help the FIs to get these cards to a higher level of protection as quickly as possible. Right now I feel like my cardholders are potential sitting ducks.
i rarely see them used… most gas stations around here tape over the chip reader..
Good thing too because we have an EMV exploit that is going to make them worthless.
Do you have any more details on the supposed exploit?
It might be beneficial to differentiate between technical fallback (where the chip supposedly can’t be read for whatever reason and the EMV-enabled terminal allows swiping) and using the magstripe because the store can’t do EMV yet. The latter is probably not a good idea right now–and may not be for quite some time–but the former may be something worth doing depending on the issuer/transaction.
Agreed on the technical fallback (and I have rules that do just that).
Unfortunately, cardholder *and merchant* education is where we run into issues. If I had a dollar for every time I had a cardholder tell me that a Wal-Mart cashier told them to “Remove and Insert the card quickly 3 times, and then you can swipe it with no issues” I’d be incredibly rich. >:(. And of course, the cardholder now thinks my GI is the bad guy because we’re still declining the transaction for true technical fallback.
Another problem is many non-retail sites still can’t use the chip readers. They just don’t have the ability. Also, the fact that the US EMV implementation is using a signature still, rather than a PIN as the rest of the world….because the US “just can’t change.” Many hospitality (restaurant) locations do not have the ability to use EMV yet. Their readers aren’t on-site or not setup yet, because the banks/card companies haven’t approved the readers to be used yet. It’s not just on the FI. It’s a huge cluster.
We’ve been waiting forever to have it working for our customers. Hopefully we’ll start seeing a few of our customers come online late this year, early 2018. Who knows.
I think NFC will be the bigger player for me. Samsung Pay or an app that has the info loaded that uses a token or “false” # that is not tied directly to my primary card #.
I thought after 2015, if the bank customer presents and EMV card and the merchant issues a mag stripe transaction, the merchant is on the hook for all of the fraud. If the banks hit Sonic with a bill for all of the costs of the fraud and make that public, merchants will get religion about switching.
Here we go again…!
In the first image of your article, those numerous small charges shown as authorized for each card, would those actually show on the true owners statement, and in this way is showing that the cards are valid?
Are digital vendors, such as iTunes and Amazon digital easy ways to quickly determine if a card is still valid?
Asking as we recently had are card replaced due to iTunes charges, we don’t have any Apple products/devices/accounts and this vendor stood out as invalid to us.
Thanks for any feedback.
of course… they are not going to clone cards and hit up ATMs or stores..
It depends on how and who they are abusing for their merchant accounts. Basically they use hacked merchant accounts to put through small dollar transactions on the cards, and the banks do try to ID those compromised merchant accounts to flag cards that are run them as completely compromised. However, not all banks will reissue just because they detect a test charge. Anyway, in my experience the vast majority of the compromised merchant accounts they use for dumps (counterfeit physical cards) are at brick-and-mortar merchants.
In some cases, the fraudsters will put a pre-authorization charge through that never actually gets charged. It’s like a check to see if the card is capable of paying and you typically will see these small 99 cent charges initiated at gas pumps or sometimes bars.
Someone can and probably will correct me here if I’m off base on any of this. It’s been a while since I dug into the compromised merchant account space.
Respected Sir, I’m a CEH having doubt regarding AI (The Automation). Does it really replace penetration testing and cyber-security jobs in future?? If Yes then I’ll better move to quantum information and computing, so whats your advise on this??
Kind of glad that I haven’t eaten at Sonic in over a year.
Last time I purchased any Sonic food was over three (3) years ago. The hamburgers that I bought tasted like rancid drek. I had a two-for-one coupon. I ate half of one sandwich and threw the remainder in the garbage. The food was so bad that I vowed never to dine there again.
I have yet to regret that decision.
I’ve complained about our local sonic to their 800 # over 100 times over the last 10 years. You should see the place. The light sockets outside regularly catch on fire, the roof leaks, their sewer floods the adjacent lots, the people that work there are single moms with 12 kids and no teeth. Typical Sonic Drive In.
ROTF!!
Where I live in upstate NY, single moms are put on the front page of the “news”paper & written up as some sort of heros! And no, I’m not talking about widows either.
99% of the time, I use their app to pay, but thanks to incentives by FIs (minimum number of Debit transactions a month for Bonus Interest Rate), it looks like I used a (non-PIN) debit card twice over the Summer. Just checked transactions and so far nothing suspicious.
What does “Fire Dump” mean?
“FireTigerrr” + “Data Dump” = Fire Dump
“Likewise, retailers that accept chip cards may present a less attractive target to hackers than those that don’t.”
But when it’s chip and sign instead of chip and pin, the full security potential of these cards is dramatically reduced. Every terminal I’ve used in the last two years that accepted chip cards, only asked me to sign and many didn’t require even that.
I never, ever, use cards at places like Sonic, only major retailers, or high dollar purchases. I still use cash, and never use a store customer rewards card especially if I want my purchase to remain annoymous.
At this rate, Brian is going to need to clone himself to cover, research and write about all the breaches, CC theft, card skimmers, phishing schemes, IoT issues, DDOS, software hacks, OS hacks, ransomware, malware, identity theft…I’ll stop here or my fingers will go numb typing all the potential “issues” for Brian’s blog.
Chip and signature still makes it far more difficult to clone cards, reducing the value of data from breaches such as Sonic’s. Plus, since most merchants are going with fully integrated EMV solutions (vs. setups where the terminal itself handles the communication with the payment processor), a significant portion of their infrastructure is subject to certification–which should in theory help to enforce security standards that frankly should be common sense at this point.
That said, it would have been nice to have the portable terminals at restaurants, but apparently the ones I’ve been to in the US that use the chip have decided that they’re not worth the expense.
When I use a “chip and sign” card, most of the time I get a text notification of the charge before I even sign. I don’t think the signature is part of verification.
The signature isn’t part of the authorization.
It’s simply proof that the customer was present when the transaction occurred. This is supposed to prevent the customer from claiming (falsely) that the charge to their card was unauthorized by themselves.
Ideally, the cashier would deny the customer from leaving (and maybe call police), if the signature doesn’t match the card and the customer lacks photo ID.
In practice, I usually draw an X on the POS card reader screens and have never been questioned, even for large purchases.
Since merchants bore no responsibility for card fraud until recently, I’m guessing that they haven’t really dealt with significant losses from fraudulent claims of “I wasn’t in the store! That’s not my signature!”
It has been decades since any merchant has compared signatures. For years I haven’t even signed my credit cards and absolutely no one has ever checked.
A signature on a receipt is absolutely meaningless.
In my retail situation, we have resorted to using video evidence of the customer’s presence at the point of sale at the time of the transaction. (Normal retail setup with traditional registers.)
That said, we do indeed eat the loss on a contested charge, when we cannot prove that the customer was present for the transaction.
Given the weakness of signatures as proof, video evidence seemed, to us, to be the new gold standard for proof of a legitimate charge.
“In my retail situation, we have resorted to using video evidence of the customer’s presence at the point of sale at the time of the transaction.”
I’ve just noted Target has cameras aimed at your face at their self serve checkouts. I do not use CC’s at Target to begin with (less data mining). But wonder if the next time I use the self serve I’ll be issued a coupon for items I bought on a previous trip, facial recognition as well as documenting the sale?
https://techcrunch.com/2015/02/24/stoplift-watches-you-at-the-self-checkout/
http://fortune.com/2015/11/09/wal-mart-facial-recognition/
https://www.eff.org/deeplinks/2015/11/how-california-cops-use-mobile-biometric-tech-field
Paranoid yet? And you thought the 143 million records theft from Equifax was hot stuff? All those thieves probably want is to steal money. All this other stuff is the really scarry story.
“Chip and X” is the EMV part that reduces fraudulent purchases due to the difficulty of producing cloned cards, but is different from (though pretty much always implemented at the same time as) E2EE/P2PE and tokenization which is what makes it harder to actually steal card information. The only real incentive for a merchant to implement the EMV portion is chargeback fraud protection, but that’s such small risk for fast food that it usually isn’t worth the slowdown it causes during the purchase process. When was the last time someone came back to Sonic two weeks later and insisted they didn’t buy that $4.99 lunch?
thats because the cardholder contacts the FI and that’s who is out the $$.
@Robert
The sole benefit of Chip and PIN as the primary authorization profile is that if someone steals your wallet it’s much harder to find a brick and mortar store payment terminal that will let them use it without knowing PIN.
Those situations are pretty rare by comparison.
The chip prevents the cloning not the PIN.
“The security of our guests’ information is very important to [us]….”
We should make a drinking game and have one every time that someone who most assuredly did NOT treat their guests’ information as important says this….
So, y9u want everyone to go though life hammered, eh?
SONIC selected MICROS systems in 2013 as the replacement to their existing 30-year-old POS system. They’ve been using MICROS since then. http://www.hospitalityupgrade.com/_news/NewsArticles/MICROS-Systems-Inc-Selected-by-SONIC-Restaurants.asp
Did Oracle ever fix anything with that big MICROS breach last year? Or did they just implement half measures and improved marketing and just left their customers unprotected? https://krebsonsecurity.com/tag/micros-breach/
Interesting. No idea, Andrew. Ask yourself how many other news organizations followed up on my reporting about the MICROS breach and actually pushed for answers? Hint: none that I could tell.
My question is why are they relying on the POS to protect CC info, everything should be handled by the payment device.
Didn’t the FIs contractually transfer liability to any businesses that have failed to implement chip readers on their POS systems? Or has that not taken effect yet?
They did back in October 2015 (except for gas pumps, which have until 2020).
The liability shift was for chargeback fraud, which isn’t really an issue for this industry.
Brian,
I had two odd experiences recently, and I was wondering if you had any comments on them. I should mention that I had three cards compromised in the last year or so. On two of those occasions, I caught a test charge, and I was able to cancel the card before anything big happened (I try to look at my accounts once or twice per day).
The first experience, about two weeks ago, I got a text message that my billing address had been changed. I immediately called the bank (Capital One), and I was told that they were updating data in their system, that they were aware that those messages were going out when they should not be, that everything was OK, and that they still had my billing address in a nearby, dangerous city where I never leave the train station. When I said that was not my billing address, the rep said that they had put it in the wrong field, and she would put it back. She basically blew me off. I looked the next day, there was an $1825 charge from Dell that they had to eat because the telephone rep paid no attention to the red flag that I was waiving.
The other incident was in a hardware store on Saturday. The merchant processed my card with a chip-enabled, stand alone POS terminal, and he ALSO typed the number into a POS program on a PC. I called Capital One, and the fraud telephone rep was shocked, but after a long call, she said that she did not see what could be done about it. If the bank’s fraud department does not know what to do about it, who does? Perhaps you could suggest how to contact Visa about that merchant? They are putting all of their customers at risk.
I’ve used my card a couple of times in Galveston, TX how can I find out about if my card is on there?
Would like to help
Ok, Hands up who hasn’t had their card compromised.
I haven’t had any of my cards compromised over the last 20+ years, but then I’m not in the US.
In this case, no, but I have never been to a Sonic. It could be something else next week however.
When can we start suing these companies who play fast and loose with our information?
Responding to Matty.
Touch wood I have never had a card compromised but I am based in the UK where the level of card fraud is much lower than the US (Chip and Pin etc).
However, I am paranoid and require my card issuer to reissue a new card every 6 months.
For Internet payments, I only use Paypal as I believe that their focus on internet banking security is better than the majority of High street banks.
For Amazon payments (they don’t accept Paypal) I only use a preloaded Internet credit card.
When I travel I use a physical preloaded credit card which is changed monthly.
Everything else is cash.
“These big card breaches are going to continue until there’s a national standard that holds retailers and merchants accountable.”
WRONG WRONG WRONG! Retailers, merchants, AND card holders are all paying customers of the financial institutions who issue and manage these cards for profit.
The problem is the financial institutions have ZERO incentive to spend the time and money needed to stop these security breaches. The breaches are statistically small in numbers compared to the total number of normal transactions, and any costs to the financial institutions caused by the breaches are simply passed on to the entire customer base.
One thing that would stop these breaches in large-part is holding the financial institutions criminally and civilly liable. But that would require new laws that specifically protect merchant and card holder rights. As it is now, by just being a customer of these card issuing financial institutions, you are forced to give up any rights that may be used to hold them accountable.
How in the world can you say a FI should be held responsible for a breach that happened at Sonic or any other location?
Because we don’t know how this breach happened, look at the Target breach. Someone hacked an HVAC company and then found that they had access to Target. They got into Target because of a hole in security, not because of the bank that issued a credit card or debit card. Please explain how this was a FI’s fault!
It’s like leaving your house unlocked and someone comes in and steals your wallet or purse. Is that also the fault of your FI or should you have locked your doors?
You clearly have no idea how much time, effort and money each breach costs your bank. The breach has to be researched, customers have to be contacted and cards need to be re-issued.
YES, I do work for an FI so I know first hand how much is put into each and every breach that occurs.
Totally agree with you and Drone has no idea how much money breaches cost banks, not only from the standpoint of material costs but that of human cost. Most restaurants or fast food do not move to EMV enabled machines are due to costs and that fact that their per transaction charge is low so if that card was stolen they would not loose that much money. Hopefully one day these multiple breaches will wake up that industry since a breach of this magnitude impacts their overall sales, like it did in the Wendy’s breach.
Steve, you are correct!!! People don’t know how much $$ the FI looses each day for these charges. Who do they think gives the $$ back to the cardholder? And most of these charges aren’t able to be sent back through to the merchant that didn’t do what they should(because of the amount of the charge). You can take anyone’s card to walmart (and most merchants)and use it.
This has to be one of the stupidest comments I have seen. How is the FI resposible for a breach at a retailer. Even if a bank has converted to EMV cards, if the retailer doesn’t accept EMV and allows mag stripe transactions the EMV chip has no benefit. I don’t think I have been to any Sonic that used chip based transactions. And the cost of reissuing the cards is not passed on to the consumer. Especially for smaller FI’s the cost of a large reissue can have a significant impact on profits given the much higher cost to produce EMV cards. If lax security controls at a retailer result in a breach, they should have to eat 100% of the costs involved to clean up the mess they created.
I wouldn’t be so quick to condemn stores because they aren’t using EMV because they are probably still waiting on becoming EMV certified.
Even if they are EMV certified the tendering process is painfully slow compared to using the swipe.
Lastly, EMV was never designed for security. It is 20 year old technology designed to reduce risk for offline authentication when communication from the merchant to the bank is unreliable.
If Card Companies really wanted to improve security they would use something a little more secure than EMV.
More important, lets get rid of the cards and let consumers push payments, done right it would eliminate risk in the brick and mortar store and in eCommerce (EMV can’t do this).
“Even if they are EMV certified the tendering process is painfully slow compared to using the swipe.”
it’s maybe 8 seconds longer, max, that I have ever seen.
I never understand this argument. taking eight seconds longer now, vs. hours and days spent waiting on hold to sort things out later.
vanity, thy name is impatience and instant gratification…
Drone, I’m curious as to the logic of holding card issuing FIs responsible for a card hack at Sonic, or its merchant processor. The “banks are the boogeyman” argument is reserved for ’60s era hippies and millennial idiots who don’t know any better.
I believe this isn’t the first time Sonic has been breached.
I never use a credit card for everyday purchases. I guess most do because of convenience. It doesn’t take me more than about two minutes to stop by a bank cash machine to get all the cash I need for a month. Of course, this way my cards are protected. I use my card to purchase things on the web, but then I only use Bank of America ShopSafe that fixes the charge to a fixed price and the card number is good for one transaction only.
I must add that I was born the year that WWII was over, so I am very familiar with and cautious when it comes to government Nazi type snooping and tracking. Today’s government snooping is anathema to me, I absolutely hate it. This is the main reason I pay everything with cash.
Actually, Nazis were not the end-all, be-all of snooping and tracking: that award goes to Communists.
Nah, the end all be all of snooping is on going in the US of A.
Having had personal experience of living for extended amounts of time both under communism and in the U.S. I can safely tell you that snooping in the U.S. is nowhere near that in a communist country.
+1
“I must add that I was born the year that WWII was over, so I am very familiar with and cautious when it comes to government Nazi type snooping and tracking. ”
Meanwhile, fools purchase and install in their homes always-on Amazon audio and, now, audio/video monitoring devices with the data from it under the control of a giant corporation just so they can ask “can cats eat cheese” from across the room.
Yes, and I am not one of those fools. My cell phone is even in airplane mode and off continuously, except when I need to make a call. When traveling out of town, the battery is removed. And go ahead and make my day. Call me paranoid.
do we have a date range of when the compromise took place?
Actually, some of you are missing good shakes, and cherry limeaids, dang good. I usually pay cash. Not hackable, heh. But, I go with the the other thoughts. Good article, but, some random thoughts. Ever been the second in line for anything? Or ever heard of jit? Just in time, where the product you want is not there just yet, ever tried to use something not there yet? Or, the rest of the system is too crowded, like in you send an email, and you see the little whirley circle for a moment, before you get the it’s sent message? In the US of a, not all systems are created equally. Part of the problem here, is the intermittent connections, handshakes, and data bursts cutting thru. Even landlines are prioritized, over the consumer. But, it’s all carried over the same communications sprectum now. How, can this be tapped?
We are all riding the wave of convenience to using our bank cards for “everything”.
We continue to see that companies are not keeping up with security from POS terminals (non chip) and scanning for issues BEFORE the “Breach event” occurs.
The lack of responsibility of the IT data is astounding! And when these companies do find out there was a breach everyone is playing the Hush…Hush game and delay…delay….delay announcing they had an issue. (No Transparency that is immediate.) All of these companies are concerned how these security breach announcements will affect their stock price and patrons trust.
When going out to eat I always use CASH or a Gift Card (gift card-Visa/Restaurant Card) . These are still the only thing that can reduce the collateral damage since we cannot continue to trust these establishments to take serious responsibility of our card data and the credit card companies keep kicking the can down the road in making companies to update their POS technologies and shifting the fiscal responsibility back on them. (establishment that is swiping the card). Yes a Visa-Gift card can still be breached, BUT there’s a set $ limit on these cards and you would only be out that balance. Not have your checking account HIT and have to get new cards etc. These Gift Cards are NOT tied to your personal info either as they are throw-away.
CASH is king. You pay for the services and the transaction is DONE. No security or possible issues after.
I consider my time as valuable and having to chase false charges. Getting bank cards shut down, filling out charge disputes. No thanks. We all need to be proactive and take back the responsibility of our personal data and stop trusting that the companies that we do business with care. Companies seem to handle our data as a cost vs risk calculation. They really have no consequences for their bad decisions. Today Visa/Bank pick-up the Tab. Until that occurs will these companies take data and IT security seriously.
I see that you are very confident using cash. After you get mugged, you might be less confident. If you have $20 in your wallet and 3 credit cards, the mugger won’t get much out of you. But if you have $400 and no credit cards, well, the $400 is gone forever.
The point is that each method of payment has its advantages and disadvantages to the consumer. I, for one, am much more comfortable with credit cards. It’s like carrying around a huge wad of cash that I can’t possibly lose because the bank has insured it for me.
Lucky I don’t live in a major city that I would need to carry $400 in cash with me. I’m able to live off of $50-100 a week in cash or Visa Gift Cards. As far as being mugged…the mugger is going to get what you have either way as they don’t know what you have until it occurs. Sounds like you’ve had an event that makes you think in this way. That’s unfortunate. My comment is how to keep your personal data protected since the companies out that are not doing what is needed at the POS terminal and back office IT. Two different points.
How many times have you been mugged vs. had unauthorized credit card charges? Even though you don’t have to pay for it, someone does and that drives up costs for everyone.
Totally agree with FunnyBits and Steve. Until the restaurant/fast food and retailers receive financial loss for breaches they will not change. Their “per ticket” sale is so low that they can afford to take a loss on a stolen card or two. Their entire systems are too expensive to replace so the financial institutions or card issuers are on the hook. Evidently the October 2015 EMV movement did not mean much to specific industries. The Financial Services industry has been diligent in getting cards out to their customers however have also been hindered on card supply. When will we as an employee of a financial institution start pushing back and charging back the fees incurred with all of these breaches?
Yes, there is some value to using cash only.
There are also some drawbacks.
Credit Card purchases for goods and services can bring along leverage should things not go so well in the days or weeks immediately following a “completed” transaction.
Having to carry a lot of cash can be dangerous in many places.
Indiscriminate use of credit and credit cards can be quite hazardous, but “cash-only” is not the only way to mitigate the risks of the former.
A balanced use of the various financial instruments is a good idea.