I cannot recall a previous data breach in which the breached company’s public outreach and response has been so haphazard and ill-conceived as the one coming right now from big-three credit bureau Equifax, which rather clumsily announced Thursday that an intrusion jeopardized Social security numbers and other information on 143 million Americans.
WEB SITE WOES
As noted in yesterday’s breaking story on this breach, the Web site that Equifax advertised as the place where concerned Americans could go to find out whether they were impacted by this breach — equifaxsecurity2017.com —
is completely broken at best, and little more than a stalling tactic or sham at worst.
In the early hours after the breach announcement, the site was being flagged by various browsers as a phishing threat. In some cases, people visiting the site were told they were not affected, only to find they received a different answer when they checked the site with the same information on their mobile phones.
Others (myself included) received not a yes or no answer to the question of whether we were impacted, but instead a message that credit monitoring services we were eligible for were not available and to check back later in the month. The site asked users to enter their last name and last six digits of their SSN, but at the prompting of a reader’s comment I confirmed that just entering gibberish names and numbers produced the same result as the one I saw when I entered my real information: Come back on Sept. 13.
Who’s responsible for this debacle? Well, Equifax of course. But most large companies that can afford to do so hire outside public relations or disaster response firms to walk them through the safest ways to notify affected consumers. In this case, Equifax appears to have hired global PR firm Edelman PR.
What gives me this idea? Until just a couple of hours ago, the copy of WordPress installed at equifaxsecurity2017.com included a publicly accessible user database entry showing a user named “Edelman” was the first (and only?) user registered on the site.
Code that was publicly available on equifaxsecurity2017.com until very recently showed account information for an outside PR firm.
I reached out to Edelman for more information and will update this story when I hear from them.
EARLY WARNING?
In its breach disclosure Thursday, Equifax said it hired an outside computer security forensic firm to investigate as soon as it discovered unauthorized access to its Web site. ZDNet published a story Thursday saying that the outside firm was Alexandria, Va.-based Mandiant — a security firm bought by FireEye in 2014.
Interestingly, anyone who happened to have been monitoring look-alike domains for Equifax.com prior to yesterday’s breach announcement may have had an early clue about the upcoming announcement. One interesting domain that was registered on Sept. 5, 2017 is “equihax.com,” which according to domain registration records was purchased by an Alexandria, Va. resident named Brandan Schondorfer.
A quick Google search shows that Schondorfer works for Mandiant. Ray Watson, a cybersecurity researcher who messaged me this morning on Twitter about this curiosity, said it is likely that Mandiant has been registering domains that might be attractive to phishers hoping to take advantage of public attention to the breach and spoof Equifax’s domain.
Watson said it’s equally likely the equihax.com domain was registered to keep it out of the hands of people who may be looking for domain names they can use to lampoon Equifax for its breach. Schondorfer has not yet returned calls seeking comment.
EQUIFAX EXECS PULL GOLDEN PARACHUTES?
Bloomberg moved a story yesterday indicating that three top executives at Equifax sold millions of dollars worth of stock during the time between when the company says it discovered the breach and when it notified the public and investors.
Shares of Equifax’s stock on the New York Stock Exchange [NSYE:EFX] were down more than 13 percent at time of publication versus yesterday’s price.
The executives reportedly told Bloomberg they didn’t know about the breach when they sold their shares. A law firm in New York has already announced it is investigating potential insider trading claims against Equifax.
CLASS ACTION WAIVER?
Yesterday’s story here pointed out the gross conflict of interest in Equifax’s consumer remedy for this breach: Offering a year’s worth of free credit monitoring services to all Americans via its own in-house credit monitoring service.
This is particularly rich because a) why should anyone trust Equifax to do anything right security-wise after this debacle and b) these credit monitoring services typically hard-sell consumers to sign up for paid credit protection plans when the free coverage expires.

Verbiage from the terms of service from Equifax’s credit monitoring service TrustID Premier.
I have repeatedly urged readers to consider putting a security freeze on their accounts in lieu of or in addition to accepting these free credit monitoring offers, noting that credit monitoring services don’t protect you against identity theft (the most you can hope for is they alert you when ID thieves do steal your identity), while security freezes can prevent thieves from taking out new lines of credit in your name.
Several readers have written in to point out some legalese in the terms of service the Equifax requires all users to acknowledge before signing up for the service seems to include legal verbiage suggesting that those who do sign up for the free service will waive their rights to participate in future class action lawsuits against the company.
KrebsOnSecurity is still awaiting word from an actual lawyer who’s looking at this contract, but let me offer my own two cents on this.
Update, 9:45 p.m. ET: Equifax has updated their breach alert page to include the following response in regard to the unclear legalese:
“In response to consumer inquiries, we have made it clear that the arbitration clause and class action waiver included in the Equifax and TrustedID Premier terms of use does not apply to this cybersecurity incident.”
Original story:
Equifax will almost certainly see itself the target of multiple class action lawsuits as a result of this breach, but there is no guarantee those lawsuits will go the distance and result in a monetary windfall for affected consumers.
Even when these cases do result in a win for the plaintiff class, it can take years. After KrebsOnSecurity broke the story in 2013 that Experian had given access to 200 million consumer records to Vietnamese man running an identity theft service, two different law firms filed class action suits against Experian.
That case was ultimately tossed out of federal court and remanded to state court, where it is ongoing. That case was filed in 2015.
To close out the subject of civil lawsuits as a way to hold companies accountable for sloppy security, class actions — even when successful — rarely result in much of a financial benefit for affected consumers (very often the “reward” is a gift card or two-digit dollar amount per victim), while greatly enriching law firms that file the suits.
It’s my view that these class action lawsuits serve principally to take the pressure off of lawmakers and regulators to do something that might actually prevent more sloppy security practices in the future for the victim culpable companies. And as I noted in yesterday’s story, the credit bureaus have shown themselves time and again to be terribly unreliable stewards of sensitive consumer data: This time, the intruders were able to get in because Equifax apparently fell behind in patching its Internet-facing Web applications.
In May, KrebsOnSecurity reported that fraudsters exploited lax security at Equifax’s TALX payroll division, which provides online payroll, HR and tax services. In 2015, a breach at Experian jeopardized the personal data on at least 15 million consumers.
CAPITALIZING ON FEAR
Speaking of Experian, the company is now taking advantage of public fear over the breach — via hashtag #equifaxbreach, for example — to sign people up for their cleverly-named “CreditLock” subscription service (again, hat tip to @rayjwatson).
“When you have Experian Identity Theft Protection, you can instantly lock or unlock your Experian Credit File with the simple click of a button,” the ad enthuses. “Experian gives you instant access to your credit report.”
First off, all consumers have the legal right to instant access to their credit report via the Web site, annualcreditreport.com. This site, mandated by Congress, gives consumers the right to one free credit report from each of the three major bureaus (Equifax, Trans Union and Experian) every year.
Second, all consumers have a right to request that the bureaus “freeze” their credit files, which bars potential creditors or anyone else from viewing your credit history or credit file unless you thaw the freeze (temporarily or permanently).
I have made no secret of my disdain for the practice of companies offering credit monitoring in the wake of a data breach — especially in cases where the breach only involves credit card accounts, since credit monitoring services typically only look for new account fraud and do little or nothing to prevent fraud on existing consumer credit accounts.
Credit monitoring services rarely prevent identity thieves from stealing your identity. The most you can hope for from these services is that they will alert you as soon as someone does steal your identity. Also, the services can be useful in helping victims recover from ID theft.
My advice: Sign up for credit monitoring if you can (and you’re not holding out for a puny class action windfall) and then freeze your credit files at the major credit bureaus (it is generally not possible to sign up for credit monitoring services after a freeze is in place). Again, advice for how to file a freeze is available here.
Whether you are considering a freeze, credit monitoring, or a fraud alert (another, far less restrictive third option), please take a moment to read this story in its entirety. It includes a great deal of information that cannot be shared in a short column here.




I suspected that checking site is a way to scam ss numbers, since knowing the last 6 digits plus your location gives you the full number, if you have a pre 2011 number which is not randomized.
How could they possibly deduce my first three numbers if I am checking thousands of miles from where I was born(other than from brute force guessing)?
Because they ask for not only your last 6 digits but also your last name. It may not be very difficult to find where someone was located when they received their SSN if you have their last name.
There is a web site familytreenow.com that allows anyone to look up a target’s previous addresses. Its free and does not require any sort of registration to get to the target’s info.
I heard that staff bailed their shares when the incident occurred NOT when it was announced to the public. True?
The CFO sold over a million dollars in May 2017, exactly when his lock period ended after being hired in May 2014, and sold a smaller amount one quarter later. Without specific evidence otherwise, this looks like typical diversification that any financial advisor would tell an executive to do.
I should have read Daniel’s comment before I posted mine. That sounds like a good point that’s not readily known to us layperson types.
So now I’m back just to say that the timing of the selling for all involved would need to be compared to various things… like internal communications, yada-yada… which is potentially gone.
BUT… Internet servers are supposed to hang on to those things, depending on how they’re set up, just for situations like this. It’s sounding like maybe.. hopefully.. “they” were using something like Gmail or Yahoo. It seems a natural fit to other things coming out. 🙂
The more seconds that tick by after having read all this, the more one wonders… HOW does it happen to the very few who are dictated to… who are entrusted with… helping victims mitigate when this occurs via any other company out there?
Exclamation point! 🙂
Does “three top guys bailing at once” count as specific evidence?
Look at sales in September, not in May. Look for SEC Form 4, which is required to be filed when an officer buys or sells stock.
Hey Brian — I’d love to see an editorial or something from you recommending an improved “freeze” system. That we need to pay for a freeze seems wrong.
In NYS I didn’t have to pay for a credit freeze, it was free. To unlock/unfreeze it would cost $5 per agency and I can set a time limit of say 30 days unlocked then auto-lock after. I’ve actually had my credit frozen for years now to proactively protect myself.
Perhaps there will be a new federal law requiring the credit bureaus to add security freezes at no charge for any reason, nationwide. In Indiana, due to a state law (I think), there has not been any charge for adding a security freeze for many years.
Wishful thinking. That would require a law passed by congress and as we have seen the credit reporting companies spend massive amounts of cash lobbying congressmen/women to ensure that there are not laws that get in the way of their making money.
Not during the Trump Administration! Where have you been the last 10 months?
“Not during the Trump Administration!”
You’re kidding, right? Like the CONgress is any less bought just because the prez PERHAPS isn’t? Someone’s gotta’ pay for reelection campaigns in our (intentionally) far too long campaigning process.
Making a customer pay for a freeze is very profitable for the credit bureaus. Just think how much money they are making today.
>Making a customer pay for a freeze is very profitable for the credit bureaus.
To the contrary, they are unprofitable since they have fewer full profiles to sell. As proof, the credit bureaus never promote them as a good thing that regular people should do.
It’s time that Congress investigated these giant credit-reporting agencies. The type of data they maintain, and the vast amount of it, make them huge targets for hackers. They should be required by law to have a world-class intrusion and monitoring system as well as a 24 hour reporting window from time of breach to public announcement. If these companies cannot keep our data safe, they should not be allowed to remain in business.
“If these companies cannot keep our data safe, they should not be allowed to remain in business.”
Sue them out of existence after a compromise. It’s the ONLY thing corporations understand.
It’s time that Congress investigated these giant credit-reporting agencies. The type of data they maintain, and the vast amount of it, make them huge targets for hackers. They should be required by law to have a world-class intrusion and monitoring system as well as a 24 hour reporting window from time of breach to public announcement. If these companies cannot keep our data safe, they should not be allowed to remain in business.
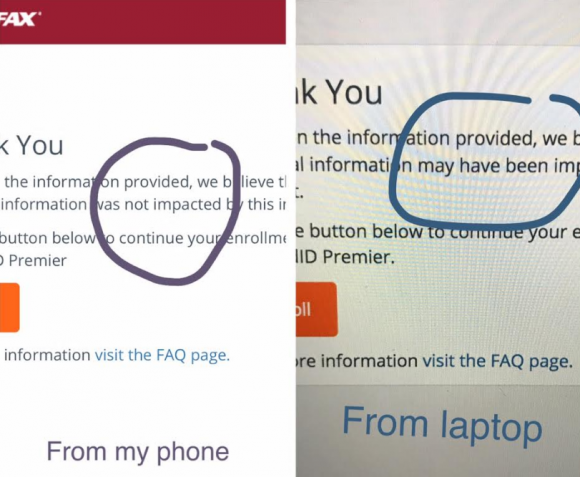
While I did get a vague message when I checked the Equifax site, a friend of mine actually got confirmation that his personal data was safe.
“Based on the information provided, we believe that your personal information was not impacted by this incident.”
Oh, so HE’s the one!
@ Candy, did your friend test both inquiry methods that Brian said he used?
That’s not for me personally. I’m just a-suming I won’t be the only one who will wonder that about *everyone’s efforts* to receive answers from Equifax now.
In fact, it wouldn’t hurt to keep reminding everyone to try both ways because of what Brian experienced. That way there’s *less of a chance* of a false sense of security going on anywhere. Best wishes 🙂
That is not exactly an ironclad guarantee. As I’m sure the forced arbitration will point out.
When does something like this cross over into “insider information”? Those words first started dancing in my head as I read the part about Equihax. A few more paragraphs down, and boom, there you go…………..
To release a credit freeze you need your PIN. I
f you forget your pin, you can get it by providing name, address, SSN, DOB. Which is the data that was lost in the breach.
https://www.experian.com/ncaconline/freezepin
Not able to confirm, but I believe they will mail it to your address on record. So simply knowing the information won’t get you the PIN, you will also have to intercept the letter.
Thanks for a job well done, and promptly reported.
At what point does “failure to patch” rises to criminal negligence? This case may reach that level.
Thank you, Brian for all of your information and your great reporting.
Nobody will be held responsible, I’m sure they own many members of congress and enough members of the house of Dump too easily skate through this little breech.
So, what if your credit score isn’t that great (584) and your account was compromised. Will the thieves still try to use it, or go on to someone with a better score?
Thanks for another insightful article. Came to your freeze article from reddit this morning and immediately used blogtrottr to sign up for your feed. Please keep up the good work of keeping us informed.
Why are they still allowed to do business,period?Shut hem down.
Thanks for your continued updates on this, Brian. I went through the process of freezing my credit files at all four bureaus. Experian has been nothing short of a byzantine exercise in futility thus far, requiring documents to be sent via snail mail (online and phone attempts were useless). When I actually found someone with whom to speak at Experian, they were no help at all and simply tried to strong-arm me into signing up for the service you mentioned, and even had the nerve to tell me that freezing my credit file was a “horrible idea that I would regret”. When I told him that I knew my rights and just wanted the freeze, he hung up on me.
@Kaye – I called Experian at 888-397-3742, selected option 2, and was easily able to get a freeze implemented in 2015. I got a letter with my PIN from them via snailmail a few weeks later.
HTH.
AL
> tell me that freezing my credit file was a “horrible idea that I would regret”.
That’s a clue that similar messages posted to these Equifax breach threads are probably by employees of credit reporting agencies.
See the Transunion site. Giving away free monitoring and free credit locks.
TransUnion just charged me $10 for a credit freeze.
Another interesting piece of info: The PIN that equifax gives you for your credit freeze is literally just the Date/Time that the freeze was requested. It is not randomized at all.
Bryan – Thanks again for the freeze advice and for staying on top of this story.
I followed your advice in 2015 and have only had to temporarily unlock one of the 4 services since. Not much of a price to pay for peace of mind.
Am concerned about the IRS refund fraud angle though – seems like the stolen data is perfect for enabling refund fraud…
Love your analysis and updates. FYI, I tried freezing all 3 credit bureau accounts this afternoon. Equifax and Transunion were ‘Temporarily Unavailable” AFTER I entered all my data.
Brian – I saw this thread on Reddit earlier about how Equifax’s PIN for unfreezing is at least partially determined by the date you froze your credit. Thoughts on this?
“Equifax’s PIN generation for their credit freeze process is non-random and is nothing more than the date and time you signed up for the credit freeze, e.g. 090817xxxx; this means that, solely because a lot of people will be signing up for credit freezes today, a potential fraudster could easily guess up to 6 digits of your 10 digit PIN, potentially being able to unfreeze your credit themselves.
This makes your primary line of defense against fraud potentially useless.”
https://www.reddit.com/r/technology/comments/6yu9q3/why_the_equifax_breach_is_very_possibly_the_worst/dmqfp3u
It’s not partially determined by the date/time, it IS the date/time
Hi Brian,
Look what happened when you come to visit us in NY. 🙂
Have you check the darkweb to see if any of the info is up for sale yet? Interested to see what are some of the findings resulting from Mandiant’s investigation.
We’ll definitely do the Charlie’s Angel post next time.
Haha. Guess I was right about the “assume you’re compromised” bit, eh? 🙂
I knew something serious was up: I’m in retail security and have been seeing fraudsters coming in to one store and using at the same time not one but two and three different credit accounts belonging to the same individuals (in one case a VISA, MC, and Amex). I have not seen that in almost twenty years in the field. Not only that but the sale people are saying the cards used are matching what type of cards and banks the accounts are from, and the cards have chips!
I had no problems with their site last night. A couple of people this morning checked without incident while I had them on the phone.
My concerns are that: (1) We’ve made credit checks mandatory for employment (at least in many states). Those laws need to get repealed and replaced. (2) Equifax still hasn’t released any details as to how their web system was exploited. (3) Their disclosure time is suspiciously long. it will indeed be interesting to see what the follow-ups to the Bloomberg story indicate.
In the interim I’m hoping that the unknown hackers/perpetrators have improved my credit 🙂
Brian-
I have frozen our credit file for all 3 today. It was done online and took around 20 minutes. Not sure why I waited.
We have had a membership with the Experian Monitoring Service for years. While it has enabled us to get our credit situation in very good standing, at $48/month for me and my wife, I am not so sure of it’s value now.
If I am reading correctly, your advice is to maintain the monitoring along with putting a freeze on the credit file?
What I’ve said is that it’s not generally possible to sign up for free monitoring when there’s a freeze in place. So if that’s valuable to you, set it up before you freeze. But I would never encourage anyone to pay for credit monitoring services when they are on offer for free probably from dozens of companies you have done business with that got breached over the past year.
If you’re really lost on that last point, check out the California OIG’s office, which lists each day several new breach victims that are offering free credit monitoring:
https://oag.ca.gov/ecrime/databreach/list
Funny How they waited to announce until the world was gripping with natural disasters like hurricanes and earthquakes, did they think that they would second page news?
I’d like to suggest that everyone contact your state attorney general asking that Equifax provide a credit report freeze to anyone who might be affected. There should be no charge for the freeze and *no future charges* for things like “unfreezing” when one needs to apply for credit. And no “mandatory arbitration” clauses, either.
If every AG gets a few hundred such requests, about half of them may be moved actually to do something, and they have the clout to make things happen.
Myself, as a resident of a freeze fee state, I just very vaguely thought of using the fee I’d pay to instead apply for a new SSN once the Equifax-devulged one is abused.
I put credit freezes in place a while back. I’m trying to switch cell providers and need to lift it temporarily. The carrier uses Experian. When I try to lift it, it redirects me to the listing that says under California law they can charge me $10. Not happy, but OK. But in order to do that, I have to send them snail mail with my info and credit card number. Huh? I’m a week into waiting to get it lifted, but I would guess at this point they are kind of busy ;-> I guess I should be glad they aren’t running an ecommerce site that would let me give them my cc on line, since they don’t seem to know what they are doing.
It’s hardly surprising. This is the same company that still has my employment listed as my ex-husband’s employer from 15 years ago. And this is who banks rely on to make credit no/go decisions. Nice.
Coincidence or not? The date Equifax stated was the day they discovered the breach was July 29…July 28 I was assisting my parents to freeze their credit reports-my newly deceased father’s identity was stolen. We first obtained their free credit reports then placed the freeze, it was seamless on Transunion and Experian. Equifax would not let us obtain the credit reports or freeze the credit. Makes you wonder why…
The Equifax response is totally inadequate. I requested the case number for their internal investigation, and the case number of the FBI investigation. They do not have either. Yet they require an investigation case number (and report) to waive their fees. I spoke with a supervisor, Erick. He was the only level of escalation. He would not transfer me to his boss. I explained that it was Equifax’s fault, and not mine. He would not budge. I said “do the right thing”. He would not escalate and stated he had no other solution other than the web site and “credit monitoring”. Clearly Equifax needs to be shut down in an orderly fashion, as they do not have the trust level needed for a financial company. If they are not shut down, a massive class action lawsuit should be filed to bankrupt them.
If the executives were NOT notified within an hour of the breech being discovered, I would consider that grounds for someone being fired.
So is someone getting fired or are the execs getting off unpunished from selling their stock on the bad news…?
As I said yesterday, the breech occurred in May (as far as they know) and we only hear about it 3 months later…?
I’d allow 24 hours to allow the IT guys to go through, “Holy shmoke! Are you sure?!?” However, once IT has assimilated to awfulness of what happened and assessed the evidence, the so-called C-level executives should have been notified.
Most of the credit reporting companies use ‘previous addresses’ as security questions. There is a genealogy web site that lets a user look up anyone they want (for free) and see all the previous addresses that a target has lived at. That information combined with the data taken from Equifax will allow for a criminal to do a lot of damage.
There is an opt-out option for this genealogy site. I used it for myself and every family member I have (alive and dead).
I learned about the site from Time magazine and read about it in many other reputable news outlets.
http://time.com/money/4634434/family-tree-now-opt-out-protect-yourself/
https://www.washingtonpost.com/news/the-intersect/wp/2017/01/12/youve-probably-never-heard-of-this-creepy-genealogy-site-but-its-heard-all-about-you/
Re previous address:
I forgot the number in my previous address (hey, I left there over 17 years ago …).
It took me one minute to find it w/Google.