Deloitte, one of the world’s “big four” accounting firms, has acknowledged a breach of its internal email systems, British news outlet The Guardian revealed today. Deloitte has sought to downplay the incident, saying it impacted “very few” clients. But according to a source close to the investigation, the breach dates back to at least the fall of 2016, and involves the compromise of all administrator accounts at the company as well as Deloitte’s entire internal email system.

In a story published Monday morning, The Guardian said a breach at Deloitte involved usernames, passwords and personal data on the accountancy’s top blue-chip clients.
“The Guardian understands Deloitte clients across all of these sectors had material in the company email system that was breached,” The Guardian’s Nick Hopkins wrote. “The companies include household names as well as US government departments. So far, six of Deloitte’s clients have been told their information was ‘impacted’ by the hack.”
In a statement sent to KrebsOnSecurity, Deloitte acknowledged a “cyber incident” involving unauthorized access to its email platform.
“The review of that platform is complete,” the statement reads. “Importantly, the review enabled us to understand precisely what information was at risk and what the hacker actually did and to determine that only very few clients were impacted [and] no disruption has occurred to client businesses, to Deloitte’s ability to continue to serve clients, or to consumers.”
However, information shared by a person with direct knowledge of the incident said the company in fact does not yet know precisely when the intrusion occurred, or for how long the hackers were inside of its systems.
This source, speaking on condition of anonymity, said the team investigating the breach focused their attention on a company office in Nashville known as the “Hermitage,” where the breach is thought to have begun.
The source confirmed The Guardian reporting that current estimates put the intrusion sometime in the fall of 2016, and added that investigators still are not certain that they have completely evicted the intruders from the network.
Indeed, it appears that Deloitte has known something was not right for some time. According to this source, the company sent out a “mandatory password reset” email on Oct. 13, 2016 to all Deloitte employees in the United States. The notice stated that employee passwords and personal identification numbers (PINs) needed to be changed by Oct. 17, 2016, and that employees who failed to do so would be unable to access email or other Deloitte applications. The message also included advice on how to pick complex passwords:
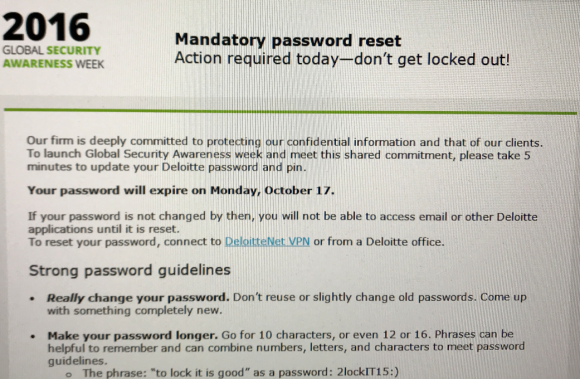
A screen shot of the mandatory password reset message Deloitte sent to all U.S. employees in Oct. 2016, around the time sources say the breach was first discovered.
The source told KrebsOnSecurity they were coming forward with information about the breach because, “I think it’s unfortunate how we have handled this and swept it under the rug. It wasn’t a small amount of emails like reported. They accessed the entire email database and all admin accounts. But we never notified our advisory clients or our cyber intel clients.”
“Cyber intel” refers to Deloitte’s Cyber Intelligence Centre, which provides 24/7 “business-focused operational security” to a number of big companies, including CSAA Insurance, FedEx, Invesco, and St. Joseph’s Healthcare System, among others.
This same source said forensic investigators identified several gigabytes of data being exfiltrated to a server in the United Kingdom. The source further said the hackers had free reign in the network for “a long time” and that the company still does not know exactly how much total data was taken.
In its statement about the incident, Deloitte said it responded by “implementing its comprehensive security protocol and initiating an intensive and thorough review which included mobilizing a team of cyber-security and confidentiality experts inside and outside of Deloitte.” Additionally, the company said it contacted governmental authorities immediately after it became aware of the incident, and that it contacted each of the “very few clients impacted.”
“Deloitte remains deeply committed to ensuring that its cyber-security defenses are best in class, to investing heavily in protecting confidential information and to continually reviewing and enhancing cyber security,” the statement concludes.
Deloitte has not yet responded to follow-up requests for comment. The Guardian reported that Deloitte notified six affected clients, but Deloitte has not said publicly yet when it notified those customers.
Deloitte has a significant cybersecurity consulting practice globally, wherein it advises many of its clients on how best to secure their systems and sensitive data from hackers. In 2012, Deloitte was ranked #1 globally in security consulting based on revenue.
Deloitte refers to one or more of Deloitte Touche Tohmatsu Limited, a private company based in the United Kingdom. According to the company’s Web site, Deloitte has more than 263,000 employees at member firms delivering services in audit and insurance, tax, consulting, financial advisory, risk advisory, and related services in more than 150 countries and territories. Revenues for the fiscal year 2017 were $38.8 billion.
The breach at the big-four accountancy comes on the heels of a massive breach at big-three consumer credit bureau Equifax. That incident involved several months of unauthorized access in which intruders stole Social Security numbers, birth dates, and addresses on 143 million Americans.
This is a developing story. Any updates will be posted as available, and noted with update timestamps.




This reads a lot like the Verifone breach. And if I remember right, didn’t it happen around the same time?
“…involves the compromise of all administrator accounts at the company…”
Does the above only mean all email accounts, or is it asserting that Windows and other accounts were compromised?
With control of email accounts, obviously many different cloud-based services that corporate individuals use could have been compromised via their password reset mechanisms. But simply changing passwords would be noticed.
Ouch.
Admin accounts mean root level access for any system; for AD authenticated accounts (Microsoft single sign-on) it means they had access to the “world” at Deloitte.
This is well understood, but the phrasing of the quote could be interpreted to mean the email system admin accounts were compromised, not (necessarily) the client or server machine accounts. It simply isn’t clear.
You’re right. If proper segregation of duties was implemented, application admins would not have the same level of access as enterprise admins… The article is not as clear as it could be.
Did shares get sold before the coming clean story? I find it shocking the period of time these big guys get away with before disclosing such a thing happens..
“Deloitte refers to one or more of Deloitte Touche Tohmatsu Limited, a private company based in the United Kingdom”
This explains a lot… Our users received spam invoices from them but it was confusing since they came from Deloitte servers as far as i could tell. I am going to see if i can dig them up from an archive.
Might be more about them charging fraudulent invoices than anything else.
I.e. this company: https://register.openownership.org/entities/59c5082b67e4ebf3406d5ff5
Deloitte, like the 3 other “Big 4” accounting firms and most law firms is a private partnership, not a public company.
I like the way they send out emails requesting users do a password reset. Sent out via email which was already compromised…
Can most US corporate security really be this lame…?
I would ask “What next?” but I think I already know what’s next. More of the same.
The screenshot is actually that of the internal Intranet site, in addition to the emails that were sent out.
Pardon me if I don’t hire them for infosec services…
Most of these organizations professional services arm i.e the consulting and advisory teams that advise the clients are not the ones in charge of internal IT or security. Clearly there is a discrepancy in capability that needs to be addressed between the groups.
Wait, which one are you saying is better? Internal IT or the consultants? In my experience neither are particularly competent.
I’d agree, but most major consulting firms don’t use their own consultants to review their environment because (1) they don’t want to spend their consultant’s chargeable time on non-chargeable work and (2) a company auditing itself raises an independence issue, so any work their own consulting arm does for the internal network would have to be replicated by an independent third party in order to be valid for a client or regulator.
Actually, Deloitte cybersecurity is one of their own biggest customers
What do they consider administrator accounts? Domain admins or administrative assistants?
Most of these organizations professional services arm i.e the consulting and advisory teams that advise the clients are not the ones in charge of internal IT or security. Clearly their is a discrepancy in capability that needs to be addressed between the groups.
All Administrator accounts. Lateral attacks
Deloitte is supposed to lead the way in terms of security and compliance as an IT auditor (SOC, SOX, HITRUST, etc.). They were clearly lacking in a common control. It escapes me why they would hold their clients to a high standard but not themselves.
Because those that operate the Deloitte internal infrastructure and security are not the same people who consult for the company.
That still is no excuse..something about eating your own dogfood before telling others how they should do their security.
Even worse: bill them for it.
With Deloitte, they initially bring some good people to impress and rhenreplace them with people with very little experience. This is the same with all the consulting orgs. I have personally dealt with their client facing teams a number of times, they have no enterprise or real world experience, but can throw around the buzz words
if it wasn’t for suits eating up buzzwords.. i doubt “the valley” would be as successful as it has been. Snake oil for all.
Ditto – all these affiliated consulting companies feature fresh faced MBAs from great schools. Limited or no real world, cyber, or security experience. See Duff McDonald’s “The Firm – the Story of McKinsey”for how this works. He also exposes Harvard Biz School in “The Golden Passport” though I have not read that one.
Dealt with these idiots. Most pompous set of characters. Couldn’t have happened to a nicer bunch of people
+1
Being pilloried in the town square will be quite humbling. Yeh?
I like this line:
“Deloitte remains deeply committed to ensuring that its cyber-security defenses are best in class…”
Did they copy it from Equihax?
What we need is a legislature that would impose heavy fines on companies that breach their customer data. So only then they will start spending on cyber-security equal amounts to marketing and sales.
GDPR maybe?
“Deloitte remains deeply committed to ensuring that its cyber-security defenses are best in class, to investing heavily in protecting confidential information and to continually reviewing and enhancing cyber security,” the statement concludes”
Deloitte doesn’t seem to be committed to protecting their employees before this happened DOH!
And how many more shoes are ready to drop? Is cyber security truly that difficult, or are companies simply not up to the challenge? Forgive my cynicism, but I’ll opt for the second alternative.
The answer to both of your questions is yes. Combating it the modern threat landscape is hard. Even with the right tools and expertise getting it right all the time every time is no easy task. Some companies are better than others, but in large companies with thousands of virtual servers across various local and cloud platforms, it’s tough to coordinate all of the things that need to be protected. The other aspect of this is yes a lot of companies are just this inept. Simple things like patching and privileged account management goes undone because of lack of priority, manpower, attention, or skill. I’m amazed at the ridiculousness some of these F500 companies allow in their internal IT. Delloite needs to take a dose of their own medicine and have a full security posture assessment done regularly with a full audit trail of remediation tasks.
I’m just a wanna be, but I’ve heard Steve Gibson say doing security right is difficult. However, it doesn’t seem these people(at all the breached companies) even try!
Brian we are a Deloitte client and did contact them today. They are claiming we were not impacted and it was only one mail server that was breached. That is all they would tell us. Seems different than what you heard and I am concerned since we do send them sensitive information (as do most of their clients).
Right, just one server. Because there’s no way they have a cluster of email servers that replicate data among themselves. But the hackers only got to one server…
It might have started at one email server but certainly didn’t end there. Even one email server compromised at the administrator level should leave you extremely concerned. It isn’t like they could send out seemingly legitimate emails requesting confidential info from clients or password resets to employees or anything like that. Or harvest the message database. Or distribute malicious bespoke payloads like in the CCleaner incident. Or any number of things you can do when you have complete control of a server and can masquerade as a trusted source.
How many weasel words were in their response? As of today our investigation… We have identified one server… We are not aware of additional…
“Deloitte has a significant cybersecurity consulting practice globally, wherein it advises many of its clients on how best to secure their systems and sensitive data from hackers. ”
Seems they could use some of their own “best in class” cyber security advice…
Most of these consultancies unfortunately rarely use the capabilities of their highly paid advisors and rely on other teams or third parties for their internal infrastructure and security. I bet that is about to change. I have been a client of some of these firms and can attest to the talent that some of their teams have from a client service standpoint.
I agree. My previous company brought them in for cybersecurity consulting and their team had a lot of knowledge. The main issues we had was that their solutions were outrageously expensive and would have made it impossible to get work done. They definitely used their own internal network as an example when they were advising what they could do for us. As we were getting set up on their Sharepoint, we noticed that what they were saying about their internal network, and what they were doing were two different things.
Change company name to Toilette & Douche ?
Yup, they are a bunch of douchbags!
Deloitte got Touched?
I am always amazed when tech admins use their mighty AdminAccounts for daily end-user tasks like email, wordpro and surfing. Not sure this was a aggravating factor, but the fact the news cites both – I would say there is more than one element of lazy administration at play.
#1World1Date1Day
…these companies should be using encrypted and ephemeral communication platforms like Wickr Pro.
“Wickr Pro is a secure messaging ecosystem, differing from our standard platform in that you’re isolated to your own network only allowing access to you and your teams. ”
The hackers got an admin’s credentials. That made them one of the “team”. Game Over.
Brian – as someone who works in a Big 4 Firm in the cyber services (not Deloitte) this is a great write up. It’s going to be hard for their Cyber practice to justify their services and offerings. However, at the end of the day this boils down to standard IT General Controls around password settings…
Let’s see how many of the other big 4 are in the same boat, it might just be that they have a good muzzle on the situation or worse yet unable to even know they have been compromised. I highly doubt anyone is immune in this age.
I don’t think anyone is safe. I don’t believe there is or will ever be an end to this. The only way to stop it is to unplug. No hope.
While investigative journalism is good, I think some of the statements provided by your source and publicly published here may impact their ongoing investigation. All of us in the cyber community are waiting for details surrounding the incident – but lets be careful on what to publish.
I completely disagree. Deloitte sat on this to protect their reputation. They owe a complete and open explanation of the impact to their clients. Since they have chosen to not talk to all of their clients we have to rely on people like Krebs to do our own risk analysis of this breach. This appears to be much more significant than Deloitte has admitted to and other businesses need to know what happened.
Worst, if they have not fix GPP issue or not implemented the LAPS in there environment then lateral movement is sky is the limit (might extend to there clients network)
“Source” is obviously insider, provided you with a screenshot. Rules for password reset are actually for internal-use only, it is not a public information, if otherwise not stated in company’s internal procedures. Or, the screenshot is fake. So, one more lesson learned for Deloitte.
How many member-firms use the comprimised environment? Deloitte.com is not limited to the US.
Have a friend who works there who told me they didn’t use two factor authentication. If thats the case this didnt have to happen,
No, D does not use 2 factor authentication.
Larry Quinlan, the CIO, needs to be fired. All things IT falls on his shoulders. This breach falls on him.
Sadly, more and more of these service providers are jumping to the cloud, especially for their email provider, without fully understanding the risks. I’m not sure which email provider they were using, but if it was a cloud provider, on many of them (i.e. Google) you cannot specify dual-factor auth at the enterprise level as a requirement even if you wanted to. When we asked Google about this – they said it was “coming soon” for their enterprise customers, but that was over a year ago…
The real problem is that Deloitte (and many other similar companies) decided to “accept the risk” of these lacking controls in favor of moving to the cloud. Whether they were using a cloud email provider or running their own email on a cloud service – they didn’t take the time to effectively secure their new environment.
deloitte.com has 2 MX records with hostnames that include deloitte.iphmx.com, iphmx.com points back to Cisco cloud email security tech. Cisco is acting as the protector at the email gateway before having to then likely forward email onto internal servers at Deloitte.
Google has had the ability to enforce 2 factor since 2012. https://gsuiteupdates.googleblog.com/2012/06/ability-to-enforce-2-step-verification.html?m=1
This isn’t going to age well.
Now my rant about the big 4: pompous
Check the profiles of these cyber Security experts and most you will find their job experience is in the big 4 echo chamber.
No experience outside of their consultancy vacuum
Not all but most…
Got to love their sophisticated password advice, too:
10, 12, maybe even 16 whole characters! (Leave out the spaces, though, let’s not be crazy!)
“…involves the compromise of all administrator accounts at the company…”
Yet D seems to have a privileged account management solution in place. I wonder if it was breached? Or simply wasn’t used effectively or even deployed?
How do I know they at least have a PAM solution? I looked in the careers section and there was a posting for a specific solution expert for their internal IT group.
Here’s a pen tester that doesn’t skip their reconnaissance. Job postings FTW
Suprised no one has commented on the screenshot verbiage. “really change your password” implies that there might not be a technical mechanism preventing password reuse.
This is saying:
don’t change “passw0rd” to “passw0rd1” or “p@ssw0rd1!”.
If a user is submitting their old password and their new password, it is possible to perform a Levenshtein distance [1] to determine if a password is too similar.
If a user isn’t submitting their old password, and you have a strong hash on the old password, then what you’d have to do is assign resources to defuzz the new password and hash each variant and then check those variants against the old hashed password. It isn’t impossible, but it’s definitely computing power. — Instead, they’re asking their employees (who are contractually bound to honor such requests) to play nice, some won’t, but they do risk a lot if something bad happens because of it and they’re later discovered to have cheated.
Note: while one could fuzz and store all the variants, to some extent, storing lots of variants may make it easier for someone to find a match and thus work backwards to a password. (The password in such a case isn’t useful for the specific system, but is useful when it’s reused by the user elsewhere.) As such, it isn’t really a good idea to store all of these.
Personally, I’d rather users be issued smart cards w/ proper PKI, and use a 2FA system.
I’d also encourage everyone to move away from short passwords to very long passwords and password manager managed passwords (32+ characters would be good).
I’m not going to claim that my security is perfect (far from it). I’m sure someone could hack me if they wanted to. Anyone who thinks they aren’t hackable is asking for trouble.
[1] https://en.wikipedia.org/wiki/Levenshtein_distance
As a pentester/auditor, I’ve seen so many organizations send new account passwords via email. Even for accounts with elevated privileges to applications. So it doesn’t surprise me to hear they aren’t sure if they’ve entirely cleaned their networks.
Email servers aren’t the keys to the kingdom, but it is many flies on the wall to get to the keys.
Read an email, get the password and use it before the real user. When the real user finds it doesn’t work, they simply ask for a reset, but by then (if the account is elevated), the hacker has created their own account and is off and rolling. Perhaps even reset the password to the original.
It only takes time and patience to get an elevated privilege account. Especially with a large corporation, who has many of them.
Imagine sending passwords in plain text comms over email and with the username? LMAO!!!
We all know that have the same exact vulns as Deloitte and can be pwned exactly the same way. Most such companies do not have strong 2-factor authentication, services and data have been moved to one of the big cloud service providers and many critical functions have been outsourced to the cheapest option. There is usually weak security monitoring in place, if any, and even if something out of the ordinary was detected, there is no response mechanism and process implemented.
Companies spend millions on crappy blinky appliances that claim to defend against the next 0-day. Meanwhile basic controls, such as network segmentation, security patching, basic hardening of platforms is not happening. It is not a question if but when pwnage will be discovered.
Usually by some third party and not internally. Most large companies do not even know where there data is anymore or have trouble creating a simple model of their business, required for basic security risk assessment and threat modeling. These sort of hacks (Deloitte, Equifax, OPM, etc) will keep coming thick and fast in the foreseeable future since there is large digital debt that will be cashed in by attackers and miscreants.
When I worked at Deloitte, about 10 years ago, we used RSA keys. I can’t believe that they would drop 2FA. Was this a bean counting decision?
2fA is a nuisance and slows productivity.
Hacks are just part of the cost of business, but less costly than the loss of productivity of 2fA.
If you worked there, you should know profitable business is not just maximizing profit… it’s also minimizing expenses, including obstacles to productivity.