Big-three consumer credit bureau Equifax says it has removed third-party code from its credit report assistance Web site that prompted visitors to download spyware disguised as an update for Adobe’s Flash Player software.
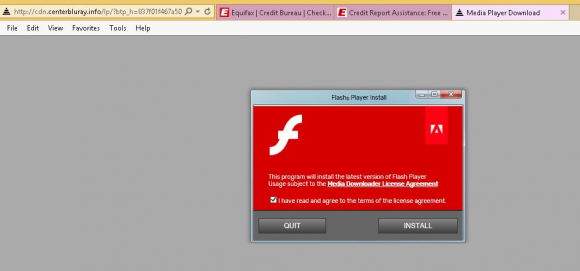
Image: Randy-abrams.blogspot.com
On Wednesday, security expert and blogger Randy Abrams documented how browsing a page at Equifax’s consumer information services portal caused his browser to be served with a message urging him to download Adobe Flash Player.
“As I tried to find my credit report on the Equifax website I clicked on an Equifax link and was redirected to a malicious URL,” Abrahms wrote. “The URL brought up one of the ubiquitous fake Flash Player Update screens. ”
Ars Technica’s Dan Goodin was the first to cover the discovery, and said the phony Flash Player installer was detected by several antivirus tools as “Adware.Eorezo,” an intrusive program that displays advertisements in Internet Explorer and may install browser toolbars and other unwanted programs.
Several hours after Goodin’s piece went live, Equifax disabled the page in question, saying it was doing so out of “an abundance of caution” while it investigated the claims.
In a follow-up statement shared with KrebsOnSecurity this afternoon, however, Equifax said the problem stemmed from a “third-party vendor that Equifax uses to collect website performance data,” and that “the vendor’s code running on an Equifax Web site was serving malicious content.” Equifax did not say who the third party vendor was.
“Since we learned of the issue, the vendor’s code was removed from the webpage and we have taken the webpage offline to conduct further analysis,” reads the statement. “Despite early media reports, Equifax can confirm that its systems were not compromised and that the reported issue did not affect our consumer online dispute portal.”
That closing line of Equifax’s statement may do little to assuage a public that has grown increasingly weary of Equifax’s various security and public relations failures since it announced on Sept. 7, 2017 that hackers broke into the company’s servers and stole Social Security numbers and other sensitive data on more than 145 million Americans.
On Sunday, KrebsOnSecurity published a story warning that Equifax’s payroll and tax administration site made it simple to access detailed salary and employment history on a large portion of Americans using little more than someone’s Social Security number and date of birth — both data elements that were stolen in the recent breach at Equifax. Equifax disabled that service just hours after the story ran, replacing it with a message stating the site was under maintenance. Four days later, that site remains offline.




Poor Equifax. This company need more professionalism
Poor Equifax?????!!!!!!!
Poor those who suffer the consequences of its negligence.
Equifax CEO just retired with 90mil.
My greatest fear in all this is that Equifax stock does not suffer permanent loss over all this serious lack of security.
All these security failures are exactly what we spend countless hours and enormous number of dollars trying to prevent. But if there are no long or even medium term financial consequences for this then I can see our security budget getting taken out back and shot at a future board meeting.
If equifax stocks recover soon then the next company with a security breach and stock drop will be just another “great buying opportunity”.
Their stock will not suffer as long as they have money-stream projects like the no-bid contract with the IRS.
Remember that consumers (a.k.a. “the product”) are not Equifax’s customers.
I wonder who was the third-party.
Doesn’t anybody have a capture of the html they had on the site from a few days ago? Should be easy to make a diff and see what changed…
More info on source of malware – a defunct software product and a bad guy picking up a released URL registration!
https://www.wsj.com/articles/equifaxs-latest-security-foil-a-defunct-web-service-1507937742
“Equifax was still using a defunct web analytics plugin called Fireclick which had since been taken over by scammers.
Malwarebytes Corp. researchers investigated the matter and discovered that Digital River, the company which made Fireclick, discontinued the service in mid-2016 and subsequently released the Netflame.cc domain where it was hosted. That domain was subsequently acquired by scammers and used to host “fraudulent online surveys, adware and software designed to steal online-banking credentials,” Malwarebytes analyst Jerome Segura told the Journal, adding that he had discovered a similar security hole on competitor TransUnion’s Central American site.
According to the paper, the likeliest explanation is Central Source LLC, a joint venture between Equifax and TransUnion to run annualcreditreport.com which had a Fireclick contract which expired in May 2014.”
https://gizmodo.com/equifaxs-website-redirected-people-to-malware-thanks-to-1819474245
1. Is annualcreditreport.com safe?
2. Yes, Equifax is at fault. But also worth noting that Digital River was too cheap to protect their customers by spending a few bucks per year to renew that old domain name.
“We’re the accountability people. Everything from our advanced commerce cloud to our full-service solutions is designed to ensure risk-free global ecommerce.”
https://www.digitalriver.com
“Segura [of Malwarebytes] browsed to the affected TransUnion site several times, first getting redirected to a survey scam, then to a bogus Flash Player update and finally to the RIG exploit kit. While display advertisements weren’t a part of the TransUnion situation – the key component for malvertising – Segura says known malicious ad networks and exchanges were involved in the redirections.
It appears that attackers have compromised the third-party library. Corrupting such libraries is a powerful way to affect many sites. The service Segura used that led to TransUnion’s problematic website probably showed more than 1,000 others using the same library.”
https://www.bankinfosecurity.com/equifax-transunion-websites-served-up-adware-malware-a-10379
This is the part that just kills me sometimes. It’s not always the websites that are compromised, it’s the third party ad networks who don’t vet their advertisers and/or disable the malicious script based attacks.
They just serve the content, collect the money, and who cares what kind of crap they’re serving out.
That’s not the case here though. The third party wasn’t responsible, they could have continued to license that domain to avoid a malicious actor using it, however their service agreement with Equifax was long expired and Equifax, as usual, was too damn negligent to remove the code which interacted with that domain. For more than a year they were running an analytics script that communicated with a service that had been taken offline.
Again, the third party didn’t do a good job here but they’re certainly not responsible. Also, basic user level testing (meaning this can be conducted by non-technical manual testers, rather than actual engineers) would have revealed this problem. I mean, it’s in the happy path. Most places with decent engineering practices would catch this very quickly and further more, they would have the competence to avoid it in the first place by removing HTTP calls to services they no longer pay for when the contract’s term ends rather than leaving around old code.
To fly back out and look at this at a higher level, here’s basically what happened… One day there is a legit service at myservice.com, after a few years that service is no longer offered, people who used the service added JavaScript to their pages which made HTTP requests to myservice.com. The service is no longer offered, after that the domain is released and becomes available on the open market. Once this happens a malicious actor purchases the domain and puts malicious software there which takes advantage of people like Equifax that haven’t bothered updating their site in a year and still have old code from the once legit service which calls myservice.com. The third party, myservice.com is clearly in no way accountable here. Any non-negligent organizations would have removed the script from their sites prior to the contract ending, and even negligent ones would have cleaned it up after the fact but in less than a year after the fact. It’s like you left a ton of trash in your car for a year then complained that mold grew on your seats. Obviously it’s not the fault of the car seats, it’s your fault for leaving the trash there for a year.
+1
Buying LinkedIn Endorsements, Connections and Followers, is truly the latest way for boosting your professional identification. To know a few guidelines concerning this keeps on reading this article.
Got to be concerned how many of these companies have the same lousy level of security as Equifax? I find that even with several high profile examples of stupidity. This stuff keeps happening. Is anyone learning by example?
If lulzsec didn’t get that across with all their defacing and script kiddie pranks in 2011, i’m not sure anything will.