Big-three consumer credit bureau Equifax says it has removed third-party code from its credit report assistance Web site that prompted visitors to download spyware disguised as an update for Adobe’s Flash Player software.
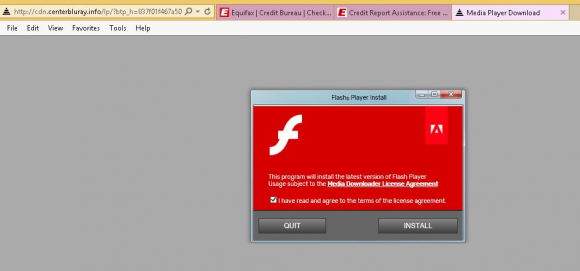
Image: Randy-abrams.blogspot.com
On Wednesday, security expert and blogger Randy Abrams documented how browsing a page at Equifax’s consumer information services portal caused his browser to be served with a message urging him to download Adobe Flash Player.
“As I tried to find my credit report on the Equifax website I clicked on an Equifax link and was redirected to a malicious URL,” Abrahms wrote. “The URL brought up one of the ubiquitous fake Flash Player Update screens. ”
Ars Technica’s Dan Goodin was the first to cover the discovery, and said the phony Flash Player installer was detected by several antivirus tools as “Adware.Eorezo,” an intrusive program that displays advertisements in Internet Explorer and may install browser toolbars and other unwanted programs.
Several hours after Goodin’s piece went live, Equifax disabled the page in question, saying it was doing so out of “an abundance of caution” while it investigated the claims.
In a follow-up statement shared with KrebsOnSecurity this afternoon, however, Equifax said the problem stemmed from a “third-party vendor that Equifax uses to collect website performance data,” and that “the vendor’s code running on an Equifax Web site was serving malicious content.” Equifax did not say who the third party vendor was.
“Since we learned of the issue, the vendor’s code was removed from the webpage and we have taken the webpage offline to conduct further analysis,” reads the statement. “Despite early media reports, Equifax can confirm that its systems were not compromised and that the reported issue did not affect our consumer online dispute portal.”
That closing line of Equifax’s statement may do little to assuage a public that has grown increasingly weary of Equifax’s various security and public relations failures since it announced on Sept. 7, 2017 that hackers broke into the company’s servers and stole Social Security numbers and other sensitive data on more than 145 million Americans.
On Sunday, KrebsOnSecurity published a story warning that Equifax’s payroll and tax administration site made it simple to access detailed salary and employment history on a large portion of Americans using little more than someone’s Social Security number and date of birth — both data elements that were stolen in the recent breach at Equifax. Equifax disabled that service just hours after the story ran, replacing it with a message stating the site was under maintenance. Four days later, that site remains offline.




Oh god, just make it stop. these daily f-ups by Efax became so annoying. It’s like watching DJT Tweeter feed; Every day you open the news hoping the world is still there. we just want some peace. and our identities to be secured…
E-Fax Get a WAF!
Things are not looking good for Equifax
Hey no worries re their payroll and tax site. The message says if you come back “tomorrow”, they’ll have everything updated.
But it looks like that message has been there for a while. Say, you don’t suppose Equifax isn’t being any less than 100% honest and forthcoming about that status, do you??
I hate to see people lose their jobs, but this company needs sued out of existence.
I cannot believe my eyes!!!
What else Equifax has to do to get some of it’s managers in a trial or closed for good?
Here in Spain things are not much different, but, USA’s supposed to be different… 🙁
Third party code. Faulty scanner. Lousy security tech making human error. All these externalities to blame. Why, I’m half-expecting former CEO Richard Smith to release a tell-all blame-all book “What Happened (at Equifax)?” and go on a speaking tour.
Not exactly the example of accountability and competent cyber governance, are they?
Equifax has the worst communications/PR department in the world. Not their fault because it was a third party performance data collector? You really can’t make that up. Translation – our third party tracker/data slurper was compromised and we had no idea.
Why was there a third party plug-in running on a security sensitive site? What data are they collecting?
Next time I get in a car accident I’m going to blame my Nike shoes which I have no control over.
These guys are amazing.
This is outsourcing for you. It’s not about saving money, it’s about outsourcing risk and blame.
So – right off? FIRE the 3rd Party Vendor. This isn’t an EBAY Sales Site – theoretically.
Will someone please tell Equifax about “integration testing”. The whole argument “but my code works”, or ” that’s not my code” just makes you look like an idiot.
If you include it, you’re responsible for it. Adding third-party analytics code is OK. Not know what is does is not OK. And not testing it along with your code, (hint: Integration testing) is just f-ing stupid. This should have been caught, easily, before it went live.
Integration testing does not detect fraudulent scripts from 3rd parties. Sure, the initial script passes initial inspection. But later the criminals insert the script on 1 of N visitors to slow detection.
I’d like to know who the 3rd party was who was compromised. The implication is that many other sites were service the malicious script via this same statistics vendor.
Moike: “The implication is that many other sites were service the malicious script via this same statistics vendor.” <—–THIS!*!*!*!*!*!
Efax probably follows flawed “devops” concepts that say, “It compiles? SHIP IT!”
When I worked around financial services customers, all of their staff were “major big time” into testing and retesting before placing anything into “production”.
Sometimes it pays to “move slower”, be very careful, and even consider doing most if not all tasks “in house” where you have greater control over everything compared to using 3rd parties and being limited by contractual language.
Slow is smooth, and smooth is fast
I work in the IT security field so I do indeed understand the seriousness of this whole debacle. But honestly, for that very same reason, I’m starting to find it laughable. How much worse can this company f-up? I don’t want them to make even another nickel off of my information.
They need to be shutdown. Today. All that have used their services in the past – for credit granting, employment, anything at all – need to stop using them. Today.
And the hits just keep coming. At this point there is no excuse for Equifax’s continued access to my (and millions of others) personal PII.
Time to send the entire company’s database to the shredder.
Forever.
Just when you thought it couldn’t get any worse….
And it burns, burns, burns…. the dumpster fire….
Equifax practices “Waterfall” approach — Their reputation went over the waterfall in a barrel.
EXTRA, EXTRA, hot off the presses!
“The IRS has temporarily suspended a contract it awarded to Equifax, following reports that the company suffered a second data breach, Politico reports. … According to Politico, the IRS will continue reviewing Equifax’s security systems during the suspension.”
http://thehill.com/blogs/blog-briefing-room/355247-irs-suspends-equifax-contract-report
Still waiting to see if someone/country starts releasing the hacked data. Should create a nice mess, especially if they do so just before the start of the holidays.
“Gee, I thought I only spent $300 on Xmas presents, why is my CC statement showing $3000?!?”
Wait till you file your tax return and the IRS tells you it will now take 10-12 months to process, only to find out at month 12 that someone else already requested your tax refund and it’ll take another 12 more months of investigating by the IRS before they will cut you your refund check.
If the corporate execs who sold their stock just before the announcement had turned around and sold short, they could have added another 40% to their pockets.
…and another 20+ years to the prison sentences they would have gotten by such flagrant evidence they knew something about the impending nature of bad news for the company’s stock price.
The company itself is pretty desperately trying to push the argument that the individuals did not know of the breach and were just cashing out of previously-granted stock options as a routine rebalancing of their personal portfolios. That defense will undoubtedly be tested severely in the investigations by the FTC, Congress and various states’ Attorney-Generals. Selling short would have been a dead giveaway for their having knowledge and preclude any viable opportunity for the company to use lack of knowledge in its own defensive strategy.
Its worse. TransUnion hacked as well:
https://arstechnica.com/information-technology/2017/10/equifax-rival-transunion-also-sends-site-visitors-to-malicious-pages/
Equifax to consumers: “No, our systems weren’t compromised — only a 3rd party Javascript provider was compromised … running code on your system. Not our system.”
By this point, I wouldn’t be surprised if Equifax started to run Bitcoin mining — via 3rd party Javascript of course.
Wittingly or unwittingly? Who cares.
Equifux
+1 (with a bullet!)
Remember. Follow the money.
Should never have trusted E to protect us. We aren’t their customers. The banks are.
You aren’t hearing about problems with security to/from the banks, are you? No. Only the public-facing systems have problems.
We, us, don’t matter to Equifax. There are more than enough of us to keep them funded. From the banks.
Be real and knowing about “follow the money” going forward.
You make a very good point, we aren’t the customer, we are the product.
What’s incredible here is that in order to protect ourselves, we have to pay. So the product pays for protection for the product’s security, and the actual customer (the banks) pay for access to the product.
Equifux and the other credit bureaus have positioned themselves quite nicely to not only get paid from the customer, but also paid from the product! Incredible! What other company can say that?
I think it is overdue for Equifax to be subjected to an Internet Death Penalty. Equifax, any subsidiaries, and any parent businesses, must be permanently banned from having any access to the Internet or any other public communication networks.
Add the EFF’s Privacy Badger extension to Chrome, Firefox, or Opera. Then go to the homepage of any company. Privacy Badger lists all the analytic tools and tracking junk that is running on the webpage. One or two trackers like google-analytics.com are necessary. But many financial companies have a couple of dozen, most with names you have never heard of. These unnecessary services are a huge hazard for any company, especially a financial company.
https://www.eff.org/privacybadger
(This site has only two gadgets, neither one of which is tracking you.)
State sponsored attacks on our credit system? Imagine all of the data stolen from Equifax and who knows where else being suddenly used in an automated compromise of 150 million (or whatever the count is now) people. It doesn’t matter if the compromises succeed, just that the attempts are detected and the reaction that would bring. Also, what if state-sponsored hackers stole via hacks from the sites that sell them the millions(?) of stolen credit card numbers that are never sold and are, therefore, never detected as compromised and also used them in an rapid, automated compromise?
And this is why I run No Script. It’s not about blocking adds but stopping the harvesting of my information, saving CPU cycles (thus battery life), and protecting my system from compromise.
“And this is why I run No Script.”
You must not be using the latest version of Firefox, since it it incompatible with NoScript. No date in sight for providing compatibility.
NoScript is too crippling. I run ABP and RequestPolicy, a better balance in my opinion, and few sites complain about “ad blockers”. Those sites that complain I abandon– it is too hard to tell if those complaining sites are duly diligent about verifying their advertisers are not serving up malware.
“Despite early media reports, Equifax can confirm that its systems were not compromised and that the reported issue did not affect our consumer online dispute portal.”
…But (hee, hee) it may have affected our consumers systems, you know the people who we could care less about. More importantly the money we received from this 3rd party spyware company will help us defray the costs associated with our other screw-ups.
Que up the Yackety Sax background music!!!
And put it on repeat mode until further notice.
Having worked for a large company that provided services to banks and other financial services firms, I experienced first hand that these firms normally stand ready to terminate their contracts if their service providers have a significant security failure. Since Equifax is a service provider to banks and other financial institutions and this has been a security debacle of the highest order, I absolutely do not get how the banks do not seem to be making any moves to terminate their relationships with Equifax. I agree with a previous comment that Equifax should be shuttered…they clearly have not made security a priority and nobody seems to be holding them accountable.
It’s good to know that that marvelous thing known as the invisible hand of a free and unfettered free market has done it’s thing once again in putting Equifax out of business.
Hey VC types and Entrepreneurs, this is the perfect opportunity for disruption. All three of these Credit Reporting Agencies are based on the same model. It should be possible to create a new model where the consumer is a participant (not a bystander) in allowing access to the credit history. It should have multiple layers of encryption, any requests for credit should be able to be authorized by the consumer. If this is created, and gets a foothold, it could replace all three of these companies.
Michael I like that thought if you can get all the suppliers of the info and purchasers of the credit reports to trust the new product.
Different credit reports serve different niches and not all creditors provide payment info to all the credit reporting agencies. The utility company may report payment history to a different agency than the cell phone payment history. What worked well for these long established agencies (and helped us consumers obtain credit instead of paying deposits or pre-paying here and there) wasn’t given sufficient vision when the world started going digital. They totally failed to give sufficient consideration to the bad guys… like Congre$$ continuously fails to be forward thinking about consequences.
These agencies figured out ways to further monetize their business… directly with consumers in order to satisfy management and Wall Street demands. Lots of blame to go around here. How could Smith have best measured the competency and abilities of IT staff ? What % of any budget is considered reasonable for equipment and securing data?
Whoever takes up your disruption challenge needs to get input from lots of different players and angles.
They should just change the company name to “Equi-Lax.”
It is important to note that many web sites pull JavaScript from shared sources. Example: jQuery. If the shared source gets compromised, many web sites will be affected instantly.
If your web site needs to be secure, never pull scripts from outside of your control. Never.
For example, if Google analytics gets hacked and someone inserts JavaScript to grab all user id and password values from any page on which they are keyed and send them to some database, you would never know.
Do not use shared JavaScript if you want your site to be secure. Copy the script into your site and manage updates manually.
As a user, rather than website developer, I love that so many intrusive, obnoxious Javascript files are centralized.
So many sites run the same ad scripts, tracking scripts, and analytics scripts.
And running them from third party locations makes those scripts easier for a novice like me to find… and block.