For the second time in as many years, hackers have compromised Verticalscope.com, a Canadian company that manages hundreds of popular Web discussion forums totaling more than 45 million user accounts. Evidence of the breach was discovered just before someone began using that illicit access as a commercial for a new paid search service that indexes consumer information exposed in corporate data breaches.
Toronto-based Verticalscope runs a network of sites that cater to automotive, pets, sports and technology markets. Verticalscope acknowledged in June 2016 that a hacking incident led to the siphoning of 45 million user accounts. Now, it appears the company may have been hit again, this time in a breach involving at least 2.7 million user accounts.
On Thursday, KrebsOnSecurity was contacted by Alex Holden, a security researcher and founder of Hold Security. Holden saw evidence of hackers selling access to Verticalscope.com and to a host of other sites operated by the company.
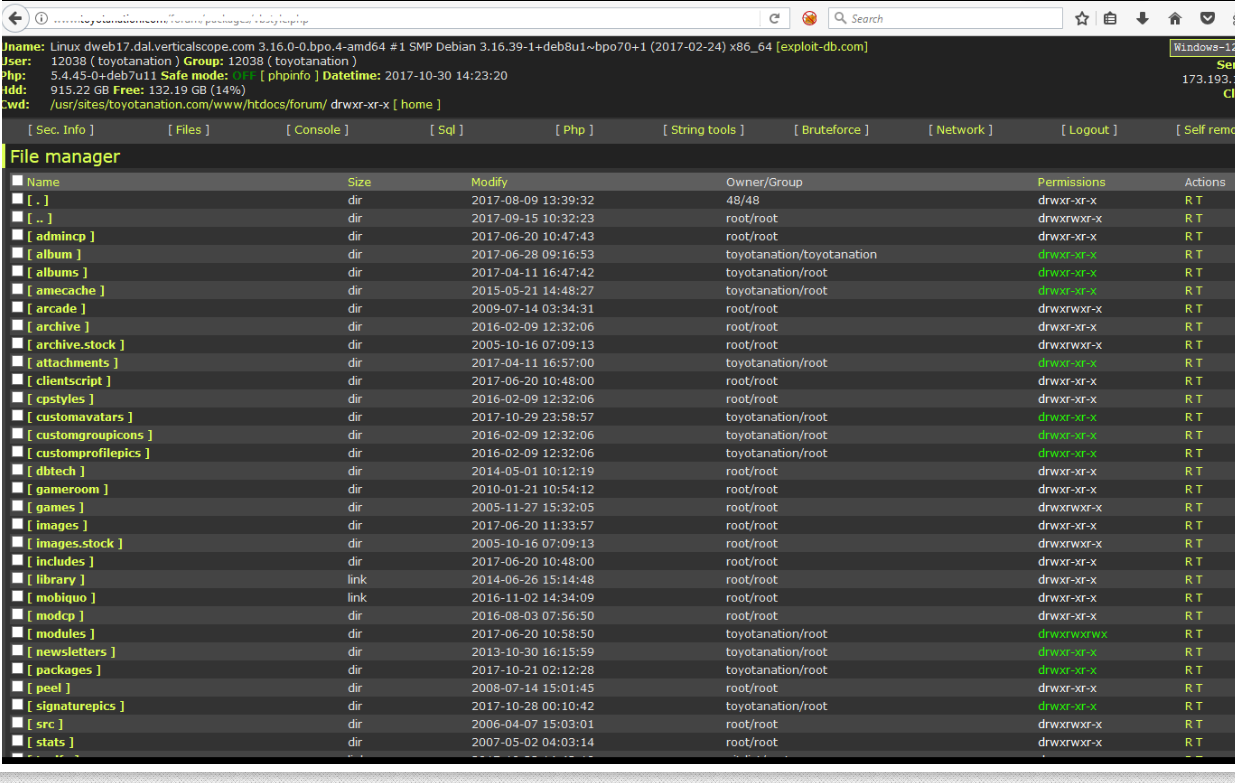
Holden said at first he suspected someone was merely trying to resell data stolen in the 2016 breach. But that was before he contacted one of the hackers selling the data and was given screen shots indicating that Verticalscope.com and several other properties were in fact compromised with a backdoor known as a “Web shell.”
With a Web shell installed on a site, anyone can remotely administer the site, upload and delete content at will, or dump entire databases of information — such as usernames, passwords, email addresses and Internet addresses associated with each account.
Holden said the intruders obfuscated certain details in the screenshots that gave away exactly where the Web shells were hidden on Verticalscope.com, but that they forgot to blur out a few critical details — allowing him to locate at least two backdoors on Veriticalscope’s Web site. He also was able to do the same with a second screen shot the hackers shared which showed a similar backdoor shell on Toyotanation.com, one of Verticalscope’s most-visited forums.
Reached for comment about the claims, Verticalscope said the company had detected an intrusion on six of its Web sites, including Toyotanation.com.
“The intrusion granted access to each individual website files,” reads a statement shared by Verticalscope. “Out of an abundance of caution, we have removed the file manager, expired all passwords on the 6 websites in question, added the malicious file pattern and attack vector to our detection tools, and taken additional steps to lock down access.”
Verticalscope said the other forums impacted included Jeepforum.com — the company’s second most-popular site; and watchuseek.com, a forum for wristwatch enthusiasts.
Verticalscope admitted a breach in 2016 after their forum users’ data was outed in a blog post on Leakedsource.com, a now-defunct service that sold access to username and password details stolen in some of history’s largest data breaches.
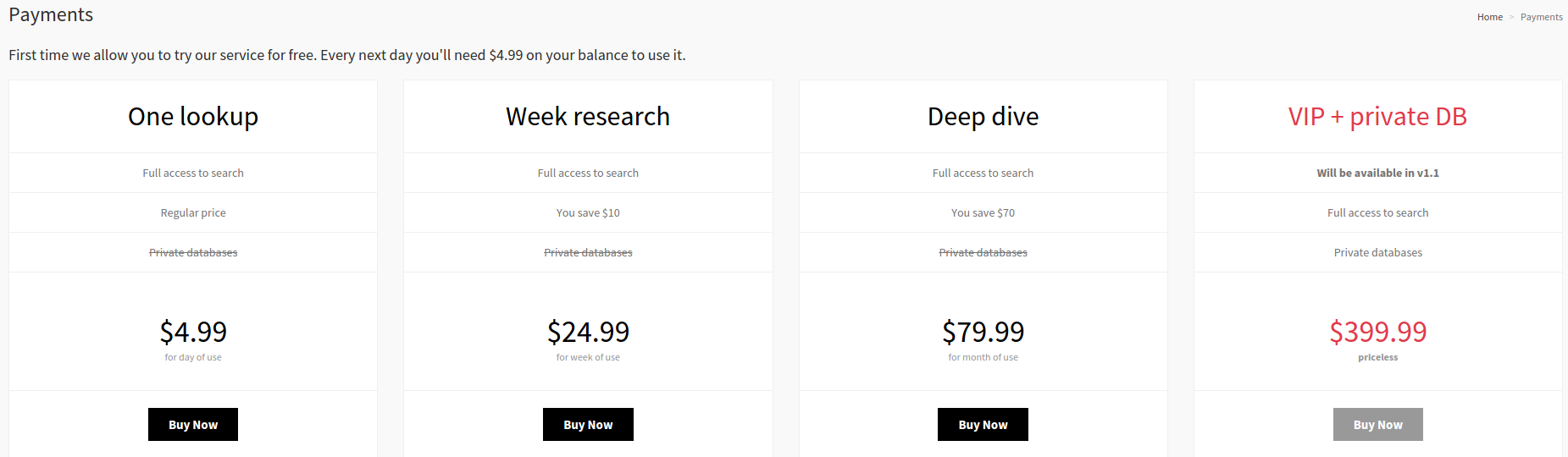
An Internet search on one of the compromised Verticalscope domains leads to a series of now-deleted Pastebin posts suggesting that the individual(s) responsible for this hack may be trying to use it to advertise a legally dicey new online service called LuiDB.
Similar to Leakedsource, LuiDB allows registered users to search for account details associated with any data element compromised in a breach — such as login, password, email, first/last name and Internet address. The first search is free, but viewing results requires purchasing a subscription for between $5 and $400 in Bitcoin.
People who re-use passwords across multiple Web sites tend to be those hardest-hit by these breaches, and by these dodgy password lookup services. It may not seem like a big deal if someone chooses to re-use the same password across a range of sites that don’t ask for or store your personal data, such as discussion forums. The problem is that this encourages poor password habits, and for many folks this eventually results in using that forum password at more important sites that do store sensitive data.
In practice, there’s no reason people should ever re-use the same password. Password managers can help users pick and remember unique, strong passwords for all sites that require a login; all the user needs to do is remember a single “master password” to unlock all the others. Old schoolers like Yours Truly tend to stick to local password managers like Keepass (or even PwdSafe), although many folks I admire in the security industry rely heavily on cloud-based password managers like LastPass and Dashlane.
While few online discussion forums offer two-factor or multi-factor authentication (requiring you to log in using a password and a one-time code, e.g.), a great many services do offer this very effective security measure. Check out twofactorauth.org to see if there are online services you use that could be furthered hardened by turning on two-factor authentication.




My institution requires identical passwords on 4 different areas run within its domain. The areas are Network login, email login, electronic learning module, and work order for a computer problem. Security problem do you think?
Chris, Brian isn’t advocating that every password be different. He’s advocating that different passwords be used at different websites. The fact your institution admins are using SSO for different services inside the domain they control doesn’t indicate a security issue, it indicates they are trying to keep their end users from driving them insane with password reset requests.
Chris may be trying to point out a subtle risk factor regarding SSO.
By using SSO or RSO practices, an organization is essentially putting all (or majority) of the accesses for a given user under a single credential. This can definitely pose a different risk factor for users with broad accesses across an enterprise that is implementing SSO or RSO practices.
Every enterprise owner should be attempting to reduce the number of credentials involved with systems operations for multiple reasons. There is no dispute there
However, for those organizations that are implementing SSO/RSO practices, I believe it is also important that they look at applying stronger or more aggressive security practices to the credentials involved (eg. multi-factor authentication, aggressive session management, etc).
Using SSO across network login, email, training system, and request system in an enterprise environment is mostly a non-issue (unless the user is actually managing one of those systems). Access control is managed through a third-party via tickets and session keys. The user doesn’t just have access to all of those systems – the user requests access to a resource and the resource checks if it’s a valid request.
It would be nice if there was a web service that could do this. Facebook has a logon feature if a website integrates it, but that typically comes with sharing a lot of information between Facebook and the website. A KDS, on the other hand, doesn’t care about what you’re doing after accessing a resource, just if you’re allowed to access it.
Good article
Looks like both Keepass and PwdSafe are not available for OSX.
Brian, any OSX recommendations?
@Mac
I use keychain for all my passwords.I create a keychain entry which holds the account name and password. I use only one computer and don’t tend to do much with mobile devices so I keep the keychain local. If I used several devices then I would probably use iCloud to keep the keychain. If an account requires security questions then I create a somewhat random string of characters (long strings of gibberish that I type) as the “answer” to that question and store the string along with the question in the comments section of the kcychain entry which contains the account name and password.
Its a bit of a pain, but has worked for years.
I have a few master passwords that I have memorized.
There are KeePass ports for OS X.
KeePassXC and KeePassX to name two.
I didn’t encounter any problems with the latter, but switched to XC because it’s more actively maintained.
KeePass (keepass dot info) does indeed support Mac and there is 3rd party support for Android.
Mac: Take a look at 1Password by Agile Bits. I don’t work for them but am a happy user of their product for several years now.
iCloud Keychain.
– iCK is free and built into every Apple device from the factory;
– has a built in p/w generator that creates a default p/w of the form xxx-xxx-xxx-xxx, where x=aA1. On many sites that don’t allow the hyphens, if configured properly, iCK recognizes this and proposes a p/w w/o them;
– has been expanded in iOS 11 to also put p/w’s into apps as well as sites browsed on Safari;
– is encrypted before being sent to iCloud for sync to all your other Apple (only) devices and storage there;
– I’m pretty sure that a) Apple has the resources to do a good job on this feature, and b) if they bungle it and this data were breached in any way, it be in the news everywhere so one could timely change their p/w’s;
– it is easy on both Mac and iOS to get into the Keychain to see domain, u/n and p/w info. In addition, on Mac, via the built-in KeyChain Access (in utility folder on desktop), one can access more granular info like date-stamps for each authentication key, etc.;
– it is also possible on the Mac to change p/w parameters to generate longer or different form p/w (but I’m unsure if the settings are then synced back out to your iOS devices as I never bothered to check for this opportunity);
– it doesn’t have all the bells and whistles of the paid p/w managers but is nicely integrated into both Safari and iOS apps and works well almost all the time (occasionally a newly generated p/w is not saved to the iCK and you will have to do a reset, generate another p/w, take a pic or note the new p/w, and then either manually create the key in iCK tool, or just login to the site with the info and the iCK will save it that way);
– given the emergence of FaceID technology, it could be there are advantages to using iCK although some 3rd Party p/w managers have already upgraded to make use of FaceID.
We are using this throughout our family and several friends and I hear no complaints about it. As a result, one need not maintain a p/w list, nor know any of their p/w’s with the exception of their ApoleID p/w. Theoretically, one could also use a randomized p/w for their AppleID but since we also use it for our screen unlock codes (this so my mom can keep it fresh in her mind).
I hope this helps!
Regarding Security Q&A, I have asked Apple to expand the functionality of the Keychain feature to allow the storage of these and other useful via their feedback website; maybe one day! In the meantime, I store them in the notes section of a contact card (admittedly low tech and not as secure as if in an p/w manager, but vastly superior to using/reusing true (or bogus) answers across multiple sites.)
I use mostly Password Gorilla which I can use on Mac and also under my Live Linux CD with a usb stick or in a directory on the HDD. It also works on windows. It is more spartan looking than KeePassX but works on all three platforms.
I also use both KeePassX that uses version 1.x .kdb files which I can use with KeePass 1.x on Windows. I have not gotten KeePassX to work with my live distro of choice and thus this is why I mostly use Password Gorilla. I hope to try KeePass under WINE sometime to see f that would work.
I plan to checkout KeePassXC soon.
You’re absolutely correct that passwords should never be re-used anywhere else. I always make sure my clients are aware of this simple fact. Unfortunately a lot of people are slow at changing their passwords, and reluctant to try something new (like a secure password manager).
Keep up the great work Brian!
Steve Gibson & I use Lastpass.
Good article..
Hi Brian,
In the article VerticalScope claimed that they detected the breach. Did they give any indication as to whether this was before or after Alex had been in contact? Looking at various forums, it suggests they made configuration changes and reset passwords on the 2nd of November to a small number of sites.
Do we know when Alex had contacted them with this information? Does Alex have any idea as to when this might have originally occurred?
Which are the 6 websites that were breached?
Previously, I was notified by them when several of them were breached.
This time round, I am not notified by them. Can I assume that I’m not affected?
They were:
toyotanation.com
jeepforum.com
watchuseek.com
diychatroom.com
pbnation.com
hystersisters.com
Thank you!
Brian,
I have the niggling feeling that the last time VerticalScope breached that they didn’t immediately disclose the breach (or the extent of it). Do you recall this too?
I don’t have an account on any of the sites in your list, but I do on a different VS site. After seeing this post, I logged in there and was not presented with any request to change my p/w.
Just to be safe, I changed my p/w using the p/w generator on the site. (in this case, the iCloud keychain didn’t offer a suggestion, but the offered p/w from VS was super complex.
If my recollection above is correct, but also even if now, I’d recommend anyone with a VS account change their p/w just to be safe (because all old rabbits have seen by now how some site operators are often not aware of the extent of a breach, or even if they are, have been known to suppress this information until they are caught having done so.
The best, most secure, and cheapest password store I’ve found to date is LibreOffice Calc. I create a spreadsheet that contains the password/account combinations then encrypt that with a strong password. You must use a strong password, thought, to prevent CUDAHashCat and John the Ripper type attacks.
See the caveats at https://passwordrecovery.io/
Brian,
The date on your articles is showing as Nov 17. Might want to look into that.
The big number is the day.