Take care when typing a domain name into a browser address bar, because it’s far too easy to fat-finger a key and wind up somewhere you don’t want to go. For example, if you try to visit some of the most popular destinations on the Web but omit the “o” in .com (and type .cm instead), there’s a good chance your browser will be bombarded with malware alerts and other misleading messages — potentially even causing your computer to lock up completely. As it happens, many of these domains appear tied to a marketing company whose CEO is a convicted felon and once self-proclaimed “Spam King.”

Matthew Chambers is a security professional and researcher in Atlanta. Earlier this month Chambers penned a post on his personal blog detailing what he found after several users he looks after accidentally mistyped different domains — such as espn[dot]cm.
Chambers said the user who visited that domain told him that after typing in espn.com he quickly had his computer screen filled with alerts about malware and countless other pop-ups. Security logs for that user’s system revealed the user had actually typed espn[dot]cm, but when Chambers reviewed the source code at that Web page he found an innocuous placeholder content page instead.
“One thing we notice is that any links generated off these domains tend to only work one time, if you try to revisit it’s a 404,” Chambers wrote, referring to the standard 404 message displayed in the browser when a Web page is not found. “The file is deleted to prevent researchers from trying to grab it, or automatic scanners from downloading it. Also, some of the exploit code on these sites will randomly vaporize, and they will have no code on them, but were just being weaponized in campaigns. It could be the user agent, or some other factor, but they definitely go dormant for periods of time.”
Espn[dot]cm is one of more than a thousand so-called “typosquatting” domains hosted on the same Internet address (85.25.199.30), including aetna[dot]cm, aol[dot]cm, box[dot]cm, chase[dot]cm, citicards[dot]cm, costco[dot]cm, facebook[dot]cm, geico[dot]cm, hulu[dot]cm, itunes[dot]cm, pnc[dot]cm, slate[dot]cm, suntrust[dot]cm, turbotax[dot]cm, and walmart[dot]cm. I’ve compiled a partial list of the most popular typosquatting domains that are part of this network here (PDF).
KrebsOnSecurity sought to dig a bit deeper into Chambers’ findings, researching some of the domain registration records tied to the list of dot-cm typosquatting domains. Helpfully, all of the domains currently redirect visitors to just one of two landing pages — either antistrophebail[dot]com or chillcardiac[dot]com.
For the moment, if one visits either of these domains directly via a desktop Web browser (I’d advise against this) chances are the site will display a message saying, “Sorry, we currently have no promotions available right now.” Browsing some of them with a mobile device sometimes leads to a page urging the visitor to complete a “short survey” in exchange for “a chance to get an gift [sic] cards, coupons and other amazing deals!”
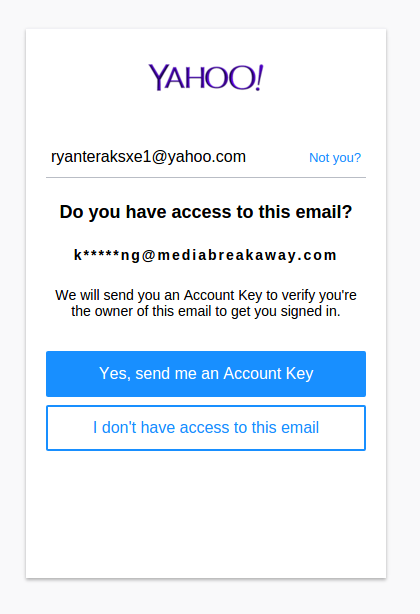
Those antistrophebail and chillcardiac domains — as well as 1,500+ others — were registered to the email address: ryanteraksxe1@yahoo.com. A Web search on that address doesn’t tell us much, but entering it at Yahoo‘s “forgot password” page lists a partially obfuscated address to which Yahoo can send an account key that may be used to reset the password for the account. That address is k*****ng@mediabreakaway[dot]com.
The full email address is kmanning@mediabreakaway[dot]com. According to the “leadership” page at mediabreakaway[dot]com, the email address ryanteraksxe1@yahoo.com almost certainly belongs to one Kacy Manning, who is listed as the “Manager of Special Projects” at Colorado based marketing firm Media Breakaway LLC.
Media Breakaway is headed by Scott Richter, a convicted felon who’s been successfully sued for spamming by some of the biggest media companies over the years.
In 2003, New York’s attorney general sued Richter and his former company OptInRealBig[dot]com after an investigation by Microsoft found his company was the source of hundreds of millions of spam emails daily touting dubious products and services. OptInRealBig later declared bankruptcy in the face of a $500 million judgment against the company. At the time, anti-spam group Spamhaus listed Richter as the world’s third most prolific spammer worldwide. For more on how Richter views his business, check out this hilarious interview that Richter gave to the The Daily Show in 2004.
In 2006, Richter paid $7 million to Microsoft in a settlement arising out of a lawsuit alleging illegal spamming.
In 2007, Richter and Media Breakaway were sued by social networking site MySpace; a year later, an arbitration firm awarded MySpace $6 million in damages and attorneys fees.
In 2013, the Internet Corporation for Assigned Names and Numbers (ICANN), the nonprofit firm which oversees the domain name registration industry, terminated the registrar agreement for Dynamic Dolphin, a domain name registrar of which Richter was the CEO.
According to the contracts that ICANN requires all registrars to sign, registrars may not have anyone as an officer of the company who has been convicted of a criminal offense involving financial activities. While Richter’s spam offenses all involve civil matters, KrebsOnSecurity discovered several years ago that Richter had actually pleaded guilty in 2003 to a felony grand larceny charge.

Scott Richter. Image: 4law.co.il
Richter, then 32, was busted for conspiring to deal in stolen goods, including a Bobcat, a generator, laptop computers, cigarettes and tools. He later pleaded guilty to one felony count of grand larceny, and was ordered to pay nearly $38,000 in restitution to cover costs linked to the case.
Neither Richter nor Media Breakaway responded to requests for comment on this story.
Chambers said it appears Media Breakaway is selling advertising space to unscrupulous actors who are pushing potentially unwanted programs (PUPs) or adware over the network.
“You end up coming out of the funnel into an advertiser’s payload site, and Media Breakaway is the publisher that routes those ‘parked/typosquatting’ sites as a gateway,” Chambers said. “Research on the IP under VirusTotal Communicating Files shows files like this one (42/66 engines) reporting to the IP address that hosts all these sites, and it goes back to at least March 2015. That file SETUPINST.EXE has detection primarily as LiveSoftAction, GetNow, ElDorado, and Multitoolbar. I think it’s just pushing out [content] for sketchy advertisers.”
It’s remarkable that so many huge corporate brand names aren’t doing more to police their trademarks and to prevent would-be visitors from falling victim to such blatant typosquatting traps.
Under the Uniform Domain-Name Dispute-Resolution Policy (UDRP), trademark holders can lodge typosquatting complaints with the World Intellectual Property Organization (WIPO). The complainant can wrest control over a disputed domain name, but first needs to show that the registered domain name is identical or “confusingly similar” to their trademark, that the registrant has no legitimate interest in the domain name, and that the domain name is being used in bad faith.
Everyone makes typ0s from time to time, which is why it’s a good idea to avoid directly navigating to Web sites you frequent. Instead, bookmark the sites you visit most, particularly those that store your personal and financial information, or that require a login for access.
Oh, and if your security or antivirus software allows you to block all Web sites in a given top-level domain, it might not be a bad idea to block anything coming out of dot-cm (the country code top-level domain for Cameroon): A report published in December 2009 by McAfee found that .cm was the riskiest domain in the world, with 36.7% of the sites posing a security risk to PCs.




Very interesting article. Wish AVs would allow blocking countries.
Someone on Twitter mentioned that the TLD for Cameroon (.cm) may not have agreed to the UDRP process.
https://twitter.com/GeorgeKirikos/status/979370287085965313
“Are you sure that the UDRP (designed by ICANN for gTLDs, although some ccTLDs have adopted it) applies to the .cm (Cameroon) ccTLD? See: wipo.int/amc/en/domains… which seems to indicate that it hasn’t been adopted by Cameroon.”
And…
https://twitter.com/GeorgeKirikos/status/979373459892391937
“Further evidence (from 2 years ago) it hadn’t adopted it is at: giga.law/blog/2016/06/2… (5th paragraph)”
If this is true, it may be another example of ICANN behaving like ICANN’T.
I’m using Bitdefender and it threw up warnings – either phishing or trojans – for all of the .cm sites I went to, except the ones actually owned and redirecting to the .com address holder.
Your article cites “fake” domains citicards[dot]com and costco[dot]com. Either you meant “.cm” or I should be very afraid?
Fixed that, thanks. It hurts your eyes after a couple of minutes typing those. :/
Amazing there is $ in it for these “advertisers”. Who in their right mind with do business with any of these people, including the lucky fat fingers who gets this .cm crap on their computer.
The .cm story is actually quite old. I remember hearing about it back when I owned over 1,000 domain names (no spam or typo squatting, for the most part). I forget who was the first person to recognize and exploit the concept. But he struck up a deal with those in Cameroon that I am sure was quite profitable. The idea was that the typo traffic for all or most unregistered .cm domains would redirect to a landing page full of ads or links to ads. The cost for creating this system using the DNS would have been quite low, so any income would be mostly profit.
I think the same thing was done with .co for a time and perhaps other TLDs that were typos of .net.
Yep. I link to a report from 2015 by Cisco that looked at some of these same domains. Either they weren’t linked to Media Breakaway at the time or Cisco didn’t delve into that aspect of them. But yes this is not a new problem by any stretch; it’s just incredible to me that some of the biggest banks in the world haven’t wrested control over these domains, because they must get a decent amount of traffic and they could be used for anything, including phishing.
What’s also interesting and that I didn’t mention in the story is that if you do a passive DNS lookup on the list of .cm domains, many of them have tons of subdomains like “mail.domain.cm” and “login.domain.cm,” which are caught in passive DNS because these .cm domains have a wildcard on the root domain. That means that many people have directly navigated to these subdomains and typed in .cm by accident. Here are a few examples (from Farsight/DNSDB):
logmein.cm. A 85.25.199.30
help.logmein.cm. A 85.25.199.30
secure.logmein.cm. A 85.25.199.30
accounts.logmein.cm. A 85.25.199.30
—–
chase.cm. A 85.25.199.30
m.chase.cm. A 85.25.199.30
w.chase.cm. A 85.25.199.30
w.w.chase.cm. A 85.25.199.30
wo.chase.cm. A 85.25.199.30
ww.chase.cm. A 85.25.199.30
api.chase.cm. A 85.25.199.30
pop.chase.cm. A 85.25.199.30
wee.chase.cm. A 85.25.199.30
wew.chase.cm. A 85.25.199.30
imap.chase.cm. A 85.25.199.30
mail.chase.cm. A 85.25.199.30
in.mail.chase.cm. A 85.25.199.30
pop3.chase.cm. A 85.25.199.30
smtp.chase.cm. A 85.25.199.30
wwww.chase.cm. A 85.25.199.30
cards.chase.cm. A 85.25.199.30
mail2.chase.cm. A 85.25.199.30
omwww.chase.cm. A 85.25.199.30
relay.chase.cm. A 85.25.199.30
ucard.chase.cm. A 85.25.199.30
cpanel.chase.cm. A 85.25.199.30
mycard.chase.cm. A 85.25.199.30
uscard.chase.cm. A 85.25.199.30
banking.chase.cm. A 85.25.199.30
careers.chase.cm. A 85.25.199.30
rewards.chase.cm. A 85.25.199.30
webmail.chase.cm. A 85.25.199.30
jpmorgan.chase.cm. A 85.25.199.30
wwwucard.chase.cm. A 85.25.199.30
myaccount.chase.cm. A 85.25.199.30
resources.chase.cm. A 85.25.199.30
rosalinda.chase.cm. A 85.25.199.30
secure07c.chase.cm. A 85.25.199.30
chaseonlne.chase.cm. A 85.25.199.30
mymortgage.chase.cm. A 85.25.199.30
chaseonline.chase.cm. A 85.25.199.30
creditcards.chase.cm. A 85.25.199.30
chaseaseonline.chase.cm. A 85.25.199.30
ultimaterewards.chase.cm. A 85.25.199.30
xn--chaseonlne-8sb.chase.cm. A 85.25.199.30
ultimaterewardspoints.chase.cm.
—–
comcast.cm. A 85.25.199.30
mx.comcast.cm. A 85.25.199.30
out.comcast.cm. A 85.25.199.30
pop.comcast.cm. A 85.25.199.30
imap.comcast.cm. A 85.25.199.30
mail.comcast.cm. A 85.25.199.30
smtp.comcast.cm. A 85.25.199.30
cable.comcast.cm. A 85.25.199.30
mx.cable.comcast.cm. A 85.25.199.30
imap.cable.comcast.cm. A 85.25.199.30
mail.cable.comcast.cm. A 85.25.199.30
smtp.cable.comcast.cm.
Fortunately seems like it was harmless, but the other day I typed seekingalpha.co (omitted the m) which re-directed me to a covered call investment service. Is this is a fairly common form of trying to get page views/visitors for legitimate (or seemingly legitimate) businesses?
its amazing how these guys run these sketchy businesses and get away with minor slaps on the wrist…
Much appreciated. I blocked the entire .cm TLD in response.
As I said in another reply above, the .cm story is old and an interesting read if you can find the story about the first person that was able to exploit the concept with the help of those managing the .cm TLD.
There is no reason to ever be typing the .com. For any .com site, simply enter the “middle” part of the domain name, then hit Ctrl-Enter. That will automatically fill in the www. before and the .com after. Works in every good browser. Always has. Think of the time saved…
Hey Pete, thanks for sharing that! I’m ashamed to say I never heard that before.
Works the same way on MacOS: domain+[control]+[enter] = http://www.domain.com
SHIFT+ENTER = .net in FireFox…
It didn’t work for the couple of sites I tried in 2 different browsers (on Android) and all I get is the Google search results. Maybe I need to turn off the search from address bar, if that’s still possible.
Not working for me — using both Chrome and Safari on Mac OS. Could this be OS / browser specific?
Edit: Missed the “then hit Ctrl-Enter”. So it works, but IMO I doubt the average web surfer will go to the effort to do this.
“Always has”
Untrue. That’s fairly recent browser behavior and only in the few browsers that have a combined search/address field. It’s not a standard behavior or a safe practice, as it assumes a particular browser behavior that’s not universal.
“Everyone makes typ0s” lol. I see what you did there.
Thanks Brian for your terrific work. Lo0k1ng g0od!
Darn!! I was hoping I was the only one to notice that. 🙂
Can someone post a link to instructions on how to block all Web sites in a given top-level domain? I poked around my Norton Security, but couldn’t find a way to do this.
Thanks!
http://bfy.tw/HNdh
Chris Nielsen, Don’t get hurt patting yourself on the back.
be on the lookout for Krebsonsecurity[dot]cm 🙂
All you need is a “krebsonsecurity(dot)cm”
I played around with some of those .cm sites using obvious domain-squatting names and on more than a few occasions was redirected to Amazon.com, Walmart.com, Bedbathbeyond.com and Edmunds.com (the real versions). Looking at the url, there were affiliate codes affixed with a source of “admarketplace”, “Barefruit” and others (those are the source, not the affiliate ID). Admartketplace (http://www.admarketplace.com/) appears to be an established, NYC-based advertising company, so I’m curious what their relationship is to whomever is registering these sites and why they wouldn’t have caught or prevented what appears to be a blatant misuse of affiliate marketing. Similarly, are these major stores aware of this practice and taking active steps to prevent it?
Also, a lot of the squat domains redirect through a domain “diggergrice.com” before going to the final landing site. The domain registration of diggergrice also uses the same ryanteraksxe1@yahoo.com email address and a different company name, Offer Function LLC, registered to David Steinberg out of Wyoming (http://website.informer.com/David+Steinberg+Offer+Function+LLC.html).
I put the “cm” TLD in my pi-hole (https://pi-hole.net); blocks everything DOT cm.
The headline should but add ‘and the “t” in .net too’!
If your browser won’t block domains, or you have a network with several machines, it may be better to block the .cm domain for the entire network. People running BIND can make their configs authoritative for the .cm domain. I’m (still) running Windows Server 2008. It turns out that simply adding a “cm” zone (no dots) appears to block all of Cameroon. It may be possible to do this with SOHO routers that have local DNS capability, too.
Sawing off an entire TLD seems drastic, but for individuals and many businesses, the protection gained might outweigh the inability to contact domains in the .cm TLD.
Symantec has the IP address listed as “observed sending spam in a format that is similar to snow shoe spamming”. Is S. Richter perhaps leading himself towards another spam lawsuit?
I do see many IP’s in the /16 network range listed for spam, etc, doing lookups using talosintelligence.
Hello, Brian. ICANN’s UDRP policy is only reliably applicable to gTLD domain names. But the domains here are on .CM, the ccTLD of Cameroon. .CM does not use UDRP (see http://www.wipo.int/amc/en/domains/cctld/index.html) and I can’t tell if the .CM registry operator has adopted a dispute resolution policy of any kind at all. So the recourse that people have in this case is unclear.
The network operator, heg, of 85.25.199.30 lists Intellectual Property: Fraud_and_Abuse_Policy.pdf
Paragraph 3.3.6 with Host Europe Group.
When I read “Spam King” I thought it was going to be Sanford “Spamford” Wallace. I think he went to prison. Richter probably should be there too.
Malware? LUL. They’re simply Co-Registration paths promoting Affiliate Offers for a few bucks… Brian, you’re normally on point but you are trying so hard with this one… Yeah, so sketchy but using mediabreakaway.com without hiding… Seriously? Focus on Russians and real cyber crime, this is a joke article.
just from looking at the site records for the sites named above, it seems like these guys were hiding behind LLCs fronted by people who front for spammers, and got sloppy with the recovery email address for the one listed in the story.
anyway even if that wasn’t the case, who cares if they’re not hiding? I learned a lot from this article, and any company doing in this kind of thing deserves to be put on the spotlight.
sounds like DontBelieveTheHype works in this same business. can’t really understand someone defending this kind of behavior otherwise.
Last time I checked, locking up your system with fake malware alerts and sending you to a fake Microsoft support line where they charge you hundreds of dollars to do nothing or (worse) install actual malware would be considered “real cyber crime”.
This isn’t really new, though. It’s been going on since the days of Metacrawl vs Metacrawler, although I forget which was the porn site, and whitehouse[dot]com.
I wonder if there’s a whitehouse[dot]cm
Beat me to it Matt – when I took some computer courses at the turn of the century, that URL was the main joke in the classroom. We’d get an uninitiated student to type that into the address bar then point to him/her and get the instructors attention. Red faces all around! LOL!! 😀
So when you type in the URL does it only affect when you type in .com, or .cm, or both.
espn cm redirects to 207 246 92 127 ch which is a fake tech support website. It takes over the mouse making it very difficult to close in both Firefox and Chrome. I filed an issue with both browsers.
https://bugs.chromium.org/p/chromium/issues/detail?id=827259
https://bugzilla.mozilla.org/show_bug.cgi?id=1450083
Also IC3 issued a warning today for tech support fraud.
https://www.ic3.gov/media/2018/180328.aspx
If you’re using OpenDNS at home (and you should be :)) then you’ve got some automatic protection. Per their FAQ:
“OpenDNS will return .cm domains when the root server delegates to a name server. However, if an A record is hosted directly on the root .cm server, then OpenDNS will block that domain. This is done because the .cm authoritative name servers used to engage in domain parking for wildcard domains.
If you need to resolve a .cm domain that is currently blocked please add that domain to a allow list.”
Just blocked Cameroon via L7 rule in my Meraki firewall – thx!
ESET does not like your .PDF link at the end of the 5th paragraph , blocks it and says it contains PDF/Phishing.A.Gen trojan
Thank youuuuuu
Brian,
Great article. I didn’t know a simple typo in the domain name can cause such damage. I think there should be restriction on using any other domain rather than the top level domain(TLD). except for the country TLD. example .au for Australia. Also, if there is such a case of tying .cm instead of .com leading the browser to redirect the user to a spam site, those websites must have a policy to redirect the url to the original site. example typing google.cm should redirect the browser to the original domain which is google.com. Can the governing bodies like ICANN impose such restrictions.
As far as the user’s computer getting attacked by malware are concerned, the users should be savvy enough install antivirus software in their machine. The firewall of the ISP’s (Internet Service Provider) must also be strong enough to identify and block the malicious sites, or atleast be able to warn the users.
I think the demographic who will be prone to this type of attack are those who are not too technologically savvy. Usually the older age group. I think the government, along with other large scale business must take the initiative to educate the people regarding these types of attack.
Also, the users should avoid using the websites that uses the HTTP protocol since it is not secure. They should only enter critical information on websites that use the HTTPS protocol since it is encrypted and a secure way to browse the internet. People might often ignore which protocol the website is using since no one types the entire url like https://www.google.com. However, they can look for a small lock icon that is displayed in most of the browsers, to identify if the sites are protected or if they use the HTTPS protocol.
Thanks for sharing this information. This is the first time I viewed this blog and now I intend to visit this blog often to remain knowledgeable of the security threats.
If anyone wants to know how to block the entire .cm TLD in uBlock Origin (might work for AdBlock too):
! *.cm TLD
||*.cm
@fugalism, the proper filter would be (using your example):
||cm^
This works for all blockers compatible with ABP syntax.
Your filter could lead to man false positives, as this would also filter out URLs like:
https://example.com/file.cm