Multiple security firms recently identified cryptocurrency mining service Coinhive as the top malicious threat to Web users, thanks to the tendency for Coinhive’s computer code to be used on hacked Web sites to steal the processing power of its visitors’ devices. This post looks at how Coinhive vaulted to the top of the threat list less than a year after its debut, and explores clues about the possible identities of the individuals behind the service.
Coinhive is a cryptocurrency mining service that relies on a small chunk of computer code designed to be installed on Web sites. The code uses some or all of the computing power of any browser that visits the site in question, enlisting the machine in a bid to mine bits of the Monero cryptocurrency.

Monero differs from Bitcoin in that its transactions are virtually untraceble, and there is no way for an outsider to track Monero transactions between two parties. Naturally, this quality makes Monero an especially appealing choice for cybercriminals.
Coinhive released its mining code last summer, pitching it as a way for Web site owners to earn an income without running intrusive or annoying advertisements. But since then, Coinhive’s code has emerged as the top malware threat tracked by multiple security firms. That’s because much of the time the code is installed on hacked Web sites — without the owner’s knowledge or permission.
Much like a malware infection by a malicious bot or Trojan, Coinhive’s code frequently locks up a user’s browser and drains the device’s battery as it continues to mine Monero for as long a visitor is browsing the site.
According to publicwww.com, a service that indexes the source code of Web sites, there are nearly 32,000 Web sites currently running Coinhive’s JavaScript miner code. It’s impossible to say how many of those sites have installed the code intentionally, but in recent months hackers have secretly stitched it into some extremely high-profile Web sites, including sites for such companies as The Los Angeles Times, mobile device maker Blackberry, Politifact, and Showtime.
And it’s turning up in some unexpected places: In December, Coinhive code was found embedded in all Web pages served by a WiFi hotspot at a Starbucks in Buenos Aires. For roughly a week in January, Coinhive was found hidden inside of YouTube advertisements (via Google’s DoubleClick platform) in select countries, including Japan, France, Taiwan, Italy and Spain. In February, Coinhive was found on “Browsealoud,” a service provided by Texthelp that reads web pages out loud for the visually impaired. The service is widely used on many UK government websites, in addition to a few US and Canadian government sites.
What does Coinhive get out of all this? Coinhive keeps 30 percent of whatever amount of Monero cryptocurrency that is mined using its code, whether or not a Web site has given consent to run it. The code is tied to a special cryptographic key that identifies which user account is to receive the other 70 percent.
Coinhive does accept abuse complaints, but it generally refuses to respond to any complaints that do not come from a hacked Web site’s owner (it mostly ignores abuse complaints lodged by third parties). What’s more, when Coinhive does respond to abuse complaints, it does so by invalidating the key tied to the abuse.
But according to Troy Mursch, a security expert who spends much of his time tracking Coinhive and other instances of “cryptojacking,” killing the key doesn’t do anything to stop Coinhive’s code from continuing to mine Monero on a hacked site. Once a key is invalidated, Mursch said, Coinhive keeps 100 percent of the cryptocurrency mined by sites tied to that account from then on.
Mursch said Coinhive appears to have zero incentive to police the widespread abuse that is leveraging its platform.
“When they ‘terminate’ a key, it just terminates the user on that platform, it doesn’t stop the malicious JavaScript from running, and it just means that particular Coinhive user doesn’t get paid anymore,” Mursch said. “The code keeps running, and Coinhive gets all of it. Maybe they can’t do anything about it, or maybe they don’t want to. But as long as the code is still on the hacked site, it’s still making them money.”
Reached for comment about this apparent conflict of interest, Coinhive replied with a highly technical response, claiming the organization is working on a fix to correct that conflict.
“We have developed Coinhive under the assumption that site keys are immutable,” Coinhive wrote in an email to KrebsOnSecurity. “This is evident by the fact that a site key can not be deleted by a user. This assumption greatly simplified our initial development. We can cache site keys on our WebSocket servers instead of reloading them from the database for every new client. We’re working on a mechanism [to] propagate the invalidation of a key to our WebSocket servers.”
AUTHEDMINE
Coinhive has responded to such criticism by releasing a version of their code called “AuthedMine,” which is designed to seek a Web site visitor’s consent before running the Monero mining scripts. Coinhive maintains that approximately 35 percent of the Monero cryptocurrency mining activity that uses its platform comes from sites using AuthedMine.
But according to a report published in February by security firm Malwarebytes, the AuthedMine code is “barely used” compared to the use of Coinhive’s mining code that does not seek permission from Web site visitors. Malwarebytes’ telemetry data (drawn from antivirus alerts when users browse to a site running Coinhive’s code) determined that AuthedMine is used in a little more than one percent of all cases that involve Coinhive’s mining code.
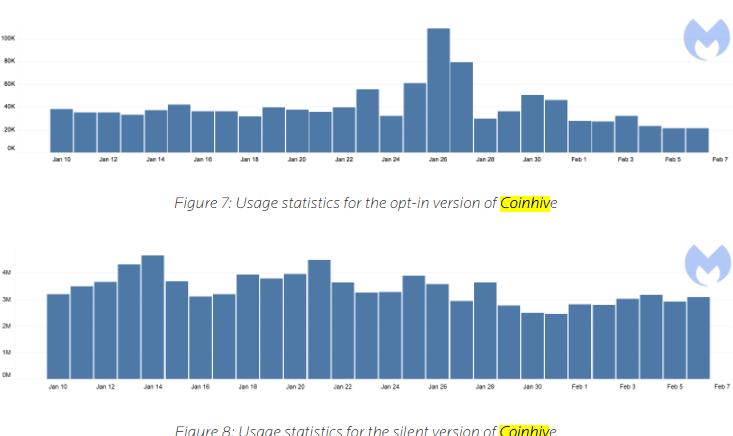
Image: Malwarebytes. The statistic above refer to the number of times per day between Jan. 10 and Feb. 7 that Malwarebytes blocked connections to AuthedMine and Coinhive, respectively.
Asked to comment on the Malwarebytes findings, Coinhive replied that if relatively few people are using AuthedMine it might be because anti-malware companies like Malwarebytes have made it unprofitable for people to do so.
“They identify our opt-in version as a threat and block it,” Coinhive said. “Why would anyone use AuthedMine if it’s blocked just as our original implementation? We don’t think there’s any way that we could have launched Coinhive and not get it blacklisted by Antiviruses. If antiviruses say ‘mining is bad,’ then mining is bad.”
Similarly, data from the aforementioned source code tracking site publicwww.com shows that some 32,000 sites are running the original Coinhive mining script, while the site lists just under 1,200 sites running AuthedMine.
WHO IS COINHIVE?
[Author’s’ note: Ordinarily, I prefer to link to sources of information cited in stories, such as those on Coinhive’s own site and other entities mentioned throughout the rest of this piece. However, because many of these links either go to sites that actively mine with Coinhive or that include decidedly not-safe-for-work content, I have included screenshots instead of links in these cases. For these reasons, I would strongly advise against visiting pr0gramm’s Web site.]
According to a since-deleted statement on the original version of Coinhive’s Web site — coin-hive[dot]com — Coinhive was born out of an experiment on the German-language image hosting and discussion forum pr0gramm[dot]com.
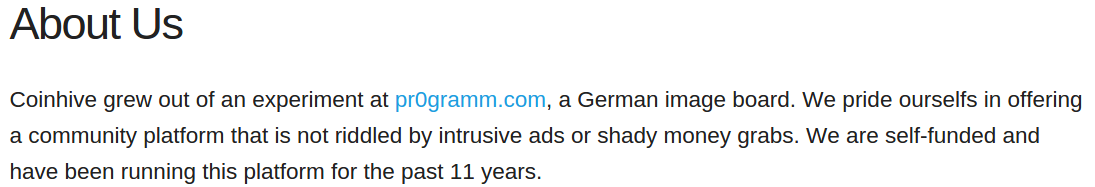
A now-deleted “About us” statement on the original coin-hive[dot]com Web site. This snapshop was taken on Sept. 15, 2017. Image courtesy archive.org.
I asked Coinhive for clarity on the disappearance of the above statement from its site concerning its affiliation with pr0gramm. Coinhive replied that it had been a convenient fiction:
“The owners of pr0gramm are good friends and we’ve helped them with their infrastructure and various projects in the past. They let us use pr0gramm as a testbed for the miner and also allowed us to use their name to get some more credibility. Launching a new platform is difficult if you don’t have a track record. As we later gained some publicity, this statement was no longer needed.”
Asked for clarification about the “platform” referred to in its statement (“We are self-funded and have been running this platform for the past 11 years”) Coinhive replied, “Sorry for not making it clearer: ‘this platform’ is indeed pr0gramm.”
After receiving this response, it occurred to me that someone might be able to find out who’s running Coinhive by determining the identities of the pr0gramm forum administrators. I reasoned that if they were not one and the same, the pr0gramm admins almost certainly would know the identities of the folks behind Coinhive.
WHO IS PR0GRAMM?
So I set about trying to figure out who’s running pr0gramm. It wasn’t easy, but in the end all of the information needed to determine that was freely available online.
Let me be crystal clear on this point: All of the data I gathered (and presented in the detailed ‘mind map’ below) was derived from either public Web site WHOIS domain name registration records or from information posted to various social media networks by the pr0gramm administrators themselves. In other words, there is nothing in this research that was not put online by the pr0gramm administrators themselves.
I began with the pr0gramm domain itself which, like many other domains tied to this research, was originally registered to an individual named Dr. Matthias Moench. Mr. Moench is only tangentially connected to this research, so I will dispense with a discussion of him for now except to say that he is a convicted spammer and murderer, and that the last subsection of this story explains who Moench is and why he may be connected to so many of these domains. His is a fascinating and terrifying story.
Through many weeks of research, I learned that pr0gramm was originally tied to a network of adult Web sites linked to two companies that were both incorporated more than a decade ago in Las Vegas, Nevada: Eroxell Limited, and Dustweb Inc. Both of these companies stated they were involved in online advertising of some form or another.
Both Eroxell and Dustweb, as well as several related pr0gramm Web sites (e.g., pr0mining[dot]com, pr0mart[dot]de, pr0shop[dot]com) are connected to a German man named Reinhard Fuerstberger, whose domain registration records include the email address “admin@pr0gramm[dot]com”. Eroxell/Dustweb also each are connected to a company incorporated in Spain called Suntainment SL, of which Fuerstberger is the apparent owner.
As stated on pr0gramm’s own site, the forum began in 2007 as a German language message board that originated from an automated bot that would index and display images posted to certain online chat channels associated with the wildly popular video first-person shooter game Quake.
As the forum’s user base grew, so did the diversity of the site’s cache of images, and pr0gramm began offering paid so-called “pr0mium” accounts that allowed users to view all of the forum’s not-safe-for-work images and to comment on the discussion board. When pr0gramm last July first launched pr0miner (the precursor to what is now Coinhive), it invited pr0gramm members to try the code on their own sites, offering any who did so to claim their reward in the form of pr0mium points.
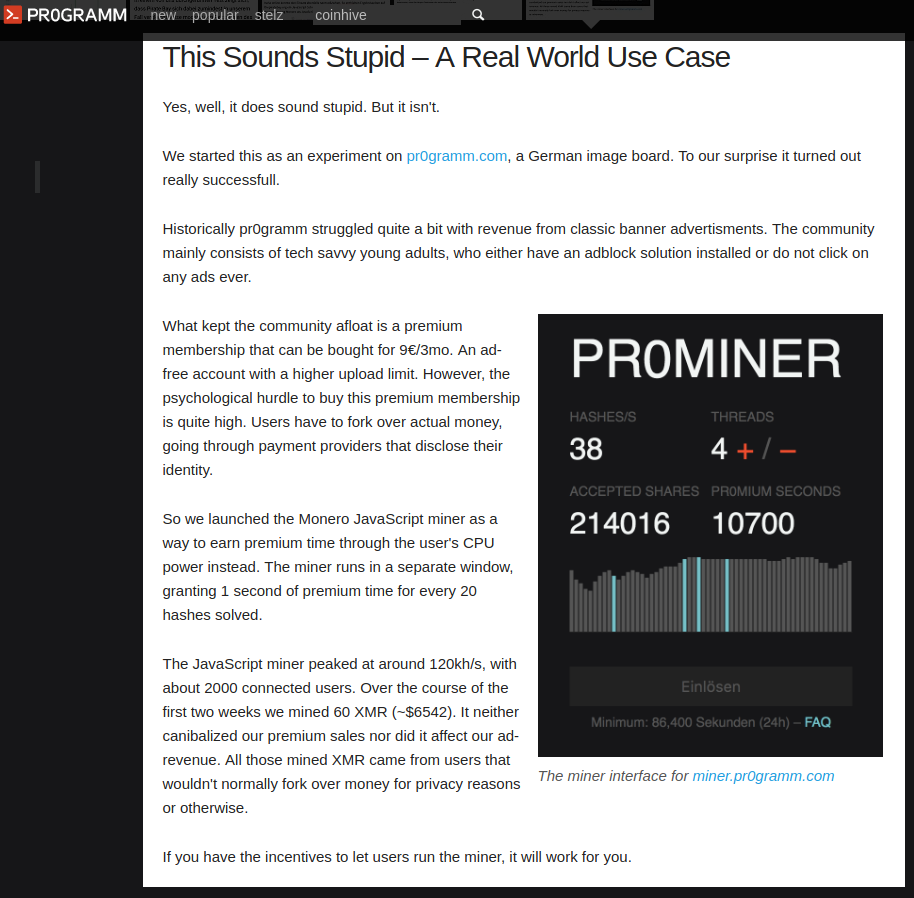
A post on pr0gramm post concerning pr0miner, the precursor to what would later become known as Coinhive.
DEIMOS AND PHOBOS
Pr0gramm was launched in late 2007 by a Quake enthusiast from Germany named Dominic Szablewski, a computer expert better known to most on pr0gramm by his screen name “cha0s.”
At the time of pr0gramm’s inception, Szbalewski ran a Quake discussion board called chaosquake[dot]de, and a personal blog — phoboslab[dot]org. I was able to determine this by tracing a variety of connections, but most importantly because phoboslab and pr0gramm both once shared the same Google Analytics tracking code (UA-571256).
Reached via email, Szablewski said he did not wish to comment for this story beyond stating that he sold pr0gramm a few years ago to another, unnamed individual.
Multiple longtime pr0gramm members have remarked that since cha0s departed as administrator, the forum has become overrun by individuals with populist far-right political leanings. Mr. Fuerstberger describes himself on various social media sites as a “politically incorrect, Bavarian separatist” [Wiki link added]. What’s more, there are countless posts on pr0gramm that are particularly hateful and denigrating to specific ethnic or religious groups.
Responding to questions via email, Fuerstberger said he had no idea pr0gramm was used to launch Coinhive.
“I can assure you that I heard about Coinhive for the first time in my life earlier this week,” he said. “I can assure you that the company Suntainment has nothing to do with it. I do not even have anything to do with Pr0gram. That’s what my partner does. When I found out now what was abusing my company, I was shocked.”
Below is a “mind map” I assembled to keep track of the connections between and among the various names, emails and Web sites mentioned in this research.

A “mind map” I put together to keep track of and organize my research on pr0gramm and Coinhive. This map was created with Mindnode Pro for Mac. Click to enlarge.
GAMB
I was able to learn the identity of Fuerstberger’s partner — the current pr0gramm administrator, who goes by the nickname “Gamb” — by following the WHOIS data from sites registered to the U.S.-based company tied to pr0gramm (Eroxell Ltd).
Among the many domains registered to Eroxell was deimoslab[dot]com, which at one point was a site that sold electronics. As can be seen below in a copy of the site from 2010 (thanks to archive.org), the proprietor of deimoslab used the same Gamb nickname.
Deimos and Phobos are the names of the two moons of the planet Mars. They also refer to the names of the fourth and fifth level in the computer game “Doom.” In addition, they are the names of two spaceships that feature prominently in the game Quake II.
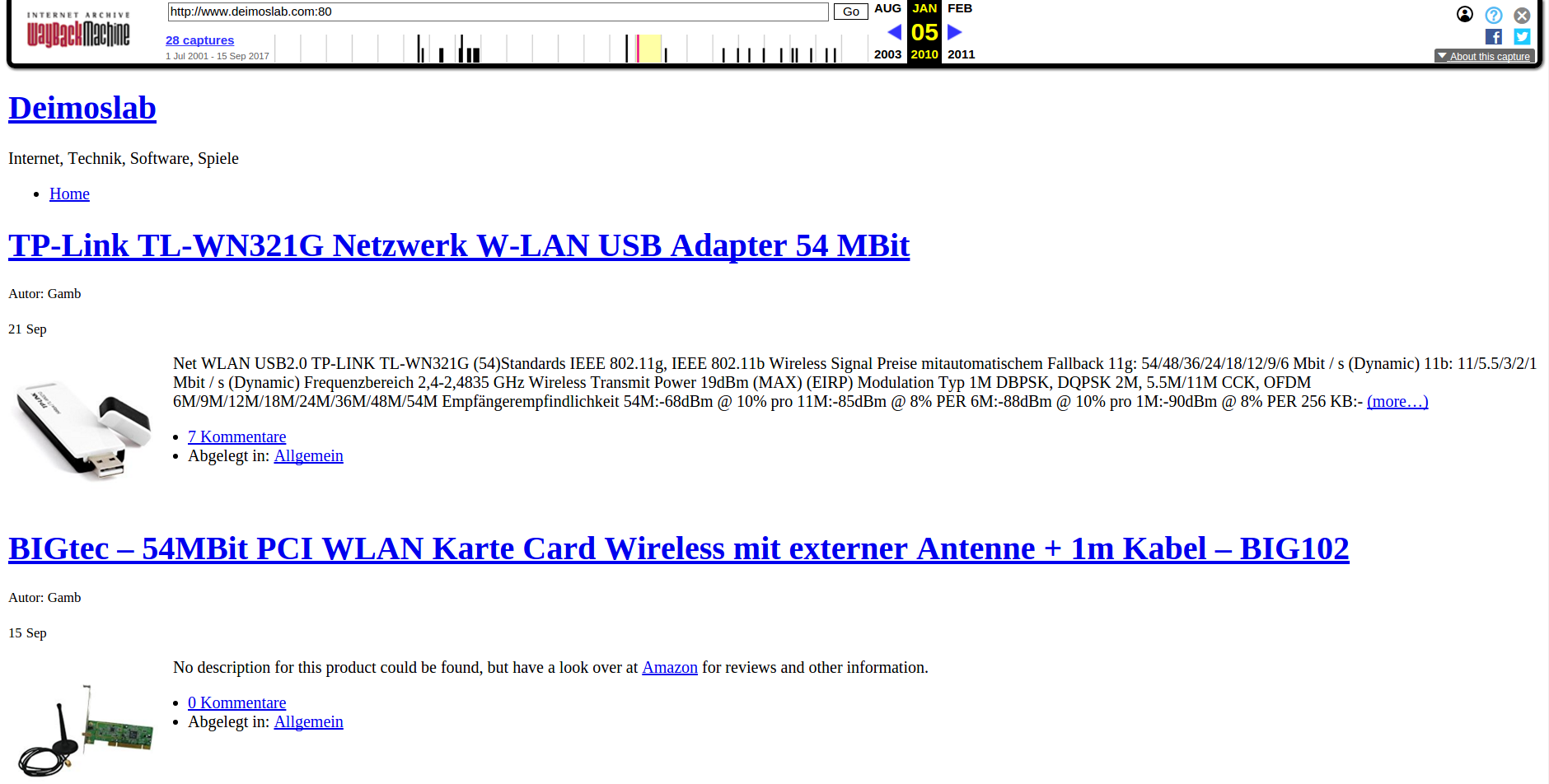
A screenshot of Deimoslab.com from 2010 (courtesy of archive.org) shows the user “Gamb” was responsible for the site.
A passive DNS lookup on an Internet address long used by pr0gramm[dot]com shows that deimoslab[dot]com once shared the server with several other domains, including phpeditor[dot]de. According to a historic WHOIS lookup on phpeditor[dot]de, the domain was originally registered by an Andre Krumb from Gross-Gerau, Germany.
When I discovered this connection, I still couldn’t see anything tying Krumb to “Gamb,” the nickname of the current administrator of pr0gramm. That is, until I began searching the Web for online forum accounts leveraging usernames that included the nickname “Gamb.”
One such site is ameisenforum[dot]de, a discussion forum for people interested in creating and raising ant farms. I didn’t know what to make of this initially and so at first disregarded it. That is, until I discovered that the email address used to register phpeditor[dot]de also was used to register a rather unusual domain: antsonline[dot]de.
In a series of email exchanges with KrebsOnSecurity, Krumb acknowledged that he was the administrator of pr0gramm (as well as chief technology officer at the aforementioned Suntainment SL), but insisted that neither he nor pr0gramm was involved in Coinhive.
Krumb repeatedly told me something I still have trouble believing: That Coinhive was the work of just one individual — int13h, the pr0gramm user credited by Coinhive with creating its mining code.
“Coinhive is not affiliated with Suntainment or Suntainment’s permanent employees in any way,” Krumb said in an email, declining to share any information about int13h. “Also it’s not a group of people you are looking for, it’s just one guy who sometimes worked for Suntainment as a freelancer.”
COINHIVE CHANGES ITS STORY, WEB SITE
Very soon after I began receiving email replies from Mr. Fuerstberger and Mr. Krumb, I started getting emails from Coinhive again.
“Some people involved with pr0gramm have contacted us, saying they’re being extorted by you,” Coinhive wrote. “They want to run pr0gramm anonymously because admins and moderators had a history of being harassed by some trolls. I’m sure you can relate to that. You have them on edge, which of course is exactly where you want them. While we must applaud your efficiency for finding information, your tactics for doing so are questionable in our opinion.”
Coinhive was rather dramatically referring to my communications with Krumb, in which I stated that I was seeking more information about int13h and anyone else affiliated with Coinhive.
“We want to make it very clear again that Coinhive in its current form has nothing to do with pr0gramm or its owners,” Coinhive said. “We tested a ‘toy implementation’ of the miner on pr0gramm, because they had a community open for these kind of things. That’s it.”
When asked about their earlier statement to this author — that the people behind Coinhive claimed pr0gramm as “their platform of 11 years” (which, incidentally, is exactly how long pr0gramm has been online) — Coinhive reiterated its revised statement: That this had been a convenient fabrication, and that the two were completely separate organizations.
On March 22, the Coinhive folks sent me a follow-up email, saying that in response to my inquiries they consulted their legal team and decided to add some contact information to their Web site.
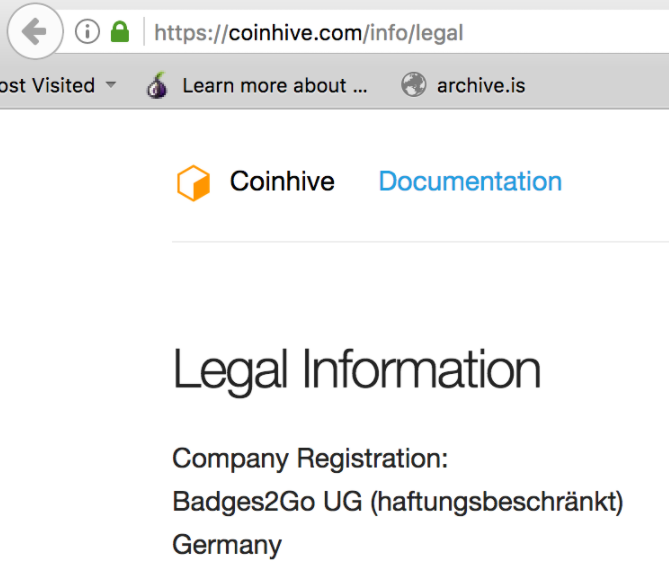
“Legal information” that Coinhive added to its Web site on March 22 in response to inquiries from this reporter.
That addition, which can be viewed at coinhive[dot]com/legal, lists a company in Kaiserlautern, Germany called Badges2Go UG. Business records show Badges2Go is a limited liability company established in April 2017 and headed by a Sylvia Klein from Frankfurt. Klein’s Linkedin profile states that she is the CEO of several organizations in Germany, including one called Blockchain Future.
“I founded Badges2Go as an incubator for promising web and mobile applications,” Klein said in a instant message chat with KrebsOnSecurity. “Coinhive is one of them. Right now we check the potential and fix the next steps to professionalize the service.”
THE BIZARRE SIDE STORY OF DR. MATTHIAS MOENCH
I have one final and disturbing anecdote to share about some of the Web site registration data in the mind map above. As mentioned earlier, readers can see that many of the domain names tied to the pr0gramm forum administrators were originally registered to an individual named “Dr. Matthias Moench.”
When I first began this research back in January 2018, I guessed that Mr. Moench was almost certainly a pseudonym used to throw off researchers. But the truth is Dr. Moench is indeed a real person — and a very scary individual at that.
According to a chilling 2014 article in the German daily newspaper Die Welt, Moench was the son of a wealthy entrepreneurial family in Germany who was convicted at age 19 of hiring a Turkish man to murder his parents a year earlier in 1988. Die Welt says the man Moench hired used a machete to hack to death Moench’s parents and the family poodle. Moench reportedly later explained his actions by saying he was upset that his parents bought him a used car for his 18th birthday instead of the Ferrari that he’d always wanted.
Matthias Moench in 1989. Image: Welt.de.
Moench was ultimately convicted and sentenced to nine years in a juvenile detention facility, but he would only serve five years of that sentence. Upon his release, Moench claimed he had found religion and wished to become a priest.
Somewhere along the way, however, Moench ditched the priest idea and decided to become a spammer instead. For years, he worked assiduously to pump out spam emails pimping erectile dysfunction medications, reportedly earning at least 21.5 million Euros from his various spamming activities.
Once again, Mr. Moench was arrested and put on trial. In 2015, he and several other co-defendants were convicted of fraud and drug-related offenses. Moench was sentenced to six years in prison. According to Lars-Marten Nagel, the author of the original Die Welt story on Moench’s murderous childhood, German prosecutors say Moench is expected to be released from prison later this year.
It may be tempting to connect the pr0gramm administrators with Mr. Moench, but it seems likely that there is little to no connection here. An incredibly detailed blog post from 2006 which sought to determine the identity of the Matthias Moench named as the original registrant of so many domains (they number in the tens of thousands) found that Moench himself stated on several Internet forums that his name and mailing addresses in Germany and the Czech Republic could be freely used or abused by any like-minded spammer or scammer who wished to hide his identity. Apparently, many people took him up on that offer.
Update, 4:14 p.m. ET: Shortly after this story went live, an update was added to phoboslab[dot]org, the personal blog of Dominic Szablewski, the founder of pr0gramm[dot]com. In it, Szablewski claims responsibility for starting Coinhive. As for who’s running it now, we’re left to wonder. The new content there reads:
“Brian Krebs recently published a story about Coinhive and I want to clarify some things.”
“In 2007 I built a simple image board – pr0gramm – for my friends and me. Over the years, this board has evolved and grown tremendously. When some trolls in 2015 found out who was behind pr0gramm, I received death threats for various moderation decisions on that board. I decided to get out of it and sold pr0gramm. I was still working on pr0gramm behind the scenes and helped with technical issues from time to time, but abstained from moderating completely.”
“Mid last year I had the idea to try and implement a Cryptocurrency miner in WebAssembly. Just as an experiment, to see if it would work. Of course I needed some users to test it. The owners of pr0gramm were generous enough to let me try but had no part in the development. I quickly built a separate page on pr0gramm.com that users could open to earn a premium account by mining. It worked tremendously well.”
“So I decided to expand this idea into its own platform. I launched Coinhive a few months later and quickly realized that I couldn’t do this alone. So I was searching for someone who would take over.”
“I found a company interested in a new venture. They have taken over Coinhive and are now working on a big overhaul.”




Nice write up and a bit of doxx. I’ve been watching coinhive attempt to use compute from my users but we just block at the local firewall and web proxy. It’s annoying but nice to see confirmation that YouTube ads were indeed part of it.
Subhed on German headline, poorly translated: “Your cries of death were music to my ears.”
“THEIR cries of death were music to my ears.”
Super scary :/
Nice work done here, very interesting read!
I was thinking about putting the authedmine miner on our page and removing all banners for the users that mine a little bit for us. But with all the antivirus programs flagging even this as malware I am afraid that our reputation will drop and the people will leave our site.
What a pitty, I am really searching for an alternative for the banners.
I found jsecoin (jsecoin.com) and it looks nice, but there is no guarantee that there ever will be any (real) return when mining their coins. Brian, or anybody else, know of some alternative serviçe?
It might be best to hold off on the site-mining for now because of its high profile. It might be better for you to add a subscription/donation option to your site, if it gets enough visits.
Yes, was thinking about this.
I heard about micro donations. Will have a closer look.
Very unfortunate that mining was misused. Hope somebody will come up with something similar that can use the users processing power for generating revenue…
salon.com has taken to a mining alternative for those who use adblockers. The only problem is it pegs your cpu at about 85% or more. Site visitors are informed and given a choice.
Nice, now maybe (doubt it) they will play nice and think about the consequences of the products they engineer. By the sounds of it, they should have SOMEONE in that shady organization who could have easily spotted that this program would reach epic usage for good and bad. It very well may have been their plan to have others create the mining and kill the key, and take the spoils.
Some how I feel this is only the beginning from this group. They may hide under a rock for a little while, but it is like anything else – greed will take over.
Question, to block coinhive, is there a list of URLs located some place we can add to our webfilter?
Thanks
Try:
https://github.com/ZeroDot1/CoinBlockerLists/blob/master/list.txt
Thank you, wow that was a lot.
I tested a couple to see if our filtering service already blocked them – not the ones I tested.
Blocking now 🙂
Good investigative work!
Yesh. Threatening people is definitely goid investigative work. And leaving false information in it knowing that it is wrong. I mean, he’s got my respect for digging so deep, but not for twisting facts. So overall i am not so happy with this article
Solid journalism as always Krebs
man spricht nicht über das pr0gramm
Someone posted it on programm and it got deleted direclty and the user got banned
Saw the Post, but didn’t exptect the user to be banned immediately. But I’m not surprised either¯\_(ツ)_/¯
Don’t you thing this is part of their annual april fools joke?
They don’t know any fun about anonymity. Perhaps someone is afraid of a second 80 kg steel furnace.
“they don’t understand any fun” – good English, first cream!
Gott strafe es!
Tanz, du Hure
Minus
What a great idea ruined by greed and lack of concern for others!
If anyone wants to start an HONEST mining company that treats users as partners, let me know. I would love to be involved. The potential is unlimited from signing up users who will let their machines mine in off-hours to those that will invest in low-cost “mining equipment” that will run of solar power(to make it cost-effective).
as we see more and more cases like this related with crypto currencies, its not the surprise coz carding in cybercrime sphere is dead. and untwortentely now the old carders will turn to cryptocurrency business.
say bye bye to cvv hacking bank transfers and say hello to monero bitcoins ethereum and all kind of crypto currency.
i saw the word bavarian here so no wonder what kind of mind set those poeple have. no wonder why they like bavarain symbols no wonder they reconize each other in the world.
No, not the poodle ! LOL
Great work Brian! Just as a side note, have you ever used Paterva’s Maltego and CaseFile? If you haven’t I would highly recommend them for the “mind mapping” task.
Yes, I have a paid license to Maltego, and used the SocialNet plugin extensively for this research.
Krebs du Hurensohn, hoffentlich verreckst du dran!
Haha, someone is salty!
The pr0gramm.com-admins spend the whole day banning users that upload screenshots of this article to the platform.
Not true. They simply deleted the posts because some of the admins personal information was doxxed which is against their TOS.
Do know of a way to identify code from coinhive that has been installed on a server? I manage a number of servers, so this is of special interest.
so now doxxing people is called journalism? Really sad and pathetic…
§ 186
Üble Nachrede
Wer in Beziehung auf einen anderen eine Tatsache behauptet oder verbreitet, welche denselben verächtlich zu machen oder in der öffentlichen Meinung herabzuwürdigen geeignet ist, wird, wenn nicht diese Tatsache erweislich wahr ist, mit Freiheitsstrafe bis zu einem Jahr oder mit Geldstrafe und, wenn die Tat öffentlich oder durch Verbreiten von Schriften (§ 11 Abs. 3) begangen ist, mit Freiheitsstrafe bis zu zwei Jahren oder mit Geldstrafe bestraft.
~Just letting you know
So goddamn true
The prerequisite for slander (in German: “Üble Nachrede” or “Verleumdung”) is that the allegations are false… and it seems that they aren’t 😉
§ 186
Üble Nachrede
Wer in Beziehung auf einen anderen eine Tatsache behauptet oder verbreitet, welche denselben verächtlich zu machen oder in der öffentlichen Meinung herabzuwürdigen geeignet ist, wird, wenn nicht diese Tatsache erweislich wahr ist, mit Freiheitsstrafe bis zu einem Jahr oder mit Geldstrafe und, wenn die Tat öffentlich oder durch Verbreiten von Schriften (§ 11 Abs. 3) begangen ist, mit Freiheitsstrafe bis zu zwei Jahren oder mit Geldstrafe bestraft.´
~ just letting you know
Geil! Mir egal ob das alles nur gelogen ist! Solange das Programm drunter leidet ist mir jedes Mittel recht! Die geistigen Säuglinge auf Programm sind wegen der Story extrem butthurted!
Looks like a banned kiddy rages kek
If this has consequences for our beloved site, you will feel the wrath of germanys biggest troll army! My mum always told me, don´t poke a bee hive with a stick.
….with this articel you lost my respect
Mine as well
‘journalism’, misses some trump quotes. last time i visited your blog, brian.
Die Deutscher sind kerplumpft!
I am having a hard time here understanding what the security implications of these findings should be.
So there is a mining service and hackers use to mine stuff on sites they took over.
Well hackers manipulating websites is not really news over here, this service just provides a more convenient way than infecting a computer with malware or displaying your own ads. Incidently it is even more safe for users since they won’t get a crypto trojan encrypting their personal files.
So there is a service doing this, which is good to know, but that leaves me wondering why most of the article is spend on exposing the very real people hosting a image board.
Because he felt so good finding this out. Obviously his attempts to understand why this service did what it did ended after he received “a highly technical response”.
Who wouldn’t stop trying to find out about the real issue at this point then?
Total dubious, poorly researched crap! People like you are the reason for serious journalism going under.
This seriously crossed all the borders of journalism. Whoever thinks putting peoples (who obviously want to stay anonymous) adresses online should not call him self a journalist, especially not something like “Security Researcher”.
Not only is this against every moral, the reason for putting this online – the “top malicious threat to Web users” is actually not even a thread. Most people are more OK with using a bit more electricity and hearing their PC getting more noisy than they are with click-jacking and popups.
Hey Mr. Krebs, everybody in this community knew coinhive was active for a certain period of time, they made it transparent and it was no problem for the users, since we love that imageboard. It is fun, very creative and it it is one of the few places today that really allows free speech. You are just another antidemocratic american that wants to restrict free speach in the name of your pseudo morale and an ethics of opinion, instead of an ethics of responsibility.
Poorly researched article, a lot of blatant lies. This is no journalism, but your attempt for a clickbait article.
Good advertisment for coinhive! Didn’t know this service! Thanks
You know too much.
lemme see if i have this right….
Coinhive prints a statement on their site saying they ran programm as “their” platform for 11 years.
Coinhive says no, that was a lie that worked for us for a while, until we no longer needed that lie.
Krebs finds the admins of programm using public WHOIS records and social media accounts of programm admins, and reaches out to them to get comments about their relationship with Coinhive.
The admins of programm all deny they have anything to do with Coinhive, and refuse to say who they know is the person behind it. Krebs prints a story based on his research into public data.
Coinhive changes its policies to fix the problems highlighted in the story.
Then the original admin of programm comes out to say he was indeed the guy behind the birth of Coinhive.
How is this bad reporting?
+100. BK ignore these Germanphobes. you struck too close to the nest with this one and the hive is pissed, nothing more.
and why exactly was it necessary to find out who created coinhive? it not even malware rofl
You know… I got to this article because I was googling why my damn “Malwarebytes Service” was just taking up all my disk usage and CPU since I upgraded. Is Malwarebytes malware for using all my damn CPU usage? Or are my video games?
They really need to put CPU and disk throttles in windows and OS X so that every time you boot you don’t have to wait for all the damn programs to do its damn thing. If slowing down your computer to a crawl is a problem then Windows Update is one hell of a virus.
Look, yes… If you know how I am, I support Coin Hive in a sense… I support what it does if it was with permission and you could throttle it to 10% because everyone is entitled to do whatever they want with their CPU if they know what is going on. Just blocking it still doesn’t solve the problem of crappy programs by Microsoft and Google doing too much crap in the background.
At least the task manager shows GPU now so I can see what the games are doing.
Look. The problem is that we need better managment of our apps. In task manager we need to be allowed to right click on a program and say “only use 10% of the resources”. Is anyone going to scream at Microsoft and Malware bytes so their programs don’t steal my CPU too? Seriously. Microsoft has stole more electricity and time that any crytpo miner ever has!
Also I am a veteran of the ad pop up appocolypse of 2008. Did MS ever fix the goddamn issue of popups and viruses you got through ads in IE. No. We had to use damn Firefox and Chrome until the only thing IE was used for was to install the above. Jesus people its like your being paid to ignore the real problem of technology. Sorry… I still want to know why Malwarebytes service was using 100% of my disk and CPU even though I just did a scan 20 minutes ago.
Also… Coin Hive is a technology not a virus.
Javascript ads can deliver malware too yet you guys probaly don’t recommend that everyone install uBlock because you want more money even though it has been proven ads are a vector for malware.
https://www.techdirt.com/articles/20160111/05574633295/forbes-site-after-begging-you-turn-off-adblocker-serves-up-steaming-pile-malware-ads.shtml
Again, this problem can be solved if we had some software that can throttle all CPU and disk usage in task manager. You know this seems like it should be a thing. Why isn’t task throttling a thing? I just checked to see if I wasn’t being dumb and no… You can only set priority in the details. WHY CAN’T I JUST RIGHT CLICK AND SET % OF HOW MUCH A PROGRAM USES!
If this does become a thing system needs a category… Its been 20 goddamn years and I have to get a cup of something to drink every time I boot my computer even though its a exponentially faster than my old pentium.
. . .
Can all those coinhive fans who are slamming Krebs for writing a crappy article and being a disgrace to journalism, please write and indicate what it is they are actually complaining about?
*crickets*
. . .
LOL!!!
Here in Germany the political landscape is pretty rough right now. People get their houses, vehicles and family attacked by the radical alt lefts. What you are doing is slender in its purest form and especially with your past you should know better.
You don’t think he’s true that its all publicly available information? Which part?
1) Slender might be good after all that Easter chocolate.
2) Please stop promoting fairy tales of left wing extremism being a big issue in Germany. Americans might actually believe you.