The Federal Bureau of Investigation (FBI) is warning that a new malware threat has rapidly infected more than a half-million consumer devices. To help arrest the spread of the malware, the FBI and security firms are urging home Internet users to reboot routers and network-attached storage devices made by a range of technology manufacturers.
The growing menace — dubbed VPNFilter — targets Linksys, MikroTik, NETGEAR and TP-Link networking equipment in the small and home office space, as well as QNAP network-attached storage (NAS) devices, according to researchers at Cisco.

Experts are still trying to learn all that VPNFilter is built to do, but for now they know it can do two things well: Steal Web site credentials; and issue a self-destruct command, effectively rendering infected devices inoperable for most consumers.
Cisco researchers said they’re not yet sure how these 500,000 devices were infected with VPNFilter, but that most of the targeted devices have known public exploits or default credentials that make compromising them relatively straightforward.
“All of this has contributed to the quiet growth of this threat since at least 2016,” the company wrote on its Talos Intelligence blog.
The Justice Department said last week that VPNFilter is the handiwork of “APT28,” the security industry code name for a group of Russian state-sponsored hackers also known as “Fancy Bear” and the “Sofacy Group.” This is the same group accused of conducting election meddling attacks during the 2016 U.S. presidential race.
“Foreign cyber actors have compromised hundreds of thousands of home and office routers and other networked devices worldwide,” the FBI said in a warning posted to the Web site of the Internet Crime Complaint Center (IC3). “The actors used VPNFilter malware to target small office and home office routers. The malware is able to perform multiple functions, including possible information collection, device exploitation, and blocking network traffic.”
According to Cisco, here’s a list of the known affected devices:
LINKSYS DEVICES:
E1200
E2500
WRVS4400N
MIKROTIK ROUTEROS VERSIONS FOR CLOUD CORE ROUTERS:
1016
1036
1072
NETGEAR DEVICES:
DGN2200
R6400
R7000
R8000
WNR1000
WNR2000
QNAP DEVICES:
TS251
TS439 Pro
Other QNAP NAS devices running QTS software
TP-LINK DEVICES:
R600VPN
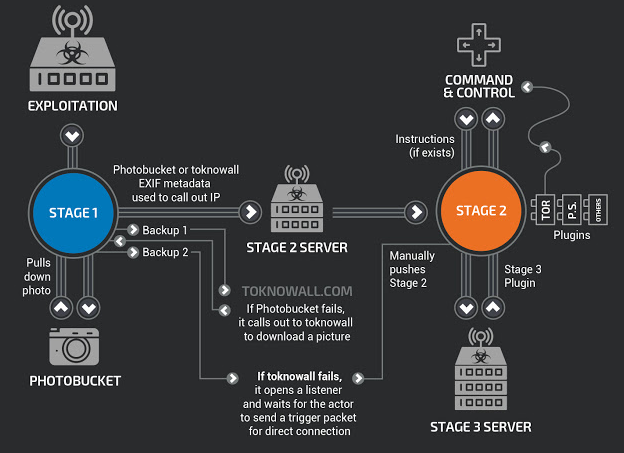
Image: Cisco
Unfortunately, there is no easy way to tell if your device is infected. If you own one of these devices and it is connected to the Internet, you should reboot (or unplug, wait a few seconds, replug) the device now. This should wipe part of the infection, if there is one. But you’re not out of the woods yet.
Cisco said part of the code used by VPNFilter can still persist until the affected device is reset to its factory-default settings. Most modems and DVRs will have a tiny, recessed button that can only be pressed with something small and pointy, such as a paper clip. Hold this button down for at least 10 seconds (some devices require longer) with the device powered on, and that should be enough to reset the device back to its factory-default settings. In some cases, you may need to hold the tiny button down and keep it down while you plug in the power cord, and then hold it for 30 seconds.
After resetting the device, you’ll need to log in to its administrative page using a Web browser. The administrative page of most commercial routers can be accessed by typing 192.168.1.1, or 192.168.0.1 into a Web browser address bar. If neither of those work, try looking up the documentation at the router maker’s site, or checking to see if the address is listed here. If you still can’t find it, open the command prompt (Start > Run/or Search for “cmd”) and then enter ipconfig. The address you need should be next to Default Gateway under your Local Area Connection.
Once you’re there, make sure you’ve changed the factory-default password that allows you to log in to the device (pick something strong that you can remember).
You’ll also want to make sure your device has the latest firmware updates. Most router Web interfaces have a link or button you click to check for newer device firmware. If there are any updates available, install those before doing anything else.
If you’ve reset the router’s settings, you’ll also want to encrypt your connection if you’re using a wireless router (one that broadcasts your modem’s Internet connection so that it can be accessed via wireless devices, like tablets and smart phones). WPA2 is the strongest encryption technology available in most modern routers, followed by WPA and WEP (the latter is fairly trivial to crack with open source tools, so don’t use it unless it’s your only option).
But even users who have a strong router password and have protected their wireless Internet connection with a strong WPA2 passphrase may have the security of their routers undermined by security flaws built into these routers. At issue is a technology called “Wi-Fi Protected Setup” (WPS) that ships with many routers marketed to consumers and small businesses. According to the Wi-Fi Alliance, an industry group, WPS is “designed to ease the task of setting up and configuring security on wireless local area networks. WPS enables typical users who possess little understanding of traditional Wi-Fi configuration and security settings to automatically configure new wireless networks, add new devices and enable security.”
However, WPS also may expose routers to easy compromise. Read more about this vulnerability here. If your router is among those listed as using WPS, see if you can disable WPS from the router’s administration page. If you’re not sure whether it can be, or if you’d like to see whether your router maker has shipped an update to fix the WPS problem on their hardware, check this spreadsheet.
Turning off any remote administration features that may be turned on by default is always a good idea, as is disabling Universal Plug and Play (UPnP), which can easily poke holes in your firewall without you knowing it). However, Cisco researchers say there is no indication that VPNFilter uses UPnP.
For more tips on how to live with your various Internet of Things (IoT) devices without becoming a nuisance to yourself or the Internet at large, please see Some Basic Rules for Securing Your IoT Stuff.
Update, June 2, 10:30 a.m. ET: Netgear provided the following statement about VPNFilter:
To protect against this possible malware, we strongly advise all NETGEAR router owners to take the following steps:
• Make sure that you are running the latest firmware on your NETGEAR router. Firmware updates include important security fixes and upgrades. For more information, see How do I update my NETGEAR router firmware using the Check button in the router web interface?.
• Make sure that you have changed your default admin password. For more information, see How do I change the admin password on my NETGEAR router?.
• Make sure that remote management is turned off on your router. Remote management is turned off by default and can only be turned on in your router’s advanced settings.To make sure that remote management is turned off on your router:
1. On a computer that is part of your home network, type http://www.routerlogin.net in the address bar of your browser and press Enter.
2. Enter your admin user name and password and click OK.
If you never changed your user name and password after setting up your router, the user name is admin and the password is password.
3. Click Advanced > Remote Management.
4. If the check box for Turn Remote Management On is selected, clear it and click Apply to save your changes.
If the check box for Turn Remote Management On is not selected, you do not need to take any action.NETGEAR is investigating and will update this advisory as more information becomes available.




I use WPA2 and a randomly generated 63 character key for the home wireless router. Also, the router firmware should be regularly checked for updates.
Any computer generated random sequence is never totally random. If someone was to use the same computer or website tool as you, they could generate the same code much faster than someone using a different computer.
It’s a physics thing.
Instead use two separate computers to each generate a 32 character code. Stitch the two codes together. Viola!
or let your computer generate a 62 character code, then manually append the sum of 10 dice rolls.
Not true. However, not entirely false.
Most PCs have very poor randomness generation.
A few websites like random.org do generate true random numbers; obviously you have the trust issue.
The Linux kernal random number generator is pretty good; the problem is feeding it true randomness that’s pretty rare on physical machines are almost non-existent on virtual machines.
The best way to “mingle” random sources is currently a hash like SHA2. The easiest way to get a little bit of true randomness is using dice … lots of them, a total of 50 rolls with as many different dice as possible for 128 bits of randomness.
It all depends on the effective length of the seed. The good pseudo-RNG’s take human input, not just what you input but the length of time between the keystrokes. But you could probably just hash everything in RAM or an arbitrary section of drive and get even better.
Plenty of ways to have very high confidence with randomness using external hardware. TrueRNG is one such device:
https://www.amazon.com/TrueRNG-V3-Hardware-Random-Generator/dp/B01KR2JHTA
This device passes all standard “randomness” tests available.
Must be convenient to type when connecting a new device … also, completely irrelevant when there is a security hole.
Instead of comparing the length of your … passwords, which at this point is completely irrelevant, because already order of magnitudes too long (why not 192 characters ?), you should focus on more relevant security aspects. Like, how you manage to remember the code (write it down on a paper ?).
lots of “random” experts here, but no one offering the practical and important advice that the SSID of the network is actually part of the hashing process. Having a common network name (like wifi) makes it much more likely that your password will end up in a rainbow table.
So pick something unique
F.B.I. with more of their F.U.D.
Is Cisco Talos also spreading FUD? Because most of the info comes from Cisco, not the FBI. The FBI just took down one of the C&C domains, but most of the research comes from Cisco.
Next month they Cisco Talos will be rambling about something else, people will panic and thousands of articles will be written Repeat !
So, if my router device is not listed, I don’t need to do this?
I believe that many routers have vulnerabilities that are little known to the owner.
I have already taken the steps recommended in Brian Krebs’s article even though it’s not listed. I’d rather be careful.
If I understand things correctly, there are several passwords for a router: WPA2 passwords for the (one or more) WiFi networks, the admin password, and (possibly) a remote administration password. I’d change them all, making sure they were all unique and complex.
Thanks, Bob.
Bob is giving good advice. Even if it isn’t listed, it is still a good idea to assure that remote control is not enabled from the WAN side, and if you have more than one computer on your LAN side, perhaps setting the router to only take administrative duty from the IP address of that computer is called for. It just helps lower your threat profile a little.
Some routers won’t let you change the user ID from that obnoxious “admin”; but if you have a complex enough password, you will probably be alright as long as there is no reason to target you otherwise.
It has been my experience that once you are identified as someone that has Intellectual Property to protect, or any of the myriad of other factors Brian brings up often on KOS, you would really have to be an expert to even have a chance of defending yourself from disruption. Spearfishing emails are the favorite vector for most bad actors, so learning how to avoid this, is a good start.
Malware can launch a take over of a router that has the default user ID and password from the factory, and do it from your infected computer; once the router is taken over your web experience will no longer be yours to control. Router manufacturers have a bad habit of putting a back door on the WAN side administration, and the crooks have been known to discover just what routers are configured this way and how to break into them from remote administration – if you have that disabled, it should block this possibility.
I found, for the Netgear R8000, that the most recent firmware seems to brick your router. Not sure why. Had to roll it back (so my network was at least functional) and now shopping for a new router. Probably time to also install a firewall that isn’t on the router.
Check pfSense (appliance)
I use a router with ” intrusion protection”, do you think that I worry about these things? Absolutely not !
Intrusion prevention is a nice marketing term.
The flaws typically circumvent the built in protection
In my book there is no such thing as intrusion prevention. Even the best gateways call it IDS, which stands for Intrusion Detection System. It may detect it the first time, if you are lucky, but if you do nothing about the first detection; you are toast.
Agree
Then youre probably infected, or a Russian disinformation agent, considering your above post about FBI FUD.
IPS is a single layer of defense. Firewall is another. Most fancier home routers have both of these and some even let you modify the rules directly and look at logs.
However, routers supplied by ISPs often have backdoor accounts created so they can perform maintenance, install approved firmware, and do troubleshooting when you have issues. You can’t access this account or change its password.
Even routers you purchase yourself, if they are for home use, have features that increase your risk such as UPnP, DNLA, remote administration, built-in VPN, and WPS. They also allow you to set up the WiFi with whatever parameters you wish, including poor passwords and inadequate encryption. Incidentally, the IPS on the router most likely is for network traffic only, not for WiFi. So it won’t detect someone snarfing all your traffic and running it through an offline attack to decrypt your PSK. What is your PSK? Is it a couple of dictionary words and a number? That makes it much easier to get your friends set up when they visit, but it is also more likely to be cracked.
The point I am trying to make is that security is not a product, it is a process.
There’s some very good advice at routersecurity.org.
Worth a look if you’re in the market to improve your router security.
One upvote for you sir!!
Re-boot early and often.
I’m mildly surprised some folks fail to realize rebooting is one of the easiest aspects of basic computer hygiene. It won’t solve everything, but it helps clean the drains, so to speak. Some devices rely on software to control power; others include a physical power switch; and some require that you disconnect the power supply. I suggest once every 24 hours is reasonable, and that can be a bit squishy.
from this story: “After resetting the device, you’ll need to log in to its administrative page … If neither of those work ….” Hmmn, not for an instant relinquishing my amateur standing, in the depths of my ignorance, it seems reasonable to me to confirm how to log onto your router’s administrative page *before* nuking the device; just sayin’.
Nuking a router’s personalized settings *doesn’t* change the log-in procedure, but this leads to a question I’ve not seen answered: Any router I’ve ever used included a procedure to export personalized settings to a file, and subsequently reload those settings utilizing the saved file. It’s unclear from this story (and others on this subject) if the nasty stuff as well as personalized settings is exported to this notional file.
Not explicitly in this story, but it’s alluded to in the mention of “internet of things”. It also comes up at least once per month on Patch Tuesday. Adobe’s Flash. While eliminating Flash from your browser(s) is agreed to be a Very Good Idea, hardware vendors frequently use free-standing versions of Flash to install hardware-specific drivers and software. Depending on the vendor and the hardware, this is difficult or impossible to avoid.
I use a digital lamp timer to turn off the router every 24 hours, then 60 Seconds later, to turn it back on. Helps keep my networks more reliable. Router/switch/access point devices also have surge protection and UPS Battery backup to help reliability in both undervolt and overvolt situations.
I have some further questions.
1. Would use of a VPN protect me against this malware attack (a) when on WiFi and (b) when connected via Ethernet to the router?
2. If the answer to 1(B) is yes, maybe I should use a VPN even on devices that are connected via Ethernet to the router. Does this make sense?
3. If I visit a public library or an airport or coffee shop or barber or friend’s house that provides WiFi, how can I protect my WiFi-connected device against the possibility that the WiFi router is infected? They can’t very well reveal to just any old Tom, Dick, or Harry what their security arrangements are.
With this news, the security advantages of a mobile hotspot loom larger.
1. No. VPN does not change the fact that your router is still connected to that telephone pole outside. And that is where the bad guys connect to find your router.
The Internet company won’t block the bad guys. Their job is to connect, not block.
If you supply your own router, check with the manufacturer and Internet service provider about keeping it updated. If the ISP supplies the router, ask if they’ll update it automatically.
Follow Krebs’ advice in the article, too.
2. See above.
If you need some help with a home system, many libraries, high schools, and junior colleges have classes in technology for adult enrichment.
If you’re running a business, hire someone with experience to come by and make sure everything is done right. Ask other members of your community or commerce group for recommendations.
3. Generally speaking, your devices won’t catch any sort of technological illness just by using free wifi. Just keep the devices updated and they should remain germ free.
Criminals can mimic a trusted business’ wifi router, looking to get your personal information. And some businesses have no respect for keeping your Internet usage a private matter.
Therefore, use caution to use only free wifi if you’re certain you’re connecting with a hotspot you trust. A friend or library should be fine.
To my way of thinking, there is a big difference between reboot and reset. Reboot only shuts down and restarts the device. The device still has the same settings. I think the better choice is to reset the device, which sets it back to factory-default settings. Your article is the only one I’ve seen that even mentions this. For folks to think that all they need to do is to restart the device is not good.
In my mind, reboot, reset, and restart all mean the same thing. Its not until you add the word “factory” in front of reset that it changes it’s meaning.
I’m a bit disappointed to find the phrase “pick something strong that you can remember” here in regards to picking a new router password.
Please use a password manager, or just write it down on a piece of paper. A post-it on the bottom of your router is fine, since that’s where in most cases there is a sticker with the factory default password anyway.
Paper is generally not remotely exploitable, so that’s a fine method for keeping sensitive stuff in a private residence. If a home invasion to get your passwords is a realistic worry, you’re in a different risk-class anyway, and fortunately that’s not something most people need to worry about.
I generally agree with you that paper is a fine place for a password, except that there are cameras everywhere that can capture that info. Keep that paper in a dark hidden area nearby.
Jesus Christ… if you have to worry about spy cameras reading over your shoulder while you write down a password in the privacy of your own home, you’re in a risk-class that THIS article is not valid for.
Does your tablet have a camera? The same question with your laptop? The same with your home security system? Is your Google or Alexa program listening for their name, is your Apple TV listening for the same call? Put on the tinfoil hat. You cannot control all of your security issues. Especially those that have not been reported on. Do you drive a GM or one of the other cars? Have process controls on your phones, any system?
Why? Companies operate under espionage rules, if we got it, someone wants it. And, there are some governments that require that the programs to run a device are known to them.
I know this is a quote but “Other QNAP NAS devices running QTS software” is just BS
All consumer QNAP NAS devices are running QTS
Without providing affected QTS version just is just spreading panic.
Nice Post! Indian Cyber Army’s the most awaited Summer Internship on cyber crime investigation and ethical hacking is live now
While the FBI isn’t too sure what VPNFilter was supposed to do, there is ample evidence that this attack was aimed at the Ukranian power grid telecommunications.
See https://blog.talosintelligence.com/2018/05/VPNFilter.html
That said, this attack was clearly built in modules, so it can be re-purposed quickly. Just because you’re not the target now doesn’t mean you won’t be in the future.
Patch your SOHO router/firewall now.
I have a R7000 but I flashed it with AdvancedTomato a few months back…
My personal router is not Internet facing, rather it gets its IP address from my ISP’s modem/router. Is it fair to assume that the only affected devices are directly Internet facing? I power-cycle both devices once a week regardless but I’m a bit curious about the extent of the intrusion. And some password changes are probably in order. Thanks for all the great info
If your ISP router gets infected, it can then infect your internal router, potentially. Best to keep both up to date and reboot both.
Thanks
one way they may have gotten in.
https://nakedsecurity.sophos.com/2015/04/13/we-told-you-not-to-use-wps-on-your-wi-fi-router-we-told-you-not-to-knit-your-own-crypto/
Before resetting to factory default, I recommend logging into the administration of the device and screen printing the setup screens, especially the ISP side. That way you know you can log in after the reset and you can get the device talking to the Internet.
Backup/take notes – if you have settings you want in the refreshed router. I have a list of CDN that only pump adds out, that are blocked at the router. Low overhead add/popup filter 🙂
Some may have VPN settings or altered LAN settings for static IP devices.
I didn’t see anyone mentioning white listing devices connected to the router. For Linksys, that is an option. Would that not keep out “invaders”?
This only keeps out local devices, not remote. It is one way to go, but really isn’t needed as much as a good secure WPA2 password. If someone is going to crack your WPA2 password and wants on, then they’ll just spoof your MAC address anyway and get in.
I’m not very tech-minded about these things, but my device is not one of those listed in the article. I have a DSL modem supplied by Verizon. I do not need a password to logon. I turn the modem off after each session and I get a new IP address each time I log back onto the computer. Is there anything I should do?
I don’t have any of the devices listed in the article. I have a DSL modem supplied by Verizon and need no password to logon. I turn the modem off after each session and get a new IP address the next time. Is there anything I should do?
You’re safe.
You mentioned only a modem. If you are not using a router, you are safe from this particular vulnerability.
Thank you, but the device is an Actiontec combination modem/router supplied by Verizon. I only use it as a modem, although other computers may be hooked up to it as well as part of a home network, but is not.
It sounds likely from your description, that your equipment is not really a firewall – even some routers that claim they are firewalls, are nothing but NAT translators and do not fit the true definition of a hardware firewall.
Make sure you have a very good software firewall on you PC, or any PC connected to the ports on your Actiontec device. You should be able to download the manual for your device online, or perhaps even Verizon provides some details, to see if you can password protect it, or even perhaps they will let you shutdown WAN side administration. I rather doubt that will be possible though, as every ISP I knew that used that brand always insisted on having administrative access to those devices, to cut down on help desk calls. In those cases, you just have to use the best practices you can to keep from getting malware that might take advantage of such a situation, or a weak firewall to reconfigure your device.
Shutting off the device after each session is not a guarantee either, as you could catch malware in a bad email or other attack vector, while online, and still end up with a pwned modem/router. Once that happens, it depends on what kind of malware they used as to whether the malware can survive another shutdown or not. Some are so virulent that they can live through all but factory resets.
Since Stage 1 is persistent and also loads Stage 2/3, the only solution is to factory reset the box. A reboot won’t fix the issue cuz the malware can just reload the modules.
That said, it’s incredibly likely that the factory reset is also only a temporary fix in at least some cases. Unless the only reason your device was compromised was the use of default passwords then you’ll also need a firmware patch to fix whatever exploit was used to gain access in the first place. Without that, it’s probably just a matter of time until it’s back.
“Cisco said part of the code used by VPNFilter can still persist until the affected device is reset to its factory-default settings.”
A reset/reboot/restart only buys time until it’s reinfected.
Let’s summarize: it’s unknown how a device is infected, there’s no way to tell if a device is infected, and the reinfection time is completely unknown.
If the reinfection time is greater than 24 hours and you reboot everyday, that might make you seem safe. But only until the reinfection time is falls below 24 hours.
Until that are patches/fixes/updates to apply, there is little to do besides reboot and panic.
Brian Krebs,
Please consider an edit. After the Cisco image, where you say to reboot the devices, your parenthetical says to unplug, wait, and re-plug one’s device. Please clarify that for the masses that you mean unplugging the *power* from the device. Yes, there are people who will just unplug whatever they first touch. I work with high-IQ professionals who have a major prejudice against technology. They love using it, but constantly declare that when it comes to doing a set-up or anything, if it’s computer-related, they don’t understand it. the prejudice is that if it has to do with any kind of administrative function on a computer or creating connections, they assume (loudly) that they can’t understand such things. Your instructions, as they now read, will get people disconnecting and reconnecting any-and-not-every connection they randomly find on the router.
A corollary of Murphy’s Law: if someone can misunderstand instructions, they will.
“I took out the router plug, but the lights are still flashing…”
“So, I sprayed the cooking oil before lighting the stove….”
“Oh, 3 teaspoons? I put 3 tablespoons.”
I am wondering if I should plug my external backup drive into the computer or the router.
So to properly perform the requisite safety measures, someone needs to do the following:
1. Logon to the affected device using the current password
2. Document existing settings so as to be able to recreate them
3. Factory reset the device – either via the UI or reset button
4. Set up a new complex password
5. Load the latest firmware
6. Restore the settings
And I’ll admit, that if there is any corruption in the existing settings, they will be reinstated. However, I don’t know the best way to communicate to home users (or even small business owners) how to differentiate “normal” from “malicious” settings.
Personally, I would not “restore” the router settings onto a newer version of firmware. I would manually type them back in, because trying to load settings from an older firmware version may not be a good experience on a later firmware version (compatibility issues).
See this article by Lawrence Abrams from BleepingComputer on why just rebooting is not enough…
https://www.bleepingcomputer.com/news/security/reboot-your-router-to-remove-vpnfilter-why-its-not-enough/
Two pieces of worrying news, firstly that this has happened – and secondly that the news to reboot the affected routers hasn’t been spread very well.
I unplug my anal vibrator so I won’t get infected by Russian agents.
Two thumbs up. Way up!!
Instead of factory resetting and then installing the firmware, I skipped the factory reset and installed the most up-to-date firmware, thereby keeping the settings.
Would this be enough or should I really do a factory reset and then install the new firmware?