Popular file-sharing site Mega.nz is warning users that cybercriminals hacked its browser extension for Google Chrome so that usernames and passwords submitted through the browser were copied and forwarded to a rogue server in Ukraine. This attack serves as a fresh reminder that legitimate browser extensions can and periodically do fall into the wrong hands, and that it makes good security sense to limit your exposure to such attacks by getting rid of extensions that are no longer useful or actively maintained by developers.

In a statement posted to its Web site, Mega.nz said the extension for Chrome was compromised after its Chrome Web store account was hacked. From their post:
“On 4 September 2018 at 14:30 UTC, an unknown attacker uploaded a trojaned version of MEGA’s Chrome extension, version 3.39.4, to the Google Chrome webstore. Upon installation or autoupdate, it would ask for elevated permissions (Read and change all your data on the websites you visit) that MEGA’s real extension does not require and would (if permissions were granted) exfiltrate credentials for sites including amazon.com, live.com, github.com, google.com (for webstore login), myetherwallet.com, mymonero.com, idex.market and HTTP POST requests to other sites, to a server located in Ukraine. Note that mega.nz credentials were not being exfiltrated.”
Browser extensions can be incredibly handy and useful, but compromised extensions — depending on the level of “permissions” or access originally granted to them — also can give attackers access to all data on your computer and the Web sites you visit.
For its part, Google tries to communicate the potential risk of extensions using three “alert” levels: Low, medium and high, as detailed in the screenshot below. In practice, however, most extensions carry the medium or high alert level, which means that if the extension is somehow compromised (or malicious from the get-go), the attacker in control of it is going to have access to ton of sensitive information on a great many Internet users.
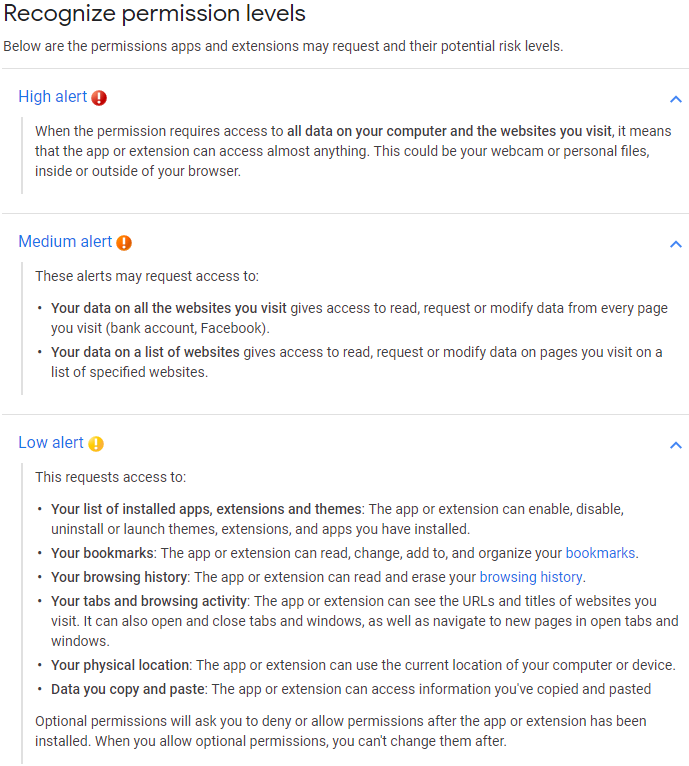
In many instances — as in this week’s breach with Mega — an extension gets compromised after someone with legitimate rights to alter its code gets phished or hacked. In other cases, control and ownership of an established extension may simply be abandoned or sold to shady developers. In either scenario, hacked or backdoored extensions can present a nightmare for users.
A basic tenet of cybersecurity holds that individuals and organizations can mitigate the risk of getting hacked to some degree by reducing their overall “attack surface” — i.e., the amount of software and services they rely upon that are potentially vulnerable to compromise. That precept holds fast here as well, because limiting one’s reliance on third-party browser extensions reduces one’s risk significantly.
Personally, I do not make much use of browser extensions. In almost every case I’ve considered installing an extension I’ve been sufficiently spooked by the permissions requested that I ultimately decided it wasn’t worth the risk. I currently trust just three extensions in my Google Chrome installation; two of them are made by Google and carry “low” risk alert levels. The other is a third-party extension I’ve used for years that carries a “medium” risk rating, but that is also maintained by an individual I know who is extremely paranoid and security-conscious.
If you’re the type of person who uses multiple extensions, it may be wise to adopt a risk-based approach going forward. In other words, given the high stakes that typically come with installing an extension, consider carefully whether having a given extension is truly worth it. By the way, this applies equally to plug-ins designed for Web site content management systems like WordPress and Joomla.
At the very least, do not agree to update an extension if it suddenly requests more permissions than a previous version. This should be a giant red flag that something is not right.
Also, never download and install an extension just because a Web site says you need it to view some type of content. Doing otherwise is almost always a high-risk proposition. Here, Rule #1 from KrebsOnSecurity’s Three Rules of Online Safety comes into play: “If you didn’t go looking for it, don’t install it.” Finally, in the event you do wish to install something, make sure you’re getting it directly from the entity that produced the software.
Google Chrome users can see any extensions they have installed by clicking the three dots to the right of the address bar, selecting “More tools” in the resulting drop-down menu, then “Extensions.” In Firefox, click the three horizontal bars next to the address bar and select “Add-ons,” then click the “Extensions” link on the resulting page to view any installed extensions.




I have that MEGA’s Chrome extension, on one of my laptops , but I think it’s a older version . None of the affected websites are used on that browser with that particular extension,
Good advice. I actually can’t remember seeing those icons regarding risk alerts when installing an extension. I’ll have to look out now.
I don’t recall seeing the risk alerts either.
@Brian: I just tried (LastPass) on win10 w/ Chrome 69, and I didn’t get any risk warnings..
I don’t either. Maybe Brian can enlighten us. I looked in my list of installed extensions and found nothing, and then went to the link for each extension (“View in Chrome Web Store”) and found nothing. I’m not seeing the warnings. That would be incredibly useful; however, I don’t have that many extensions installed and only install from major players or those who have been around for a while and focus on security.
Answered my own question (LMGTFY, well for me). From Google:
“When you install or update apps and extensions, a warning to access your data may appear.”
This only shows up on install or when you update. It’s not something you see after it is installed.
I wonder, if an extension or app wants too many permissions, can’t we just give simulated permissions like mock location, fake disk, empty history, blank clipboard?
I wanted to put this into browsers over a decade ago. It didn’t happen.
There were also proposals to do the same thing for the Android platform. I think one vendor actually did, but I’m not sure it’s still around.
what did you do to get on mozilla hof
That would be like having a virtual OS sandbox with all critical data purged/randomized. Then you would need to install the app inside it’s own copy of such a sandbox. But I don’t know if Android can allow a custom sandbox installer to take over the install process for legit Play Store apps
Installing any software from the pirate king, Kim Dotcom is just asking for trouble.
I use the 1Password extension and now I’m all paranoid about that. Sheesh
Yep. Security is all about trade-offs. That said, I think 1password is probably going to care a great deal more about protecting its extensions than most extension authors.
You can use 1Password without the extensions and just get the credentials from the app every time. Annoying I know, but safer.
I’m not sure you could pay ME to use a browser-based extension/plugin for password management.
I mean, yeah, it’s convenient, but as Brian was saying: tradeoffs.
I’ve learned to live with a lot of inconveniences as such. A lot of these are not nearly as bad as people make them out to be. Some are, but can be livable.
And you might even develop some skills you didn’t know you had. A few years ago I couldn’t recite a license plate worth of digits for you five minutes after reading it- even if it was important.
These days I can regurgitate 12-16 character passwords long-defunct from memory.
The mind’s a muscle.
I would say the fewer extensions you use, the better.
Not to be snide, but the less you use the internet the better. 😉
Firefox just started to take privacy more seriously and started blocking trackers… if only they could also block ads and referrers by defaults, it would reduce my reliance on addons….
but they also keep removing features claiming that addons are good enough so I don’t know
A Tale of Two Extensions
‘Firefox started blocking trackers.’ My recollection is that option has been available in the Privacy Settings for a while. The extension Firefox Lightbeam is installed in my computer–it’s a graphic display of potential trackers. Before I installed Electronic Frontier Foundation’s (EFF) Privacy Badger extension, Lightbeam was chock-a-block full of potential tracking graphics. After installing Privacy Badger the tracking icons disappeared. I trust EFF as much as I trust any entity, so the Badger stays. Lightbeam is installed as a check, and for the enjoyment seeing it empty brings. (-:
What about Lastpass, Ad blocker, Privacy Badger & Canvas fingerprint block?
Extensions can be a mixed bag. Those rules about only installing something you went looking for and get it from the source are key.
I do like the way some extensions do things to help security, for instance noscript, https everywhere, ublock origin, etc.
Sure for every nice one that gives the user some control over our http/s transactions there is a sea of crapware extensions to wade through, but I would rather be able to pick those nice ones occasionally wash up from a polluted ocean than not have them at all.
Comes down to having some judgment about what you install, and considering why do you need to install it I think. That again goes back to the Krebs rules 🙂
The advice I’d offer is to disable auto-update on extensions.
Google NEEDS to make 2FA mandatory on developer accounts. One person getting their account hacked shouldn’t be able to result in THOUSANDS of people getting infected with a malicious extension.
Firefox was not affected by this, the less you use the better.
Google seems to run only some superficial automated test, which of course fails as soon as the extension is able to pull external code or if the code is sufficiently obfuscated – which in case of the Mega extension was not even necessary.
Additionally it does not help that Google automatically signs the uploaded extensions with its own keys and does not allow an additional, non-transferable publisher key, which would add another barrier against extensions changed by a 3rd party.
Of course all of that wouldn’t help in cases like “Better History” or “User-Agent Switcher”, where original publisher sold the extension and the new owner itself had put fishy code inside; there needs to be an easy to understand way to *verify* that the publisher didn’t change between updates too.
My personal approach to extensions:
Not install but download and unzip them, scrutinize the source code, if necessary change it, disable auto-update in the manifest and re-pack them with my own key – or don’t install them and write my own.
Only tech savy people can inspect the code that they use. In most cases, the common people who use the extension for their day to day activity is affected.
@skeptical panda:
‘Tech savvy’ is the main point indeed.
@QuHno is the kind of extension writer who we in the old Firefox addons community would have valued highly.
Having been a member of the Firefox addons community for more than 14 years, I can say that the only way to police code that isn’t under the full scrutiny of a browser developer is to have
an active and community driven team of code scrutineers inside the tent – ie addon writers running the addons distribution centre. Only those who work the extensions code can fully understand how it can be subverted – even the WebExtensions APIs, while being less capable of subversion because they offer restricted access to the browser innards, still need code scrutineers. With the old Firefox addons ecology, those of us with fewer code skills were able to get the value of the skills of those like QuHnoe from within the community. Reviews and word of mouth counted a lot.
The Google model of automated scrutiny is a joke.
And sadly for those of us who participated in the messy anarchy of AMO (Addons Mozilla Org) for those many years, Mozilla Corp has redesigned Firefox so that most of the extensions community has departed, so there is very little participation by actual extension writers in code scrutiny. We must now trust that Mozilla developers will only allow ‘safe’ extension access and hope that some third party will pick up the inevitable exploits. Their Addons distribution model has a few extra scrutiny steps than the Google one, but has already displayed that it fails in precisely the same way:
https://www.ghacks.net/2018/08/17/mozilla-bans-23-snooping-firefox-extensions/
While I’d extended the old Firefox – over many years and with lots of reviewing from other extensions users and writers inside the community – with up to 13 very useful addons that helped with page navigation, text extraction, referrer obfuscation, network data, server credential checks, file getting, etc etc, all the things a browser wants to be capable of to make web navigation smooth and efficient, I’ve resigned myself to extending the redesigned Firefox with only 2 developer’s products:
NoScript because of a long association with a man who is fully invested in protecting browser clients from web traps, and Flagfox because it is the most carefully developed multi-tool for keeping an eye on network actors.
Trust should be hard won and it seems that the modern browser wants all trust reserved for itself while not doing all that much to deserve it.
These days if an extension offers you the world, it’s probably offering you to the world 😉
Re User-Agent Switcher, can you point to a reference regarding “fishy code inside”?
The extension seems to be available and provides some privacy through obscurity.
I can’t on a quick search (“User-Agent Switcher” phish) find anything but recommendations!
I appreciate your providing detailed, practical advice, e.g., how to know what extensions you’re running in Chrome.
Keep up the good and thorough work you do, Mr. Krebs.
One can turn off automatically updating of extensions/add-ons in Firefox.
https://blog.mozilla.org/addons/how-to-turn-off-add-on-updates/
If anyone is wary of clicking the link provided by a stranger, you can find the same information by Web-searching these words:
firefox disable extension auto update
Other browsers may have similar mechanisms to disable automatic updates of extensions or plug-ins.
It’s safer to manually update things, I’ve found.
How about security extension like noscript and ghostery?
Is there a chance that these extensions too become a security threat?
As with any code you install, do due diligence.
That doesn’t mean trust AMO (the Firefox addons certification site where NoScript is distributed) but go to the NoScript developer’s own website, support forum, and to read up on other’s opinions about NoScript – or any extension for that matter.
My opinion is worth zip, but that of credentialled security researchers – those with wide internet good standing – should fill in the trust blanks around such an addon.
Without that research, no addon deserves a place on anyone’s system.
How about extensions like noscript and ghostery which people use for added security?
Is there a chance that these extensions too become a security threat?
In that scenario, is it better not have these extensions?
I can disable the javascript from the firefox config. But that is not as convenient as the enable/disable script option of noscript.
Now I’m curious which 3 extensions you use. Are you willing to share them?
This is good advice. Thank you.
I’ve often had issues with extensions other than security, and have had to disable some of them at times, but didn’t know about the security issues.
again, this falls under user education. so long as those using computers, same as those using guns, are not educated on how to use them properly, there will be consequences.
The google bears a TON of responsibility for this.
They put the plug-in on their webstore without verifying the author is with the company they are posting the software for.
“an unknown attacker uploaded a trojaned version of MEGA’s Chrome extension, version 3.39.4, to the Google Chrome webstore.
So this means anyone cam write some malware, call it the same as some big banking software, upload it to the webstore – with no questions asked – google you are one special company.
WTF?
While you watch nonsense tv shows and grammys the soneone is stealing and doing a lot frauds and scams.
All this things will make usa go into deep debt.
The debt to federal reserve is allready high.you americans will have to back this debt either way.
Just because you borrow the money and you let it to steal someone doest make you innocent it is your duty to protect the country and bring the wrong people into justice.
All the internet and banking security is big joke , if any data leaking happening then nobody has no responsebility
If you as the american people dont do that then who you blame for this ?
You see people what you do for yourself but i guess you dont deserve even nothing better because you dont want to make it better.
Once again look how safe banking and cyber system are in europe look the cards have chips, you guys still using 101 non chip cards just swipe. Yea customets dont care if they get frauded because banks will cover you..okay but this money will be classified as debt. Because all this fraud and vulnebrity in security the debt will rise.
And internet security is joke too comanies who operating online has no obligations really to follow any policy or rules or regulations.
But the irs are just taxing people offcourse in usa there a lot good things but finacial side and cyber side is total chaos.
Now my question is why the have not fixed this mess ??
Id like to hear what the Mister Brian krebs will say about this.
Are there any security risks to having plugins “installed” but disabled? I have quite a few extensions installed, but usually just enable one when I need it, then disable it again. My understanding was that a disabled extension can’t _do_ anything, but is that correct?
I consider the red-orange-yellow alert as a joke.
Google’s priorities are upside down.
On one hand they expose extremely powerful tools (i.e. browser extensions) to hackers allowing an almost seamless distribution of their malware etc. and on the other hand they play the “red-orange-yellow” with the end users?
IMO Google has a responsibility to protect the users – if they can’t ensure the legitimate and super-controlled use of browser extensions it’s better they remove them entirely.
Another thing to think about is Chrome Sync — the feature in Chrome that syncs bookmarks, auto-fill history, EXTENSIONS, etc. across all of a user’s Chrome installations. We had a case where a user had unintentionally installed a malicious pop-up blocker extension as an extension on her home PC — and because Chrome Sync was enabled in Google Chrome on her work PC, that extension synced right across to her workstation in the office. Tokens to secure websites were then being intercepted and transferred offsite to a database accessible by hackers to take those tokens and attempt to login to the secured sites. The office workstation in question did not have local admin privileges, but that didn’t matter in this case because the extensions synced across without any user intervention.
AG, you have put into words and described what once I thought but did not give enough attention! Thanks for raising it.
Thank you for sharing that!
It has given me one more reason to keep Chrome out of our company that I can share with management – that they will be able to understand.
Thanks for bringing this issue to the forefront of my attention.
It spurred me to go through and delete about half the extensions that I had added to Chrome over time.
The article made me realize that “cool toys” can always be reinstalled later (and re-deleted again) if needed, but having them around all the time is a security exposure.
I thought WebExtensions were designed to mitigate stuff like this.
Nice blog, I found useful information on topics. I actually benefit from the blog, thanks for sharing
So, basically, after years of a status-quo of insecurity on the ‘net, it’s *still* status-quo. What’s the basic message here… don’t do anything important on the net?
Things keep going sideways – a few years ago we were being encouraged for 2FA, even using our cell phone SMA’s – now even that physical hardware is being hacked (SIM Swaps).
…oops, should have been “SMS’s”
The quickest way to check extensions is by going here chrome://extensions/