mSpy, the makers of a software-as-a-service product that claims to help more than a million paying customers spy on the mobile devices of their kids and partners, has leaked millions of sensitive records online, including passwords, call logs, text messages, contacts, notes and location data secretly collected from phones running the stealthy spyware.
Less than a week ago, security researcher Nitish Shah directed KrebsOnSecurity to an open database on the Web that allowed anyone to query up-to-the-minute mSpy records for both customer transactions at mSpy’s site and for mobile phone data collected by mSpy’s software. The database required no authentication.
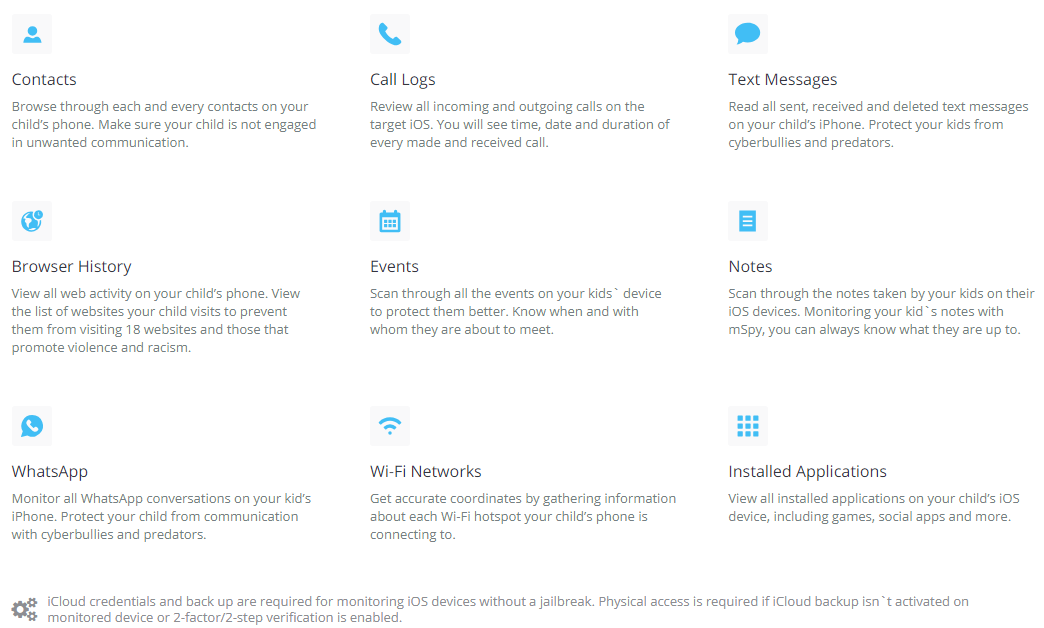
A list of data points that can be slurped from a mobile device that is secretly running mSpy’s software.
Before it was taken offline sometime in the past 12 hours, the database contained millions of records, including the username, password and private encryption key of each mSpy customer who logged in to the mSpy site or purchased an mSpy license over the past six months. The private key would allow anyone to track and view details of a mobile device running the software, Shah said.
In addition, the database included the Apple iCloud username and authentication token of mobile devices running mSpy, and what appear to be references to iCloud backup files. Anyone who stumbled upon this database also would have been able to browse the Whatsapp and Facebook messages uploaded from mobile devices equipped with mSpy.
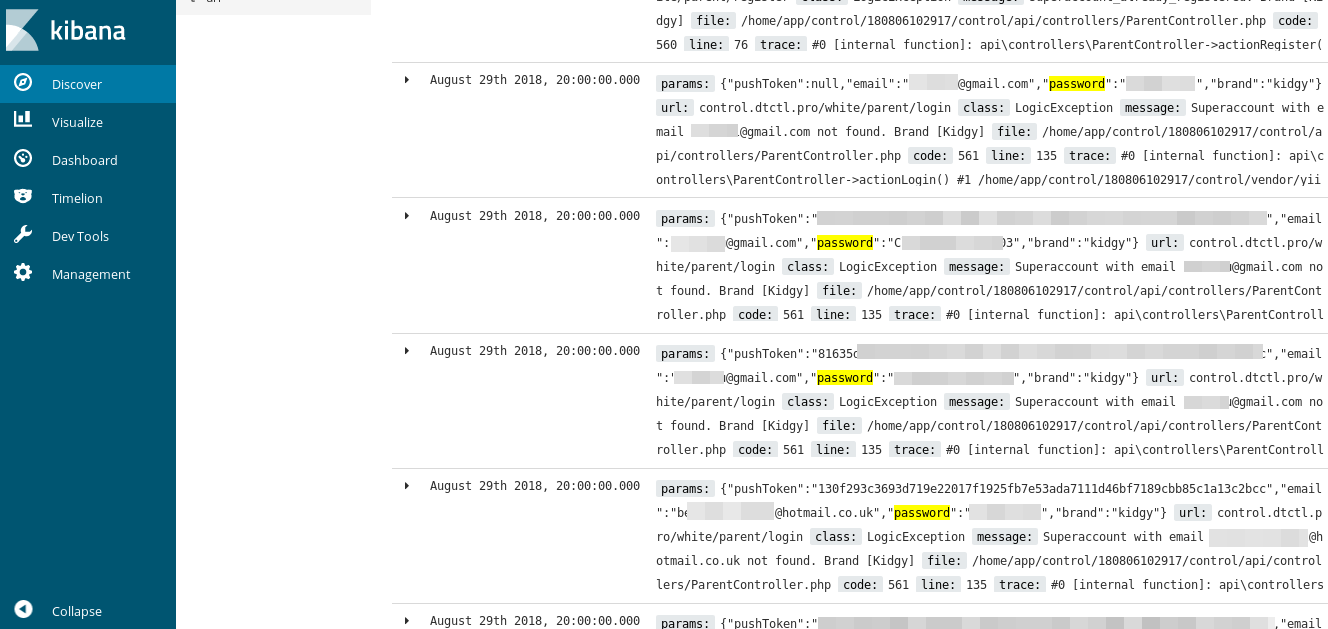
Usernames, passwords, text messages and loads of other more personal details were leaked from mobile devices running mSpy.
Other records exposed included the transaction details of all mSpy licenses purchased over the last six months, including customer name, email address, mailing address and amount paid. Also in the data set were mSpy user logs — including the browser and Internet address information of people visiting the mSpy Web site.
Shah said when he tried to alert mSpy of his findings, the company’s support personnel ignored him.
“I was chatting with their live support, until they blocked me when I asked them to get me in contact with their CTO or head of security,” Shah said.
KrebsOnSecurity alerted mSpy about the exposed database on Aug. 30. This morning I received an email from mSpy’s chief security officer, who gave only his first name, “Andrew.”
“We have been working hard to secure our system from any possible leaks, attacks, and private information disclosure,” Andrew wrote. “All our customers’ accounts are securely encrypted and the data is being wiped out once in a short period of time. Thanks to you we have prevented this possible breach and from what we could discover the data you are talking about could be some amount of customers’ emails and possibly some other data. However, we could only find that there were only a few points of access and activity with the data.”
Some of those “points of access” were mine. In fact, because mSpy’s Web site access logs were leaked I could view evidence of my own activity on their site in real-time via the exposed database, as could Shah of his own poking around.
WHO IS MSPY?
mSpy has a history of failing to protect data about its customers and — just as critically — data secretly collected from mobile devices being spied upon by its software. In May 2015, KrebsOnSecurity broke the news that mSpy had been hacked and its customer data posted to the Dark Web.
At the time, mSpy initially denied suffering a breach for more than a week, even as many of its paying customers confirmed that their information was included in the mSpy database uploaded to the Dark Web. mSpy later acknowledged a breach to the BBC, saying it had been the victim of a “predatory attack” by blackmailers, and that the company had not given in to demands for money.
mSpy pledged to redouble its security efforts in the wake of the 2015 breach. But more than two weeks after news of the 2015 mSpy breach broke, the company still had not disabled links to countless screenshots on its servers that were taken from mobile devices running mSpy.
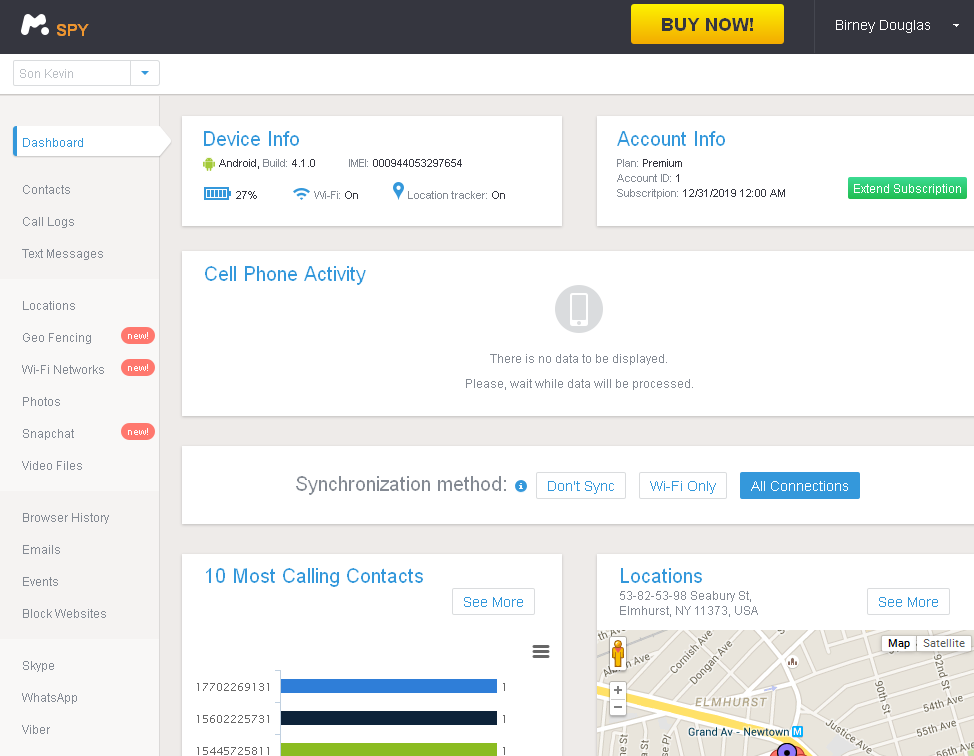
Mspy users can track Android and iPhone users, snoop on apps like Snapchat and Skype, and keep a record of everything the target does with his or her phone.
It’s unclear exactly where mSpy is based; the company’s Web site suggests it has offices in the United States, Germany and the United Kingdom, although the firm does not appear to list an official physical address. However, according to historic Web site registration records, the company is tied to a now-defunct firm called MTechnology LTD out of the United Kingdom.
Documents obtained from Companies House, an official register of corporations in the U.K., indicate that the two founding members of the company are self-described programmers Aleksey Fedorchuk and Pavel Daletski. Those records (PDF) indicate that Daletski is a British citizen, and that Mr. Fedorchuk is from Russia. Neither men could be reached for comment.
Court documents (PDF) obtained from the U.S. District Court in Jacksonville, Fla. regarding a trademark dispute involving mSpy and Daletski state that mSpy has a U.S.-based address of 800 West El Camino Real, in Mountain View, Calif. Those same court documents indicate that Daletski is a director at a firm based in the Seychelles called Bitex Group LTD. Interestingly, that lawsuit was brought by Retina-X Studios, an mSpy competitor based in Jacksonville, Fla. that makes a product called MobileSpy.
The latest mSpy security lapse comes days after a hacker reportedly broke into the servers of TheTruthSpy — another mobile spyware-as-a-service company — and stole logins, audio recordings, pictures and text messages from mobile devices running the software.
U.S. regulators and law enforcers have taken a dim view of companies that offer mobile spyware services like mSpy. In September 2014, U.S. authorities arrested a 31-year-old Hammad Akbar, the CEO of a Lahore-based company that makes a spyware app called StealthGenie. The FBI noted that while the company advertised StealthGenie’s use for “monitoring employees and loved ones such as children,” the primary target audience was people who thought their partners were cheating. Akbar was charged with selling and advertising wiretapping equipment.
“Advertising and selling spyware technology is a criminal offense, and such conduct will be aggressively pursued by this office and our law enforcement partners,” U.S. Attorney Dana Boente said in a press release tied to Akbar’s indictment.
Akbar pleaded guilty to the charges in November 2014, and according to the Justice Department he is “the first-ever person to admit criminal activity in advertising and selling spyware that invades an unwitting victim’s confidential communications.”
A public relations pitch from mSpy to KrebsOnSecurity in March 2015 stated that approximately 40 percent of the company’s users are parents interested in keeping tabs on their kids. Assuming that is a true statement, it’s ironic that so many parents may now have unwittingly exposed their kids to predators, bullies and other ne’er-do-wells thanks to this latest security debacle at mSpy.
As I wrote in a previous story about mSpy, I hope it’s clear that it is foolhardy to place any trust or confidence in a company whose reason for existence is secretly spying on people. Alas, the only customers who can truly “trust” a company like this are those who don’t care about the privacy and security of the device owner being spied upon.




Does GDPR come into play for this? Don’t they have to report it now?
If they have customers in the EU AND since it contains data that GDPR defines as private – Yes, I believe that GDPR is in play here. I hope they throw the book at these people.
Leaving a database full of your customer’s records wide open on the Internet is just unconscionable. It’s an act out of a playbook that I’ll never understand.
And if they are based in the EU and they have assets in the EU. If not, GDPR still applies, but good luck attempting a cross-border GDPR lawsuit against a foreign entity.
Thing is Readership1 – having an outstanding GDPR related law suit, or really any that are suspended in the EU makes a company far less attractive to potential investors or other companies who’d like to buy it out as they can’t expand into the EU without potentially taking a hit straight away to reputation and financially.
GDPR : the answers are Yes, and Yes.
The company is potentially liable for a very large fine, especially if an action is brought against them in the Czech Republic (see below).
The mspy website has a Privacy Policy (www.mspy.com/privacy-policy.html) which says :
“This Privacy Policy is governed by and construed with the laws of Czech Republic … Those who access the website from locations outside of the Czech Republic and European Union are responsible for compliance with local laws.
Controller for the purposes of the General Data Protection Regulation (GDPR), other data protection laws applicable in Member states of the European Union and other provisions related to data protection is: Altercon Group s.r.o., Londýnská 730/59, Prague, 120 00, Vinohrady, Czech Republic
Tel.: +420 296 245 838”
The European servers are in France, so GDPR gets them there as well.
The Privacy Policy includes this earnest entreaty, which I am sure the 60% of mspy users who are NOT concerned parents have all fully complied with –
“You warrant … that you have informed any user(s) that are 18 years old or more that the devices used by them include mSpy software and have obtained consent from such user(s) for this kind of activity … “
London based company so the UK implementation of GDPR applies. Since they offer services to EU citizens they should be represented somewhere in EU, and that country’s implementation of GDPR applies too.
mspy is not based in the UK and does not have its headquarters here. MTechnology, up until its dissolution in May 2014, supposedly had a London office but that address was only a front – a fancy address for show, but no physical presence there. If mspy are in the UK I have not been able to find them, although the assertion that they are London-based is endlessly repeated.
At the time of the 2015 data leak the BBC News report said
“(The) initial investigation is aimed at finding out whether the company, which has a London office, is based in the UK.
The BBC has been told the company is based in California.”
mspy currently has no UK office or phone number that I have been able to find.
As a side-issue, the Prague-based GDPR controller (Altercon) is also registered in the UK and has an office in Edinburgh. Companies House data shows only one name, a Ukrainian from Kiev (Andrii Kurniavtsev) as a “Person with significant influence or control”.
And Brian may be mistaken in saying that Fedorchuk is Russian, because the UK Companies House records for MTechnology give his nationality as “UK”, which could stand for Ukraine. Those records also show that Daletski previously had a correspondence address at 839 Howard Street, San Francisco.
Great article
I really think spying on your kids Snapchat is a bad idea. There are things you can’t unsee!
But, children in the US don’t have any civil rights until they’re 18; ergo, no right to privacy. It’s the parents responsibility to exercise due diligence in attempting to ensure their safety. I see no reason that parents shouldn’t have administrative access to their childs online activities. In fact, I feel, they should know if little Annie is taking nude shower pix and posting it on Snapchat, Instagram, Pinterest, etc., their pix are most likely geo-tagged and leaves them exposed to sexual predators. Children, and increasingly adults, are naive to the cyber risks inherent in internet activities. I find it absolutely disconcerting that in their attempt to provide safety by trusting so-called cyber-security firms to protect them, they ultimately are helping to expose them!
I was reading this and was thinking to myself, “sounds like what a Russian company would do.”
And then looking at names of founders, of course they are Russian 🙂
PS. Guys, I’m curious. Wasn’t iPhone supposed to protect against this kind of behavior of apps. Namely, having access to text, or call records?
PS2. Brian, it would be nice if you suggested to people how to prevent installation of such spyware on people’s phones? Any measures one needs to take so that a jealous spouse/partner didn’t install this on your phone.
Thanks for the article.
To do the text message thing on an iPhone you need to be the MitM unless they can forward all texts somewhere. Guess the latter is possible but I have yet to see that done.
Generally speaking (unless it is malware – which this technically is not) you need physical access to the device to install the software. Generally seen them put some MDM type of software on to allow this.
I’m sure there are a ton of other possibilities as mobile forensics is not my specialty but with the iPhone generally being locked down more than a Droid, it is a bit more challenging from what I have seen.
Go to a Droid and I throw my hands up and all bets are off.
How do you protect yourself – know who has access to or is using your phone besides yourself. Don’t click on crappy links.
The software requires physical access to the device if it is not vulnerable to a remote jailbreak (i.e. the user hasn’t updated their OS in a while). So, if you don’t trust those around you or those who may be in your space, keep your phone close at hand all the time. Use a complex and unique 6-digit pin that’s needed to unlock your phone.
My understanding from the last time I researched mSpy was that it utilized iCloud to provide remote monitoring ability for non-jailbroken iPhones. That is, you enter your target’s iCloud credentials into the mSpy platform and go from there. So, of course, you need to know those credentials. However, since the person spying is often a spouse or significant other, it’s not uncommon for that info to be known.
With Android, it requires physical access to the device, the unlock code (if any) and you must set it to allow apps from unknown sources (pretty easy if you already have physical access). Once installed, these apps can be hidden from the user which, IMHO, is what classifies them as true spyware, rather than parental control apps (you don’t need to hide from your kids that you’re monitoring them). Many of the security apps (e.g., Lookout) will flag spyware like mSpy, but it can be hit or miss. When I looked at this a few years ago, a surprising number of spy apps slipped through the cracks (https://www.techlicious.com/review/mobile-security-apps-perform-dismally-against-spyware/). At the time, many of the security researchers at the anti-malware companies I spoke with considered these app as PUA (“potentially unwanted applications”), rather than malicious spyware.
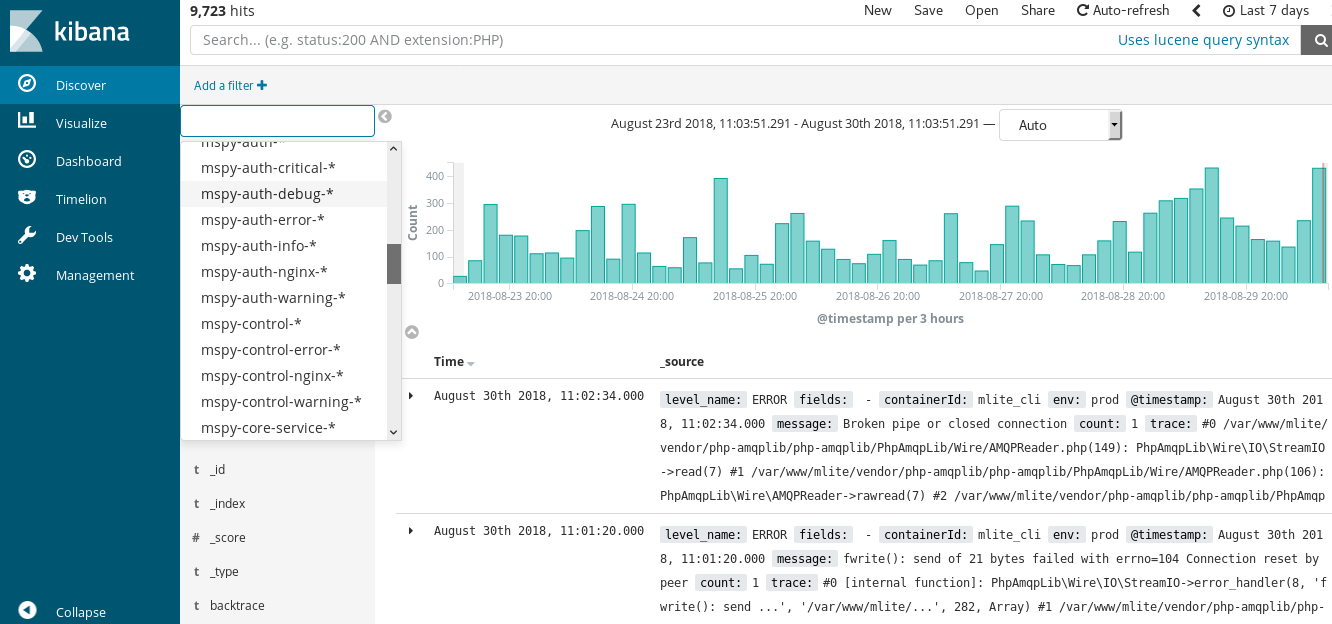
Ah, Kibana*. Its security costs extra, and it’s based around elasticsearch* which mostly doesn’t have security at all.
We use it because having something to aggregate log files is handy, but, it’s a scary system. My approach is to stick it behind a web server which manages authentication and leave elasticsearch without a public IP address. But I have no faith that our system won’t be compromised. Thankfully we shouldn’t be managing PII, so I have less to worry about.
*Disclaimer–I contribute to both, I feel that’s the minimum price to pay if not paying for a product.
Wow!
The mind boggles!
I like your takeaway, Brian, and it applies to more than just phones.
Thanks again,
Nobby
Where are we safe at the moment? The amount of fraud or mockery increases from day to day, allying itself with technology that is said to be a safety aid.
Is this the type of response you’d expect from an org regulated by GDPR?
My Phone ID is . I want to cancel mSpy because Installation problem – please refund my order. Software never worked.
Chat started
Alex Scott joined the chat
Alex Scott – Hello. My name is Alex. I will assist you today. Could you please tell us what is the reason for your cancellation request? Have you encountered any technical problems while using our software or have some personal issues occurred? Maybe we can improve something?
You — the software was never able to be installed. Additionally, it appears you just had a breach of my personal information.
Alex Scott – Would you maybe like me to help you with installation? Could you please be more specific about that?
You — please cancel service and refund prorated annual subscription amount
Alex Scott – I’m afraid no valid reason for refund was stated.
You — the software doesn’t work and it was never installed and that you then allowed your systems to be hacked and my personal information to be stolen is not sufficient reason for a prorated refund?
Alex Scott – Please note that according to our refund policy that you read and accepted during purchase, No refund can be issued to a user in case the reasons for a refund are completely beyond mSpy control. They include […] personal reasons (I’ve changed my mind, I’ve made a purchase by mistake, Software was not used, etc.); https://www.mspy.com/refund-policy.html
Unfortunately without any specifications I’m unable to open investigation about your hacked personal information.
Um, you gave some pretty sad and nonspecific reasons (the ‘breach’) for asking for a refund. He tried to help you with the non-working non-installed app. So, yea, he did as expected.
Also it reads like Alex is a bot – fine for FAQ-level troubleshooting but not much more.
Of course. “Alex Scott” rhymes with “Bot”.
They’re all failing…
https://securityaffairs.co/wordpress/75888/data-breach/family-orbit-hacked.html
I feel bad for the kids and partners who were spied on.
Conversely, I hope the radiation of 10,000 suns sear the eyeballs of those who installed this spyware on their kids and partners.
“Shah said when he tried to alert mSpy of his findings, the company’s support personnel ignored him.”
I’m SHOCKED! Shocked, I say…
Seriously, this is a pattern of behavior that is common. Someone sees a problem and reports it but the support personnel do nothing.
Why do they do nothing? Because that is their job. They are not there to fix problems. The typical support personnel contacted in a case like this are there SPECIFICALLY to dismiss people who complain but try to do so in a polite manner so no feelings are hurt.
1. Read complaint (or not–it really doesn’t matter).
2. Send boilerplate apology email and delete complaint.
3. Done.
I think that parents do need to know what their dependents are doing on their devices. In my understanding, in the US the parent, not the child, is responsible for what is done with the device. However, that does not make spying OK. I advise parents to make it clear to their children that they do not legally own the device and therefore must provide admin access and be willing to let the parent see any and all information on it. That is done openly. If the child complains about privacy invasion the response is there is no privacy on an internet connected device so they are not losing anything. Its just now the parents can see what too many miscreants (to use Brian’s word) can see.
A parent who doesn’t completely trust a child with a phone should just not give her one until she’s old enough to be trusted. If that means waiting to age 21, that’s fair!
It’s better to deny a treat than to spy. A phone is a treat. No child needs a phone of their own.
Even if you deny them a phone there are still other digital devices. I guess you could deny them all access to any device that can communicate with the internet, but that would mean no computer making it impossible to complete schoolwork.
Czech Office of Personal Data Protection
https://www.uoou.cz
Phone:
+420 234 665 800 (GDPR infoline)
E-mail:
posta@uoou.cz
Mgr. Tomáš Paták, Spokesman, phone: +420 234 665 286, e-mail: tomas.patak@uoou.cz
Mr Jiří Měsíček, International Officer, phone: + 420 234 665 235, e-mail: jiri.mesicek@uoou.cz
Folks, I think we should regard two sides. Since been using the app for 4 months, I was shocked. I thought my teen would know what I was checking on her all this time. Anyway, here’s how they excuse themselves: https://blog.mspy.com/dont-panic-your-data-is-safe-blog-mspy/
A spy app that gives the physical location of the cell phone of someone in a confidential woman’s shelter puts a lot of people at risk.
These secret shelters exist specifically because the women in them are escaping violent men who are likely to try to find those women and willing to kill themselves, their partners, and anyone else nearby once they find them.
mSpy’s blog article about this issue amounts to a hilarious list of lame excuses and downright lies which are unlikely to convince anybody with half an ounce of sense.
https://blog.mspy.com/dont-panic-your-data-is-safe-blog-mspy/
mSpy has a Wikipedia entry which was originally created by somebody who was later permanently banned for being a paid editor.
This is an interesting topic. I’m glad that I saw this article.
https://en.wikipedia.org/wiki/Los_Alamos_National_Laboratory