The owner of a Swedish company behind a popular remote administration tool (RAT) implicated in thousands of malware attacks shares the same name as a Swedish man who pleaded guilty in 2015 to co-creating the Blackshades RAT, a similar product that was used to infect more than half a million computers with malware, KrebsOnSecurity has learned.
At issue is a program called “WebMonitor,” which was designed to allow users to remotely control a computer (or multiple machines) via a Web browser. The makers of WebMonitor, a company in Sweden called “RevCode,” say their product is legal and legitimate software “that helps firms and personal users handle the security of owned devices.”
But critics say WebMonitor is far more likely to be deployed on “pwned” devices, or those that are surreptitiously hacked. The software is broadly classified as malware by most antivirus companies, likely thanks to an advertised feature list that includes dumping the remote computer’s temporary memory; retrieving passwords from dozens of email programs; snarfing the target’s Wi-Fi credentials; and viewing the target’s Webcam.
In a writeup on WebMonitor published in April 2018, researchers from security firm Palo Alto Networks noted that the product has been primarily advertised on underground hacking forums, and that its developers promoted several qualities of the software likely to appeal to cybercriminals looking to secretly compromise PCs.
For example, RevCode’s website touted the software’s compatibility with all “crypters,” software that can encrypt, obfuscate and manipulate malware to make it harder to detect by antivirus programs. Palo Alto also noted WebMonitor includes the option to suppress any notification boxes that may pop up when the RAT is being installed on a computer.
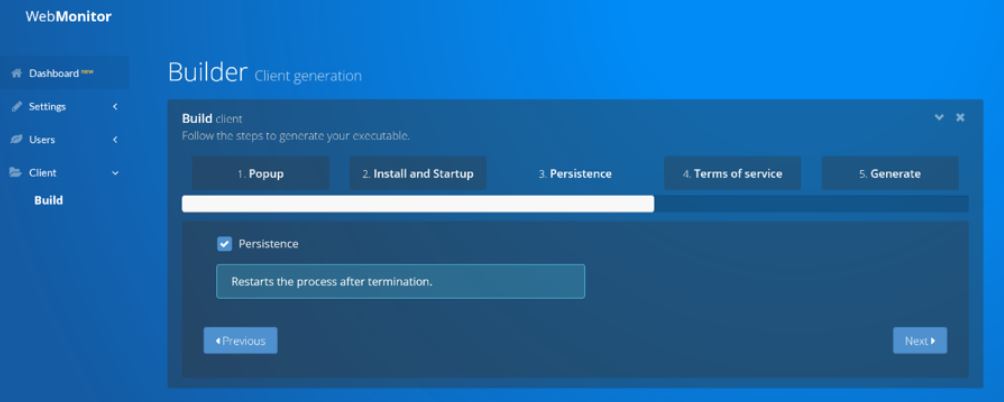
A screenshot of the WebMonitor builder panel.
RevCode maintains it is a legitimate company officially registered in Sweden that obeys all applicable Swedish laws. A few hours of searching online turned up an interesting record at Ratsit AB, a credit information service based in Sweden. That record indicates RevCode is owned by 28-year-old Swedish resident Alex Yücel.
In February 2015, a then 24-year-old Alex Yücel pleaded guilty in a U.S. court to computer hacking and to creating, marketing and selling Blackshades, a RAT that was used to compromise and spy on hundreds of thousands of computers. Arrested in Moldova in 2013 as part of a large-scale, international takedown against Blackshades and hundreds of customers, Yücel became the first person ever to be extradited from Moldova to the United States.
Yücel was sentenced to 57 months in prison, but according to a record for Yücel at the U.S. Federal Bureau of Prisons, he was released on Nov. 1, 2016. The first advertisements in hacker forums for the sale of WebMonitor began in mid-2017. RevCode was registered as an official Swedish company in 2018, according to Ratsit.
Until recently, RevCode published on its Web site a value added tax (VAT) number, an identifier used in many European countries for value added tax purposes. That VAT number — first noted by the blog Krabsonsecurity.com (which borrows heavily from this site’s design and banner but otherwise bears no relation to KrebsOnSecurity.com) — has since been removed from the RevCode Web site and from historic records at The Internet Archive. The VAT number cited in that report is registered to Alex Yücel, and matches the number listed for RevCode by Ratsit AB.
Yücel could not be immediately reached for comment. But an unnamed person responded to an email sent to the customer support address listed at RevCode’s site. Presented with the information and links referenced above, the person responding wrote, “nobody working for/with RevCode is in any way related to BlackShades. Anything else suggesting otherwise is nothing but rumors and attempts to degrade our company by means of defamation.”
The person responding from the RevCode support email address contended that the Alex Yücel listed as owner of the company was not the same Alex Yücel convicted of co-authoring Blackshades. However, unless the Ratsit record is completely wrong, this seems unlikely to be true.
According to the Ratsit listing, the Alex Yücel who heads RevCode currently lives in a suburb of Stockholm, Sweden with his parents Can and Rita Yücel. Both Can and Rita Yücel co-signed a letter (PDF) in June 2015 testifying to a New York federal court regarding their son’s upstanding moral character prior to Yücel the younger’s sentencing for the Blackshades conviction, according to court records.

A letter from Alex Yücel’s parents to the court in June 2016.



Someone should mail his parents a link to this article.
The real shame is that just looking at the website, the software looks good enough to stand on its own as a legitimate remote access tool. I guess that extra dark market money is just too tempting sometimes.
Wow, the question I have, Brian, what the heck is `Krabsonsecurity.com`? Did you do any investigative work on that and why are they ripping you off like that?
It’s Mr. Krabs doing security pieces, though he’s much better at following the money trail. Sorry, terrible joke.
In all honesty, I am in the same boat and wanted to know how legitimate it is. I didn’t go to the site at all because I didn’t trust it. But it’s interesting nonetheless.
KrabsOnSecurity is a site that originated as a joke years ago by me, but I decided to turn it into a serious blog and posted my malware analysis work there.
To answer Dennis, I was the first to notice this (as pointed out by Krebs himself when he said that this was “first noted” by me), after which I emailed Krebs a while ago regarding this information. So no, I did not “rip” Krebs off.
You believe your blog is serious? Impersonating Mr. Krebs using a cartoon figure from Spongebob Squarepants? Nuff’ said.
I don’t know, you tell me. I provide informative articles on malware, I reverse engineer them, I find out about things like Revcode bring ran by Blackshades’ developer (keep in mind that it was me who emailed Krebs about this lol). So it’s more serious than you have ever been in your entire life probably.
Let’s sing together Spongy Spongebob!
Fun is when you
Fun is it’s like, it’s kind of, sort of like
What is fun?
Let me spell it for you!
F is for friends who do stuff together
U is for you and me
N is for anywhere and anytime at all
Oh yeah. Your blog is so serious.
You don’t have a reason to hide, do you? Very credible!
How’s Plankton doing these days btw.?
Doesn’t matter what you “provide” on that site, nobody will ever take you seriously (except maybe 13-14 year olds, which you definitely sound like).
13 year olds aren’t interested in articles reversing malware. It’s over their heads. And likely over yours as well.
https://www.youtube.com/watch?v=SDKwmbqxS64
His parent’s letter to the court reads like a form letter: “we’re saddened”, “our son is naïve”, “he learned his lesson”, and “it won’t happen again.” Closing with the obligatory appeal to the judge’s fairness.
Judges must read hundreds of this same letter.
People should go with OmniRAT. I don’t trust Webmonitor, after all that what happened with blackshades.
People should grow a spinal column and stop being sponges.
Alex Yücel parents are in serious denial about their sons criminal activity.
Well I guess they just want their son back. I mean, as a swedish citizen, would you like being extradited to another country, in another part of the world, where you maybe haven’t even been before.
In the end they’re just living their role as parents.
Will the real Alex Yücel please stand up?!
“Palo Alto also noted WebMonitor includes the option to suppress any notification boxes that may pop up when the RAT is being installed on a computer.”
Every decent installer includes install switches to install silently… this is not a red flag.
RevCode is absolutely intended to be used as malware; this was clear to me even before knowing the Blackshades connection (which should eliminate any benefit of the doubt you give even by itself).
Anything evidential to back that up, any other than just “it was clear to you”? Also where does this article indicate that it’s “absolutely intended to be used as malware”?
Are you sure that what you’re saying is not anything but defamation Mr. PatricK?
“defamation” huh? Kinda sounds like maybe you work for Revcode, since that’s exactly what they said.
Being able to activate the webcam and microphone without permission from the user, is a red flag. Being able to dump passwords from browsers etc, is another big red flag. This is designed with features only criminals would have a need for. Its a malware tool designed and used by criminals, give up your BS already.
No, but “the product has been primarily advertised on underground hacking forums” is definitely a red flag. What legitimate enterprise would want that business?
What’s the point of this article when the company is obviously registered in Sweden, where all IT-based companies are subject to inspection by Datainspektionen (The Swedish Data Protection Authority (DPA) ) to ensure that local laws are followed?
The government supports the nature of the company’s activities, which is stated on the Ratsit page in Swedish: “Bolaget skall erbjuda programvara för fjärrstyrning och övervakning av trådlösa och stationära enheter via webbgränssnitt samt därmed förenlig verksamhet.”, translating: “The company shall offer software for remote control and monitoring of wireless and stationary devices via web interfaces”.
Unfortunately for RevCode… selling products internationally means they need to follow more than just the law of local jurisdiction.
That’s the nature of the Internet… even with software and without the need to send physical products through the mail… they can still be held criminally liable for where they sell their products.
I own and operate a VPN service since about 6 years.
The use of VPN is illegal in some countries, including Belarus. Are you saying that my company has to follow the laws of Belarus, or could it be that people from Belarus purchasing a VPN subscription from my company are responsible to follow their local laws?
VPN usage? So not selling software?
That is very different. Harder to enforce even if they wanted to. It is illegal to pirate movies… but law enforcement mostly goes after the supply side, not the demand/consumer side.
Yes we sell a software client that customers use to connect to our VP service with. Are you making up your own backyard laws here? Provide some sources instead.
Sources to what? What are you asking? If it is illegal to sell your VPN software to people in some countries even even when it is legal in your home country?
“YÜCEL, 24, a Swedish national, was arrested in Moldova in November 2013. He was the first defendant ever to be extradited from Moldova to the United States. In addition to the prison term, YÜCEL was sentenced to three years’ supervised release, and forfeiture of $200,000 and the computer equipment used.
Brendan Johnston, an administrator for the Blackshades organization, pled guilty in November 2014, before U.S. District Judge Jesse M. Furman to conspiracy to commit computer hacking. On June 19, 2015, Johnston was sentenced to one year and one day in prison.”
Source: FBI
https://www.fbi.gov/contact-us/field-offices/newyork/news/press-releases/swedish-co-creator-of-blackshades-malware-that-enabled-users-around-the-world-to-secretly-and-remotely-control-victims-computers-sentenced-to-57-months-in-prison
Your comparison to weak/unenforced laws against VPN software in Belarus is not relevant here.
That is mostly likely a law intended to be tacked onto other criminal charges. Has anyone been charged for just using a VPN, with no other charges? Provide sources.
Getting back to the issue at hand, selling internationally does have legal consequence in foreign jurisdictions. That is why extradition is a thing…. and that is why this article exists… because this guy plead guilty to this crime before. Not in Sweden, not in Moldova… but in the US. Why the US? Because he sold malware to customers in the US.
So your theory that his activity being “okay with Sweden”, doesn’t actually protect him from US law.
I don’t necessarily agree that weapon makers should be held responsible for the actions of those who use those weapons. But they aren’t completely blameless either.
And hiding behind local laws doesn’t work when you want to make international money.
What you don’t seem to understand from this is that a venue has to be established. That is specified in the overt acts. Read the indictment.
With Blackshades, the author was conspiring with other US citizen to commit crimes, which established a venue.
A venue establishes in which state an offense may be tried. Then there has to be an intent as well to commit the crime. In the US, it must be proven beyond a reasonable doubt that someone intends and knowingly commits an offense. The evidence to support intentions are commonly derived from sting operations or other records, such as chat logs.
That is exactly my understanding. That when a customer in the US purchases and receives technical support for a product.. that is what makes the product seller criminally culpable.
Yes, it requires a lot of evidence from the prosecution to proceed and get an extradition… but it has been done, and could be done again with RevCode.
It isn’t automatic guilt just selling malware to someone in the US… the prosecution has to make the case. And this article is shows one of the pieces of evidence against him, as it shows a history of criminal behavior.
It is possible that prosecutors need only an email from a single US based customer asking about one of the features that has no legitimate use, but rather is obviously used only for illegal use… then if someone from RevCode responds, supporting that feature… boom, there could be charges of “conspiracy”.
It is a myth that conspiracy charges need to have all parties fully knowledgeable of the entire attack. RevCode doesn’t need to know who is being attacked or why. If they support someone who hacking by giving them the tools that cannot reasonably used for anything but hacking… they are at legal risk.
Intent is a tricking thing to prove, but they do it all the time on pretty thin evidence. This idea that being a seller in a country that doesn’t care what they are selling, shields them from US law, is the myth. Prosecutors in the US may not have an open/shut case every time… but they aren’t going to just back off.
Dear Brian,
You are partially correct while your understanding of the U.S federal criminal law is flawed.
First off, a foreign company can’t be criminally held responsible in the U.S, but it’s the persons and their acts.
The article aims to establish the person behind Revcode. How is that evidence or of any help to investigators for that matter? An investigator can easily find out who the person behind Revcode is by means of international channels, and without the need to read your article. Secondly, a criminal record is not evidence. In fact, in a U.S court, prosecutors can’t use evidence of prior convictions to prove a defendant’s guilt or tendency to commit crimes.
In a federal U.S indictment, an identified person or group is being accused along with their individual overt acts, not a whole company (that’s a lawsuit). What if the author behind Revcode only invested and registered the company in their name, while a group of others develop, carry out marketing and provide support?
Joe != Brian
Sorry, although I wrote RevCode, I do mean Yücel specifically, I just wanted to type quickly without umlauts.
It is always up to the judge to decide what is or is not admissible as evidence.
”
In deciding whether to admit evidence of a prior conviction, courts consider the following factors:
the type of crime
whether the crime indicates that the defendant is untruthful
how much time has passed since the conviction (convictions that happened 10 years or longer ago are often inadmissible)
the length of imprisonment, if any
the defendant’s age at the time of the conviction
whether the defendant’s credibility is central to the current case
the importance of the defendant’s testimony in the current case (the defendant may refuse to testify if evidence of the prior conviction will come in), and
the defendant’s conduct since the prior conviction.
”
You make the mistake of thinking in black/white terms. Prosecutors WILL try to make the case regardless of whether the defendant, the defense, or those sympathetic think it is “fair”.
“What if the author behind Revcode only invested and registered the company in their name..”
Good point. Which is why investigations happen.
I don’t suggest that prosecutors “need” articles like this for evidence. But rather that the evidence that prosecutors will use, is the same as what Krebs has found. At most, law enforcement is often alerted to easier cases to prosecute. Why would the US go after some random malware provider, when they can get Yücel handed on a plate for another conviction with half the effort. They are busy and do like the lower hanging fruit.
Revcode doesn’t ship any software. WebMonitor is fully web-based. Where are you getting your information from? Aren’t you a journalist? Try to follow the codex and attach some sources. To be criminally liable, especially in the US, there has to be an intent behind the offense. I don’t see how selling and operating legally from Sweden would render the company liable in another jurisdiction.
“Revcode doesn’t ship any software.”
I said specifically, “without the need to send physical products through the mail… they can still be held criminally liable for where they sell their products.”
Software is still a product. And subject to laws for both the origin and destination.
“Aren’t you a journalist?”
No, that would be Brian.
To be criminally liable, especially in the US, there has to be an intent behind the offense.”
Yeah, that is the whole point of the article and the Palo Alto Networks write-up. They are making the case that the author of WebMonitor DOES have intent to have that product break the law. Many of the key features don’t have lawful purpose, and the argument is that there must be intent for unlawful use.
“I don’t see how selling and operating legally from Sweden would render the company liable in another jurisdiction.”
Maybe if they made a sincere effort to prevent sale outside of Sweden, you may have a point.
But there is no such effort, and in fact, RevCode does attempt to sell to buyers all over the world, without regard to the legality. That is a mistake.
Yücel has already be extradited for similar offenses… where the US law was applicable even without setting foot in the US. Where legality of local jurisdiction didn’t protect him.
This idea that is being spread that only local jurisdiction matters, is a myth. Kinda like people who believe they can escape the highway patrol when they cross state borders.
The company Revcode is registered in Sweden as providing services, not products. That is what the Swedish government has listed it as and should be respected. The generated client you may be referring to will prompt for approval once executed.
Services will likely be even worse from a legal standpoint.
That suggests a more hands on role into the activity of the malicious actor.
If someone uses a product for nefarious purposes, at least there is a plausible deniability. As a service… there is probably a lot more legal liability.
Krebs has uncovered a few DDOS for Hire “services”. And they get taken down even quicker and with much less ambiguity than just a malware software provider.
And if they registered as providing a service, but instead are selling software licenses as a product, that could eventually get them in other types of trouble.
There are all sorts of shady business practices that these small businesses try to get away with. Being registered as a business does not get “respect” or even legitimacy. It just means nobody has caught them yet.
When they do get caught, he will just create a new company.
I’m in for the legal use since I got WebMonitor about year ago. It’s one of the best administration tools I’ve ever used. All web based and no need to play around with downloading or installing software.
Oh. Well in that case….
If you can’t grasp the reason for this article, then you failed Reading Comprehension 101
The message behind this article goes deeper than you can comprehend.
Given Revcode obeys their local laws, as so is practically forced anyway, then I see no point with this article at all, regardless of the people behind the company.
It’s sad that the article is attempting to dishonor the Swedish government’s decision to declare Revcode as a legal entity. Seems to be like a political thing going on here.
There are plenty of instances where a person or company is breaking laws in other countries, yet the home company doesn’t really have laws that make it illegal, or even unwilling to enforce.
Tax shelters are often legal in their home countries. And many countries have more lenient laws for activity that would are seen as criminal elsewhere.
This is why extradition is often used for people who wouldn’t even be convicted in their own country.
The Internet makes the world smaller. And selling products globally means that the company can be subject to the laws of other countries… not just the where the headquarters is located.
the guy maybe had time to study the law and know what to do this time and not conspire with Americans.
after all as long as one stay away from America and have no ties to them, will always be good.
Ouch, come on. Posting parents letters. That’s way under the belt and a magnitude beyond unbiased. Where is the honor, Krebs?
That letter was sent to court, and thus, open and public record. Also, it is material to this legal case.
It is not like Krebs went fishing on Facebook to get photos of the parents or any personal information. The parents wanted this letter to be seen to influence the judgement.
Using the letter in an article about the case, is perfectly relevant.
Ouch, come on. Posting parents letters. That’s way under the belt and a magnitude beyond unbiased. Where is the honor?
Agreed. That wasn’t really necessary. Someone hanging out my mother like that as if we lived in Saudi Arabia, wow.
Unbiased? Below the belt? It’s public record. Anyone can access it.
More to the point, the nice people at RevCode could have just told the truth instead of lying to me, and I wouldn’t have needed to call BS on their lies.
That letter was sent to court, and thus, open and public record. Also, it is material to this legal case.
It is not like Krebs went fishing on Facebook to get photos of the parents or any personal information. The parents wanted this letter to be seen to influence the judgement.
Using the letter in an article about the case, is perfectly relevant.
You can’t have it both ways, keeping this private, but submitting it to court.
It is clear that BK is attempting to make the allegation that a former prisoner of the US has returned to criminal behavior.
So why is there no mention of an attempt to gather comments from the former defense counsel (or current lawyer)?
Was comment sought from the lawyer (or government agency) who handled the incorporation of RevCode, to confirm the identity of the principal?
Finally, re: the letter from the parents. I don’t feel a current public interest is served by its inclusion here.
P.S. Why wasn’t a comment sought from the podcaster who brought the 2014 charges against this guy? He has an opinion on everything these days.
Why do assume that every attempted contact should be included in the article? There is nothing to say until there is something to say.
Hack journalists often publish their attempts to contact as a means of bias to suggest there is a cover up or sneaky denial going on.
It is far better for journalist to NOT include every contact that has not yet responded for comment.
Did you even read the article?
BK did include a denial from the support email person and that “Yücel could not be immediately reached for comment.”
It’s perfectly reasonable to write the truth, even if it doesn’t prove the central premise or it just casts shade. That doesn’t make someone a hack.
Yücel is the main subject of the article. So of course info about being reached for comment is relevant.
But it sounds you are demanding all of Kreb’s records regarding everyone he has tried to contact.
“there no mention of an attempt to gather comments from the former defense counsel (or current lawyer)”.
“Why wasn’t a comment sought from the podcaster…[from 2014]”
Geez… you are very demanding of Kreb’s to provide notes and evidence of his investigation.
Allahu akbar w Inshallah !!!!!
*vest bomb explodes*
Allah w akbar to our beloved brother Brian.
Dear Krebs, I don’t think your methods of investigation would work on someone above 5 years old mentally.
As in, most grown ups have a good idea how to separate real life identity from online, especially from public view.
You waste your time chasing amateurs to get some pat on that back as a “security researcher”, it’s kind of pathetic.
Your like a mall cop that calls the real cops on the kids smoking outside.
And what kind of “security researcher” lets all users get tracked by google analytics??
Actually, I have found that *very* few cybercriminals are good at operational security. What’s more, I have yet to find one that couldn’t be tracked down in real life with enough effort and time spent on the research.
The truth is most cybercriminals do not grow up thinking they want to be cybercrooks. They get into it gradually, and during that transition period almost always fail to fully airgap who their are in real life from who they are online. I have yet to find a single example I’ve pursued to suggest otherwise.
By the way, this includes lazy and sloppy criminals as well as some of the most accomplished crooks out there. Sometimes, it takes days of research. In other cases, it’s taken many months.
Nonetheless, in part due to the prolific nature of their activities and the frequency with which they must establish new identities, domains and other forms of identity online that leave trails, it’s rare to encounter someone who is extremely good at opsec. The rare few that fit this profile are almost without exception sociopaths.
By the way, if anyone doubts what I have just said here, check out some of the cybercriminals exposed in my Breadcrumbs series. You will find some extremely well-resourced and accomplished criminals who get found out because they made some fairly rudimentary mistakes.
https://krebsonsecurity.com/category/breadcrumbs/
It’s sometimes said the average person who commits murder leaves dozens of clues behind. I would venture to say that the average person who commits cybercrimes on a regular basis probably leaves many times more clues behind.
You’re right. I wrote a similar comment a few months ago about the origins of many of these criminals being their undoing (though admittedly I learned some of it from you). 🙂
https://krebsonsecurity.com/2019/01/three-charged-for-working-with-serial-swatter/#comment-482432
“Nonetheless, in part due to the prolific nature of their activities and the frequency with which they must establish new identities, domains and other forms of identity online that leave trails, it’s rare to encounter someone who is extremely good at opsec. The rare few that fit this profile are almost without exception sociopaths.”
What about journalists in oppressive regimes, intelligence operatives, and other non-criminals who must routinely practice such aggressive OPSEC?
Some people get really good at it, without needing to be blackhat.
Officially registered companies are often bad actors. Registering your company doesn’t grant you immunity from scrutiny.
This is especially true if the company is founded by an ex-con who appears to be doing the same thing that got him locked up in the first place. To top it off, he was sloppy. At the very least, take this article as a lesson in opsec.
I don’t support the legal theory that devs should be found in violation of law for developing tools that could be used by bad actors any more than I support lawsuits against gun manufacturers. But this *is* relevant news in the community.