Almost weekly now I hear from an indignant reader who suspects a data breach at a Web site they frequent that has just asked the reader to reset their password. Further investigation almost invariably reveals that the password reset demand was not the result of a breach but rather the site’s efforts to identify customers who are reusing passwords from other sites that have already been hacked.
But ironically, many companies taking these proactive steps soon discover that their explanation as to why they’re doing it can get misinterpreted as more evidence of lax security. This post attempts to unravel what’s going on here.
Over the weekend, a follower on Twitter included me in a tweet sent to California-based job search site Glassdoor, which had just sent him the following notice:
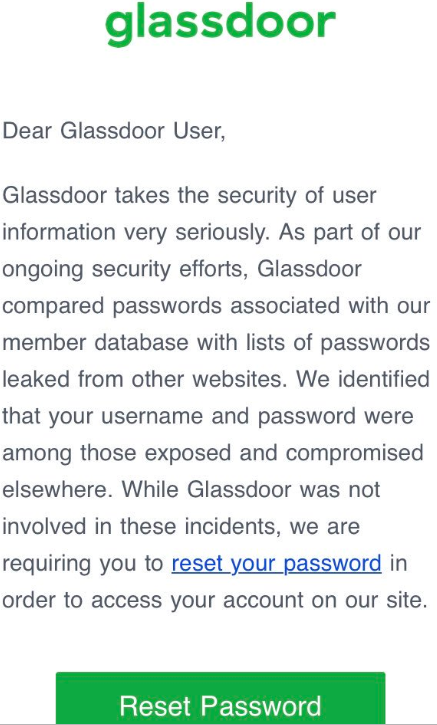
The Twitter follower expressed concern about this message, because it suggested to him that in order for Glassdoor to have done what it described, the company would have had to be storing its users’ passwords in plain text. I replied that this was in fact not an indication of storing passwords in plain text, and that many companies are now testing their users’ credentials against lists of hacked credentials that have been leaked and made available online.
The reality is Facebook, Netflix and a number of big-name companies are regularly combing through huge data leak troves for credentials that match those of their customers, and then forcing a password reset for those users. Some are even checking for password re-use on all new account signups.
The idea here is to stymie a massively pervasive problem facing all companies that do business online today: Namely, “credential-stuffing attacks,” in which attackers take millions or even billions of email addresses and corresponding cracked passwords from compromised databases and see how many of them work at other online properties.
So how does the defense against this daily deluge of credential stuffing work? A company employing this strategy will first extract from these leaked credential lists any email addresses that correspond to their current user base.
From there, the corresponding cracked (plain text) passwords are fed into the same process that the company relies upon when users log in: That is, the company feeds those plain text passwords through its own password “hashing” or scrambling routine.
Password hashing is designed to be a one-way function which scrambles a plain text password so that it produces a long string of numbers and letters. Not all hashing methods are created equal, and some of the most commonly used methods — MD5 and SHA-1, for example — can be far less secure than others, depending on how they’re implemented (more on that in a moment). Whatever the hashing method used, it’s the hashed output that gets stored, not the password itself.
Back to the process: If a user’s plain text password from a hacked database matches the output of what a company would expect to see after running it through their own internal hashing process, that user is then prompted to change their password to something truly unique.
Now, password hashing methods can be made more secure by amending the password with what’s known as a “salt” — or random data added to the input of a hash function to guarantee a unique output. And many readers of the Twitter thread on Glassdoor’s approach reasoned that the company couldn’t have been doing what it described without also forgoing this additional layer of security.
My tweeted explanatory reply as to why Glassdoor was doing this was (in hindsight) incomplete and in any case not as clear as it should have been. Fortunately, Glassdoor’s chief information officer Anthony Moisant chimed in to the Twitter thread to explain that the salt is in fact added as part of the password testing procedure.
“In our [user] database, we’ve got three columns — username, salt value and scrypt hash,” Moisant explained in an interview with KrebsOnSecurity. “We apply the salt that’s stored in the database and the hash [function] to the plain text password, and that resulting value is then checked against the hash in the database we store. For whatever reason, some people have gotten it into their heads that there’s no possible way to do these checks if you salt, but that’s not true.”
CHECK YOUR ASSUMPTIONS
You — the user — can’t be expected to know or control what password hashing methods a given site uses, if indeed they use them at all. But you can control the quality of the passwords you pick.
I can’t stress this enough: Do not re-use passwords. And don’t recycle them either. Recycling involves rather lame attempts to make a reused password unique by simply adding a digit or changing the capitalization of certain characters. Crooks who specialize in password attacks are wise to this approach as well.
If you have trouble remembering complex passwords (and this describes most people), consider relying instead on password length, which is a far more important determiner of whether a given password can be cracked by available tools in any timeframe that might be reasonably useful to an attacker.
In that vein, it’s safer and wiser to focus on picking passphrases instead of passwords. Passphrases are collections of multiple (ideally unrelated) words mushed together. Passphrases are not only generally more secure, they also have the added benefit of being easier to remember.
According to a recent blog entry by Microsoft group program manager Alex Weinert, none of the above advice about password complexity amounts to a hill of beans from the attacker’s standpoint.
Weinert’s post makes a compelling argument that as long as we’re stuck with passwords, taking full advantage of the most robust form of multi-factor authentication (MFA) offered by a site you frequent is the best way to deter attackers. 2fa.directory has a handy list of your options here, broken down by industry.
“Your password doesn’t matter, but MFA does,” Weinert wrote. “Based on our studies, your account is more than 99.9% less likely to be compromised if you use MFA.”
Glassdoor’s Moisant said the company doesn’t currently offer MFA for its users, but that it is planning to roll that out later this year to both consumer and business users.
Password managers also can be useful for those who feel encumbered by having to come up with passphrases or complex passwords. If you’re uncomfortable with entrusting a third-party service or application to handle this process for you, there’s absolutely nothing wrong with writing down your passwords, provided a) you do not store them in a file on your computer or taped to your laptop or screen or whatever, and b) that your password notebook is stored somewhere relatively secure, i.e. not in your purse or car, but something like a locked drawer or safe.
Although many readers will no doubt take me to task on that last bit of advice, as in all things security related it’s important not to let the perfect become the enemy of the good. Many people (think moms/dads/grandparents) can’t be bothered to use password managers — even when you go through the trouble of setting them up on their behalf. Instead, without an easier, non-technical method they will simply revert to reusing or recycling passwords.




Great information as usual. Question – Most of the sites I deal with only give me two or three unsuccessful tries at login without shutting me out for either a time period or other cooling off period. How are hackers able to perform multiple scans to crack passwords and not get stopped after a few tries?
@Robert: If the attacker is credential stuffing, they’re trying many accounts with 1 password each. It’s not the same as cracking the passwords. That’s one failed login for thousands of accounts.
If you’ re talking about trying to crack the password then normally the attacker would get a copy of the database for a site, and then hash and try to match billions of passwords with records in the database. This is called an offline attack, as they don’t need the anything other than the data itself to perform it. It can also be extraordinarily fast for each attempt. This is an older but still relevant article about trying just that. https://www.troyhunt.com/our-password-hashing-has-no-clothes/
Checking that a password hasn’t already appeared in a breach will help fight credential stuffing. So will Multi-Factor authentication. Choosing a strong hash algorithm (including salts) and good password practices will combat password cracking.
Andy, I think you’re confusing Credential Stuffing with Password Spraying. They are very similar, but two totally different avenues of attack. Credential Stuffing is where an attacker uses breached account credentials on other platforms. Password Spraying is exactly what you mentioned. It is using a one-to-many approach with just 1 password to many accounts as you stated. This is actually extremely effective in pentesting because you can use generic passwords such as “August2019!” over tons of different accounts and be pretty successful.
There are different methods, but here are two:
1. Don’t attack the logon screen; breach the back-end system via a vulnerability and read the password database directly.
2. Attack slowly; i.e. don’t continuously send login attempts from the same account. Instead, try a different password every 31 minutes (some sites will use a 30 minute timeout for clearing the invalid login counter). This sounds like it would take forever but if the attacker has a list of thousands of accounts to try they can just cycle through the list between each attempt on a single account. Example:
[user1 password1]
[user2 password1]
..
[user999999 password1]
[user1 password2]
[user2 password2]
etc.
The attacker would likely farm the process to a bot net to spread the connection attempts around to try and get past detection tools like an IPS.
The hackers have HUGE lists to go through so they rely on low and slow attacks. If the site locks after a few attempts then maybe they only try once or twice per user, then move on to the next. After a few million different users, the list starts over. They are not trying hundreds of passwords against a single account all at once. They are doing so over days and weeks, if not months.
@Robert In my experience, they don’t try more than once per account. Due to the sheer volume of credential sets available, they just try each set at sites they’re interested in. If one doesn’t work, their tool just moves on.
I would say though, that a discussion I’m not hearing much is the use of non-email address usernames. Personally, I’m not sure it’s viable for everyone, from a user experience perspective, but it does reduce the risk of credential stuffing. e.g. I’m unaware of any FIs that use email addresses as usernames.
Thanks for taking the time to put this together. I have produced a couple of newsletters describing credential stuffing to my firm, so having you corroborate that detail is perfect.
My new motto:
“If it’s easy for you, it’s easy for them.”
I’ve kind of gotten down to the point in the “security vs convenience” struggle where I’m kind of telling people they need to just bite the damned bullet here.
Because there’s really no way around this: you’re going to have to put effort (read: ‘difficulty’) into this if you want good outcomes.
What I find with grandparents and people of an older persuasion is that at this point they just throw up their hands and say- and I’m pretty much quoting directly here, “Then I don’t care if my bank account gets stolen”.
I’m not really sure how you correct for that depth of entitlement- that people feel that anything that requires effort on their part is completely unconscionable and unacceptable- and most importantly: they’re not doing it.
I feel like “the perfect is the enemy of good enough” narrative is part of the problem, too. And this is mostly because “perfect” and “good enough” are highly subjective terms, and in most of these discussions at least one of the parties isn’t really qualified to determine what is perfect or good enough.
I think you have also skipped over the part where some of us want to reuse passwords because we don’t care about the security on a site that requires a login for no real purpose. If I have to have a password to access a site that does not contain real data about me, I use a throwaway email address and a really dumb password I can remember and I do this across every dumb site that requires a password but shouldn’t. Am I worried if it gets hacked. Nope. Am I reusing passwords. You betcha. Have site administrators figured out they require too many passwords just to save preferences for their one website that I don’t care about my identity on. Nope. So the saga continues. And if one anonymizing domain gets blacklisted…I just move to another. But I refuse to be curtailed into the Papers Please mentality of site administrators (especially ones trying to monetize their knowledge of you).
I didn’t skip over it.
The part where I said “one participant often doesn’t have the expertise/knowledge to qualify ‘good enough’.” covers it. If you do have that knowledge or expertise? Great. Good for you.
Most do not. And probably a fair amount in-between think they do, but are probably oversimplifying the issue.
I’m also not ~just~ talking about the reuse of passwords. I’m talking about password practices in general.
Good advice in this post.
I noticed this post was silent about advice for requiring periodic password resets. NIST now recommends that companies do not expire passwords because of the bad user behavior is causes like writing down passwords or using a password increment scheme to help remember them. They advise that the only time users should be forced to change passwords is when there is evidence that the password was compromised (which is what Glassdoor did).
Many security experts disagree because periodically expiring user’s passwords would reduce the period of time a stolen password (like the ones compromised/mentioned above) are usable by the bad guys.
Yep, I covered that in my last post on this topic, about a set of password requests from Citrix that initially seemed to be the result of them being proactive, although it was later revealed that they did have an intrusion that relied on password spraying, which is where they take a small set of commonly used passwords and try them against all known usernames for the targeted organization.
https://krebsonsecurity.com/2018/12/a-breach-or-just-a-forced-password-reset/
How about we just use the Perfect Password Generator at GRC.com ?
Its not just the amount of time a stolen password is usable. Its about the amount of time it would take to brute force crack that password. If its going to take 3 months to crack and the password gets reset every 3 months, theres no point in even trying to crack it. But if the password remains the same indefinitely, its only a matter of time before it is cracked and usable.
I think the main reason NIST thought keeping passwords without changing every three months or whatever the office requires, is that users were found to get frustrated at having to memorize a new complicated password each time, and tended to violate SOP by using passwords or phrases that were too easy to crack. I think I agree with them too.
Too many folks in the security field get stuck on the time to brute force hashing versus time to run a dictionary fuzzing attack. Dictionary fuzzing is a combination of trying every known password from a previous breach with fuzzing the password by changing case, leetspeaking, adding the site name and other variations. Adapting for a random salt is simply another step in the fuzzing part.
Good advice in this post.
I noticed that the post was silent on advice for periodic password expiration.
NIST now recommends that organizations no longer force users to periodically change their passwords. They say that this previous best-practice was actually more likely to cause the wrong user behaviors like writing passwords down or resorting to incrementing the last digit.
However, many other security experts suggest that the forced expiration of passwords will limit the period of time a stolen password is a risk.
Part of the NIST recommendation is that you also screen for compromised credentials. Stopping the forced periodic password reset necessitates MFA or password/credential screening. Many companies are screening customer accounts at login and screening employee accounts in Active Directory becuase it reduces some fo the friction for the end user.
Great info – thanks !
More websites needs to start enforcing the use of MFA like with the use of the Thetis Fido U2F Security Key
Checking *password only* against a leaked list is even simpler than you describe, since Troy Hunt publishes the list of password re-hashed with SHA1. See https://blog.cloudflare.com/validating-leaked-passwords-with-k-anonymity/
This is actually very interesting that companies like Glassdoor do this. It’s a win in my book! I think this is a great way to stay ahead of the game. Credential stuffing is successful because it’s convenient for users to remember just 1 password. In my opinion, if you’re going to remember 1 password, why not use a password vault?
I think the counter-defense to this is two-fold: MFA and User Awareness. I think people typically stress the more technical controls such as MFA, but tend to forget the more process controls such as awareness. Credential stuffing and phishing wouldn’t be nearly as successful if users were aware of the dangers of them, and what they can do to prevent them.
Things I am not hearing in the “we should all just make MFA standard” conversation:
How are we to deal with people who see MFA as “more trouble” and thus refuse to participate?
I mean, I know Google is a success story in regards to this idea, but I don’t think you can discount in that tale that Google’s users aren’t really the same as userbases in other industries.
@Dana – The entire household I live in absolutely swears by the ‘one pass shall rule them all’, but without the pass manager or anything extra involved. The wifi access, emails, facebook, netflix ecetera. They use the same exact password on all those. I’ve had some conversations with the people involved about using a password manager. The bottom line is that they would not be able to keep track of a manager. A software based solution will get lost in their system due to a lack of comprehension if anything is not directly visible on the desktop and clearly laid out & explained (I’ve shown them multiple times where I’ve been ‘hiding’ movies inside their movie folder, but they have yet to even try deciphering the menu structure) A physical key will get misplaced, likely left on the floor under a table at a coffee shop, or permanently lost under the drivers seat in their car. I really have no idea what security solution will actually work for people like this. Maybe a physical implant running a fully self-aware AI?
Google Authenticator/Authy apps are the best MFA solution in these cases, but SMS (despite possible SIM swap attacks) is much better tha nothing.
I bet they don’t lose track of their phones too often (and Authy has cloud backup, even if they do).
“Your password doesn’t matter, but MFA does,” Weinert wrote. “Based on our studies, your account is more than 99.9% less likely to be compromised if you use MFA.”
– This should be the new norm.
In the recent past, TD Ameritrade limited passwords to 15 alphanumeric characters and did not support MFA. That was absolutely shocking to me.
They’ve since changed that to allow passwords up to 64 characters, allow special characters and they now support MFA.
I hope they use bcrypt as well.
Without doing any research, I’ve always thought that Password managers that can share among multiple devices or use the Cloud are too ripe of targets for hackers, despite any security in place. I believe my laptop is less likely to be breached than an online service. I also believe that a person should only use one device for any financial transactions (and keep the kids off of it), hence, I only need a local password manager, not a shared/fancy one.
Thus, I prefer to save my passwords in an encrypted office document using a good, long, complicated passphrase. I found this on Wikipedia (so it may not be accurate) with a quick Google;
—————————————–
Microsoft Office password protection is a security feature to protect Microsoft Office (Word, Excel, PowerPoint) documents with a user-provided password. As of Office 2007, this uses modern encryption; earlier versions used weaker systems and are not considered secure.
Office 2007–2013 employed 128-bit key AES password protection which remains secure. Office 2016 employed 256-bit key AES password protection which also remains secure.
The Office 97–2003 password protection used 40-bit key RC4 which contains multiple vulnerabilities rendering it insecure.
——————————————-
Does anyone see any flaws in my logic?
I think your basic plan is sound, but MS Office may not be the best way to store passwords locally. There are password managers that don’t use the cloud. My concern about MS Office is the program is so complicated that the attack surface is large. Note if you are cutting and pasting passwords, the paste buffer is something to hack.
I really think a time based 2FA is the way to go. Just beware if the service provides some easy one time bypass of the 2FA.
– you left out one detail: the backup of your entire laptop for the day when your hardware fails and you discover that nothing will open those Office files
I would only add that you should use a boring and innocuous name for this Office document.
Gary beat me to it. Your single point of failure is MS Office, a very complex, scriptable application. That’s a *huge* attack surface.
Your logic supports saving your passwords in an encrypted file. Just don’t use MS Office as an encryption tool.
Your solution totally works (assuming you have a sound backup and restore strategy) but the primary “flaw” in your logic is that you clearly aren’t a typical user. My guess is you wouldn’t use the same password for every website and your work account(s). That automatically means you’re being more secure than a significant majority of people.
The solution for people using the same password is to make it as simple as possible to not use the same password for everything. A password protected Excel spreadsheet will never work for those people.
As for password managers, sure there is a risk that the company could get compromised, but remember, they aren’t storing all of your (well, my) passwords in a gigantic plaintext database. My password vault is encrypted by a key that only I control. Therefore if the attacker gets in, they just get access to a whole pile of individually encrypted files. There’s also the risk of a vulnerability in the software (as we have seen in the past). However, this all comes back to the perfect vs. good enough debate. A person using a password manager with a bunch of unique passwords is far better off than using the same password for everything.
Multi factor authentication makes the basic password strength almost irrelevant. If the crook can’t get access to the alternate authentication device whether USB key or phone, they are just out of luck.
I much prefer to USB key because phone numbers change or you can be the victim of a SIM swap, but USB key doesn’t change.
The biggest contribution to security could be lowering the price of the USB key and making more sites able to use them. My domain registrar, Namecheap, is set up for them, but my bank isn’t!
There is an assumption here that all accounts are equal. They’re not.
I have my “high security” accounts: bank, payroll, medical: passwords are strong and always typed by hand.
Next tier is the “high value” accounts: Amazon, Google, Apple. These use 2FA.
Next tier is bread-and-butter accounts: username chosen at random, strong password, no duplication (of course).
Finally, are the junk accounts: those required by a website to do something, but no value for me. I don’t worry about protecting those.
Problems in doing this:
– Many websites use your email as your account name. How do I create a unique account name?
– Many websites can’t handle non-alphanumerics well. CBS.com let me create an account with special characters in the password, but I couldn’t log in again. Say what?
– I like the idea of Yuba keys and the like, but not available for my iPhone, etc. (There may be hope in this area…)
“– I like the idea of Yuba keys and the like, but not available for my iPhone, etc. (There may be hope in this area…)”
Actually, they are. Yubico just came out with a new key that has both USB-C and Lightning (iPhone) connections. Full disclosure: They are an advertiser on this site.
https://www.yubico.com/product/yubikey-5ci
And if you don’t mind your 2FA being FIDO/U2F-flavored, there are also bluetooth-connectable offerings.
“– Many websites can’t handle non-alphanumerics well. CBS.com let me create an account with special characters in the password, but I couldn’t log in again. Say what?”
Don’t discount the possibility of undisclosed character limitations.
Some systems will actually fail to warn you that they only took ~PART~ of your password when you entered it the first time (because the remaining part was over the limit). This means your password is there, it’s just some portion of what you typed and not the whole thing.
Other systems will warn you, but offer a default notice that “your password isn’t strong enough”, even though what you entered technically speaking is stronger, not weaker.
“In that vein, it’s safer and wiser to focus on picking passphrases instead of passwords. Passphrases are collections of multiple (ideally unrelated) words mushed together. Passphrases are not only generally more secure, they also have the added benefit of being easier to remember.”
I agree. Unfortunately, most websites still have password rules requiring a digit, special character, and upper/lowercase letters.
“Unfortunately, most websites still have password rules requiring a digit, special character, and upper/lowercase letters.”
All of which reduce the universe of possible passwords.
Excellent article. Thanks for the explanation.
In the last line, there’s a pet peeve of mine: “revert back”. Isn’t that redundant? 🙁 Would “revert” be good enough?
Yup, thanks.
Made use of the free built Apple iCloud Keychain for self, 86yo mom, sisters and a few friends. Once they were set up (for self mom sister blind friend, I went thru and changed all p/w’s , other friends just a few to show them how do they could do by selves).
None have looked back.
For each, formerly forgotten or long lists of weak or recycled p/w’s were replaced by countless jumbled p/w’s created by the Keychain and a single non jumbled memorable complex one for Apple ID.
Organization and security is liberating.
I use a password algorithm. First I take something about the site I’m visiting I’ll recognize and remember (at least within 3 tries), for instance here I’d choose kreb then I’ll add a constant word of my own choice (for instance scratch) and a number of my own choice (for instance 135) which will give me (for this site) krebscratch135. For a different site it might be something like amazonscatch135, etc. ad infinitum. Thus giving me an endless supply of passwords I can always remember or deduce within 3 tries and I don’t have to write anything down or use a password program. I’ve been online for more than 30 years and I’ve never had a password hacked.
Very similar here except that I just use a multi character suffix that has no meaning but I can easily remember. I do keep a list of sites and passwords for work related sites in and encrypted 7-zip file on my laptop.
@Ed Tomchin
Yeah, I used to use a very similar “clever” algorithm. But found out the hard way that is was relatively easy to be deciphered when my old LinkedIn password was read back to me over the phone by my security monitoring company. Luckily I had already changed it when the hack was first announced.
Then proceeded to change all my other passwords using the same technique.
Because once one password is cracked, in this case LinkedIn, it’s no stretch for a hacker to now try the same email address with all major banks, etc. e.g.
userid: edtomchin@gmail.com
passwords:
chasescratch135
wellsfargokrebscratch135
facebookkrebscratch135
etc.
https://en.wikipedia.org/wiki/2012_LinkedIn_hack
I don’t have any issues with creating a long (maybe 20 characters) complex password and using it while at home on a desktop but problems often occur when you are using devices without a keyboard (netflix account on a tv using a tv/cable remote) and on the road.
If you are having flight/travel issues, time is very limited and you have to enter in a complex long password on your phone, typos are common and it is a big pain.
Also if you are out of the country some sites then want to send you a 2nd factor to your cell phone before you can enter their site. Well depending where you are at, you can encounter fees and/or have limited/no cell reception which then means you can’t even access the email or web site.
Just sitting at home with a desktop computer, solutions aren’t too hard (at least for me) but on the go and out of the country problems seem to multiply.
And yeah, writing down passwords isn’t perfect but if it is strictly for home use, it is much better than using Password123456.
Or people who think they are being tricky by using Pa22word. Not really fooling any hacker.
I commonly will reuse the same password for websites which have no value for a hacker such as news websites. I know these passwords are in known hacked password databases as chrome password checker gives me a warning. When google releases information about how many accounts are using known hacked passwords I’m in this group but I see no personal security risk.
The article was quite helpful until it got to the gratuitous insult: “(think moms/dads/grandparents).”
Not an insult, a statement of near fact. Those of us reading this blog are typically of adult age and have been in computer use for decades, those that typically have trouble with online security are those who got into computers at an age which have more difficulty dealing with new tech, are old school and expect most everyone to be good not evil. I completely understand the reference, if you are offended by it, that is your choice. It’s stereotypical for a reason, right? It took me years to educate my mom on online security, she thinks good of everyone. Only you can allow yourself to be insulted, no one can do it for you.
Great article, thanks for sharing. I work for a large company and would like to put this to practice like Glassdoor, Facebook etc for end customers. In looking at the haveibeenpwned API doc set, it is not obvious where one can input an email address and receive back a plain text password (breached from a previous site). Do you know if this is a direct service that Troy offers or are there other providers that sell this functionality? To “mine the darkweb” for this information would seem to be an iterative process with sources changing and to track all of that would be labor intensive. Seems a service, selling this information would make sense as there is apparent value. Of course, on the flip side, hackers could be customers of this service as well, ensuring continued trouble for the end user. Thoughts?
My understanding (which could be wrong) is that what you are asking is impossible – BY DESIGN.
There are services that match based on hashes, not plain text and only sell to legit companies without passing any passwords back. Look up Enzoic.com it only sends back a token that shows a match or doesn’t show a match, not the actual password.
What you CAN do however, is get the list of all compromised passwords from HIBP in a file sorted by Hash. You then encode the proposed password, hash it using SHA-1 and then see if there is a match in the file. If you index the file by hash, this becomes very efficient. The bonus is you can tell your user how many times that particular password has been known to be compromised. Very educational.
Not to call Glassdoor out, but isn’t it a bad idea to keep the salt that is used for hashing your passwords in the same DB as the password hash itself. It would appear you are making things a ton easier for a hacker since if they can steal the DB with the password hashes they would have the salt values as well. Am I missing something?
It is standard practice. The salt is only there to prevent a simple scan of the password database for duplicate hashes. With the salt you have to hash each password in the reuse database once per known salt not simply once period.
“there’s absolutely nothing wrong with writing down your passwords”
A few years ago I would have been one of those readers who took you to task for this advice. Then I realized a few things:
1) Attackers are almost always remote
2) All websites can be breached
3) Reuse of passwords is the primary way accounts are compromised
Based on that, when it comes to the choice between reusing passwords or writing them down I think the average user is much safer to write them down.
Yes using a password manager and MFA are the best choices but much of the population still isn’t there yet and might not ever be. Security professionals need to be able to help these people too and not just say “don’t write down passwords”.
“there’s absolutely nothing wrong with writing down your passwords”
A few years ago I would have been one of those readers who took you to task for this advice. Then I realized a few things:
1) Attackers are almost always remote
2) All websites can be breached
3) Reuse of passwords is the primary way accounts are compromised
Based on that, when it comes to the choice between reusing passwords or writing them down I think the average user is much safer to write them down.
Yes using a password manager and MFA are the best choices but much of the population still isn’t there yet and might not ever be. Security professionals need to be able to help these people too and not just say “don’t write down passwords”.
“Don’t write down passwords!” was the mantra of IT people in 1995. Before the internet and online shopping and facebook, Instagram, Twitter, etc.
Things have changed considerably. The need for unique passwords (one for every site) has grown tremendously.
As you say, attackers are almost always remote and the local thief is interested in quick profit – jewelry, electronics, cash – and won’t bother with a book, even if left out in the open.
The ppl we need to worry about these days come in through MS Windows, not bedroom windows.
Article great – but I HAVE to comment on the example letter from Glassdoor…
Yup, READ letters of this ilk – BUT NEVER CLICK THAT RESET PASSWORD link. GO to site by other means, THEN Change Passwords.
Betting that these “letters” with embedded “Reset Password” links will become very popular with all the WRONG people.
Yet another example of why standard character sets should not be used to create passwords. 2fa is not the solution it is to easily compromised or otherwise the user is exposed to the risk complete lockout which defeats the purpose of having it.
As an educated and very experienced IT professional, I deserve to have my right to use the internet and operate a computer taken away, because here’s how I have always stored my usernames and passwords on my personal laptop and desktop PCs – inside a .txt file that I store on my primary desktop and occasionally I will email the file to myself so I have an updated copy available.
Great article – great discussion!! This is what keeps me coming back to KOS!!
Easy to remember, unique password tip that includes UC, LC, numeric, and special char:
1. Take one word as a standard key, ex. “Turtle”
2. Take 2nd + 3rd letter of website name, ex. “re” for krebsonsecurity.
3 Take numeric value of 1st letter of site name, ex. 11 for “k”
4. Steering them to turngether and add, say, “$” at the end…
Unique password is: Turtlere11!
5. Use same pattern for all your important passwords – obviously, you can modify this pattern for one the suits you. The key however, is consistency.
“4. String them together…”