Top domain name registrars NetworkSolutions.com, Register.com and Web.com are asking customers to reset their passwords after discovering an intrusion in August 2019 in which customer account information was accessed.
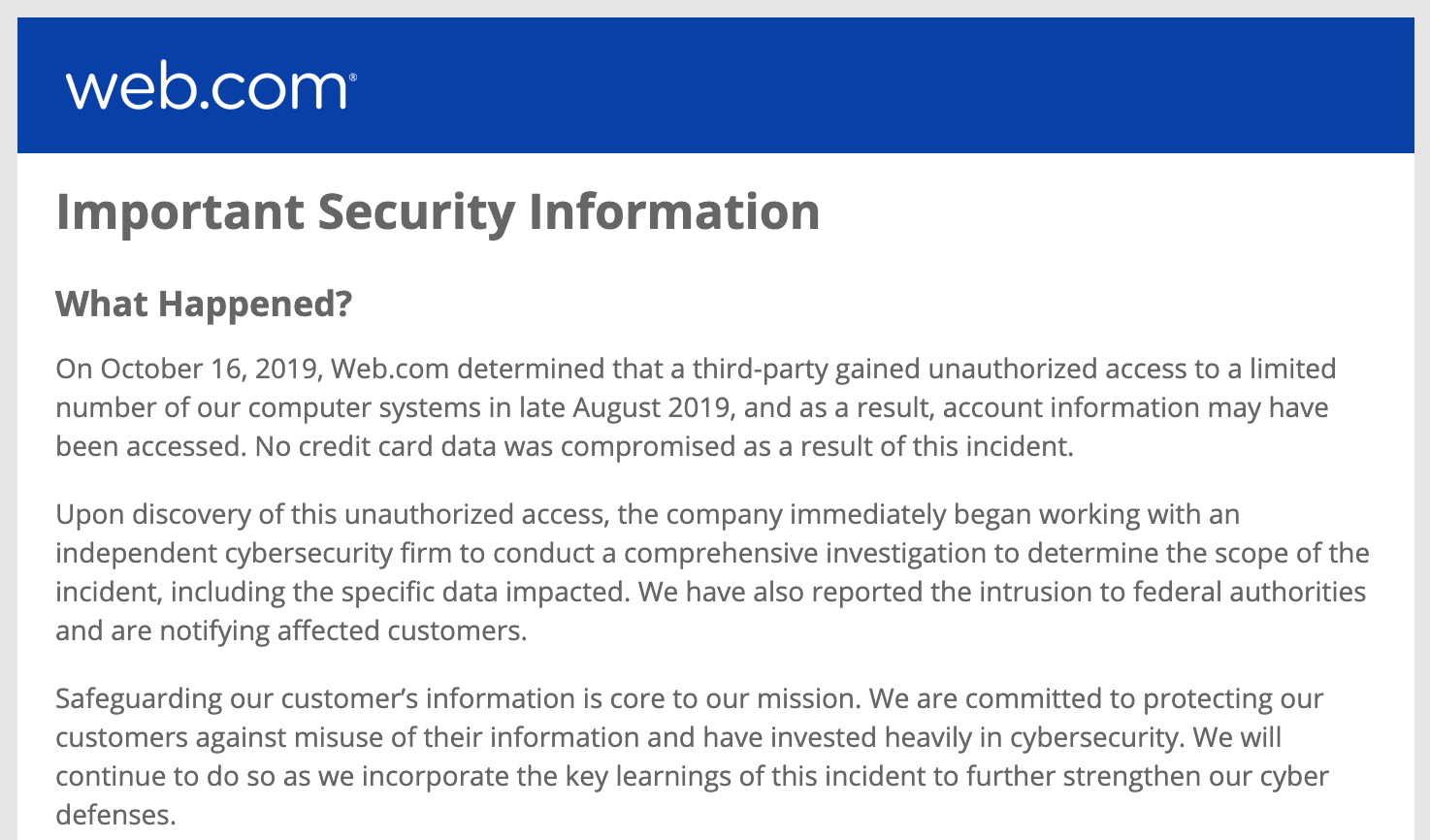
“On October 16, 2019, Web.com determined that a third-party gained unauthorized access to a limited number of its computer systems in late August 2019, and as a result, account information may have been accessed,” Web.com said in a written statement. “No credit card data was compromised as a result of this incident.”
Jacksonville, Fla.-based Web.com said the information exposed includes “contact details such as name, address, phone numbers, email address and information about the services that we offer to a given account holder.”
The “such as” wording made me ask whether the company has any reason to believe passwords — scrambled or otherwise — were accessed.
A spokesperson for Web.com later clarified that the company does not believe customer passwords were accessed.
“We encrypt account passwords and do not believe this information is vulnerable as a specific result of this incident. As an added precautionary measure, customers will be required to reset passwords the next time they log in to their accounts. As with any online service or platform, it is also good security practice to change passwords often and use a unique password for each service.”
Both Network Solutions and Register.com are owned by Web.com. Network Solutions is now the world’s fifth-largest domain name registrar, with almost seven million domains in its stable, according to domainstate.com; Register.com listed at #17 with 1.7 million domains.
Web.com’s homepage currently makes no mention of the breach notification.
NetworkSolutions.com does not appear to currently link to any information about the incident on its homepage, nor does Web.com. To get to the advisory, one needs to visit notice.web.com.
Web.com said it has reported the incident to law enforcement and hired an outside security firm to investigate further, and is in the process of notifying affected customers through email and via its website.
The company says it plans to circle back with customers when it learns the results of its investigation, but I wonder whether we’ll ever hear more about this breach.
Web.com wasn’t clear how long the intrusion lasted, but if the breach wasn’t detected until mid-October that means the intruders potentially had about six weeks inside unnoticed. That’s a long time for an adversary to wander about one’s network, and plenty of time to steal a great deal more information than just names, addresses and phone numbers.
H/T to domaininvesting.com‘s Elliot Silver for the heads up on this notification.




hmm never received notification from NetworkSolutions.com about this
logged in was asked to reset password
only a max 16chars time they upped that!
Nothing from Register.com either.
They also put the ‘no index’ robots instruction on notice.web.com so that Google doesn’t index it.
Love that web.com screenshot. Website security seems to be inversely proportional to the number of ‘verified by’ badges they display and how many times they say something stupid like ‘Gain credibility with every email’.
Hey, you forgot a picture of a hot chick, or a puppy.
Every time a company has to say something like “We take (system) security seriously,” it means one thing: They didn’t.
I know I’m beating a dead horse here yet again but does Web(dot) com off multi-factor authentication on users hosting /domain name accounts?
Apparently not…
I couldn’t find them on twofactorauth.org.
In a “totally unrelated event”, one of our customers suffered from a phishing attempt in “mid-october” to change direct deposit information. The tie in? The header information traced to an IP and email domain that appears to be controlled by “NetworkSolutions.com, Register.com and Web.com” … Interesting
My guess would be that the “bad guy”, for lack of better term, is using them as a service to register their domain that they’re using for their phishing campaign(s). Happens all the time. I’d report that site to their abuse@ email address. I’ve done this before for a hosting provider, but the domain is still active. Fun times!
“We invested heavily in cyber security”
Hey, they forgot “military grade encryption” there.
I wonder if these companies copy and paste some template from HowToShowThatYouDontUnderstandSecurity.com
I would register that domain, but I don’t trust web.com
We’re thankful Network Solutions is no longer the only game in town. If you had a domain way back when, you had to deal with them. To change a whois line involved an archaic, even for the 90’s, rigamarole of sending emails back and forth to NetSol, hoping it would show up correctly. Good riddance.
Say what you want, but their processing time cut out a huge amount of fraud. The automaticity of registrars like Namecheap and Godaddy allows and encourages spam, typo-squatting, trademark violations, and setting up botnets.
Correct me if I’m wrong, but this is more of an incident than a breach, right? According to their statement, it doesn’t seem to be a breach:
“No credit card data was compromised as a result of this incident.”
There has been no mention of the data being released or compromised. If that’s the case, I can see why it wasn’t reported on their site. As far as I know, companies aren’t required to report most incidents.
With up to 6 weeks of access there’s always the possibility of custom malware or high privilege login credentials being put in place for future use.
Which makes the real question: What are Web.com doing to look for those kind of threats?
Time to move
I cringe every time I read some prepared statement where they claim that they “encrypt” passwords. I really hope they’re not encrypting passwords! You’re supposed to be hashing them!
hashing is one way encryption…
Incorrect. Hashing is a one-way cryptographic function. Wholly separate from encryption. Your attempt at being pedantic has backfired.
We so need some emoticons, Brian!
The registrars under the Web.com umbrella are tire fires in burning dumpsters, and I have no confidence in their systems security. The equivocal phrasing of their response inspires exactly no confidence. I’d bet the farm that a more significant compromise than they’re intimating has occurred. In February, Brian wrote about the EPP takeover that occurred at Key-Systems as part of the DNSpionage campaign. I’d be interested in Web.com’s response to a specific question asking whether or not their EPP was compromised, which would have huge implications.
“We encrypt account passwords and do not believe this information is vulnerable as a specific result of this incident.”
That says to me that the hashes WERE nabbed.
How can this be?! That couple looks so happy using web.com I was going to sign up just to save my marriage.
When companies say ‘they encrypt’ your information, in my view it is a meaningless statement. They might be using ‘monkey’ as the password, and obsolete encryption standards. The ISO have many rubbish, dated standards on encryption. It seems to me that they need a routinely updated ISO standard number nnnn which specifies the minimum requirements. It might have level 1, 2 and 3 and 4 etc depending on the needs in question. There needs to be a global standard, because no one national government can be trusted.
“We encrypt account passwords and do not believe this information is vulnerable as a specific result of this incident. ”
Passwords should be hashed, not encrypted.
“As with any online service or platform, it is also good security practice to change passwords often”
Especially when their Op Sec sucks
“and use a unique password for each service.”
The only valid piece of advice.
NIST no longer recommends changing passwords often or at specific intervals. Research found that it causes users to pick simplistic passwords (to avoid having to memorize a new one every so often) or to merely change one character, i.e. Test123A becomes Test123A (because it’s easier to recall).
Instead, create a long password that’s not too hard to memorize, but not so complex you’ve got to write it on your wall. Example: “The only practical reason to stop eating cats” is better than “22×%44=aeetefydudud.”
Actually, NIST no longer recommends frequent password changes:
https://pages.nist.gov/800-63-FAQ/#q-b05
So the fact that they “encrypt” passwords instead of hashing with a salt makes me even less happy about the state of their internal security. Perhaps this is a spokesperson that does not understand the details, but the details in security are important.
NetworkSolitions.com doesn’t even offer MFA; after the Feds recommended utilizing MFA with registrars.
https://krebsonsecurity.com/2019/02/a-deep-dive-on-the-recent-widespread-dns-hijacking-attacks/
The more I read of breaches like this, the more I wonder:
If you all had to put a percentage number on things, how would you rank:
1) Company/employee laziness plus lack of funding commitment about implementing high-level info security measures;
2) Company/employee lack of knowledge why & how to implement high-level info security measures, and;
3) The technology just does not exist today to stop these sort of breaches.
Is it sort of a 50-45-5% thing?
Or more like 20-70-10% thing?
(Should number 3 be even considered?)
Curious what some of you more knowledgeable readers think/believe from what you’re seeing going in your daily life at places you work and/or manage.
70-30-0%
I’d say it’s closer to 50/50/0.
Most of the non-technical staff is likely to not bother thinking about any kind of security threats. They’re just there to go about their daily routines and collect their paycheck at the end of each month. This does include a lot of management.
Learning about and implementing IT security is something that usually doesn’t happen until after a breach has occured. It’s generally not lazyness, but rather them being unaware of the damage these types of breaches can cause.
I would say it’s more 33%-66%-1%.
I wouldn’t say the vast majority of breaches occur due to laziness and funding, I’d say the majority are due to a lack of knowledge. You have to break it down into what is causing breaches in the first place. (1) Business Email Compromise/Phishing or (2) Password Reuse is seen in nearly every breach. Both of which are not due to laziness, they’re due to a lack of knowledge. You could argue that reusing passwords would be lazy, and I would agree, but if more people were aware of the dangers of reusing passwords, then it might decrease the amount of users “being lazy” with their password hygiene.
People think most hackers are these extremely skilled and technical individuals–some are–but in reality, most of them find credential dumps and do password spraying or credential stuffing attacks to gain unauthorized access.
Can I throw a curveball at this?
I agree with the comments about – lack of cybersecurity awareness and knowledge. Additionally:
For #3, In general, I agree that there is no single solution to this stop the breaches. Instead, we leverage the best practice of “depth in defense” to detect the incident as early as possible and (hopefully) mitigate the risk before it becomes a compromise.
My take is around 40-60-?
In my experience, funding has been a greater problem than knowledge.
And, if you really think about it, in the places where knowledge is a problem, it is *usually* a by-product of insufficient funds for staffing and/or training.
I’d say that 40-59-1 or even 30-69-1 is more realistic.
I give them 10% for security commitment – I begged Netnation to adopt double verification for changed password, i.e. texting a pin. But they laughed at me, said it was impossible for someone to hack my password.
Also, everyone I have spoken to at Netnation has a Russian accent (this worries me).
Just to touch on the 1) aspect of funding, my organization just spent over $6000 on a FortiGate 201E bundle. However, and sadly, the reason wasn’t Op Sec, it was failing PCI compliance that finally allowed me to push it through. That is what we are dealing with in the IT Op Sec industry, and why the problem continues unabated…
I’d be less concerned about the theft of contact data than I would be about other implications from compromising a registrar. Any indication if the intrusion resulted in changes of name servers for targeted domains, etc?
It’s fairly common to see things like this happen, and its actually not a big deal. There are a myriad of websites such as myspace which had more significant breaches than this. I would not sweat this one at all.
Krebs, you always provide a good read, and insight into these breaches. Krebs, I have one question, if the organizations we depend on for cloud security are being breached every so often and the have all these compliance checks, and frameworks in place, where does that leave the data in the cloud?
Perfect work you have done, this web site is really cool with great information.
Hmm it seems like your blog ate my first comment (it was super long) so I guess I’ll just sum it up what I wrote and say, I’m thoroughly enjoying your blog. I too am an aspiring blog writer but I’m still new to everything. Do you have any helpful hints for inexperienced blog writers? I’d definitely appreciate it.
as long as optical fiber can be eavesdropped, data intercepted by placing a tap on the optical fiber – all of the crypto is not going to fix things, the doors and windows are ajar……
Umm, that’s exactly what encryption is designed to protect against. Remember, encryption doesn’t happen in just one place when it’s being used properly (there are obviously a lot of people who don’t use it properly, but I doubt (and hope I’m correct) that that describes an organization like Network Solutions. You have encryption at rest for data that’s stored, encryption in transit for data that’s moving from point A to point B. They are not the same encryption, and they protect against different vectors of attack, so a properly implemented system is not vulnerable to wire tapping/man-in-the-middle attacks.
Thanks for the heads up, don’t recall receiving notification from networksolutions.
YAY. Network Solutions FINALLY sent an email informing us of the breach. Good thing it wasn’t important.
Thanks to Brian for keeping us informed.
Epstein didn’t kill himself.
they never sent me any notice … I hope I have no problems … in the meantime I will look for another reliable registrar…thanks