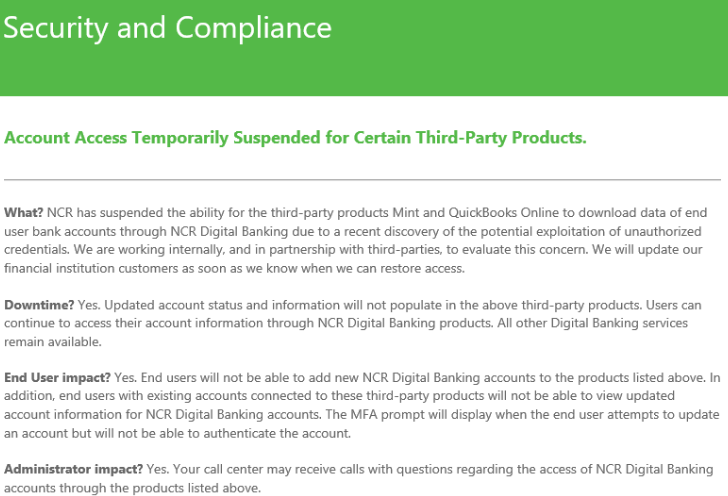
Banking industry giant NCR Corp. [NYSE: NCR] late last month took the unusual step of temporarily blocking third-party financial data aggregators Mint and QuickBooks Online from accessing Digital Insight, an online banking platform used by hundreds of financial institutions. That ban, which came in response to a series of bank account takeovers in which cybercriminals used aggregation sites to surveil and drain consumer accounts, has since been rescinded. But the incident raises fresh questions about the proper role of digital banking platforms in fighting password abuse.
On Oct. 29, KrebsOnSecurity heard from a chief security officer at a U.S.-based credit union and Digital Insight customer who said his institution just had several dozen customer accounts hacked over the previous week.
My banking source said the attackers appeared to automate the unauthorized logins, which took place over a week in several distinct 12-hour periods in which a new account was accessed every five to ten minutes.
Most concerning, the source said, was that in many cases the aggregator service did not pass through prompts sent by the credit union’s site for multi-factor authentication, meaning the attackers could access customer accounts with nothing more than a username and password.
“The weird part is sometimes the attackers are getting the multi-factor challenge, and sometimes they aren’t,” said the source, who added that he suspected a breach at Mint and/QuickBooks because NCR had just blocked the two companies from accessing bank Web sites on its platform.
In a statement provided to KrebsOnSecurity, NCR said that on Friday, Oct. 25, the company notified Digital Insight customers “that the aggregation capabilities of certain third-party product were being temporarily suspended.”
“The notification was sent while we investigated a report involving a single user and a third-party product that aggregates bank data,” reads their statement, which was sent to customers on Oct. 29. After confirming that the incident was contained, NCR restored connectivity that is used for account aggregation. “As we noted, the criminals are getting aggressive and creative in accessing tools to access online information, NCR continues to evaluate and proactively defend against these activities.””
What were these sophisticated methods? NCR wouldn’t say, but it seems clear the hacked accounts are tied to customers re-using their online banking passwords at other sites that got hacked.
As I noted earlier this year in The Risk of Weak Online Banking Passwords, if you bank online and choose weak or re-used passwords, there’s a decent chance your account could be pilfered by cyberthieves — even if your bank offers multi-factor authentication as part of its login process.
Crooks are constantly probing bank Web sites for customer accounts protected by weak or recycled passwords. Most often, the attacker will use lists of email addresses and passwords stolen en masse from hacked sites and then try those same credentials to see if they permit online access to accounts at a range of banks.
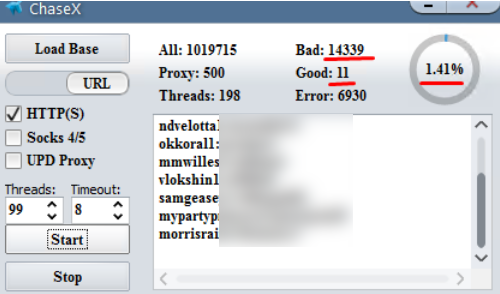
A screenshot of a password-checking tool that can be used to target Chase Bank customers who re-use passwords. There are tools like this one for just about every other major U.S. bank.
From there, thieves can take the list of successful logins and feed them into apps that rely on application programming interfaces (API)s from one of several personal financial data aggregators, including Mint, Plaid, QuickBooks, Yodlee, and YNAB.
A number of banks that do offer customers multi-factor authentication — such as a one-time code sent via text message or an app — have chosen to allow these aggregators the ability to view balances and recent transactions without requiring that the aggregator service supply that second factor.
If the thieves are able to access a bank account via an aggregator service or API, they can view the customer’s balance(s) and decide which customers are worthy of further targeting.
But beyond targeting customers for outright account takeovers, the data available via financial aggregators enables a far more insidious type of fraud: The ability to link the target’s bank account(s) to other accounts that the attackers control.
That’s because PayPal, Zelle, and a number of other pure-play online financial institutions allow customers to link accounts by verifying the value of microdeposits. For example, if you wish to be able to transfer funds between PayPal and a bank account, the company will first send a couple of tiny deposits — a few cents, usually — to the account you wish to link. Only after verifying those exact amounts will the account-linking request be granted.
The temporary blocking of data aggregators by NCR brings up a point worthy of discussion by regulators: Namely, in the absence of additional security measures put in place by the aggregators, do the digital banking platform providers like NCR, Fiserv, Jack Henry, and FIS have an obligation to help block or mitigate these large-scale credential exploitation attacks?
KrebsOnSecurity would argue they do, and that the crooks who attacked the customers of my source’s credit union have probably already moved on to using the same attack against one of several thousand other dinky banks across the country.
Intuit Inc., which owns both Mint and QuickBooks, said there is no indication of a breach of Intuit systems.
“As you heard from NCR, we continue to work closely with NCR Digital Banking to enable a secure, reliable customer experience as well as continued ongoing analysis,” Intuit spokesperson Kali Fry said.
NCR declined to discuss specifics about how it plans to respond to similar attacks going forward.




Thank You Brian,
I’m not very tech savvy, and I’m very paranoid about my financial data, so I do not use any automated account services. Instead I manually enter my data from recipes & balance against my statement. Yes, very old school but I used to work bank fraud cases in the early 90s.
I’ve been so busy I haven’t been doing this for a couple of months. I was just about to download & use Mint when your email arrived. Needless to say, I’ve decided to continue my method. My Sunday afternoon will be reconciling accounts Old School.
Great comment, Chris, and thank you Brian. I also thought about Mint and had similar concerns.
If I read it corectly, it sounds like the new(er) requirements around MFA that banks have implemented (and required under PSD2 and SCA) is being bypassed by Intuit services once the accounts are linked – negating the security of MFA in the first place..?
From memory the problem is that the systems were trusting the vendor (Mint/Intuit). It wasn’t tied to a specific account.
That meant that an attacker could use an arbitrary account to perform these account inquiries.
(I could be misunderstanding/misrecalling.)
Basically, there isn’t a good way for any of these things to do what they need to do, so poor trust links are established instead.
And attackers have found a way to connect the weaknesses together for profit.
In short, you using Mint didn’t make you more vulnerable, Mint existing and being useful did.
If accounts all offered 2FA (and in some countries most banks do not, the USA may be getting better here, last I checked, Canada was horrible), then Mint/Intuit could be forced to ask you for 2FA, but it would make their “automatically retrieve account information” process painful.
If there was a way to provide “app specific passwords” (Google does this for Email) that were only issued in response to a 2FA challenge, then Mint/Intuit could be forced to use that. But, that would require everyone to set up 2FA (this would be good for the ecosystem, but expensive initially).
Agreed that Canada has some of the worst bank security. No 2FA and only weak passwords allowed at some banks. For instance, no more than 8 characters and no special characters allowed.
Sounds about right.
If people want to get a sense of how well the banking system works in Canada, “Meet Deborah Oguntoyinbo” [1] and look at how Royal Bank of Canada allowed her to deal so much damage to one of their customers (probably more, since there were at least 20 victims over 2 years). Note that RBC is probably the largest of the five major banks in Canada. But that doesn’t make it special, I wouldn’t be surprised if the story had listed any of the other banks.
[1] https://www.cbc.ca/news/canada/toronto/meet-deborah-oguntoyinbo-accused-of-being-a-professional-and-prolific-identity-thief-1.5348438
Brian ,Did you know that Experian is doing consumers aggregate to multiple financial institutions for their new “Experian Boost” program They claim that if you link your bank ,credit card and utilities accounts to their website that it will supposedly boost your credit score
Claims from their website
“Experian Boost empowers Experian customers with the ability to immediately add non-traditional credit information, such as your utility and mobile phone bills, to your Experian credit file. Adding this record of your recurring payments for these accounts will build your positive payment history and your length of credit history. Over time, improving these two important aspects of your credit health can improve your FICO® Score 8 as well as other credit scores that consider this data. This information gives lenders a much better view of your overall creditworthiness so you can more easily qualify for credit.”
“After agreeing to let Experian have read-only access to your bank account payment history, you’ll connect the bank account you use to pay your bills. By connecting Experian to your bank account, we can see a verified record of your electronic payments for your utility and telecom bills. With world-class encryption, Experian will look for at least three payments within six months and present the accounts found so you can verify the data and add it to your Experian credit file for an immediate boost. Experian can access up to 24 months of data to add to your credit file as determined by your bank. If you miss a payment, that negative data won’t be added to your credit file. If no data is reported for three months, then the account will automatically be removed from your credit file”
Wow that is horrifying! But hey, I am sure they can be trusted. This time.
A local credit union has several methods of detecting who is attempting to access an individual’s account. They include incoming IP address, device type, and browser. If any of those change for any one access attempt the CU forces a 2nd factor login before the customer can access their account information.
I wouldn’t doubt an accomplished bad actor could somehow bypass these controls, but I wouldn’t know how. Hopefully it is at least a speed bump for the crooks!
The problem here is that the Bank only sees the IP address of the aggregator whereas the aggregating service will see the IP of the person attempting to access the account information.
Today I tried to link a USAA and a BB&T bank account to PayPal and got an odd message that they’re not accepting any more linked accounts to those banks. Perhaps this is related.
Ironically, Intuit used to own Digital Insight…
Where Mint users are concerned, this is merely inconvenience. The users and owners of the account are generally the same people. With Quickbooks (QB) many of its users are bookkeepers who work for a business owner who doesn’t want them to have any direct access to bank, credit card and investment accounts. (They don’t have account names, passwords or MFA info.) The. business owner links the accounts to QB and periodically has to refresh the connection. When the bookkeepers log into QB, they only see the downloaded bank or investment information to then enter into the various income, expense, asset and liability accounts.
Often the bookkeepers are using QB remotely or when the business owners are not around. It would require the business or account owner to often or even daily renew the aggregation, which woukd likely render QB impractical if mot unusable.
@Brian, you listed Plaid twice
So, which one was responsible? Mint, Quickbooks, or none of the above? And why couldn’t NCR tell where the fraudulent transactions were originating?
NCR was responsible.
They whitelisted extra trust to those vendors. The crooks almost certainly distributed their attacks through multiple vendors (if they didn’t, then it’s possible different crooks used different vendors).
By weakening its security, NCR enabled this attack.
But… partially, this is a failing of the banking system as a whole [1].
I need to try to work on a HIPAA metaphor.
Let’s try one out. Please let me know if it works for you.
Scene:
Boston Medical Center (BMC), Brigham and Women’s Hospital (BWH), and Massachusetts General Hospital (MGH) [2] have HIPAA data (namely patients, and their privacy).
1. ABC comes and films there. The odds are that ABC entered into some contract with BMC/BWH/MGH in order to film. ABC is probably a series of corporations each of whom have contracts with each-other establishing a chain.
2. ABC’s filming completes.
3. The final product is transmitted via some mechanism and aired on TV networks.
4. It’s seen by viewers.
5. A complaint is filed.
Does the DHHS-OCR sue the TV stations that broadcast the private information? No.
Does the DHHS-OCR sue ABC? No (afaict)
Who does DHHS-OCR sue? BMC/BWH/MGH.
Why? Because they were responsible for protected the confidentiality of their patients/patients’ data.
The mapping here is to NCR. They’re at fault, they didn’t protect the data (by not enforcing 2FA to ensure only the correct users looked at data). Now, it might not be possible to actually do this, because there might not be a way to actually get 2FA approval. But, if that’s the case, then maybe NCR shouldn’t be offering this service, and should instead be working w/ the banks to set up a proper 2FA system that could be used throughout the banking system.
Disclaimer: I picked this instance [2] at random from a long list of HIPAA Violations & Breaches [3]. I know nothing about the particulars beyond a cursory reading of its description [2]. I’m merely designating it to work as an analogy to our scenario here.
[1] https://krebsonsecurity.com/2019/11/ncr-barred-mint-quickbooks-from-banking-platform-during-account-takeover-storm/#comment-499409
[2] https://www.hhs.gov/about/news/2018/09/20/unauthorized-disclosure-patients-protected-health-information-during-abc-filming.html
[3] https://compliancy-group.com/hipaa-fines-directory-year/
I was hacked on the 5th May by a fake UK TV Licence reminder. My bank, Santander UK, told me that I had done nothing wrong & it’s clear that they didn’t know how their two-stage log-on procedure had been breached. They said they thought it was to do with a common App used by gamers – if you think that the name of that App would be useful to you I’ll dig out my papers.
Do you think is it possible that this NCR/Digital Insight might be how my account was hacked, Brian?
Typically, aggregation services act as a browser and will prompt for MFA the first time a login to the service occurs, which they then store a token for subsequent logins, negating the MFA challenge for each subsequent login. Clearly account credentials are being reused in this type of attack and the aggregation service storing the token is allowing the access to the accounts. My experience working with digital banking vendors is that they don’t always have a great relationship with the aggregation services and it is difficult for them to understand which service is being used to access the accounts.
Dinky banks? That’s a rather harsh pejorative.
As the IT Admin at one of those “dinky banks” that didn’t need a government bailout in 2008 and treat customers as people instead of numbers, I wish you hadn’t used that term.
I was all set to share this article with our staff as an example of why it’s important to use unique passwords across all sites, but I’m not willing to deal with the blowback I’ll get when someone reads that term.
I’m sorry that came across as pejorative. That wasn’t my intent. I was trying to express the reality that there are thousands of very small banks that don’t really have much in the way of resources to fight this kind of activity, and that it makes way more sense to combat this at the service provider level, instead of expecting every credit union and small bank to have oodles of resources to uniquely deal with this on their own.
Change the word, everybody wins. Make the kid happy.
Not that you need our approval, but I like the word choice — because it does a good job of expressing exactly what you’re trying to express.
Your word choice is spot on! Do not listen to one person that is offended and probably does not know how to use a dictionary that works at the “dinky bank” OR SMALL bank he works at. All of us who know what you are talking about do not need an explanation. Dinky literally means small. Look it up smart alec before you come commenting here about how disgraceful and offended you are. Appraising your position like you are some god at probably a 3 branch bank.
Brian, Thank you for addressing my comment. I did share the article with my coworkers, though I changed the word “dinky” to “resource-constrained”.
We’re, otherwise, big fans of the work you do and greatly appreciate the amount of effort you exert. I frequently share your ATM skimming articles with our security officer and when we see an uptick in card fraud you’re one of the first places we look to see if there’s a big event happening.
Lol, are you really offended right now?
Dinky can also mean “Attractively small and neat”. As in “Dinky little restaurant”. This is as per British English, not as per American.. You should probably consider sharing the article with your staff, looking at the benefit it will serve.
Use of third party aggregators could put at risk your guarantee of fraud protection at Vanguard and Schwab( and likely other financial institutions)
From Vanguard website:
“You should be aware of the risks of sharing your account information: If you share your vanguard.com user name and password, or if you allow someone to access your account information, activities performed with your shared or accessed credentials or information may be considered authorized. ”
Maybe your covered and maybe your not, there’s enough wiggle room in there to leave doubt. At the very least if the worst happens, your going to be put through the emotional wringer trying to get your money back. My preference is to not take chances with my money for a service that really shouldn’t be necessary. If you can’t manage your accounts without an aggregator then maybe you have too many accounts.
Seems like a reason to not use email addresses as usernames. If I don’t need to use email addresses, then my username (in addition to my password) can be unique for each and every website.
As always, great reporting Brian. Many thanks!
Re: “… Seems like a reason to not use email addresses as usernames … ”
EXACTLY !!!
I never use my actual e-mail address as a username; I use a random word generator to create unique usernames (and passwords) for each site.
For those “backwards” sites which still insist on using e-mail for the username, I create an e-mail alias unique for that one site. (e.g. “joesonlinestore_at_mydomain.com”)
Obviously for this to work a capable Password Manager is absolutely required …
… with a personal committment to ACTUALLY adhere to your own process …
… as well as an e-mail provider capable of providing aliases “on the fly.”
I don’t often use my e-mail for user ID, but I do frequently use the same user ID across several sites. However, my password is always different, usually different lengths, and always use different security answers – often not legitimate answers.
It means I only have a few that I memorize. My little notebook holds my life. Hope I never have a fire at my home.
Re: ” … always use different security answers – OFTEN NOT LEGITIMATE – answers … ”
LOL !
I too have been born-in (or met my wife in) some pretty “unique” locales.
Most aren’t on ANY map.
“…Namely, in the absence of additional security measures put in place by the aggregators, do the digital banking platform providers like NCR, Fiserv, Jack Henry, and FIS have an OBLIGATION to help BLOCK or MITIGATE these “LARGE-SCALE CREDENTIAL EXPLOITATION ATTACKS”?
KrebsOnSecurity WOULD ARGUE THEY DO…”
Brian, I bet the keys on your keyboard were going down a little heavier than usual when writing that last sentence. As you have been pointing out the past 3 years, Fiserv, Jack Henry, FIS—jeez, if people only knew how these 3 dominate the small-to-mid-somewhat-large banks/credit-unions/etc in the USA, they’d be truly afraid.
The scary thing is not so much the third party aggregators (and people who re-use passwords in this day & age, dam#, do they need to be taught a lesson by suffering a $$$ penalty for pulling this obvious no-no stunt?)…anyhow, the truly scary thing is if one of these big 3 back-end/financial website software providers actually itself suffers a breach. A breach where hackers and/or rogue employees get in & install malicious code in the development and/or maintenance process of these big three’s software offerings to banks, credit unions, etc across the U.S. If that happens, the look out below…… Most of these small-to-mid banks & credit unions have no idea (nor the personnel skill level) to understand what is being updated & maintained when Fiserv, Jack Henry & FIS continuously roll out and update their offerings.
Another good article, Brian, thank you. This sort of article is the “canary in the coal mine” for coming financial breaches. I’d like to take a hard copy of this article (and past Krebs articles discussing their problems) and staple them all to the heads each of the respective CEO(s) and all their respective Board members of Fiserv, Jack Henry and FIS.
An email addresses should not be allowed as a banking login name. An email address is part of a low security login credential. Banks should know better than to allow the same type of credential used on their high-security website as thousands of low-security websites.
It’s predicable that low-security websites are going to get hacked. But it’s nonsensical that the same credentials would be allowed on a high-security website.
Most banks have a process where the user name is used rather than the email. I know do this.
I just attempted to verify using PayPal the other day – and they wanted my online banking credentials to verify the transactions. And when I hit the link to verify them myself – it simply went to an error page. Paypal claimed they wouldn’t save the information anywhere – but we all know how that works.
Hi Mr. Kreb.
First of all, I appolagies for posting a request here.
I am very much interested to know about the recent hack in an Indian nuclear reactor. Could you please do a story on that.
Thanking you.
KOS predicted this aggregate API banking thing would be a problem. Sure enough, it was. Nicely done. (Not sarcasm)
Today, science tells us that the essence of nature is flow.
Consciousness consists of transmissions of quantum energy. “Quantum” means a maturing of the cosmic. Nothing is impossible.
It is time to take complexity to the next level.
To roam the circuit is to become one with it. We exist as electromagnetic forces. You and I are seekers of the quantum matrix.
Soon there will be an awakening of passion the likes of which the nexus has never seen. Imagine a flowering of what could be. It is a sign of things to come.
Where there is bondage, knowledge cannot thrive. We can no longer afford to live with delusion. Suffering is born in the gap where consciousness has been excluded.
Without consciousness, one cannot reflect.
Only a prophet of the quantum matrix may manifest this uprising of transcendence. You must take a stand against greed. Materialism is the antithesis of nature!
Interesting since Digital Insight used to be…drumroll…Intuit Financial.
Yup.
As did your previous article on the vulnerability through aggregators, I found this article also interesting, from a high level.
From a low level, however, I still don’t know whether my online access is through similar aggregators. If I log directly into the bank I’d guess probably not. What if I do some kind of paper-free electronic bill paying through that login? What about transfers between banks? Does that normally involve aggregators? Some words one way or the other would be very helpful.
Is it time to return to paper checks?
Would someone be kind enough to expound on what “aggregator” means in this context?
My first thought was that banks were “monetizing” their customer’s financial data and transactions by selling them to some third party, but surely I’m just more paranoid than normal…
Many European banks have several layers of control over access and payments.
1) You enter a contract number (which is different from the account number)
2) The bank system sends you a 6 to 8 digit code (numeric).
3) You insert your debit card into a bank provided calculator and enter the 6 to 8 digit number provided on the website.
4) The calculator generates an 8 character response code eg AB 2X 0G h6 which is valid for say 60 seconds
5) you enter the AB 2X etc code into the web page response field.
At that point you are good to go for viewing your account and making payments to the same IBAN as you previously paid. (IBAN = international bank account number used in Europe, Middle East and a few other countries. If the US used IBANs, an US IBAN might be US99 2044 2020 0982514233 where US = ISO country code, 99 is a check digit for the entire account number, 2044 2020 is the routing code of your bank and branch and the 0982514233 etc is the legacy account number.
However if the payment is going to somebody new that you never sent money to before, you have to enter say 5 characters from the IBAN into the multi-factor authentication device and the amount of the payment. It computes another code eg RR 25 X0 BQ. Which you enter into the bank web form.
In that way, there is no opportunity for an idiot to use the same login details as they use for say amazon, and each payment is locked down both in terms of who gets paid and how much they get paid.
European bank accounts are generally multi-currency – which allows one to have sub-accounts in EUR, USD, JPY etc so one can use the same procedure to pay somebody in Japan or the US, or wherever. But given that neither Japan nor the US use the IBAN standardized account number system, it becomes marginally more complicated. But no big deal complicated.
Within the Euro (currency) zone, it costs about 30c to pay anybody. eg if you live in Ireland and have a villa in Spain you can pay the internet or electricity bill for the place in Spain from your Irish bank account for 30c. Typically the Spanish utility company would use a SEPA DD to debit your Irish IBAN automatically every month.
While the above may seem complicated, there are so many stages and controls in the system that it would be hard to hack end to end. The EU (+ some other countries/banks – eg Swiss, Norway) have multi-factor authentication for online purchases. Typically by sending a 6 digit code to one’s mobile phone. SIM jacking is very difficult in Europe because most countries have ID card systems which force the mobile phone operator to check alterations to your SIM card to your ID card.
It is a matter of convenience over security.
The linking of Mint and other account aggregator creates more problem than it solves besides convenience access.
This is one of the reason why I do my finance off line (using QB pro) on a external hard drive. This ensure that I know what’s going on. The only problem I would encounter would breach at the bank sites but I have put things in to let known if attempts were made.
An example would be somebody tried to buy two items (hotels.com ($64.00) and Thrive ($.51)) which the bank approved the first and reject the second. I then got a text requesting if I made the transactions which I said no. The bank stopped the transaction cold, meaning they won’t pay for it. I then got online to change my CC after providing the necessary things.
The card breach in the above was a transaction made about two years ago and was recently breached which I got a notification from the vendor.