A ransomware outbreak has besieged a Wisconsin based IT company that provides cloud data hosting, security and access management to more than 100 nursing homes across the United States. The ongoing attack is preventing these care centers from accessing crucial patient medical records, and the IT company’s owner says she fears this incident could soon lead not only to the closure of her business, but also to the untimely demise of some patients.
Milwaukee, Wisc. based Virtual Care Provider Inc. (VCPI) provides IT consulting, Internet access, data storage and security services to some 110 nursing homes and acute-care facilities in 45 states. All told, VCPI is responsible for maintaining approximately 80,000 computers and servers that assist those facilities.
At around 1:30 a.m. CT on Nov. 17, unknown attackers launched a ransomware strain known as Ryuk inside VCPI’s networks, encrypting all data the company hosts for its clients and demanding a whopping $14 million ransom in exchange for a digital key needed to unlock access to the files. Ryuk has made a name for itself targeting businesses that supply services to other companies — particularly cloud-data firms — with the ransom demands set according to the victim’s perceived ability to pay.
In an interview with KrebsOnSecurity today, VCPI chief executive and owner Karen Christianson said the attack had affected virtually all of their core offerings, including Internet service and email, access to patient records, client billing and phone systems, and even VCPI’s own payroll operations that serve nearly 150 company employees.
The care facilities that VCPI serves access their records and other systems outsourced to VCPI by using a Citrix-based virtual private networking (VPN) platform, and Christianson said restoring customer access to this functionality is the company’s top priority right now.
“We have employees asking when we’re going to make payroll,” Christianson said. “But right now all we’re dealing with is getting electronic medical records back up and life-threatening situations handled first.”
Christianson said her firm cannot afford to pay the ransom amount being demanded — roughly $14 million worth of Bitcoin — and said some clients will soon be in danger of having to shut their doors if VCPI can’t recover from the attack.
“We’ve got some facilities where the nurses can’t get the drugs updated and the order put in so the drugs can arrive on time,” she said. “In another case, we have this one small assisted living place that is just a single unit that connects to billing. And if they don’t get their billing into Medicaid by December 5, they close their doors. Seniors that don’t have family to go to are then done. We have a lot of [clients] right now who are like, ‘Just give me my data,’ but we can’t.”
The ongoing incident at VCPI is just the latest in a string of ransomware attacks against healthcare organizations, which typically operate on razor thin profit margins and have comparatively little funds to invest in maintaining and securing their IT systems.
Earlier this week, a 1,300-bed hospital in France was hit by ransomware that knocked its computer systems offline, causing “very long delays in care” and forcing staff to resort to pen and paper.
On Nov. 20, Cape Girardeau, Mo.-based Saint Francis Healthcare System began notifying patients about a ransomware attack that left physicians unable to access medical records prior to Jan. 1.
Tragically, there is evidence to suggest that patient outcomes can suffer even after the dust settles from a ransomware infestation at a healthcare provider. New research indicates hospitals and other care facilities that have been hit by a data breach or ransomware attack can expect to see an increase in the death rate among certain patients in the following months or years because of cybersecurity remediation efforts.
Researchers at Vanderbilt University‘s Owen Graduate School of Management took the Department of Health and Human Services (HHS) list of healthcare data breaches and used it to drill down on data about patient mortality rates at more than 3,000 Medicare-certified hospitals, about 10 percent of which had experienced a data breach.
Their findings suggest that after data breaches as many as 36 additional deaths per 10,000 heart attacks occurred annually at the hundreds of hospitals examined. The researchers concluded that for care centers that experienced a breach, it took an additional 2.7 minutes for suspected heart attack patients to receive an electrocardiogram.
Companies hit by the Ryuk ransomware all too often are compromised for months or even years before the intruders get around to mapping out the target’s internal networks and compromising key resources and data backup systems. Typically, the initial infection stems from a booby-trapped email attachment that is used to download additional malware — such as Trickbot and Emotet.
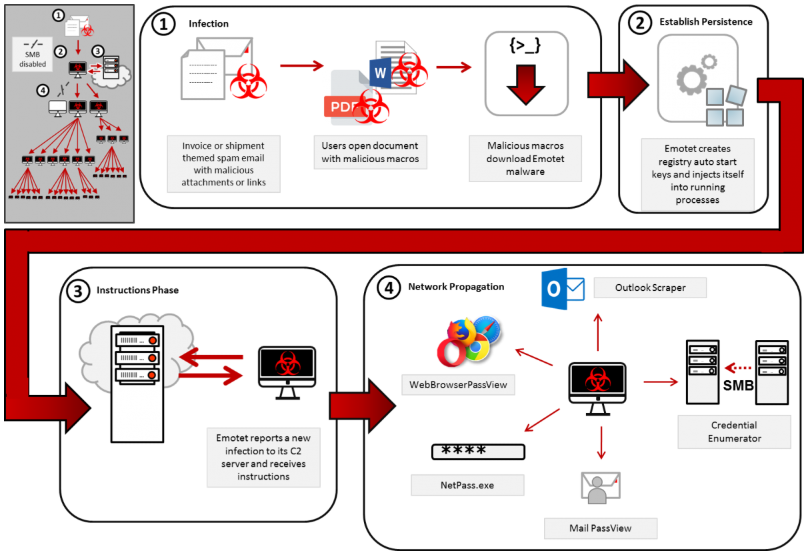
This graphic from US-CERT depicts how the Emotet malware is typically used to lay the groundwork for a full-fledged ransomware infestation.
In this case, there is evidence to suggest that VCPI was compromised by one (or both) of these malware strains on multiple occasions over the past year. Alex Holden, founder of Milwaukee-based cyber intelligence firm Hold Security, showed KrebsOnSecurity information obtained from monitoring dark web communications which suggested the initial intrusion may have begun as far back as September 2018.
Holden said the attack was preventable up until the very end when the ransomware was deployed, and that this attack once again shows that even after the initial Trickbot or Emotet infection, companies can still prevent a ransomware attack. That is, of course, assuming they’re in the habit of regularly looking for signs of an intrusion.
“While it is clear that the initial breach occurred 14 months ago, the escalation of the compromise didn’t start until around November 15th of this year,” Holden said. “When we looked at this in retrospect, during these three days the cybercriminals slowly compromised the entire network, disabling antivirus, running customized scripts, and deploying ransomware. They didn’t even succeed at first, but they kept trying.”
VCPI’s CEO said her organization plans to publicly document everything that has happened so far when (and if) this attack is brought under control, but for now the company is fully focused on rebuilding systems and restoring operations, and on keeping clients informed at every step of the way.
“We’re going to make it part of our strategy to share everything we’re going through,” Christianson said, adding that when the company initially tried several efforts to sidestep the intruders their phone systems came under concerted assault. “But we’re still under attack, and as soon as we can open, we’re going to document everything.”




“…..the IT company’s owner says she fears this incident could soon lead not only to the closure of her business, BUT ALSO TO THE UTIMELY DEMISE OF SOME PATIENTS.”
The lawsuit-cum-nuclear-option-reasoning is strong and alive in the American mindset.
“Don’t focus on my negligence!, NO, NO, think of my poor customers….” —- the continual cry we hear from U.S. businesses that continue to fall down in their duties regarding ‘basic’ info-security.
It’s all about deflecting things away from the possible “closing of their (her) business”.
Pathetic and shameful.
Not sure what your point is – her attitude is quite different from the normal “Circle your wagons, try to hide the cause, and pretend there is no serious problem” attitude often taken by victim companies.
Sure, we all want to know how this happened so that we can better learn how to protect our systems – which of course are all so secure that we have long since taken to sneaker-net Email onto disconnected systems so that an infection from a hapless Email click goes no further than that workstation. But it’s too early in the situation to expect a forensic report as part of the notification from the victim as they are in the first stages of recovery.
I use to do business with VCPI (tech side/data center) and they were “warned” against having such a dependency on Windows Server. The had 10x the numbers of servers required to do what one could on RHEL (heck a highly virtualized Z series would have been a better decision)
You do realize that it’s not only Windows servers that can be attacked with ransomware, right?
And that Windows-based networks can also be protected against ransomware, right?
The OS religious wars died a decade ago…
-ASB
You realize, do you not, that a French hospital was also listed as a victim of ransomware? VCPI is being open and transparent in its efforts to recover as well as in lessons learned.
I wish more organizations would be so.
Good.
The cloud model for healthcare is fundamentally broken and it can’t be fixed. It was a stupid experiment in cost-cutting that will deservedly result in crushing financial losses.
Entire industries have bought into this cloud snake oil. Finally, the reckoning occurs.
Separately….
This the second time that KOS cited the Vanderbilt study, even though its conclusions are bogus.
No one has ever died because of IT failures, for the simple reason that all emergent care is always provided independent of networking and records systems.
The study looked at records, not actual care; the statisticians did not observe a single health procedure in drawing their conclusions. Healthcare records are notoriously asynchronous from what actually occurs and when it occurs, which the study ignored.
cloud and outsourced ourselves to death
big and small companies alike drank the poisonous kool aid
i predict the US will have to outlaw public cloud for regulated or critical businesses within months
regulators have already indicated this is coming
The impact of breaches in the cloud supported health care is regrettable but still limited. Wait until all the, big/national/ too big to fail, financial services firms start pushing everything into the cloud… They could take down the whole economy.
“No one has ever died because of IT failures”
The fact of the matter is that there is little evidence to support this hypothesis either way – because providers and governments don’t want to attribute untimely patient expiration to their own failures of people, process or technology and secondly that when HIoT systems like medical devices fail or are suspected of causing a patient death, the first thing BMETs do is to wipe the devices of PHI for regulatory compliance reasons and initialize the thing for either return to circulation or return to the manufacturer for service. We are not actively looking, nor are our clinical staff trained to look for potential indicators of compromise in HIT and HIoT systems.
The Vanderbilt study is a vital first step in finding out what is actually happening. I would love to see the results of a study of even larger ransomware attacks and their impact on patient longevity and mortality like the Wannacry attack against the British NHS for example. Just how many Brits died prematurely as a result of this attack? I’m sure the UK government would not want this to become public knowledge any time soon – especially since they were ultimately responsible for not spending the money needed to replace, patch and secure an aging IT / HIoT infrastructure.
The bigger issue here is that we continue to brush over well planned and executed cyber attacks by extremely well trained and funded adversaries – organized crime syndicates and rogue nation states in particular, almost as misdemeanors, even when these attacks are purposely targeted at critical infrastructure industries like healthcare, when in fact we should treat these attacks for what they are – attempted murder, extortion, and cyberwar. The so called ‘long arms of the law’ seems to have become crippled stumps. The US and other governments need to step up to protect their citizens, businesses and critical industries against harm, instead of hiding with their collective heads in the sand!
“The cloud model for healthcare is fundamentally broken… It was a stupid experiment in cost-cutting that will deservedly result in crushing financial losses.”- Readership1
I generally agree.
The so called “cloud solution” is over sold in both economic terms and safety features. There is no magic genie that can provide instant business expansion and security. It takes more planning and testing to successfully and safely expand healthcare facilities rapidly.
Those top people entrusted with life and death healthcare responsibilities should be better educated on the risks of deployment to the “cloud” or datacentera – that includes following HIPPA, PII and other safety mandates. Also, those healthcare providers should have at least one backup solution in case their “cloud” deployment fails for any reason. That is just common sense. The “cloud” my be good for news blogs but healthcare is a completely different ball game.
The study looked at statistics, and the outcome drawn is statistical. It doesn’t point to any single care because that’s not the purpose of a statistical study.
You can die early because of a lack of access to medical history that prevents treatment from being tailored to your specific use case. Does’t mean any specific decision killed you.
Why do you believe that this is a *cloud* issue?
At best, it is a service provider issue — meaning that as more organizations outsource their technology support and management to an outside entity, there will be consolidation of such resources in the hands of an ever smaller number of providers, making it more tempting to hit the providers for maximum effect.
While the “cloud” falls into the same category (i.e. centralized pool of technology resources), there is nothing in the account to indicate that this was a cloud problem. There is no reason for us to conclude that if VCPI had only keep all their systems in their own data centers or co-location facilities, that this problem would not have happened.
Whether or not the cloud will result in problems for business or the economy is not the point that I am making here. I’m simply trying to understand what basis has been used for attributing the specific issues that occurred here to “the cloud”
Bad systems management is bad systems management, and none of the things that appear to have been overlooked or mishandled here appear particularly cloud related in the least.
Outsourcing is not automatically or inherently evil, but can certainly be done wrong or poorly.
Centralized systems hosting is not automatically or inherently evil, but can be done wrong or might be inappropriate or ill-advised under some circumstances. Etc.
Railing on approaches and methodologies just because, is silly. Or, at least, pointless.
Many people talk big about managing their own XYZ, but have little to no understanding of the actual costs and complexity involved in doing so. If it were easy and painless to host ones own data center, we would never have seen the rise of co-location facilities. And everyone would still be managing their own IP blocks and BGP routing. And doing their own shipping.
But, alas, some things make sense to outsource. The key is not pretending that because you aren’t directly managing the process, you no longer have any responsibility for the outcome.
-ASB
This is pathetic and most concern not just about the company but those innocent patients that may eventually trade their health for this heart-breaking issues.
Hopefully they get out of it sooner and also learn to make cybersecurity check a routine to avoid such in future.
But, why is the cloud, the future? I believe you forgot the other part. Not every it person is a superstar. And ma and Pa companies cannot keep superstars on their payroll. So, there has to be some other way. Such as, superstars spreading their talents to help the small company. Another idea, most colleges are three to five years in their classes behind, some even further, but their research groups are up to date, why not combine? And, remember this is supposedly a secure VPN company. And VPN was proven holey about a year ago. But they didn’t update? Or couldn’t update, now, insurance companies work with the same basic system, VPN over internet systems, and it’s well known, apple, microsoft, Android and Linux all update their systems, and they all change system settings without notice, even system people don’t notice till too late. Yeah, I think, someone with knowledge and enforcement duties should go and see where and why’s, and see what happened, and maybe they can get to the who.
Good article Brian.
80,000 computers in 110 nursing homes?
It is probably 110 nursing home companies, each with multiple facilities.
That’s right. It’s 110 customers of VCPI, but 2,400 facilities.
That is exactly what it is. I work at a facility that is affected by this and our parent company has 50+ buildings. It has crippled us.
80K computers (you forgot to read the Citrix part) 😉
(didn’t know people used that anymore)
I have to agree about the cloud model being inappropriate. A single PC should be able to handle all the patient records for a nursing home. Why put the data in the cloud?
Why should that computer even be connected to the internet? PCs are cheap, why try to make one do everything?
“I have to agree about the cloud model being inappropriate.”
Gosh, who couldn’t have seen this coming from a thousand miles away?
And single PCs don’t get ransomware? Since a single PC can’t handle all the staff input, you end of up a network of PCs. I hate to keep picking on Bob on accounting, but Bob always clicks on those email links…and you have a whole network of infected PCs.
The deal with the cloud is things like redundancy and backups are easy. But hey, you have to know what you are doing.
While your statement is true, I think people are stemming more from the fact that the cloud providers create a single point of failure, meaning multiple institutions can be brought down at once. At the end of the day though, these individual institutions do need to learn to manage their risks and learn proper techniques for securing their data.
The fact that cloud providers such as VCPI create a single point of failure in this case is exactly why they and many other MSPs are being targeted for attacks and demanding 14mil payout. I agree the individual institutions need to manage their own risk better and have their own backups. Realistically speaking as a security practitioner who spent a lot of time in healthcare I can tell you those are the reasons they’ve outsourced in the first place. Compliance and security are two different things. As a consultant I’ve seen first hand that all it takes is one mis-configured server exposed on port 3389 and a test account (password123) in the domain admins group that an unidentifiable sysadmin forgot about a while ago. After that you’re files are locked and you’re calling in my team to figure out what went wrong…
Agreed about the single point of failure, but that is inevitable.
ISPs also constitute a single point of failure for many businesses. Similarly payment processors, etc.
What all these single point of failures need to understand, is that they need to apply security practices to a much greater degree than any single one of their customers, because they are an aggregation point — and a commonly known one at that.
-ASB
The allure of the Cloud and the initial cost savings are having CFO’s trip over themselves to implement and cut support staff to get the fast win for their bonus. (See How much revenue I have saved!!??)
However when it comes to healthcare, there should always be a hybrid system, where portions of the data is local and replicated off-site and the rest in the ‘Cloud’.
These companies need to conduct Business Impact Analysis and create their Disaster Plans to quantify the cost of not having their data and how it affect their bottom lines, and all the technologies they believed they didn’t need or couldn’t afford, now sounds like pennies compared to the cost the outage has caused them.
The study looked at records, not actual care; the statisticians did not observe a single health procedure in drawing their conclusions. Healthcare records are notoriously asynchronous from what actually occurs and when it occurs, which the study ignored.
People are blaming the cloud model. It’s true that the cloud has spawned new types of criminality. Since its inception the number one concern of everyone (including the criminals) was security. I worked in hospitals for many years as a practice manager and IT so I am aware of the positives and negatives of connecting to the cloud.
The key line for me: ‘Holden said the attack was preventable up until the very end when the ransomware was deployed..”
The answer isn’t to disconnect from the cloud. The answer is and has always been formulation and implementation of better policies and procedures that ensure the attacks are not successful.
I would go a step further and say that ENFORCING the polices, procedures and incident response plans are and have always been the problem.
You have can policies drafted and formulated. But they don’t always get followed or taken seriously.
Part of the broader issue is how organization do NOT TAKE SECURITY ISSUES SERIOUSLY. Why? Lack of security awareness and security-minded culture.
It’s obvious the company did not understand the vital importance of Cyber Security and safe guarding data. Ransomware has been making rounds for years, any organization with a CIO worth anything, would have IPS and IDS solutions deployed to prevent attacks of this nature. It’s not ‘IF” it will happen but when.
With proper technologies deployed like Carbon Black, Crowdstrike, could defend against attacks of this nature, proper hourly, nightly and offsite backups, attacks of this magnitude could never prosper.
This is just another example of many past and many future tragedies of the human condition being exploited down to the very basic level of health care. The emr should never have been privatized and handed to the profit sector. We have created, on a petri dish of human health, an incentivized micro economy based on cloud based corporatized IT companies, software developers, fear mongerers and dark web criminals. If we want to maintain our basic humanity we need to purge the scum of profiteers and start over. Go back to paper charts for now and build a universal system that works on one software program written on basic with 16 bit intranet closed system. This would allow the true Healthcare doctors communicate with each other about their patients across the globe in real time without parasites.
From outside, Trojan detection was being made on their Proofpoint-provideed Mail Exchangers since at least June 4 2019 (Emotet/Tofsee/Kryptik…)
http://www.virustotal.com/gui/ip-address/67.231.156.10/relations
http://www.virustotal.com/gui/ip-address/67.231.148.10/relations
Do you imagine that one day perpetrators of these ransomware crimes will be charged with murder if in fact patients do die as a result of the inability to access their records?
NO I do not.
Firstly, there is the issue of attribution – Who conducted a specific attack and where are they located? Often this is not just one person or group but many groups in different locations.
Secondly, what to do about it? Perpetrators of these types of crimes are often located in parts of the world with no effective law enforcement, corrupt police and government officials that have been bought and paid for, and in countries that lack extradition treaties with the rest of the world. Even if an extradition treaty exists, nuances in legal systems and language often prevents extradition from being accomplished even with overwhelming evidence in support of a crime having taken place.
Thirdly, when extradition fails, what are your options? The US has been marginally successful in renditioning the worst offenders as Krebs reported 2 years ago with Roman Seleznev, but this is a slippery slope as I wrote about at the time https://www.cyberthoughts.org/2017/04/a-slippery-slope.html at the time. But many, many more cyber criminals go on acting with impunity, confident that they will never be caught!
Finally, and perhaps most worryingly what do we do when the perpetrator of a crime is a nation state? The PRC has tens of thousands of cyber warriors – complete PLA army units focussed on cyber crime against its neighbors and the rest of the world. This then becomes an act of war. Do you respond to economic and political damage with sanctions and trade embargoes? And if so, what is the cost given that China has essentially made the world addicted to its cheap subsidized goods? How does the west rediscover and rebuild its manufacturing capability given the efforts of China to destroy domestic capability via economic warfare? How do we all disentangle our PRC supply lines? How should a country respond when an attack results in the fatality of one or many of its citizen? Turn a blind eye?
Communist China is not alone. WannaCry was attributed to North Korea and Not Petya to the Russian GRU. Cyber attacks that blew up Turkish oil pipelines and attempt to blow up the Ukrainian power grid have been attributed to the Russian FSB, while the hands of Iran are all over other attacks against US dams and other critical infrastructure. How should we respond to these nation-state attacks without having to resort to nuclear exchange? Its very worrying and concerning but at the same time we can’t allow nation states to cause the death of patients in our hospitals or other injuries to our citizens.
We need to establish international norms for acceptable behavior as the Harvard Political Review wrote about recently https://harvardpolitics.com/covers/cyberespionage-need-norms/ NATO has already indicated that the collective defense clause could be enacted in the case of a cyber attack against one of its members. Israel took things a step further in May this year by dropping a large bomb on the roof of HamasCyberHQ just before a cyber attack could be launched against its people, as I wrote about at the time https://www.cyberthoughts.org/2019/05/when-cyber-attacks-go-too-far.html
These are certainly interesting if not scary times!
Your last comment reminds me of the ancient Chinese curse: “May you live in interesting times.” Yes, we certainly do.
This article is rather full of hyperbole and slim on technical details. Citing studies about increased deaths tangentially attributable to ransomware seems to be an unreasonable indictment in these early stages of this incident.
It’s all well and good for Mr. Holden to claim that it was preventable up until the end. But, in reality any incident is preventable, up until the end when the incident has already occurred. With the lack of technical detail, Mr. holder’s claim is accusatory hyperbole.
Perhaps Brian can get some technical detail and first person insight from Lodestone, the incident response company that is working with VCPI.
In reading VCPI’s response letter, it does seem as if they are responding appropriately to the event. Hopefully, no one will die and we will get a more and better detailed article.
I’m also very curious about the cyber insurance company(Beazley?), who seems to have chosen not to pay the ransom despite the major impact and “risk to life” due to this incident.
Golly, Anonymoose. So sorry I couldn’t get all the nitty gritty detail of the breach AND be the first to report on it.
Great article and I have to say the comments were insightful at the least. #keepcolaborating:)
We have to start tying certain critical operations to a physical action that can only be performed at the server. Want to wipe shadow copies? or modify the schedule? Someone needs to be at the server and physically hold a button down in order to save those changes. Same with erasing backups or modifying backup jobs. Can’t be done without someone at the server holding down the button that allows the changes to be committed. Not a switch that can be left in that position, a button which is released and disables any further changes. The only real security is physical, nothing else can be trusted.
Sad!I think as tempting as may be to cut cost and host services including storing health data in the cloud it is not a great idea. I think its time hospitals and smaller facilities like nursing homes start saving their data in their own local data centers and [properly securing them if not keep them away from the internet. 3rd party cloud providers are really untrustworthy!!!!
>>> some clients will soon be in danger of having to shut their doors if VCPI can’t recover from the attack. – “We’ve got some facilities where the nurses can’t get the drugs updated and the order put in so the drugs can arrive on time,” she said. “In another case, we have this one small assisted living place that is just a single unit that connects to billing. And if they don’t get their billing into Medicaid by December 5, they close their doors. Seniors that don’t have family to go to are then done.
Today’s “seniors” were Baby Boomers, Hippies back in the day. They never gave up the drugs, did they? That’s quite a party at the old folks home. They really do live it up till they die.
Done? I hope not. Maybe they can party less and live longer. Commercial and pharmaceutical druggers are not usually capable of the critical thinking necessary to secure their computer networks online.
Has ANY company that uses G Suite ever been hit with ransomware? Seems G Suite is the only true safe provider.
Boy its getting a little Shilly in here…
I thought patients would welcome being sent to “The Cloud.” Beats the alternative.
“…. Thanks Alex, let’s go now to the comments section and hear what the real experts have to say.”
My question is this. If the intruders were in the system since Sept. 2018, why did they wait so long to deploy their ransomware? Most thieves like to get in, take whatever, and get out with their goods.
Was this system so complex that they needed over a year to figure out the configuration? There were 110 clients, each with their own, probably very similar, configurations. Passwords may have been an issue, but these intruders probably got themselves an administrator account that negated the need for valid passwords. The longer you’re in the system, The better chance of a random IT guy stumbling upon your presence, maybe through log files of massive transfers of data. Or possibly an update interfering with their operation.
I believe many of these initial infections with Emotet/Trickbot are somewhat opportunistic, but the thing is they are getting so many victims that they often don’t get a chance to exploit the access until the malware is cleaned up internally. Which may help explain why this company was infected multiple times over a year before the bad guys got around to figuring out what they had.
This just proves that these ransomware cyber-criminals are one step above convicted pedophiles
Being on the board of a non-profit care facility, boy does this give me the creeps regardless of who is to blame, if anyone. I’m not an IT person but isn’t it possible to have adequate redundancy in the stored data to avoid this? Is there any type of insurance available to cover losses or even ransom requests? Nursing homes use outside data services in order to retain experts and have a quality system, and the result is a disaster. If they then try to handle computer services in-house, no doubt the same type of disaster could take place as well. Maybe the best back up includes typewriters, paper, copy machines and file folders?
I agree with your comments about redundancy and data backups. I am personally responsible for managing the expenses of a severely disabled relative. Every single receipt matters, even for a can of dog food that was purchased to feed her service animal. I scan everything into my computer, note the expense in a spreadsheet file at the time the expense is created, and I routinely back up this entire folder onto an external hard drive. Due to the personal nature of this information, I don’t upload anything to the cloud, but I do regularly email myself documents and scanned images, and everything is then forwarded to a secondary backup email account. I keep the hardcopy originals in a manila file folder and it gets stored away somewhere in my office.
Joe – if you are on the BoD of a non-profit healthcare provider, you should be very creeped out. Especially if you don’t have someone at the organization who is working everyday to not only implement protections against these attacks, but also plan for when they do occur which would include your containment, eradication, and recovery processes, as well as business continuity and disaster recovery plans. If anything in that last sentence is new to you, I suggest finding someone asap. They would be well aware of the options you have for cyber insurance, and off-site data backups (which is what you are asking about). They would also be reporting directly to the BoD as your chief security officer, and not proxying through any IT leadership, if possible.
Curious if you know which CPA firm performed their SOC 1 audit? Their site claims they have “really tight” security. https://www.vcpi.com/technology-center
SOC 1 is an auditor report on financial reporting. It does not guarantee anything about security.
KPMG and they issued qualified opinion
The ultimate programming and network administrator God is named Karma. It’s one thing to hold (just for example) a mega company like IBM hostage and demand ransomware to unlock their HR department records that were lamely stored “in the cloud.” But to hold nursing home patient health records hostage? Oh no. There are some places that even bad ***** really shouldn’t go.
Krebs, I really for for them. Whether the study about the deaths is true or not, what can we about ransomware like this? I am curious how can i contribute to stop this crime
What company most recently announced they are getting into the healthcare data business, who also has the staff who could very easily hack any system, blame it on another country ( as they always do) and get away with it?
SCUM! All of them!#
I give up. Which company?
Google: https://arstechnica.com/tech-policy/2019/11/google-you-can-trust-us-with-the-medical-data-you-didnt-know-we-already-had/
https://khn.org/news/no-safety-switch-how-lax-oversight-of-electronic-health-records-puts-patients-at-risk/
excellent review of how the industry got Congress to gut basic protections and oversight in Electronic medical records. The federal oversight of this critical infrastructure makes the FAA look like geniuses.
People have been killed by EHR functioning normally. God help us when they get hacked. The average community hospital IT department is a joke
ask any doctor if EHRs have improved patient safety, their workload or lives. I practiced medicine for 40 years but retired early driven out by EHRs
These scum need to meet justice. No doubt they would cause a bomb to go off, or sink a ship, gladly hurt or kill anyone for money. All these people so soft because its a “computer crime” not is a human crime, is terrorist activity and needs to be dealt with accordingly.
If your mother dies in one of these nursing homes due to these punks, you will be ready to burn the hackers at the stake too.
No amount of tools will always block criminals, only death will stop them.
Having been an ED RN, I can tell you that when a patient presents with certain symptoms, that we immediately start treatment based on protocols. This is because you cannot wait for results from X-rays or labs, which take time. You go back after the patient is stabilized and then do your charting. You recall things best you can. Paperwork is not the priority when a patient’s life is on the line.
Saying they want the public to know everything but their website doesn’t even mention anything about the ransomware attack… they’re actually posting offers for taking on new clients..and why to choose them.
Why are you blaming vcpi? The unabated tide of security breaches has boosted terrible pressures on CIO’s and their role in the organization. They probably have many security measures in place – no one is safe against cyber attacks of this magnitude – we can only manage the risk. The way technology is used is changing every day and attackers will continue to steal credentials as a primary vector for accessing organizational information. This is a teachable moment for all of us. Instead of getting on a high podium of negative blaming – why not lend support to this small WI company and take to heart this is too close to home and can happen to any of us. It seems they contained the damage quickly and are working diligently to get everyone affected up and running. We can all learn lessons from this incident and implement appropriate changes to our security policies; but no one is safe no matter how many secure policies are in place – and to say they could or should have been able to prevent this – really? It is easy to sit on the outside and judge – however, we are all busy in our day to day work environments just trying to do our jobs and feed our families. I think the resilience of this little company is admirable and I can’t imagine the stress and personal sacrifice that must occur when something like this happens. I for one applaud their efforts and am sorry this ever happened to them.
Cmon, attacks like these happen to companies everyday who “think” their security posture is robust and they can cut costs on mandatory infrastructure components like daily backups and off site replication.
I’m sure the Cloud vendor told them they didn’t need to do that anymore because their data is in the cloud.
They didn’t even have backups, which shows #1 the leaders in charge over looked this vital function as they have probably thrown money at the problem thinking cloud is the answer for everything.
These types of attacks has been happening in frequent over the last 6-10 years, and still their is organizations out there not even fathoming that this could happen to them.
Well said. This problem is well outside the ability of a single company (large or small) to deal with. People who blame the victim aren’t seeing the obvious – our current approach of more security, less cloud (wasn’t it more cloud just yesterday?), less Windows, more RHEL, etc. isn’t working. I hate to say it, but without a fundamental change in our approach, our companies are in for a rough ride.