Many readers probably believe they can trust links and emails coming from U.S. federal government domain names, or else assume there are at least more stringent verification requirements involved in obtaining a .gov domain versus a commercial one ending in .com or .org. But a recent experience suggests this trust may be severely misplaced, and that it is relatively straightforward for anyone to obtain their very own .gov domain.

Earlier this month, KrebsOnSecurity received an email from a researcher who said he got a .gov domain simply by filling out and emailing an online form, grabbing some letterhead off the homepage of a small U.S. town that only has a “.us” domain name, and impersonating the town’s mayor in the application.
“I used a fake Google Voice number and fake Gmail address,” said the source, who asked to remain anonymous for this story but who said he did it mainly as a thought experiment. “The only thing that was real was the mayor’s name.”
The email from this source was sent from exeterri[.]gov, a domain registered on Nov. 14 that at the time displayed the same content as the .us domain it was impersonating — town.exeter.ri.us — which belongs to the town of Exeter, Rhode Island (the impostor domain is no longer resolving).
“I had to [fill out] ‘an official authorization form,’ which basically just lists your admin, tech guy, and billing guy,” the source continued. “Also, it needs to be printed on ‘official letterhead,’ which of course can be easily forged just by Googling a document from said municipality. Then you either mail or fax it in. After that, they send account creation links to all the contacts.”
Technically, what my source did was wire fraud (obtaining something of value via the Internet/telephone/fax through false pretenses); had he done it through the U.S. mail, he could be facing mail fraud charges if caught.
But a cybercriminal — particularly a state-sponsored actor operating outside the United States — likely would not hesitate to do so if he thought registering a .gov was worth it to make his malicious website, emails or fake news social media campaign more believable.
“I never said it was legal, just that it was easy,” the source said. “I assumed there would be at least ID verification. The deepest research I needed to do was Yellow Pages records.”
Earlier today, KrebsOnSecurity contacted officials in the real town of Exeter, RI to find out if anyone from the U.S. General Services Administration — the federal agency responsible for managing the .gov domain registration process — had sought to validate the request prior to granting a .gov in their name.
A person who called back from the town clerk’s office but who asked not to be named said someone from the GSA did phone their office on Nov. 24 — which was four days after I reached out to the federal agency about the domain in question and approximately 10 days after the GSA had already granted the phony request.
WHO WANTS TO BE A GOVERNMENT?
Responding today via email, a GSA spokesperson said the agency doesn’t comment on open investigations.
“GSA is working with the appropriate authorities and has already implemented additional fraud prevention controls,” the agency wrote, without elaborating on what those additional controls might be.
KrebsOnSecurity did get a substantive response from the Cybersecurity and Infrastructure Security Agency, a division of the U.S. Department of Homeland Security which is leading efforts to protect the federal .gov domain of civilian government networks [NB: The head of CISA, Christopher C. Krebs, is of no relation to this author].
The CISA said this matter is so critical to maintaining the security and integrity of the .gov space that DHS is now making a play to assume control over the issuance of all .gov domains.
“The .gov top-level domain (TLD) is critical infrastructure for thousands of federal, state and local government organizations across the country,” reads a statement CISA sent to KrebsOnSecurity. “Its use by these institutions should instill trust. In order to increase the security of all US-based government organizations, CISA is seeking the authority to manage the .gov TLD and assume governance from the General Services Administration.”
The statement continues:
“This transfer would allow CISA to modernize the .gov registrar, enhance the security of individual .gov domains, ensure that only authorized users obtain a .gov domain, proactively validate existing .gov holders, and better secure everyone that relies on .gov. We are appreciative of Congress’ efforts to put forth the DOTGOV bill [link added] that would grant CISA this important authority moving forward. GSA has been an important partner in these efforts and our two agencies will continue to work hand-in-hand to identify and implement near-term security enhancements to the .gov.”
In an era when the nation’s top intelligence agencies continue to warn about ongoing efforts by Russia and other countries to interfere in our elections and democratic processes, it may be difficult to fathom that an attacker could so easily leverage such a simple method for impersonating state and local authorities.
Despite the ease with which apparently anyone can get their own .gov domain, there are plenty of major U.S. cities that currently do not have one, probably because they never realized they could with very little effort or expense. A review of the Top 10 most populous U.S. cities indicates only half of them have obtained .gov domains, including Chicago, Dallas, Phoenix, San Antonio, and San Diego.
Yes, you read that right: houston.gov, losangeles.gov, newyorkcity.gov, and philadelphia.gov are all still available. As is the .gov for San Jose, Calif., the economic, cultural and political center of Silicon Valley. No doubt a great number of smaller cities also haven’t figured out they’re eligible to secure their own .gov domains. That said, some of these cities do have .gov domains (e.g. nyc.gov), but it’s not clear whether the GSA would allow the same city to have multiple .gov domains.
In addition to being able to convincingly spoof communications from and websites for cities and towns, there are almost certainly a myriad other ways that possessing a phony .gov domain could be abused. For example, my source said he was able to register his domain in Facebook’s law enforcement subpoena system, although he says he did not attempt to abuse that access.
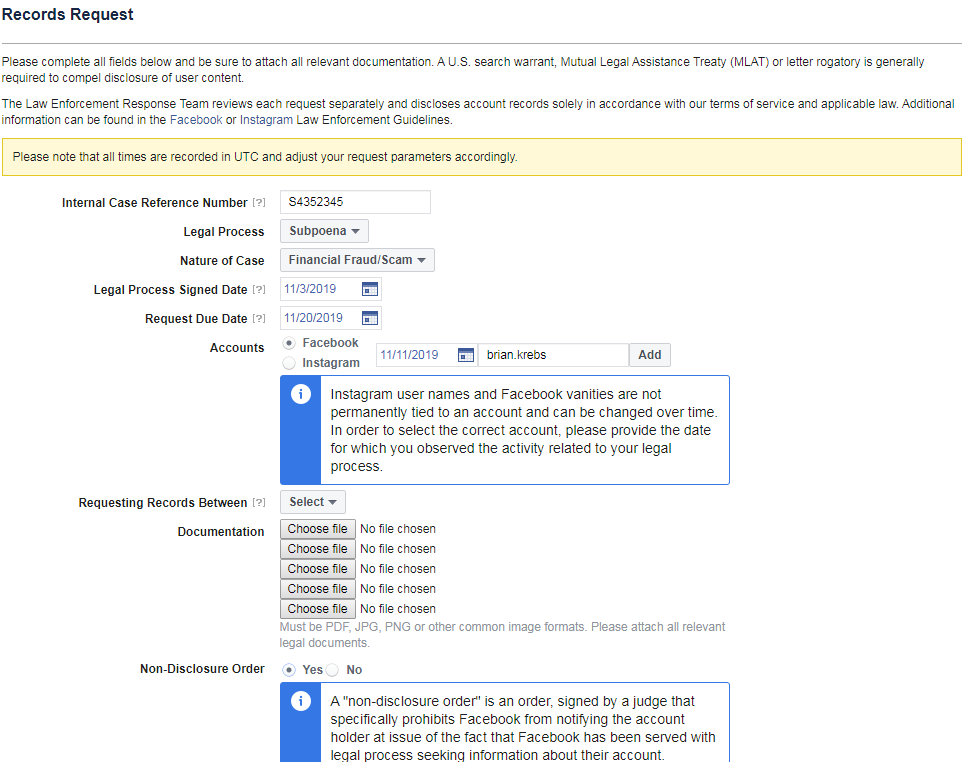
The source who successfully registered an impostor .gov domain said he was able to use that access to register for Facebook’s law enforcement subpoena system.
Now consider what a well-funded adversary could do on Election Day armed with a handful of .gov domains for some major cities in Democrat strongholds within key swing states: The attackers register their domains a few days in advance of the election, and then on Election Day send out emails signed by .gov from, say, miami.gov (also still available) informing residents that bombs had gone off at polling stations in Democrat-leaning districts. Such a hoax could well decide the fate of a close national election.
John Levine, a domain name expert, consultant and author of the book The Internet for Dummies, said the .gov domain space wasn’t always so open as it is today.
“Back in the day, everyone not in the federal government was supposed to register in the .us space,” Levine said. “At some point, someone decided .gov is going to be more democratic and let everyone in the states register. But as we see, there’s still no validation.”
Levine, who served three years as mayor of the village of Trumansburg, New York, said it would not be terribly difficult for the GSA to do a better job of validating .gov domain requests, but that some manual verification would probably be required.
“When I was a mayor, I was in frequent contact with the state, and states know who all their municipalities are and how to reach people in charge of them,” Levine said. “Also, every state has a Secretary of State that keeps track of what all the subdivisions are, and including them in the process could help as well.”
Levine said like the Internet itself, this entire debacle is yet another example of an important resource with potentially explosive geopolitical implications that was never designed with security or authentication in mind.
“It turns out that the GSA is pretty good at doing boring clerical stuff,” he said. “But as we keep discovering, what we once thought was a boring clerical thing now actually has real-world security implications.”




That’s we you need, a phishing scam criminal getting their hands on a .gov , think of the chaos it could create within any state with regards to paying taxes.
The US government tends to do communications by mail. Perhaps always uses the mail, I don’t know. My tax assessor has an option for email only. This seems like a bad idea to me so I didn’t opt in.
I could see them doing both. Send a written letter and then email or in the letter tell them to go to a .gov website.
Between the letter and the .gov site people would provide all kinds of personal info, banking info, etc.
You could easily capture in just a few days a boat load of sensitive data from people including copies of passports, drivers licenses, birth certs, etc.
Philadelphia uses phila.gov
Philadelphia is the name of a city in Georgia as well, so neither city can have the full URL.
Why in your example do you say “left leaning” cities? This would be a ploy right out of a democrat playbook. Or are you say they’d be the only ones easily duped? Also, one would only have to be watching the news, which they would be on election night, to know that this wouldn’t work. It seems as if though you have fallen into the “sky is falling” mentality, spreading more rumours and hyperbole so a loser could then say ” it, it was the Russians and their damn .gov email spam campaign is what did it, I tell ya!!!
Apparently “left leaning” has beenedited to read “Democrat leaning”.
wat
welp. get the heat boys we found the snowflake.
Democrat playbook? the democats werent the ones recently caught engaging in election fraud.
The history of voter disenfranchisement is dark, and has overwhelmingly been targeting racial minorities. Maybe, back when Dixiecrats (southern Democrats) were in power, 19th century… they were the ones suppressing the popular vote… but modern history is clear…. Minorities and urban voters are the most susceptible to threats of violence at the polls.
Rural voting locations tend to be more Republican leaning… and generally aren’t as densely populated. Meanwhile, districts with huge lines at the polls, tend to vote Democrat.
The analogy is accurate, “get over it”.
> A review of the Top 10 most populous U.S. cities indicates only half of them have obtained .gov domains, including Chicago, Dallas, Phoenix, San Antonio, and San Diego.
> Yes, you read that right: houston.gov, losangeles.gov, newyorkcity.gov, and philadelphia.gov are all still available. As is the .gov for San Jose, Calif., the economic, cultural and political center of Silicon Valley.
A minor nit: Many of these cities do have a .gov domain. For example, NYC has nyc.gov. So, I would suspect (or I’d hope) the GSA wouldn’t issue newyorkcity.gov to a random fraudster as easily.
Houston has houstontx.gov.
Philadelphia has phila.gov.
San Jose has sanjoseca.gov.
LA has .. lacity.org? That’s a bit unexpected.
maybe it would be a good idea for cities to buy all the possible .gov domains for their city
Possible, but difficult given the iterations. Not a great security control anyway given how easy it is to use international characters in domain names.
I don’t know of any unicode/punycode characters allowed or available in TLDs. So no one could set up a springfield.gоv, as the TLD doesn’t exist and can’t be created.
Throw both о & o into cyberchef gchq.github.io/CyberChef/ and convert to hex
I hope your source gets thrown in jail. “Security research”, is no excuse for breaking the law.
I don’t think he broke any laws to be perfectly honest. Just poking around and breaking into a museum to see if you can have the possibility of taking the Crown Jewels is not the same as taking the Crown Jewels.
Who got hurt here? This debate has already been answered and it’s the core principle the Security Research community is based on. Careful with your words, those sentiments could bring down an industry and draw Icarus to the sun.
John, your comment is WAY misinformed.
” breaking into a museum to see if you can have the possibility of taking the Crown Jewels is not the same as taking the Crown Jewels”
Um… no, not the same. But there are laws against breaking and entering. Intent matters… and if the jury finds there was no other legit reason other than targeting crown jewels.. it is still illegal.
Attempted murder is still illegal.
Attempted quid pro quo for personal gain is still abuse of power.
Bribery that fails, is still bribery, and illegal.
Then we would not know about this vulnerability, if those like you proceeded.
You’re just petty, research is a key part of finding vulnerabilities and intent matters immensely.
I hope one day there are proper laws in the USA to protect whistleblowers.
Pretty simple : if all you did was the minimum to assess security and you report it right away to proper channels (provided they exist) without causing any harm to anyone, nor benefit from it, then you can claim that protection.
Pretty much all security research is made illegal by laws, and yet, people reporting this kind of issues are extremely helpful to their country, likely much more than you are.
An even bigger crime than obtaining a .gov domain illegitimately is this website not being mobile-friendly.
Maybe you should try giving one to someone other than yourself.
There is precedent for allowing multiple .gov domains for the same city. Austin, TX, has austin.gov, which redirects with a 301 to austintexas.gov.
> “I used a fake Google Voice number and fake Gmail address,” said the source, who asked to remain anonymous for this story but who said he did it mainly as a thought experiment.
A minor correction: the term “thought experiment” dues not apply when actually carrying out what you were thinking about (I’m the author of https://thoughtexperiments.net).
This is an interesting proposal. This disproves that Security Research is a thought experiment and goes into practicality into proving that it works.
San Jose, Calif. uses sanjoseca.gov.
I would expect official .gov names for municipalities to include a state designator. There is far to much duplication in names otherwise. How many towns can lay claim to paris.gov?
In Georgia there are actually two cities named Bethlehem located in opposite ends of the state
I can’t find two Bethlehems in Georgia. Which counties are they in?
It was on a map years ago, checking into things there is also an area around Augusta that is known as “Bethlehem Historic District”. I thought it was Bethlehem, but there was one city in north and south Georgia with the same name.
The only one I am aware of is in Barrow County.
They generally do have to have a state designator (or other similar attribute). If the city has a unique name, one can apply for an exemption. I know because I did just that, and it was granted .
Dearest Mr Krebs, You put a lot of thought & real-world knowledge into your posts, You choose your words carefully & point out real world implications based on actual facts. Right-wing extremists *are* a real threat (as those of us who don’t drink the Fox koolaid know) Election manipulation & voter suppression efforts are historically aimed at the Democratic-leaning electorate. The possibilities of of this are extremely troubling…
Now that’s funny. Thanks Mystere, a little comedy to start off the day is a good thing.
Right Kool-Aid, Left Kool-Aid, Purple Kool-Aid, the results are the same for sheeple who depend on the government to think for them.
I suppose letting rich people or pundits on the TV/radio tell them how to think is better?
None of which has anything to do with Brian’s article. Please keep your political BS on HuffPo or MoveOn where it belongs.
It was directly mentioned in the article.
Please learn to read before you suggest other people should be quiet.
In Chicago they used to say that the election wasn’t over until all the votes from the cemetery were counted. Which party do you think that practice benefited?
That was a rhetorical question. Go read some history.
History is not on your side Jon.
Please provide evidence that a politician (or anyone in Chicago) said this phrase.
Yes, that is always the accusation from the right, that the left is getting dead people to vote. But that kind of massive voter fraud doesn’t actually happen in real life. The worse that happens is they don’t purge registration rolls after they die. That isn’t the same as voting.
The real problem is that living voters get their registrations purged because they share the same name. Registration purges tend to over do it, and they know it. And this is ultimately the intention of Republicans, to scare people into a fake crisis, so they overreact and purge as many people as possible in left leaning districts, knowing more living Democrats will get purged in the process.
The reality is that, just like anything in cyber security, the biggest risk is from remote attackers.
Absentee ballots allow mail fraud to vote, which can be done at a much larger scale than in-person fraud that is very slow and limited to very few extra votes. With the poll watchers, there is also a much higher risk to the fraudster. Meanwhile, absentee voting carries much less risk, and can be orchestrated at scale. Of course Republicans won’t dare look into this, as they benefit more from these kinds of votes.
The bottom line is, Democrats are the populous party right now… and that means the less populous party benefits from suppression and disenfranchisement. And suppression is FAR easier and more effective than bolstering.
ballot fraud… Like the Ballet Harvesting done all over California.
Yes, exactly. Ballot harvesting is newly allowed in California. It is a terrible idea and should be illegal.
Of course, with the Electoral College, it won’t really matter for presidential elections, as it is a very safe blue state.
Ballot Harvesting in North Carolina though… definitely a serious problem and the reason it became legal in California.
A story from Ars that supports your:
https://arstechnica.com/tech-policy/2017/07/how-to-get-free-us-military-weapons-build-fake-website-and-dod-will-oblige/
Or you could be like Miami and not bother with getting a .gov at all https://www.miamigov.com/Home
Good info on the threats surrounding .gov domains – and great feedback from the thread.
One other thing I am glad you cleared up:
“[NB: The head of CISA, Christopher C. Krebs, is of no relation to this author].”
🙂
Great article and thanks to the feedback thread guys!
I am also you cleared this one up:
[NB: The head of CISA, Christopher C. Krebs, is of no relation to this author].
🙂
can you send it to address 411 M.L.King blvd Gretna Folrida 32332…Name is DavidDewayneRobinson….Contrack number is 8505447380
Since my company has been using Google Apps / now GSuite for over ten years, their Web UI has been increasingly obscuring domain and also email addresses. If the trend continues, I’m not sure that anyone is going to closely inspect what is, or is not valid. Even examining all the email headers today is a daunting task that I only do if I’m really very interested in trying to discover a fraud source. Let’s also remember that the DNS system itself is rife with its own set of security problems. Redirection has been the staple side-business of every ISP, Google, Open-DNS (until Cisco bought them anyway), etc. Most any validations done today should be suspect, if it is really a critical transaction. Did that tree really fall since I didn’t hear it??
Methods for quickly and reliably testing our own security is something that no one is really trying to design into the products we use. Great Security => Great Complexity = Lots of Training = Few Experts = Simplifying UIs = Limited Ability to Validate = Lousy Security.
.gov should be available only to the U.S. federal government. But, to anyone who gets an IP address with that TLD, he’ll learn it isn’t all that wonderful. .gov addresses often face millions (no exaggeration) of hostile robotic attempts every day, from kids to criminals seeking the geek prestige, and bragging rights that go with successful access of a Federal network. If you like having an outside facing host handling that drag and want to develop your network security chops have at it.
+1
I work for a state government agency. When we created a vanity domain for a marketing campaign, we wanted to use a .gov to make it more legitimate and trust worthy. We had to jump through a couple of more hoops in our state than what you described and were required to have executive level signature. I believe your researcher, and not surprised that the same process is not always followed…but ours was harder than that….
Interesting and timely, given that a bill is moving through Congress that would make it easier for local governments to obtain dot-gov addresses. The bill also will give CISA, rather than GSA, authority to issue dot-gov addresses. The dot-gov addresses come with CISA’s network security and anti-spoofing defenses, but let’s hope they devote some resources to ensuring recipients are actually eligible. The bill is the DOTGOV Online Trust in Government Act (S 2749).
“it’s not clear whether the GSA would allow the same city to have multiple .gov domains”
I want to point out that San Francisco has at least two: sanfrancisco.gov redirects to sf.gov.
Being from Rhode Island I can understand how easy this was to accomplish.
Philadelphia.gov could only be registered by a town in Iowa.
Since about 15 years ago, municipalities must include the state name or abbreviation in their .GOV domain name.
https://www.gsa.gov/policy-regulations/regulations/federal-management-regulation-fmr/idtopicx2x89838#idconceptx2x90145
Older .gov domains like NYC.GOV and BOSTON.GOV were grandfathered. Philadelphia missed that window.
Also want to point out that the GSA charges $400 a year for a domain name. It’s not
It is astonishing to read such kind of article. this is also a huge phishing Scam government should take steps on it.
Another example of fine reporting from Mr. Krebs.
I sincerely, hope the powers that be don’t attempt to “Shoot the Messanger” — i.e. the researcher who broght this to their attention.
I trust that his contact thru Brian will help insulate him from the various bureaucrats (and their subcontractors) who SHOULD be professionally embarrassed by these revelations.
It’s appalling – but unfortunately, not surprising – that 5+ years after the huge OPM data breech; major branches of the bureaucracy are still incapable of implementing even the most rudimentary safeguards.
JLW
Seconded – better a white or gray hat found this than someone who could have done a ton of damage
Us at CNN Will Tell our readers about this.
I never thought that. Even .gov email we trust 100 percent. Thank you for eye opener.
The researcher did for free what the GAO would have probably paid a contractor to do and was proactive in doing it.
Governments hate to admit mistakes and tend to seek revenge when their shortcomings are pointed out.
Our county uses a sub domain at in.us, I’m going to see if our town wants a .gov versus our .org.
Does anyone here know if being killed by a right-wing extremist is different than a left winged one?
San Diego has used:
City of San Diego Official Website
https://www.sandiego.gov
for years. Why does your article list San Diego as not having a .gov TLD?
Correcting the article would make for smoother reading
You might want to read the story a little more closely. It says quite clearly that they DO have a .gov.
“… proactively validate existing .gov holders, ….”
Is it really being “proactive” when they’re reacting to this example?