Anyone searching for a primer on how to spot clever phishing links need look no further than those targeting customers of Apple, whose brand by many measures remains among the most-targeted. Past stories here have examined how scammers working with organized gangs try to phish iCloud credentials from Apple customers who have a mobile device that is lost or stolen. Today’s piece looks at the well-crafted links used in some of these lures.
KrebsOnSecurity heard from a reader in South Africa who recently received a text message stating his lost iPhone X had been found. The message addressed him by name and said he could view the location of his wayward device by visiting the link https://maps-icloud[.]com — which is most definitely not a legitimate Apple or iCloud link and is one of countless spoofing Apple’s “Find My” service for locating lost Apple devices.
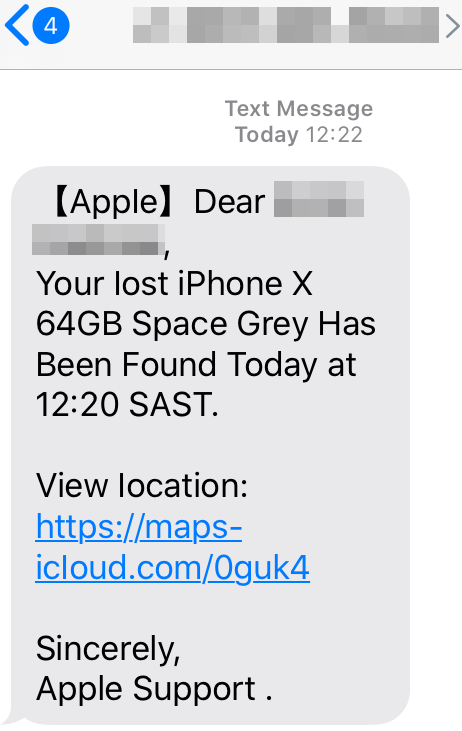
While maps-icloud[.]com is not a particularly convincing phishing domain, a review of the Russian server where that domain is hosted reveals a slew of far more persuasive links spoofing Apple’s brand. Almost all of these include encryption certificates (start with “https://) and begin with the subdomains “apple.” or “icloud.” followed by a domain name starting with “com-“.
Here are just a few examples (the phishing links in this post have been hobbled with brackets to keep them from being clickable):
apple.com-support[.]id
apple.com-findlocation[.]id
apple.com-sign[.]in
apple.com-isupport[.]in
icloud.com-site-log[.]in
Savvy readers here no doubt already know this, but to find the true domain referenced in a link, look to the right of “http(s)://” until you encounter the first forward slash (/). The domain directly to the left of that first slash is the true destination; anything that precedes the second dot to the left of that first slash is a subdomain and should be ignored for the purposes of determining the true domain name.
For instance, in the case of the imaginary link below, example.com is the true destination, not apple.com:
https://www.apple.com.example.com/findmyphone/
Of course, any domain can be used as a redirect to any other domain. Case in point: Targets of the phishing domains above who are undecided on whether the link refers to a legitimate Apple site might seek to load the base domain into a Web browser (minus the customization in the remainder of the link after the first forward slash). To assuage such concerns, the phishers in this case will forward anyone visiting those base domains to Apple’s legitimate iCloud login page (icloud.com).
The best advice to sidestep phishing scams is to avoid clicking on links that arrive unbidden in emails, text messages and other mediums. Most phishing scams invoke a temporal element that warns of dire consequences should you fail to respond or act quickly. If you’re unsure whether the message is legitimate, take a deep breath and visit the site or service in question manually — ideally, using a browser bookmark so as to avoid potential typosquatting sites.




“Savvy readers here no doubt already know this, but to find the true domain referenced in a link, look to the right of “http(s)://” until you encounter the first backward slash (/). The domain directly to the left of that first slash is the true destination; anything that precedes the second dot to the left of that first slash is a subdomain and should be ignored for the purposes of determining the true domain name.”
Backward slash? – needs more coffee…
Doh. I’m always confusing the two. Fixed.
That’s ok, I had to take a few moments to stare menacingly at my keyboard while deciding if I had it wrong all these years!
Ii thought I was the only tech literate that constantly does that. Forward/backwards, who cares its a slash right? I mean its an arbitrary decision on what to call those.
/
The top of it is farther to the right, so that makes it forward slash, but in other languages left is forward, so its backwards. Or look at the bottom part instead, its farther to the left, so its backwards.
\
That’s just the inverse and invert all the previous arguments and they still make sense.
Why don’t we just call them positive/negative for the slopes they would have if graphed on a 2d Cartesian plane graph? That would be unambiguous.
… And don’t get me started on “b” vs. “d”!
Found the kid
In the context of what that paragraph was about, you would be correct
I say “left-leaning slash” and “right-leaning slash.”
(Or, if you’re American, “Democrat slash” and “Republican slash”.)
Having made that mistake when programming in assembly language on a keypunch machine, I resolved never to make that mistake again. Never a *back*slash, unless you know it. You’ll make a mistake far less often just using a slash.
How do I know which (/ or \) is which? Easy, the slash is on the part of the keyboard that was inherited from a typewriter, usually under the ? mark. The backslash is has to hang out with another outlier, the |.
It is easy to remember if you consider that the slash (/) has always been the ordinary character used in everyday life – outside and before the computer world. The backslash was invented for computer purposes. (It was introduced into ASCII in 1961).
… and a ‘normal’ slash (/) is more ‘natural’ in handwriting (if you are not left-handed). 😉
The simplest way to remember the slashes is to think about typing the following:
mix 1/2 cup of flour, and 1/4 table spoon of butter (divisor)
C:\windows\system32\drivers
I cannot type the back-slash without taking my fingers off of the home row of keys.
Learning something new, again! Using browser bookmarks as a ‘security feature’ for all my critical websites should be standard policy
And to really do this properly, there ought to be a tool built into the browser, or router even, that monitors the address field for manually typed addresses that appear to match my whitelist. Going further, it would also be nice to have an automatically updated list of known typosquatting sites added to a blacklist
That reminds me, don’t ask me how I know it’s always possible to accidentally type your password into the address bar and broadcast that out to entire world!
Hey Phil,
Bookmarks are actually pretty great for my parents or anyone who is not tech savvy. Since I use a password manager along with 2FA, it provides extra protection as Lastpass will only autofill on the actual website. Moreover, you can launch any website through your password manager to its actual login page, which makes you immune to phishing without requiring hardware U2F or WebAuthn hardware keys. Of course, the email would have been pretty suspicious, but you have to assume that you (as a person) can be tricked. This is what makes hardware keys or password manager’s autofill so good! It protects you from yourself.
To prevent phishing and robocalls, I think the next step should be STIR/SHAKEN for phone numbers (at least all US and Canadian numbers would be verified), and TLS encryption mandatory for email servers (Gmail now has a insecure red lock for any email that did not arrive encrypted in transit). Plus, websites should list all the emails they communicate from in either a standardized way (like we have robots.txt or the newer proposed security.txt, there should be something like email.txt which something like a password manager or website information page in Chrome or Firefox can reveal). Perhaps, it can even be part of the normal HTTPS certificate by adding an extension to it. This should reduce phishing drastically.
I’ve had bookmarks changed by malware in the past, but not lately. I use search a lot to find my target site, because I can type faster than I can find my bookmarks by manually opening folders and trying to find the bookmark.
A quick look at search results will identify the legit results from bad ones – especially if you use Web Of Trust. If a see a result that is gray instead of the green one I usually go to, then I know the result is wrong, or poisoned by the search engine. Poisoning like that is rare enough now that I rarely see it, but I do occasionally see a red WOT rating on what looked like a legitimate site address on first examination. One just has to be very careful in every step you take on the wild west of the web!!
Agreed!
Everyone has their own style and workflows. I too do not use bookmarks to browse websites (I do bookmark resources that I might need later, but that is bookmark’s whole purpose), and use the password manager autofill as one of the layer to protect from phishing when entering websites.
However, keep in mind that WOT sells user data, and they have been caught selling data that was not properly anonymized (https://www.bleepingcomputer.com/news/software/google-and-mozilla-remove-extension-that-was-caught-selling-user-data/)
Firefox also has the neat feature where if you type * in the address bar, it will only search bookmarks, if that suits your needs
McAfee Site Advisor used to be the best, but it got where it was only available on paid for products or shoehorned in with cr@pware in the past, so I haven’t tried of for a while. It was the only one more accurate than WOT – I’ve tried a lot of them, that is pretty much useless. It says it is free to download, but that doesn’t mean free to use – so one has to be careful.
It’s WebAdvisor now. Still free to use, as far as I know. Not to be confused with McAfee’s Security Scan Plus, which comes bundled with other software downloads if you’re not paying attention.
In theory using the quad nine DNS (9.9.9.9) will avoid malware domains. I say in theory because I don’t click on phishing links and test it out.
only to the extent the malware domain is on someone’s list…
I have received several showing receipts for Apple ID purchases that I haven’t made….they don’t appear as actual purchases made in my account….so a the link they are providing for me to view the transaction is a phishing attempt…I haven’t opened those links, but forwarded them directly to the Apple Phishing website address….only received an acknowledgement from them.
Not sure how they are getting my general info ….email linked to my Apple account….but suspect that Yahoo has been hacked again.
With as many customers as Apple has, the bad actors probably found your email address somewhere and guessed correctly that you are a customer.
Well, seeing as Yahoo was bought by Verizon, and that Verizon is still in the middle of a really messy hatchet job on killing off groups/deleting data, now might be the time for all kinds of weird backdoors to get opened up
I received several emails saying they were from Apple.
After talking to Apple on the phone, I learned Apple always addresses you by name in their emails.
So if the email does not have your name in it, it is a fake.
The best way I find to spot a phishing scam is to look at the header information with the sender IP number. However, this is much harder on a cell phone dependent of the email client.
Is anyone else surprised nothing has replaced laissez-faire email yet?
Tis 2020! Email is so diversely antiquated and widely abused in EVERY SINGLE organization or example you can think of, it’s like if the Greeks continually allowed a steady stream of wooden horse-shaped gifts to come through the castle gates ongoing.
“Yeah that last one was full of bad guys, but this one looks fine. It’s not like we can just stop accepting random tributes from strange empires…”
There has got to be a better way. We can’t just forever defer to legacy compatibility because “everyone is still using it, it’s the only way” – that’s almost a tautology. Am I crazy or is email crazy? Custom HTML and Javascript pushed from unknown senders and running on any number of buggy clients without serious sanity checks, all at the whim of a userland click?
“Don’t open that one, it’s actually marked Trojan. Oh, Steve accidentally glanced at it? Crap…”
#Business SOP
compounded by who we let have email these days…
The Greeks built the wooden horse to tempt the Trojans (people of Troy) to dismantle their city gate to let it in, which the Trojans did, to their short-lived chagrin.
I think this is pretty sneaky as long words in newspaper breaks up with hyphens.
so for example this can be a very long wordhhhshshsh-awebfawbefibafe
Thought i could replicate it in web but failed horribly.
TIL that unbidden is a real word!
And this posting does not mention, nor, perhaps, should it, the dozens of phone calls from Apple, often with their legitimate phone number as part of thr caller ID, I have received over the past several month but never answered. BTW As a first time commenter, I am little confused when tapping the numbers key brings up a half screen with the letters F and T on it neither of which brings up the numbers keyboard on my iPad. Perhaps a few words of explanation at the beginning of the comments section?
Bobem, you might have been the target of one of these calls:
https://krebsonsecurity.com/2019/01/apple-phone-phishing-scams-getting-better/
I think the ‘F & T’ thing you are seeing is Apple Key Flicks.
https://www.imore.com/how-use-keyboard-flick-ipads-quicktype-keyboard-ios-11
I commonly see it when spinning up a new iPad or after a major iOS upgrade. You see it once as a notification and then it goes away.
Apple (and Google) need to put more visibility into what domain the email came from. (Root domian). Right now you just see Apple Support or John Smith. It needs to say “Apple Support (example.ru)”. It might help people spot fakes!
Great idea!
Great article as usual, Brian. Also great to see the FortiGate doing it’s job with your examples (using the lynx browser for safety):
lynx apple.com-support[.]id
Fortinet Secure DNS Service Portal Web Page Blocked!
You have tried to access a web page which belongs to a category that is blocked.