As an early domain name investor, Mike O’Connor had by 1994 snatched up several choice online destinations, including bar.com, cafes.com, grill.com, place.com, pub.com and television.com. Some he sold over the years, but for the past 26 years O’Connor refused to auction perhaps the most sensitive domain in his stable — corp.com. It is sensitive because years of testing shows whoever wields it would have access to an unending stream of passwords, email and other proprietary data belonging to hundreds of thousands of systems at major companies around the globe.

Now, facing 70 and seeking to simplify his estate, O’Connor is finally selling corp.com. The asking price — $1.7 million — is hardly outlandish for a 4-letter domain with such strong commercial appeal. O’Connor said he hopes Microsoft Corp. will buy it, but fears they won’t and instead it will get snatched up by someone working with organized cybercriminals or state-funded hacking groups bent on undermining the interests of Western corporations.
One reason O’Connor hopes Microsoft will buy it is that by virtue of the unique way Windows handles resolving domain names on a local network, virtually all of the computers trying to share sensitive data with corp.com are somewhat confused Windows PCs. More importantly, early versions of Windows actually encouraged the adoption of insecure settings that made it more likely Windows computers might try to share sensitive data with corp.com.
At issue is a problem known as “namespace collision,” a situation where domain names intended to be used exclusively on an internal company network end up overlapping with domains that can resolve normally on the open Internet.
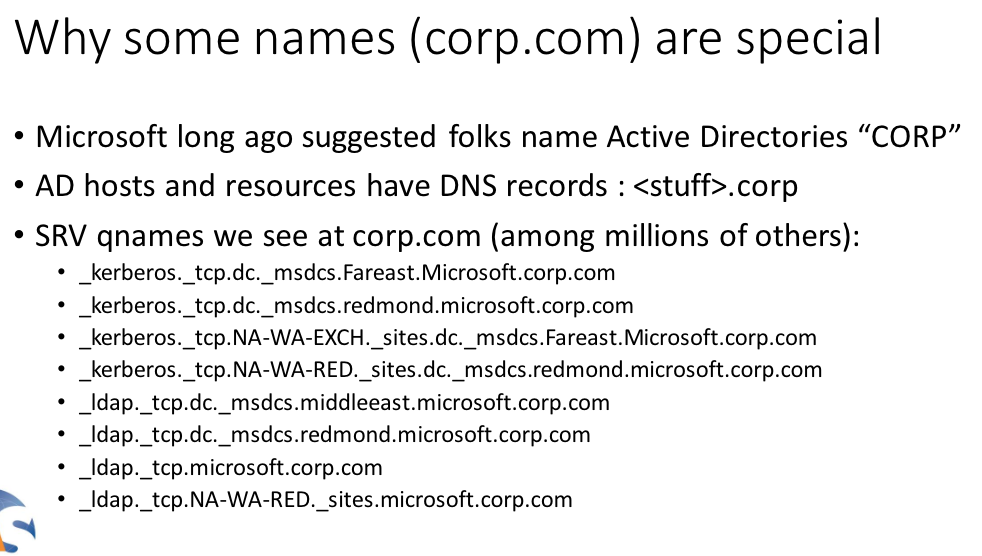
Windows computers on an internal corporate network validate other things on that network using a Microsoft innovation called Active Directory, which is the umbrella term for a broad range of identity-related services in Windows environments. A core part of the way these things find each other involves a Windows feature called “DNS name devolution,” which is a kind of network shorthand that makes it easier to find other computers or servers without having to specify a full, legitimate domain name for those resources.
For instance, if a company runs an internal network with the name internalnetwork.example.com, and an employee on that network wishes to access a shared drive called “drive1,” there’s no need to type “drive1.internalnetwork.example.com” into Windows Explorer; typing “\\drive1\” alone will suffice, and Windows takes care of the rest.
But things can get far trickier with an internal Windows domain that does not map back to a second-level domain the organization actually owns and controls. And unfortunately, in early versions of Windows that supported Active Directory — Windows 2000 Server, for example — the default or example Active Directory path was given as “corp,” and many companies apparently adopted this setting without modifying it to include a domain they controlled.
Compounding things further, some companies then went on to build (and/or assimilate) vast networks of networks on top of this erroneous setting.
Now, none of this was much of a security concern back in the day when it was impractical for employees to lug their bulky desktop computers and monitors outside of the corporate network. But what happens when an employee working at a company with an Active Directory network path called “corp” takes a company laptop to the local Starbucks?
Chances are good that at least some resources on the employee’s laptop will still try to access that internal “corp” domain. And because of the way DNS name devolution works on Windows, that company laptop online via the Starbucks wireless connection is likely to then seek those same resources at “corp.com.”
In practical terms, this means that whoever controls corp.com can passively intercept private communications from hundreds of thousands of computers that end up being taken outside of a corporate environment which uses this “corp” designation for its Active Directory domain.
INSTANT CORPORATE BOTNET, ANYONE?
That’s according to Jeff Schmidt, a security expert who conducted a lengthy study on DNS namespace collisions funded in part by grants from the U.S. Department of Homeland Security. As part of that analysis, Schmidt convinced O’Connor to hold off selling corp.com so he and others could better understand and document the volume and types of traffic flowing to it each day.
During an eight month analysis of wayward internal corporate traffic destined for corp.com in 2019, Schmidt found more than 375,000 Windows PCs were trying to send this domain information it had no business receiving — including attempts to log in to internal corporate networks and access specific file shares on those networks.
For a brief period during that testing, Schmidt’s company JAS Global Advisors accepted connections at corp.com that mimicked the way local Windows networks handle logins and file-sharing attempts.
“It was terrifying,” Schmidt said. “We discontinued the experiment after 15 minutes and destroyed the data. A well-known offensive tester that consulted with JAS on this remarked that during the experiment it was ‘raining credentials’ and that he’d never seen anything like it.”
Likewise, JAS temporarily configured corp.com to accept incoming email.
“After about an hour we received in excess of 12 million emails and discontinued the experiment,” Schmidt said. “While the vast majority of the emails were of an automated nature, we found some of the emails to be sensitive and thus destroyed the entire corpus without further analysis.”
Schmidt said he and others concluded that whoever ends up controlling corp.com could have an instant botnet of well-connected enterprise machines.
“Hundreds of thousands of machines directly exploitable and countless more exploitable via lateral movement once in the enterprise,” he said. “Want an instant foothold into about 30 of the world’s largest companies according to the Forbes Global 2000? Control corp.com.”
THE EARLY ADVENTURES OF CORP.COM
Schmidt’s findings closely mirror what O’Connor discovered in the few years corp.com was live on the Internet after he initially registered it back in 1994. O’Connor said early versions of a now-defunct Web site building tool called Microsoft FrontPage suggested corporation.com (another domain registered early on by O’Connor) as an example domain in its setup wizard.
That experience, portions of which are still indexed by the indispensable Internet Archive, saw O’Connor briefly redirecting queries for the domain to the Web site of a local adult sex toy shop as a joke. He soon got angry emails from confused people who’d also CC’d Microsoft co-founder Bill Gates.
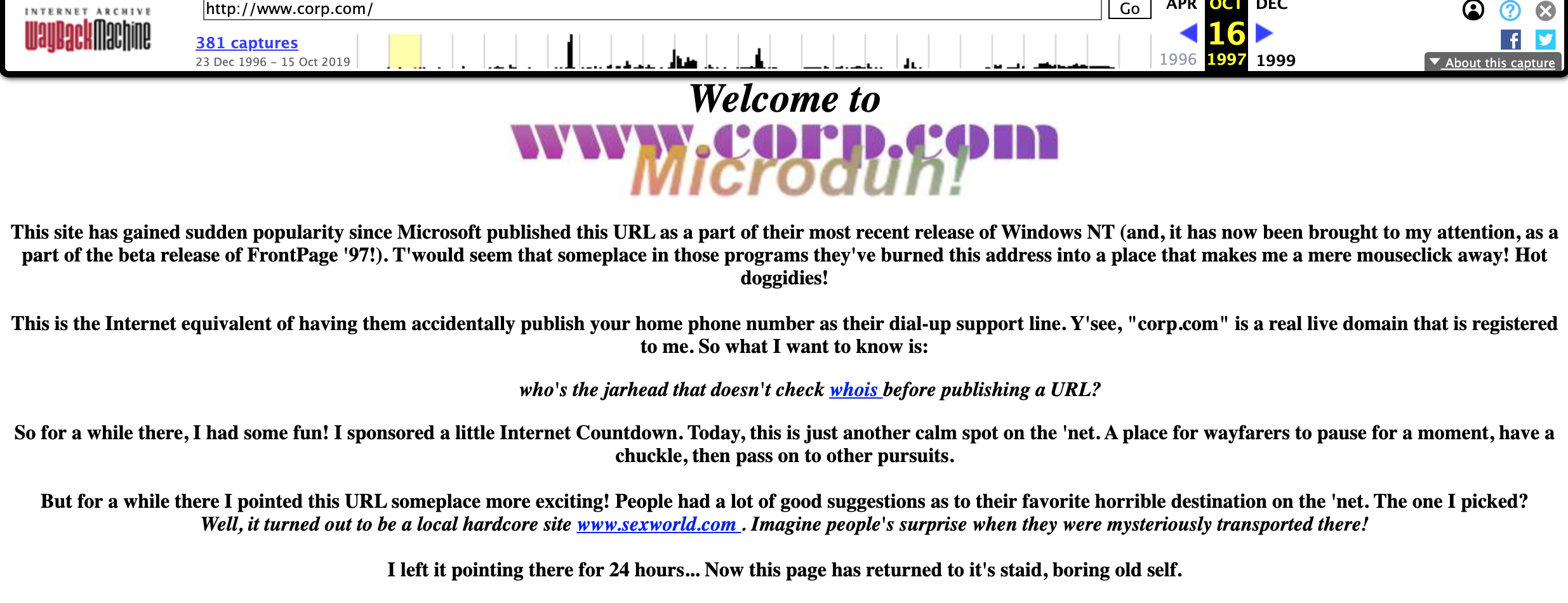
Archive.org’s index of corp.com from 1997, when its owner Mike O’Connor briefly enabled a Web site mainly to shame Microsoft for the default settings of its software.
O’Connor said he also briefly enabled an email server on corp.com, mainly out of morbid curiosity to see what would happen next.
“Right away I started getting sensitive emails, including pre-releases of corporate financial filings with The U.S. Securities and Exchange Commission, human resources reports and all kinds of scary things,” O’Connor recalled in an interview with KrebsOnSecurity. “For a while, I would try to correspond back to corporations that were making these mistakes, but most of them didn’t know what to do with that. So I finally just turned it off.”
TOXIC WASTE CLEANUP IS HARD
Microsoft declined to answer specific questions in response to Schmidt’s findings on the wayward corp.com traffic. But a spokesperson for the company shared a written statement acknowledging that “we sometimes reference ‘corp’ as a label in our naming documentation.”
“We recommend customers own second level domains to prevent being routed to the internet,” the statement reads, linking to this Microsoft Technet article on best practices for setting up domains in Active Directory.
Over the years, Microsoft has shipped several software updates to help decrease the likelihood of namespace collisions that could create a security problem for companies that still rely on Active Directory domains that do not map to a domain they control.
But both O’Connor and Schmidt say hardly any vulnerable organizations have deployed these fixes for two reasons. First, doing so requires the organization to take down its entire Active Directory network simultaneously for some period of time. Second, according to Microsoft applying the patch(es) will likely break or at least slow down a number of applications that the affected organization relies upon for day-to-day operations.
Faced with either or both of these scenarios, most affected companies probably decided the actual risk of not applying these updates was comparatively low, O’Connor said.
“The problem is that when you read the instructions for doing the repair, you realize that what they’re saying is, ‘Okay Megacorp, in order to apply this patch and for everything to work right, you have to take down all of your Active Directory services network-wide, and when you bring them back up after you applied the patch, a lot of your servers may not work properly’,” O’Connor said.
Curiously, Schmidt shared slides from a report submitted to a working group on namespace collisions suggesting that at least some of the queries corp.com received while he was monitoring it may have come from Microsoft’s own internal networks.
“The reason I believe this is Microsoft’s issue to solve is that someone that followed Microsoft’s recommendations when establishing an active directory several years back now has a problem,” Schmidt said.
“Even if all patches are applied and updated to Windows 10,” he continued. “And the problem will persist while there are active directories named ‘corp’ – which is forever. More practically, if corp.com falls into bad hands, the impact will be on Microsoft enterprise clients – and at large scale – paying, Microsoft clients they should protect.”
O’Connor said Microsoft actually offered to buy the domain several years back for $20,000. He turned them down, saying that at the time he thought it was too low and didn’t reflect the market value of the domain.
Asked why he didn’t just give corp.com to Microsoft as an altruistic gesture, O’Connor said he believes the software giant ought to be accountable for its products and mistakes.
“It seems to me that Microsoft should stand up and shoulder the burden of the mistake they made,” he said. “But they’ve shown no real interest in doing that, and so I’ve shown no interest in giving it to them. I don’t really need the money. I’m basically auctioning off a chemical waste dump because I don’t want to pass it on to my kids and burden them with it. My frustration here is the good guys don’t care and the bad guys probably don’t know about it. But I expect the bad guys would like it.”
Further reading:
Mitigating the Risk of DNS Namespace Collisions (PDF)
DEFCON 21 – DNS May Be Hazardous to your Health (Robert Stucke)
Mitigating the Risk of Name Collision-Based Man-in-the-Middle Attacks (PDF)
Update, 6:22 p.m. ET: Added the bit at the end about the $20,000 offer a few years back from Microsoft, a detail that I somehow omitted from the original story.




If I worked for NSA I would be contacting him in a heartbeat. What a way scoop up a lot of stuff for a small price!
The issue does affect national security, so maybe they should buy it.
let’s give the NSA yet another backdoor lol
Why buy when you can seize?
Why seize when you can sniff
I am confused. JAS Global Advisors was able to receive “corp” data, and then backed away. What is to stop anyone at all from doing the same thing, right now? That is, what is special about JAS Global Advisors?
The domain doesn’t belong to JAS. It belongs to a private person who agreed to let them use it for a time to help with research on namespace collisions. The owner can do with it as he wishes.
The FTC and FBI should acquire it covertly, seemingly a top-level investor who is taking it for a non-TOR but very private platform and then running that domain as a honeypot for miscreant identification and lots of ongoing intel…
Why the FTC and FBI which are US based? The possible data exposure would be worldwide, not just US.
The domain name “corp(.).com” should be given back to the register (godaddy) and permanently locked for resale to avoid these types of collisions
While true, that doesn’t capture its value to O’Connor. This seems like a security-alliance sort of thing where a group of companies should help write a check to capture the true value and then lock it.
Since Microsoft was the party causing most of this issue (using “CORP” without already owning corp.com as a backup”), I feel they should have to write the check. After that, I do agree that Microsoft should not own it (since they could use it for the same espionage purposes), but instead it should be locked.
DNS names are not property to be squatted or auctioned.
AFAIU O’Connor never had any legitimate business with corp.com, other than being the first to snatch a bunch of lucrative domains. IMO O’Connor has no legitimate claim of “value”. Being the first to snatch a domain is not something that should be considered a claim on riches.
OTOH, someone did FUP, making a domain registered to O’Conner unsuable, so IMO he should be reimbursed for his troubles/expenses.
Yes, you can buy a domain and not use it for anything (or to resell it later to those who might want it). Squatting is considered when you buy “cocacola.com” and other trademarked names. “corp.com” is not a trademarked or copyrighted name, and it doesn’t belong to an established company.
You simply sound jealous that you didn’t think of it first.
GoDaddy is just a domain reseller, it would be ICANN who could (and should) lock it permanently.
That aside, there’s no need for him to fear that a criminal organization buys it. He’s the seller so he can choose to sell it to a responsible and trustworthy organization.
Maybe. It’s being sold through a third-party service, and it’s not clear to what extent the seller would be able to properly vet the buyer through that channel. Assuming for argument’s sake that it’s an individual: How would he go about determining whether that individual was just a domain investor vs. an altruistic netizen vs. someone or a company fronting for a nation state?
That’s a novel way to call a “domain squatter”, Brian, a “domain investor” 🙂
Eh. Tomato-tomahto. When I consider what I spent on a 12-pack of beer in my senior year of college + a single phonecall to Jon Postel back then could have netted me today, I’m ashamed that I enjoyed beer so much then. Strangely enough, the only person in my dorm who had a computer in their room at the time owned an old Macintosh. Instead of buying domains on it, I played a lot of games like Chopper and Maelstrom.
Beer and fun sounds a lot more productive than domain speculation.
If ICANN is serious about its stated purpose to maintain a stable and secure DNS, they should make Mikey an offer. They can certainly afford it.
I was cleaning out the garage when I uncovered my late stepdad’s Power Mac 6100. Booted up and there on the desktop was Maelstrom.
Next thing I knew, I had been playing for several hours. I did improve my high score from 1998 though…
I truly adored that game. The best part was the sound effects for executing certain moves. Kept me playing for hours. Brilliant game. Glad I wasn’t the only one hooked on it.
For gaming on a Mac it would have to be Bolo. Had that loaded up on all the school Mac’s all through the 90’s
Anyone remember Crystal Quest? I had it on my Mac Classic running 6.8.1. It had a very unique sound when moving from one level to the next.
The problem is you can’t trust icann to never sell it. In the early days, for example, they refused to sell single letter names, then they did. And they refused to sell “obscene” names, and then they did, somewhat cheating the people who first tried to buy them and were turned away.
This is completely mind blowing and enormous to conceptualize and when invisioned. Most people will not understand the scope of this potential exploit. Understanding the technology and DNS makes this scenario one of the most frightening events I could imagine.
Microsoft and so many other corps could buy this and end the threat with the profits earned in 5 minutes. That they don’t, and would see it go to cybercrime, is so, so sad.
15 min? Try 15 sec. And it’s the right and noble thing to
do.
“…My frustration here is the good guys don’t care and the bad guys probably don’t know about it. But I expect the bad guys would like it.”
Well they know about it now!!
This story reeks of virtue signaling. The guy clearly was miffed that Microsoft only offered him a ‘measly’ $20,000 for his gold mine, so he’s parading around advertising how good of a job he’s done protecting this domain for so many years… but soon he’s going to sell it because he doesn’t want to burden his children with this unbearable weight.
Give me a break. If this guy truly cared about doing the right thing, this story wouldn’t exist – and that domain would be off the market forever.
Seems similar to how MS references the fictional company “Contoso” and contoso.com in much of their IT documentation. At least in that situation MS actually owns the domain.
What a mess! 🙁
Just a side note for those working for brands. There’s always going to be some email leakage if you don’t have the best version of your brand .Com name.
Also, add other examples.
com.com – tons of traffic and emails
Others?
CNet actually owned com.com for a long time: It wanted “news.com” but that domain was unavailable, so it bought “com.com” and launched as “news.com.com”; eventually it got news.com and some time after CBS Interactive bought the site, it let com.com lapse.
I vaguely remember there was a guy who owned “localhost.net” who got all kinds of weird traffic, too.
If this man has created wealth through the very smart buying, holding and eventual reselling of unique domain names, then why not create either a trust fund for his grown children or a charitable foundation of some sort, either one of which could hold ownership of the corp dot com domain name in perpetuity?
If he just wants money, then I think he should be upfront about this and not pretend that he wants to do something good for humanity by getting this corp dot com domain name into the right hands. He could also possibly (not sure how this works) donate the corp dot com domain ownership to some Federal government agency like the NSA.
I worked with Mike previously within the context of the domain industry. He’s the most honest person I’ve ever met within it. Microsoft should have acquired this a long time ago. This is known information regarding the datastream that comes along with that url.
Mike’s been safeguarding the internets Infinity Gauntlet and he could have spent the last 25 years leveraging that power, by at minimum monetizing it. He really hasn’t. Anyone who’s calling into question his character or morals, is just 100% wrong. Also disparaging someone who wisely invested early on in virtual real-estate with .com domains, should also crap on anyone who got involved with bitcoin early on.
It’s the most absurd accusation ever, domain squatter. It’s the same thing as buying commercial real-estate. For every category killing domain, there’s been at least 50 butt-hurt “entrepreneurs” disappointed to find out that the perfect domain for their idea also happens to have significant intrinsic value because of its proximity to consumers with intent.
What if real estate speculation is also unethical? It contributes nothing to society, after all, and meanwhile it locks poor people – the ones who need it the most – out of affordable housing. Obviously humans don’t need a domain name to survive, but businesses often do, and in either case it can only ever give an advantage to the already well-established.
Viko,
I get what you’re saying, but the genie is out of the bottle. You can’t punish people who have worked hard and want to put the money they obtained, to work in real estate. Unless aliens come down from space and force us to change how the world works, and in effect mandate that humans only consumer the required necessary resources then this isn’t really worth considering. Because if humans were to initiate that change, war would be required. Millions would have to lose their lives.
Regarding domains, there’s even less of an argument there. Someone with an idea for a business or even an actual business who would like to use a domain that is owned by someone else, they don’t actually need that domain. Like they need per your example, housing.
Fortunes have been made and lost speculating on domains. Mostly it’s the latter. People shouldn’t vilify those who have taken on the risk of domain speculation.
Aloha Mr. Krebs,
The history of DNS registration would make an interesting but wonkish expose’. I jumped online from home in Seattle in late 1993. If I recall correctly it was three “intel” functionaries that were in the right place at the right time and created Internic. I remember when people would shakedown big corporations like Sears, and Grainger over ownership of trade names. I found it to be a very unscrupulous sneaky unethical practice. I believed those trade name protections should have been the purview of the Library of Congress. But just as 90% of folks that drive cars have no idea what transpires under the hood, similarly there is great ignorance regarding computers. The registration process kind of took on a life of its own sans regulations.
If Brian Krebs controlled this domain, would he read the correspondence or give it to Microsoft?
That defcon vid on DNS is pretty good!
I have a question. Is this arp cache scam and DNS scam – only good or HTTP only sites?
Would the domain controller using a certificate be protected by HTTPS? That is a 2003 Server SP2 to 2008R2 patched MS domain controller with certificate and client be protected [assuming the certificate was modern]?
I did a quick certificate test on corp[.]com and it did not certificate. Anybody know?
So talking about mitigatioms, if an organization wants to protect themselves, would putting a sinkhole of
127.0.0.1 corp.com
in the windows hosts file would they be safe from this?
@Josh, That would not help when an employee is off-site (e.g., Starbucks).
It would need to be *.corp.com, which hosts file don’t translate to everything that ends with corp.com. But an organisation DNS resolver could punt that domain to an internal authority that would always respond with 127.0.53.53.
Geico’s internal AD domain is geico.corp.net and they don’t own corp.net.
To their own perfil. Read JAS documents to know why.
There are about 429,000 domains with “corp” in them.
https://dotdb.com/search?keyword=corp&position=any&exclude=
How many are actively used by companies… hard to say. Judging from this article a lot.
I just migrated a domain of 250 users to a new domain and it took 3 guys 2-3 months to get all AD users Migrated. Our new parent company acquires a lot of companies so they have IT dedicated to the task. The process is as follows.
1. Create new domain
2. Create domain trust between domains. Configure DNS.
3. Run script that migrates SID of old user to new user.
4. There is a tool that you can buy that will domain join the computer and migrate the profile. You can also do it remotely over VPN.
I’m not saying it will be easy for a large company. I’m saying it can be done.
It is very necessary for the domain registrar to lock this domain name crop.com to avoid problem in the future.
I hope CROP.com isn’t as bad as CORP.com. Because CROP.com is not owned by Mike. Anyone in the domain biz knows who owns that one.
One of these will buy it.
Spy agency of; US, China, Russia, Israel.
Or a haxor that will rig the bidding system and get it for $10.
Maybe we need a Kickstarter on behalf of the “cybersecurity” community to buy this and put it somewhere out of reach of criminals. corp.com or http://www.corp.com could resolve to a web server with a single page, showing the names of all donors (maybe pledge more for larger font size).
$20k is not sufficient compared to what some companies pay out for a bug bounty these days. I hear that some bug bounties for large corps pay in the hundreds of thousands of dollars. I am just trying to put this in relative terms.
Is cyber squatting on a domain name a crime? When I was in school in the 90’s, they compared domain names to real estate. This guy is an early investor. What is wrong with that? Then I guess there is imminent domain too.
Most people don’t have a basic idea of how the internet works. 🙂
So what is the real fix for this from an administrative side of things? All the links used refer to information from years ago.
I believe this is the correct approach:
https://krebsonsecurity.com/2020/02/dangerous-domain-corp-com-goes-up-for-sale/comment-page-1/#comment-504414
n.b. I haven’t done it myself and I don’t think you could pay me enough to do it.
I hope someone other that MSFT buys it and they finally fix DNS name devolution. It is literally useless.
Looking at this from the viewpoint of an old timer AD admin:
Corp . NameofDomainIOwn . com
SubdomainNameIMadeUp . corp . com
In the first example, you should be safe. In the second example, if someone you don’t trust gets corp dot com, your entire AD structure is at risk for external connected AD devices. And pity anyone that runs an Exchange server on that namespace.
What I am unclear on, is if the NETBIOS name is corp (but the actual domain is not) what might be implications on older systems that did not always use the FQDM?
I don’t understand why the laptop at Starbucks in this example defaults to com. It takes both the domain name and the TLD to resolve anything with DNS. In this case. the domain name, “corp”, is used in AD, but not with any TLD.
Generic top-level domains at the time AD was created consisted of gov, edu, com, mil, org, and net. There has never been a default gTLD. In this case, why is com used as a default TLD?
Are other gTLDs a risk, like corp.net?
vb said: “I don’t understand why the laptop at Starbucks in this example defaults to com. It takes both the domain name and the TLD to resolve anything with DNS. In this case. the domain name, “corp”, is used in AD, but not with any TLD.”
Because if your device can’t resolve a server, it appends “.com” and tries again. This is a practice from the late 1990s, when almost every site was “www.some-site.com”.
Maybe the best solution is for Microsoft to agree to donate the money to a charity agreed upon by Microsoft and the “domain investor”.
I’m not really a fan of people scooping up domains. It falls close to people who try to capitalize during emergencies and resell food/water at significant markups.
I do think Microsoft needs to pay for their stupidity (which sadly has gone on for too many years). And some companies are also culpable since they don’t want to spend the time/money to fix things properly. Kind of like people who refuse to get off of XP or Windows 7.
The real fuckup is that now that this unbelievable negligence of microsoft is so publicly known, any rogue DNS provider can spit out IPs for corp.com and collect the data from people trusting them, e.g. from all those networks using this miscreated software / instructions in their networks.
There might be countries or providers interested in doing such a thing to get a foothold at many places in just one such rush.
This clearly is a case of severely lacking due diligence.
Brian – I really enjoyed this article, his comment at the end made me chuckle out loud:
“I don’t really need the money. I’m basically auctioning off a chemical waste dump because I don’t want to pass it on to my kids and burden them with it.”
I’m sure his kids appreciate that too and $1.7 million would be a much nicer inheritance! 🙂