Finastra, a company that provides a range of technology solutions to banks worldwide, said today it was shutting down key systems in response to a security breach discovered this morning. The company’s public statement and notice to customers does not mention the cause of the outage, but their response so far is straight out of the playbook for dealing with ransomware attacks.
 London-based Finastra has offices in 42 countries and reported more than $2 billion in revenues last year. The company employs more than 10,000 people and has over 9,000 customers across 130 countries — including nearly all of the top 50 banks globally.
London-based Finastra has offices in 42 countries and reported more than $2 billion in revenues last year. The company employs more than 10,000 people and has over 9,000 customers across 130 countries — including nearly all of the top 50 banks globally.
Earlier today, sources at two different U.S. financial institutions forwarded a notice they received from Finastra saying the outage was expected to disrupt certain services, particularly for clients in North America.
“We wish to inform our valued customers that we are investigating a potential security breach. At 3:00 a.m. EST on March 20, 2020, we were alerted to anomalous activity on our network which risked the integrity of our data-centers,” reads the notice. “As such, and to protect our customers, we have taken quick and strict remedial action to contain and isolate the incident, while we investigate further.”
Update, 5:21 p.m. ET: Finastra has acknowledged that it is battling ransomware.
“At this time, we strongly believe that the incident was the result of a ransomware attack and do not have any evidence that customer or employee data was accessed or exfiltrated, nor do we believe our clients’ networks were impacted,” the company said in a revised statement.
The statement continues:
“Our approach has been to temporarily disconnect from the internet the affected servers, both in the USA and elsewhere, while we work closely with our cybersecurity experts to inspect and ensure the integrity of each server in turn. Using this ‘isolation, investigation and containment’ approach will allow us to bring the servers back online as quickly as possible, with minimum disruption to service, however we are anticipating some disruption to certain services, particularly in North America, whilst we undertake this task. Our priority is ensuring the integrity of the servers before we bring them back online and protecting our customers and their data at this time.”
Finastra also acknowledged an incident via a notice on its Web site that offers somewhat less information and refers to the incident merely as the detection of anomalous activity.
“The Finastra risk and security services team has detected anomalous activity on our systems,” wrote Tom Kilroy, Finastra’s chief operating officer. “In order to safeguard our customers and employees, we have made the decision to take a number of our servers offline while we investigate. This, of course, has an impact on some of our customers and we are in touch directly with those who may be affected.”
Once considered by many to be isolated extortion attacks, ransomware infestations have become de facto data breaches for victim companies. That’s because some of the more active ransomware gangs have taken to downloading reams of data from targets before launching the ransomware inside their systems. Some or all of this data is then published on victim-shaming sites set up by the ransomware gangs as a way to strongarm victim companies into paying up.
One reader on Twitter told KrebsOnSecurity they’d heard Finastra had sent thousands of employees home today as a result of the security breach. Finastra told this author the company closed select offices in Canada and Paddington, London today where employees were unable to access the servers which they took offline.
“The majority of the Company’s employees are already working from home,” a statement shared by Finastra reads. “This is determined by Finastra’s response to COVID-19 and not related in any way to this incident.”
Interestingly, several ransomware gangs have apparently stated that they are observing a kind of moratorium on attacking hospitals and other healthcare centers while the COVID-19/Coronavirus epidemic rages on. Bleeping Computer’s Lawrence Abrams said he recently reached out to the operators of the Maze, DoppelPaymer, Ryuk, Sodinokibi/REvil, PwndLocker, and Ako Ransomware infections to ask if they would continue targeting health and medical organizations during the outbreak.
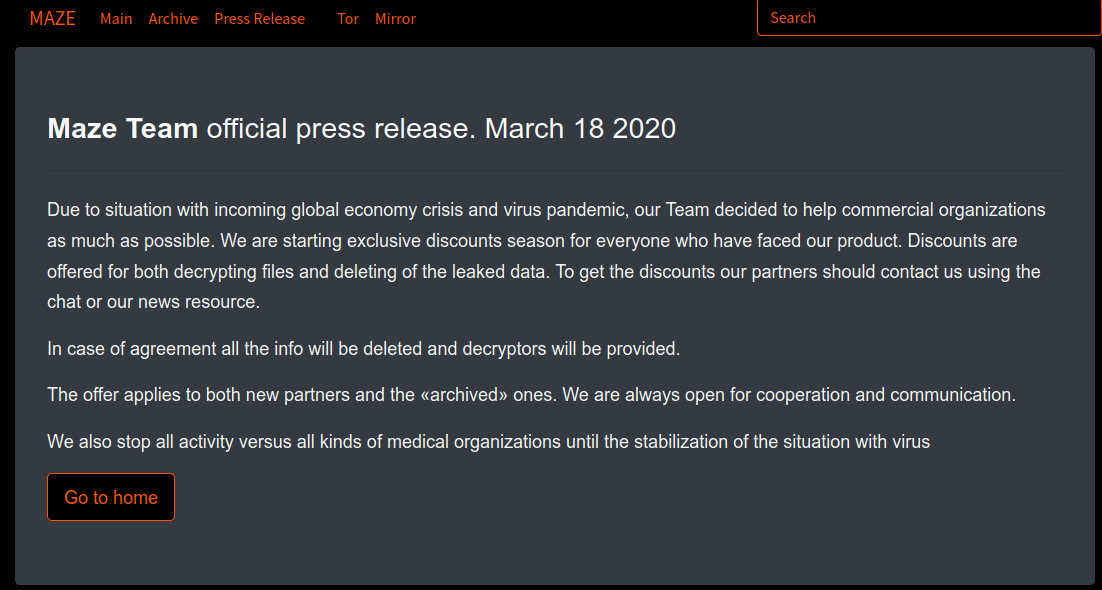
Abrams said several of those gangs told him they would indeed stop attacking healthcare providers for the time being. One gang even used its victim-shaming Web site to post a “press release” on Mar. 18 stated that “due to situation with incoming global economy crisis and virus pandemic” it would be offering discounts to victims of their ransomware.
“We also stop all activity versus all kinds of medical organizations until the stabilization of the situation with virus,” reads the release from the Maze ransomware gang.
This story will be updated as more details become available.




LOL Discounts to victims of ransomeware.
I about fell on the floor when I saw the offer of ransomeware discounts. What will these guys think of next? 🙂 If you cannot trust a ransomware operator, who can you trust?! Of course I am just kidding.
I don’t thing the gangs are doing this out of the goodness of their heart, or even as a practical reaction to the Corona problem; I think they know if they keep up operations like they were, that the world wide outrage would spill over onto them like an avalanche, and they could end up the target of a drone if they don’t watch it!!!
Scumbags!! >:-(
YES!
Hello Femtobeam! Long time no see!
A little birdie on my shoulder told me that a drone attack inside of Mother Russia is highly unlikely.
Shame organized crime outside of Russia doesn’t see the opportunities. Since the Russian gangs don’t hit up companies inside for fear of repercussions, there are green pastures there waiting to be raked from the outside.
Such honor among thieves
Perhaps when their babushkas become ill or die fro Covid-19 they will begin to give rebates?
Discounts… seriously(?)
> “…One gang even used its victim-shaming Web site to post a “press release” on Mar. 18 stated that “due to situation with incoming global economy crisis and virus pandemic” it would be offering discounts to victims of their ransomware…”
…lol…”…give half your money or you die…”
Trojan at their mail servier IP address since at least September 2019:
52.51.237.24
Do you have any additional information regarding that claim? Thanks.
Actually, I used the wrong iP, numerous for the mail exchangers:
IPs of one mail exchanger:
https://bgp.he.net/dns/us-smtp-inbound-1.mimecast.com#_ipinfo
IPs of another mail exchanger:
https://bgp.he.net/dns/us-smtp-inbound-2.mimecast.com#_ipinfo
Both mail exchangers are sharing the same IPs. All seem to have the same trojan-worm communicating with them.
Quickly looking at one of those IPs, trojan-worm is detected at one of those IPs used. I only looked at one.
finastra.com
Mail exchangers:
us-smtp-inbound-1.mimecast.com
us-smtp-inbound-2.mimecast.com
Trojan-backdoor communicating with the IP address:
http://www.virustotal.com/gui/file/58080104eebe1b56b575cf7e60e7b0075b309f38c346e03597dffd36a72a86aa/relations
http://www.virustotal.com/gui/file/58080104eebe1b56b575cf7e60e7b0075b309f38c346e03597dffd36a72a86aa/relations
http://www.virustotal.com/gui/file/bb8a1f161663ebbc016fc4914b44b0299ce9e8523d21bc1638c201b9c6f3dc68/relations
http://www.virustotal.com/gui/file/bb8a1f161663ebbc016fc4914b44b0299ce9e8523d21bc1638c201b9c6f3dc68/relations
http://www.virustotal.com/gui/file/fcdce83b2765ce7cc88ccfc9b7d637d8ebab58ccb0ba27ef001e782e9f4002a5/relations
http://www.virustotal.com/gui/file/fcdce83b2765ce7cc88ccfc9b7d637d8ebab58ccb0ba27ef001e782e9f4002a5/relations
http://www.virustotal.com/gui/file/a7eb058234caa0a000fd3e175ac0d2451842e64c45ce358208bb5918c3c6dac0/relations
http://www.virustotal.com/gui/file/a7eb058234caa0a000fd3e175ac0d2451842e64c45ce358208bb5918c3c6dac0/relations
I’d be really surprised if mimecast mail servers were involved with malware
Or, consolidated: at:
http://www.virustotal.com/gui/ip-address/52.51.237.24/relations
>
“Communicating files”
@acorn
I looked at the consolidated report at Virustotal. It is not saying a trojan-worm is detected at that IP address. It says there are 9 different malware files attempting to connect to that IP address. That is all the more it can prove.
That address is not used exclusively by Finastra. It is an inbound mail address for the third-party email service Mimecast. It has many corporate customers which will be associated with that address.
The question though is why are those maleware files (identified as a Windows 32bit executable) trying (may not be succeeding) to connect to that address? The answer could be as simple as they were all built by the same maleware toolkit which has a typo in one of the IP addresses it uses for some purpose.
At the top of the Virustotal consolidated report it identifies the address as being part of Amazon’s autonomous system AS16509. Seeing as Amazon operates cloud hosting services (of which Mimecast must be a customer), then there is a distinct possibility that a maleware toolkit is leveraging Amazon hosting as part of the maleware design.
That still leaves a lot of questions to be answered. I have only speculated on a few, I may be wrong. But, the Virustotal consolidated report linked does not implicate that IP address as a malware host.
@G.Scott H.
Correct, “attempts” to some extent. Potentially, successful travel beyond the Mimecast IP.
“Many corporate customers”.
I’m aware of email services using shared IPs, but have very little familiarity of Mimecast. My guess is no matter which is sharing the IP address, with certain malware one of those customers has malware traveling past the email IP. I will mention that another recent Krebs article perhaps a few weeks ago about ransomware also used Mimecast service, with Virustotal listings for emotet-ransomware.
An example of one Mimecast-email IP listed specifically as used–don’t know to what extent it is shared–with malware attempting to connect to some extent is:
http://www.virustotal.com/gui/ip-address/205.139.110.102/relations
All the other numerous shared IPs of the shared-mail urls, in my quick lookup, have similar trojan-worm detection.
I don’t know; but suspect there is a virustotal threshold of how many malware “communications files” are listed in history–like the log filled up and dropped the older, but still current listings. There may have been a say emotet-ransomware that attempted connection not too far back in history and doesn’t show because of the over-threshold number of retained-displayed virustotal listings, speculation.
Also, communicating with the IP address, March 20:
trojan-Ulise/Kryptik/Tofsee
http://www.virustotal.com/gui/file/aa9d452cfb5b8ba489c5a2c13ee8d23cbb533317cee0cf6cf89741f17108f779/detection
I didn’t take the time to go through the large amount of other attempted communications to the Mimecast IP, specifically shown to be used by Finastra, to see what other malware may be communicating.
This makes the third Krebs’ article on ransomware since December 7, that the customer used Mimecast.
This doesn’t necessarily implicate Mimecast.
Mimecast has a huge number of customers, so it is not unusual that 3 ransomware victims would be using Mimecast for email, anymore that if they were using Gmail, or Office365
It’s like saying 3 victims since Dec 9 use Google. It may not be related to the attacks. Correlation is not necessarily causation,
Anything connected to the internet backbone, is going to be vulnerable to some type of attack eventually
Hi Brian,
Great article, again.
Hey, as a side note, could you maybe do a 2020 updated article (like you’ve done in the past) extolling people–aimed at end consumers—to take advantage of any and/or all security measures wheverever/whenever they go online? Especially 2FA if is offered??
I’ve been gobsmacked recently, talking to what I had presumed were knowledgeable people, and finding out that they are not taking advantage of anything that their banks, insurance, investment, and other online0frequented companies, even their email provider, offer them.
I understand consumer inertia, outright laziness & all.
But when I explain to these people how, for example, that something as simple as using a ‘2fa physical key’ with a dedicated email account (we all can thank Google for their free AP Program that’s over 6+ years running now) in addition to setting up simple email login code requirements sent to that email, is a high-barrier to hurdle for hackers, malware gngs, etc.
Reading an article like this about Finistra, immediately my thoughts go to companies like FIS, Fiserv, ACI, Bottomline, Broadridge, Cardtronics, CoreLogic, Global Payments and MoneyGram. People have no idea of what could actually happen.
End consumers gotta wake up and start doing their part, on their end.
Yes, Finastra messed up majorly here, and I know this mantra of “protect yourself as much as possible” doesn’t apply to us devoted Krebs readers since we all probably already do it, but I sure could use an updated, refreshed Spring 2020 Krebs on Security article to wave in people’s faces when they look at me both glossy & crossed-eyed and say: “huh?…what??…who/what is FIS? Fiserv?? Are they a food-servng company?? etc, etc…” ;-/
Great idea for Brian to do a wrap-up article suitable for forwarding to our less-technical friends and relations.
My bank account is impacted by this. How long do these things take to resolve? I can’t view my balance and my bank isn’t telling me much other than it’s a technical difficulty. Does this mean my SSN and account info was stolen?
This is from Finastra at this time, it is an email I have received from them as a customer.
March 21, 2020, 9:00 a.m. Status Update: Attack successfully contained on Friday, March 20, 2020 . No evidence of any data loss or breach. Remediation work continuing 24/7 with the goal to restart production as soon as safe to do so in a controlled manner. More technical details are forthcoming.
How many banks in North America were affected?
Google for mortgagewebcenter.com to get a sense of the number of the banks that use their mortgage platform.
This is more than an “interruption”… this attack apparently caused my clients to not be able to close on their home on Friday, (3/20/20) and potentially (due to the current collapse of employment in the United States) they may not be able to close on their home AT ALL.
How many banks in Asia were affected?
I believe this is an informative article and it is extremely
useful and knowledgeable. I really enjoyed reading
this post. big fan, thank you!
King regards,
Demir Valenzuela