In February, hardware maker Zyxel fixed a zero-day vulnerability in its routers and VPN firewall products after KrebsOnSecurity told the company the flaw was being abused by attackers to break into devices. This week, security researchers said they spotted that same vulnerability being exploited by a new variant of Mirai, a malware strain that targets vulnerable Internet of Things (IoT) devices for use in large-scale attacks and as proxies for other cybercrime activity.

Security experts at Palo Alto Networks said Thursday their sensors detected the new Mirai variant — dubbed Mukashi — on Mar. 12. The new Mirai strain targets CVE-2020-9054, a critical flaw that exists in many VPN firewalls and network attached storage (NAS) devices made by Taiwanese vendor Zyxel Communication Corp., which boasts some 100 million devices deployed worldwide.
Like other Mirai variants, Mukashi constantly scans the Internet for vulnerable IoT devices like security cameras and digital video recorders (DVRs), looking for a range of machines protected only by factory-default credentials or commonly-picked passwords.
Palo Alto said IoT systems infected by Mukashi then report back to a control server, which can be used to disseminate new instructions — such as downloading additional software or launching distributed denial of service (DDoS) attacks.
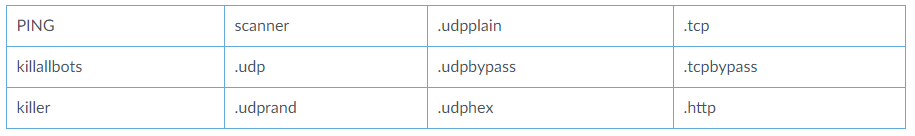
The commands Mukashi botmasters can send to infected devices include scanning for and exploiting other systems, and launching DDoS attacks. Image: Palo Alto Networks.
Zyxel issued a patch for the flaw on Feb. 24, but the update did not fix the problem on many older Zyxel devices which are no longer being supported by the company. For those devices, Zyxel’s advice was not to leave them connected to the Internet.
A joint advisory on CVE-2020-9054 from the U.S. Department of Homeland Security and the CERT Coordination Center rates this vulnerability at a “10” — the most severe kind of flaw. The DHS/CERT advisory also includes sample code to test if a Zyxel product is vulnerable to the flaw.
My advice? If you can’t patch it, pitch it, as Mukashi is not the only thing interested in this Zyxel bug: Recent activity suggests attackers known for deploying ransomware have been actively working to test it for use against targets.




I’m disappointed in Zyxel, because they used to be one of the better rated firewall routers, but it is probably better than my present Netgear at least. I really wasn’t worried either way until I was forced to buy an IoT device the other day. However I turned off remote external support on the device, and hopefully that will block any intrusions that way.
There is nothing about this on the Zyxel web site. How is anyone supposed to know what devices have this flaw, much less which ones can be patched or reset, or which should be tossed? https://www.zyxel.com/us/en/news/in_the_news_list.shtml
If your device is not listed on Zyxel’s website, or if you find it too difficult to verify it’s security, then best to assume it’s a liability & just move on without it
My DSL modem/router is a Zyxel device with Sprint branding, it’s probly over 6 years old. I’m about to solder up a phone cord with a wall power plug, in order to burn out the DSL port & make certain that device never makes it past any second hand stores
Sure, burn the router up with an electrical overload, but a ball peen hammer would do the job just as well, if not better.
Yes, there is. Scroll down to the bottom of the page you provided the link to (or probably any page on the site) to find the page footer, where you’ll find a menu. Under the heading “SUPPORT & TRAINING”, click on the item at the very bottom of the list of choices, “Security Advisories”. On the resulting page, after the big blurb at the top about how security is so friggin’ important to them, you’ll find a rather lengthy list of security bugs. Fortunately, the one you want is currently the top item: “Zyxel security advisory for the remote code execution vulnerability of NAS and firewall products”.
There’s a typo in the headline for this story:
Zxyel Flaw Powers New Mirai IoT Botnet Strain
In February, hardware maker Zyxel fixed ….
500mhz=Oleg Kucherov
https://www.linkedin.com/in/oleg-kucherov-0121b995/
bindump.com
dev@bindump.com
@BindumpSecurity