As the Coronavirus pandemic continues to force people to work from home, countless companies are now holding daily meetings using videoconferencing services from Zoom. But without the protection of a password, there’s a decent chance your next Zoom meeting could be “Zoom bombed” — attended or disrupted by someone who doesn’t belong. And according to data gathered by a new automated Zoom meeting discovery tool dubbed “zWarDial,” a crazy number of meetings at major corporations are not being protected by a password.
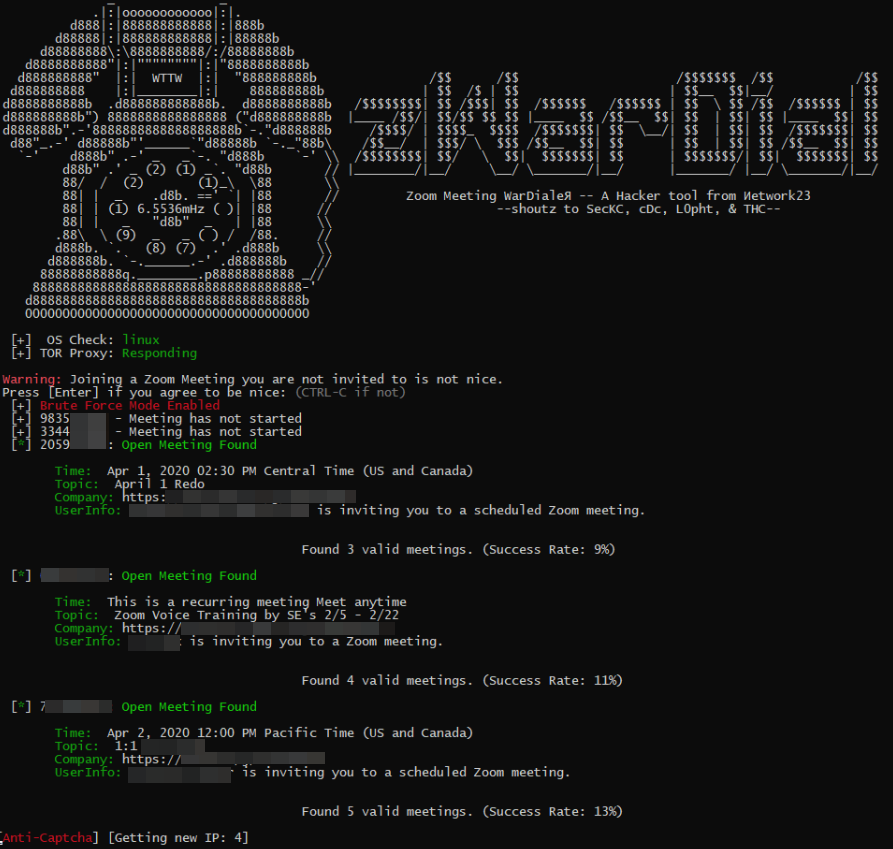
zWarDial, an automated tool for finding non-password protected Zoom meetings. According to its makers, zWarDial can find on average 110 meetings per hour, and has a success rate of around 14 percent.
Each Zoom conference call is assigned a Meeting ID that consists of 9 to 11 digits. Naturally, hackers have figured out they can simply guess or automate the guessing of random IDs within that space of digits.
Security experts at Check Point Research did exactly that last summer, and found they were able to predict approximately four percent of randomly generated Meeting IDs. The Check Point researchers said enabling passwords on each meeting was the only thing that prevented them from randomly finding a meeting.
Zoom responded by saying it was enabling passwords by default in all future scheduled meetings. Zoom also said it would block repeated attempts to scan for meeting IDs, and that it would no longer automatically indicate if a meeting ID was valid or invalid.
Nevertheless, the incidence of Zoombombing has skyrocketed over the past few weeks, even prompting an alert by the FBI on how to secure meetings against eavesdroppers and mischief-makers. This suggests that many Zoom users have disabled passwords by default and/or that Zoom’s new security feature simply isn’t working as intended for all users.
New data and acknowledgments by Zoom itself suggest the latter may be more likely.
Earlier this week, KrebsOnSecurity heard from Trent Lo, a security professional and co-founder of SecKC, Kansas City’s longest-running monthly security meetup. Lo and fellow SecKC members recently created zWarDial, which borrows part of its name from the old phone-based war dialing programs that called random or sequential numbers in a given telephone number prefix to search for computer modems.
Lo said zWarDial evades Zoom’s attempts to block automated meeting scans by routing the searches through multiple proxies in Tor, a free and open-source software that lets users browse the Web anonymously.
“Zoom recently said they fixed this but I’m using a totally different URL and passing a cookie along with that URL,” Lo said, describing part of how the tool works on the back end. “This gives me the [Zoom meeting] room information without having to log in.”
Lo said a single instance of zWarDial can find approximately 100 meetings per hour, but that multiple instances of the tool running in parallel could probably discover most of the open Zoom meetings on any given day. Each instance, he said, has a success rate of approximately 14 percent, meaning for each random meeting number it tries, the program has a 14 percent chance of finding an open meeting.
Only meetings that are protected by a password are undetectable by zWarDial, Lo said.
“Having a password enabled on the meeting is the only thing that defeats it,” he said.
Lo shared the output of one day’s worth of zWarDial scanning, which revealed information about nearly 2,400 upcoming or recurring Zoom meetings. That information included the link needed to join each meeting; the date and time of the meeting; the name of the meeting organizer; and any information supplied by the meeting organizer about the topic of the meeting.
The results were staggering, and revealed details about Zoom meetings scheduled by some of the world’s largest companies, including major banks, international consulting firms, ride-hailing services, government contractors, and investment ratings firms.
KrebsOnSecurity is not naming the companies involved, but was able to verify dozens of them by matching the name of the meeting organizer with corporate profiles on LinkedIn.
By far the largest group of companies exposing their Zoom meetings are in the technology sector, and include a number of security and cloud technology vendors. These include at least one tech company that’s taken to social media warning people about the need to password protect Zoom meetings!
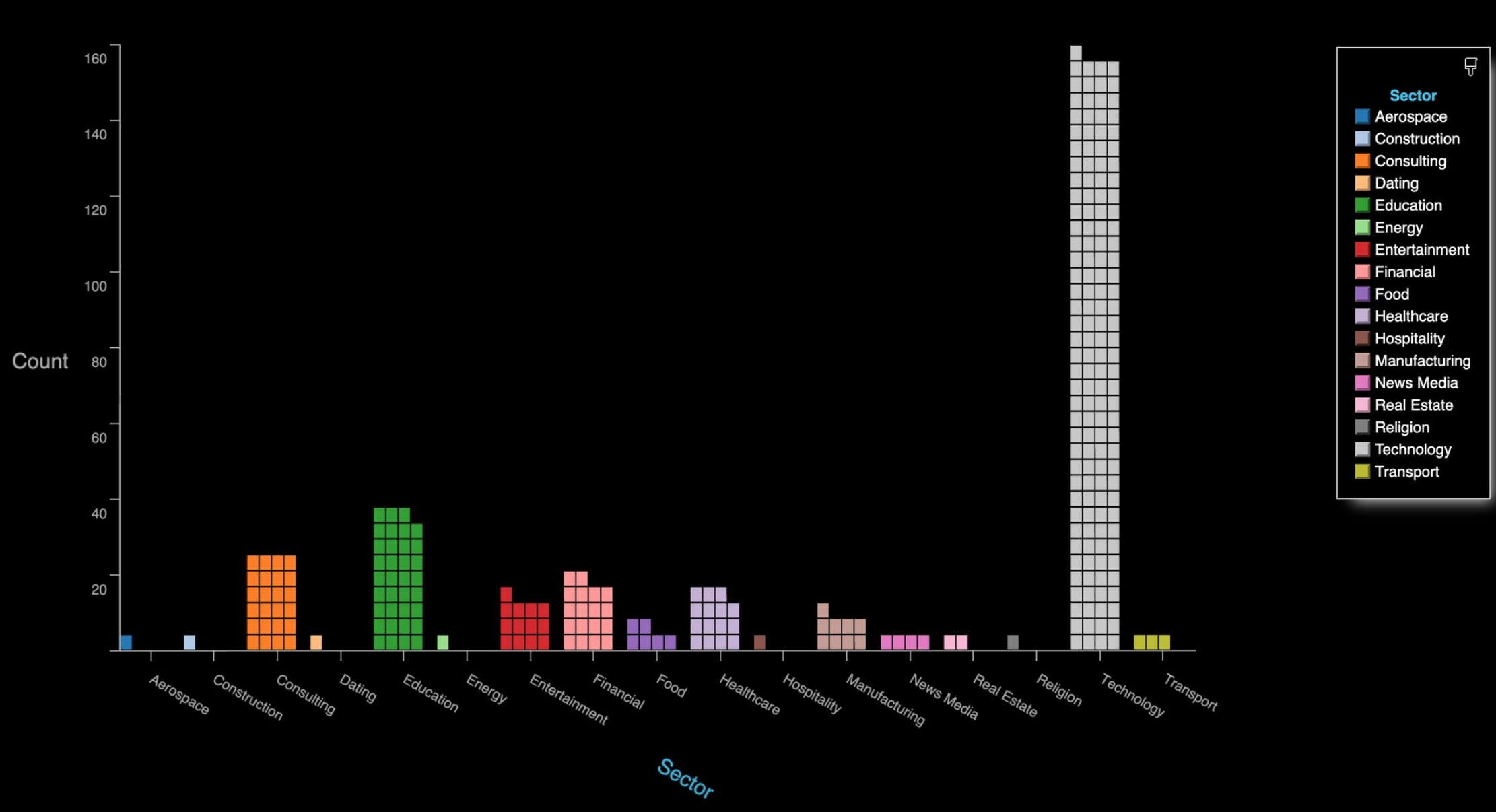
The distribution of Zoom meetings found by zWarDial, indexed by industry. As depicted above, zWarDial found roughly 2,400 exposed meetings in less than 24 hours. Image: SecKC.
A GREMLIN IN THE DEFAULTS?
Given the preponderance of Zoom meetings exposed by security and technology companies that ostensibly should know better, KrebsOnSecurity asked Zoom whether its approach of adding passwords by default to all new meetings was actually working as intended.
In reply, Zoom said it was investigating the possibility that its password-by-default approach may fail under certain circumstances.
“Zoom strongly encourages users to implement passwords for all of their meetings to ensure uninvited users are not able to join,” the company said in a written statement shared with this author.
“Passwords for new meetings have been enabled by default since late last year, unless account owners or admins opted out,” the statement continues. “We are looking into unique edge cases to determine whether, under certain circumstances, users unaffiliated with an account owner or administrator may not have had passwords switched on by default at the time that change was made.”
The acknowledgment comes amid a series of security and privacy stumbles for Zoom, which has seen its user base grow exponentially in recent weeks. Zoom founder and chief executive Eric Yuan said in a recent blog post that the maximum number of daily meeting participants — both paid and free — has grown from around 10 million in December to 200 million in March.
That rapid growth has also brought additional scrutiny from security and privacy experts, who’ve found plenty of real and potential problems with the service of late. TechCrunch’s Zack Whittaker has a fairly comprehensive breakdown of them here; not included in that list is a story he broke earlier this week on a pair of zero-day vulnerabilities in Zoom that were publicly detailed by a former NSA expert.
Zoom CEO Yuan acknowledged that his company has struggled to keep up with steeply growing demand for its service and with the additional scrutiny that comes with it, saying in a blog post that for the next 90 days all new feature development was being frozen so the company’s engineers could focus on security issues.
Dave Kennedy, a security expert and founder of the security consultancy TrustedSec, penned a lengthy thread on Twitter saying while Zoom certainly has had its share of security and privacy goofs, some in the security community are unnecessarily exacerbating an already tough situation for Zoom and the tens of millions of users who rely on it for day-to-day meetings.
“What we have here is a company that is relatively easy to use for the masses (comes with its challenges on personal meeting IDs) and is relatively secure,” Kennedy wrote. “Yet the industry is making it out to be ‘this is malware’ and you can’t use this. This is extreme. We need to look at the risk specific applications pose and help voice a message of how people can leverage technology and be safe. Dropping zero-days to the media hurts our credibility, sensationalizes fear, and hurts others.”
“If there are ways for a company to improve, we should notify them and if they don’t fix their issues, we should call them out,” he continued. “We should not be putting fear into everyone, and leveraging the media as a method to create that fear.”
Zoom’s advice on securing meetings is here. SecKC’s Lo said organizations using Zoom should avoid posting the Zoom meeting links on social media, and always require a meeting password when possible.
“This should be enabled by default as a new customer or a trial user,” he said. “Legacy organizations will need to check their administration settings to make sure this is enabled. You can also enable ‘Embed password in meeting link for one-click join.’ This prevents an actor from accessing your meeting without losing the usability of sharing a link to join.”
In addition, Zoom users can disable “Allow participants to join the meeting before the host arrives.”
“If you have to have this feature enabled at least enable “notify host when participants join the meeting before them,” Lo advised. “This will notify you that someone might be using your meeting without your knowledge. If you must keep your meeting unprotected you should enable ‘Mask phone number in the participant list.’ Using the waiting list feature will prevent unwanted participants from accessing your meeting but it will still expose your meeting details if used without a password.”
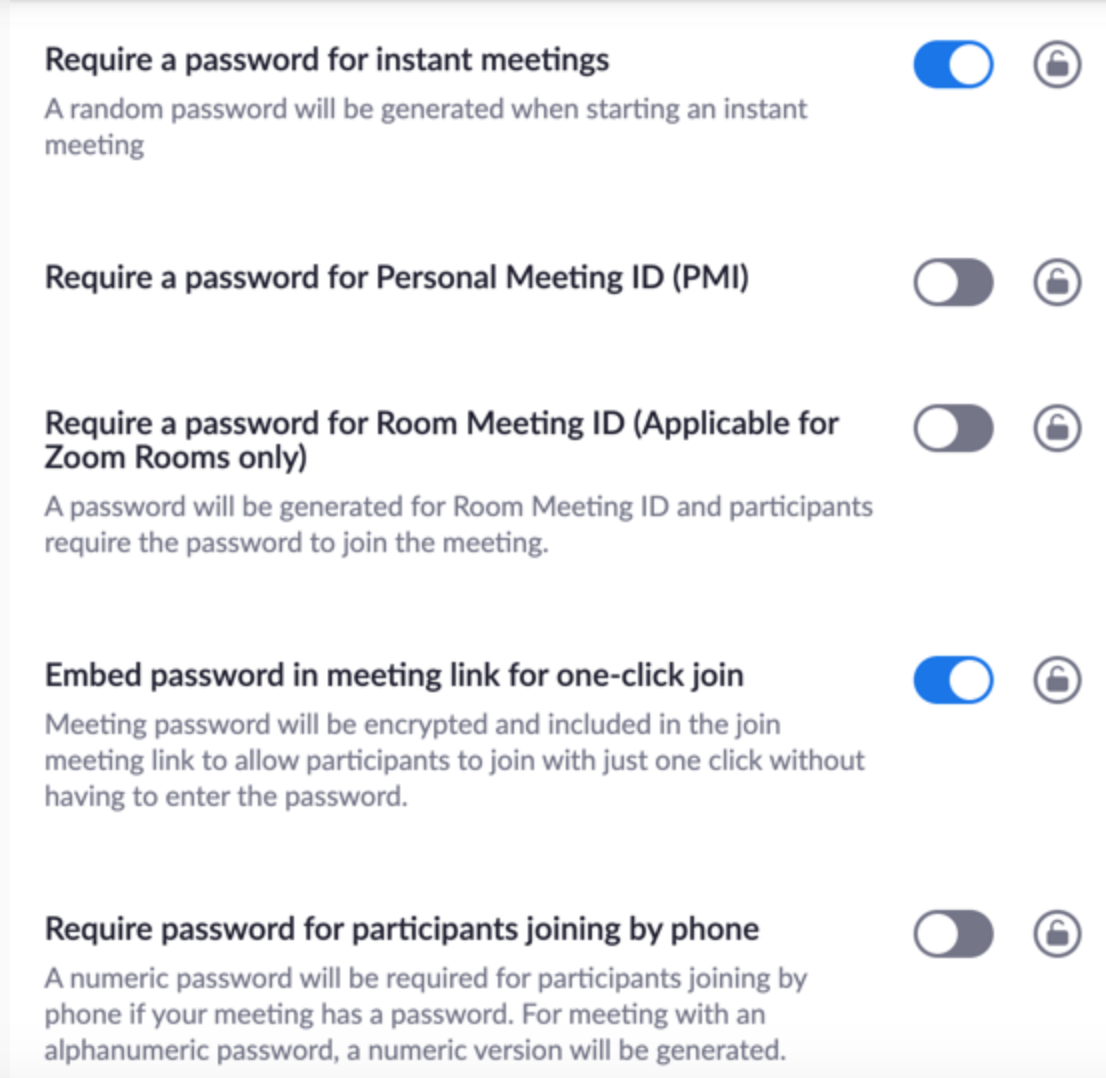
Some of the security settings available to Zoom users. These and others can be found at https://www.zoom.us/profile/settings/




At least Zoom is being responsive to the concerns, but hit-and-miss fixes do not score many points. Perhaps they should consider requiring passwords on all meetings, and remove any option to disable them. Would that be a hardship on anyone? Doubtful. Would it prove effective in thwarting the Zoom-Bombers? According to the data… likely so.
————-
“…Only meetings that are protected by a password are undetectable by zWarDial, Lo said.
“Having a password enabled on the meeting is the only thing that defeats it,” he said…”
I’m guessing, but doesn’t having a password increase the server-side workload for Zoom? I’m thinking they may have given the admins an option to disable that as a way to cut down on how many times Zoom needs to process password requests
I think Zoom is in a financial crunch to purchase more processing power. Just going by that shift in their user base that just happened. Some of their ‘security’ discussions might be asking how to continue offering free services
I don’t really see how a password request would be more expensive than video streaming which they do on a regular basis lol
There definitely needs to be more detail provided to users on what it means when they disable these settings. Perhaps the consequences weren’t fully identified before now but most users view this as easy of use without understanding the repercussions.
We are using Zoom for peer learning classes for retired people ages 65-95. We had 95% attendance within a week of switching from physical classrooms to Zoom online classes. The last 5% of users were a huge hurdle, most have gotten on only by use of pre-configured iPads, and they click join and type in the meeting ID. Adding a password would probably mean that one or two people would be excluded. And what are we are so scared of? A stranger might learn about art of the Proto Renaissance? We have taken the reasonable precaution of disabling screen sharing by anyone except the host. If a stranger appears and is disruptive, the host can mute or remove them.
> what are we are so scared of? A stranger might learn about art of the Proto Renaissance?
Heh! Yeah I was thinking the same as a I read this. Zoombombing? … meh.
I suppose someone might sneak into a big company meeting unnoticed, and happen to listen in on a confidential discussion. It would have to be more than a few people, otherwise everyone would be saying “errr… who’s the new guy?”. And the chance of hearing something confidential seems pretty slim. Most of our company meetings would be quite dull for a random outsider to listen through!
Medical providers are using Zoom to continue serving their patients. Hopefully they have the sense to password protect but I have a feeling that older providers may not understand the technology enough to know it is necessary.
The concern isn’t that someone would observe your classes, the concern is that someone would vandalize them. A user who suddenly begins screaming abuse & harassment, or displaying pornography would ruin the class for your users. Especially if they’re not tech savvy.
I second the recommendations Russ made. They’re a bit more hassle, but well worth it.
I agree. Now take this to the level of a 3 grade online classroom and you have monsters attacking children. No child ever needs to see the pornography these social deviants are spreading.
If you disagree,and I find you, May God have Mercy on you.
If your users can type in a meeting ID, they can type in a password. it’s just 5 more numbers, and they will be prompted for it.
I assume (not a zoom user since I learned about these gaping flaws last year) that all invited, including that 5% internet newbies or seniors mentioned in a previous comment, can copy/paste in the password? Disparate friends all in a family will be doing a Zoom family update tomorrow and thank goodness, after knocking on their heads forever on security, are taking these issues seriously. Thanks for making this clear Brian.
I think Defaulting to needing a password is good, but forcing it is bad. We have been having daily Zoom meetings with friends and just leave it up, anyone can join in – it’s an online bar basically, for social interaction. Passwords would be an issue for this.
So Forced passwords bad, default to password good, in my opinion.
That’s what I was thinking… Now it appears these options have been forcefully enabled in my account. Not they all say a password is needed and I can’t modify any of them as it appears they have been blocked my admin…. I thought I was the admin? what’s going on?
Hi Virginia, Zoom admins can set global settings that can not be changed at the users level, but there are several settings a user can change for their selves.
I just now created an account, and when I finished setting it up it gave me a “personal meeting ID” that was not password protected. I did not have to click anything to get that, it was just shown to me in a large font as soon as I signed in.
Zoom says require password is set by default? I have an inbox full of Zoom meeting invites that suggests otherwise.
Just enquired of my daughter if her school classes on Zoom were password protected, and she looked at me like I had grown a second head, “Of course they are, do you think we’re stupid?”
There is hope when a snarky 13 year-old can show such wisdom.
Thank you for a sustained laugh (ROFL) on a day that really needs it. Perhaps the old adage “Don’t trust anyone over 30” may still have some life in it. Maybe we need to go to the British model of a House of Commons elected by young voters and a House of Lords working in an advisory capacity for the rest of us. And yes, 30 appeared here in the rear view mirror a long time ago.
So if we address this security issue by simply treating all Zoom sessions as a publicly facing medium, for the time being until Zoom can improve their service
All of the admin settings that would open up loopholes should be accompanied by a warning message about Zoom bombing
And maybe it’s time to consider the ‘password’ as we know it to be outdated? Allowing an admin to decide what the characters should be for their password just seems to be an inherently failure prone approach
Wouldn’t it be better to use an access token?
How do you give an access token to a landline? How about a cell phone not using the app? Using an access token would make using the app mandatory, which would defeat part of the usefulness of Zoom in the first place. It pretty much becomes Slack at that point.
A meeting password of, well, password would even make this vulnerability nil, as it still couldn’t be auto discovered in this fashion. *ANY* password is better than no password.
@Osiris – I attend some evening meetings that requiring a password would be a hardship, mainly because a lot of people at these meetings are not the most tech savvy in the world, and the idea of the meetings is that anyone can join, as long as you stay on topic. And to be honest, I keep going back and fourth on requiring a password on these meetings or not. All my work related meetings do require a password (though we don’t use Zoom at work).
We have implemented most of the other options though, disabled public chat (except at the very end of the meeting) so you can only communicate with the host or co-host. We implemented the waiting room to screen out odd/suspicious looking names (which has helped a lot). Everyone is muted unless you are invited to talk and unmuted by a host/co-host. And we had enough co-hosts to monitor all the video and who had the immediate OK to kick anyone they felt was being inappropriate. We are also changing meeting IDs every day (which is annoying and has driven down attendance, but it’s the world we live in). And the meeting is locked till a host connects and they admit people.
So far these other steps seem to be working. If things change we will have to reevaluate the use of a password and do some extra hand holding with the less tech savvy people.
@Brian – keep up the great work! Especially now days your honest, to the point, investigative journalism is very, very, very important. Thank you again. I would shake your hand… but physical distancing needs to be maintained.
@Russ – those are some great tips for securing a meeting with a not-too-technical group.
Virtual high-five.
I agree! Thanks be to Russ!
@Russ, great thoughts, and thank you for sharing. It did help me to think that the session administrator is overly responsible for the configuration of that session. Perhaps password should be required as the default, but the option to disable provided. The security principle is “default deny”. With much on this thread, and the great responses, it seems like we can find a happy medium between too-little, and too-much in the way of security configurations. User experiences matter.
Cheers to all, and thanks for an informative and well-engaged thread.
As hard as it is to set up a Windows 7 chat session with my doctor; I’m surprised anyone could easily hack it – just setting one up successfully seems impossible right now! Maybe my doctor needs this Zoom! app?
They insist only Chrome works – well I have my doubts!
And no – my Win7 is not insecure – I keep it updated with OPatch.
FYI, Zoom has updated the client to fix the UNC clickable link issue that could expose your AD credentials. Version number is 4.6.9 (19253.0401).
Their download page does not show the information yet, but an autoupdate this morning installed the new version.
Thanks Moritmer; I was only half joking about it – because even if the app can be hacked, at least the function of it works!
Question 1: can this type of war dialer attack be used against other services? I know WebEx uses similar meeting IDs.
Question 2: I know WebEx has an enterprise-level setting requiring passwords. Does Zoom?
I’m confused how with the number space they have available, why random guessing is producing such a large number of matches. The researchers aren’t trying to guess flaws in their RNG. Even if there are 200 million meetings a day (that’s the number of active daily users, so meeting # is lower) with 9 to 11 digit meeting IDs, the number space should be large enough to avoid collisions at this rate.
Computer programs suck at RNG.
Over time, patterns can be found.
Makes for all kinds of easy scanning/guessing
once the patterns emerge.
Tho I would not know anything about that. 🙂
If you assume there are 200 million concurrent meetings, that means that there is a %0.2 chance you will hit a meeting. Or to put it simply 1/500. Let’s assume using a 100ms response time from zoom (my browser got a response from zoom.com in 90ms), that means I should easily be able to sample 10 meetings per second. Therefore in under a minute using a single process thread I could find at least one live meeting. It shouldn’t be too hard to imagine scaling that up even from my simple laptop to be able to find lots of meetings in very little time.
You are assuming an average of 1 call per day per user. Business users may use many more than that per user per day. Also, meetings scheduled in advance may reserve an ID for several days in advance, making it unavailable for others for that duration. I’m not sure how soon after meetings an identifier is returned to the pool of available IDs.
Also, 200 million is 20% of the search space for a 9 digit meeting ID, and 9 digit IDs are common in my experience.
My concern would be that the meeting ID space is going to get very congested if their popularity continues to increase. With free meetings possible, I worry that a denial of service may be possible by deliberately using up meeting IDs, exhausting the space of available IDs
I see Zoom trying to respond on security concerns. I don’t see them being very responsive at all on privacy concerns.
The company has been caught twice in the last month scraping social media data on their attendees. That’s twice too many for me. I’m warning my company’s employees to steer clear and use other platforms.
What do you think about Zoom’s reply on this: “On March 27th, we took action to remove the Facebook SDK in our iOS client and have reconfigured it to prevent it from collecting unnecessary device information from our users.
“On March 29th, we updated our privacy policy to be more clear and transparent around what data we collect and how it is used – explicitly clarifying that we do not sell our users’ data, we have never sold user data in the past, and have no intention of selling users’ data going forward.”
How is this different then joining a webex meeting that doesn’t have a password?
I personally know of a couple groups that have had their meetings crashed, called slurs, etc. It’s traumatizing. Zoom should implement anti-harassment measures and ban users and/or devices that do this. It wouldn’t stop 100% of it but it would help.
Those screenshots of the app really take me back. My guess is that the average age of people attending SecKC is over 50. Ha ha. And that’s undoubtedly pronounced ‘sexy, no’? Ahhh, the 80’s hacker community. In some ways I really miss it.
So, what universal platform (OS and hardware) secure alternatives exist? FaceTime is supposedly private and secure, but Apple only. Signal video is mobile device only.
Hey, So if zoom is not safe. Do you think another video conferencing software is safe to use in the coming future?
ALL: Zoombombing CAN mean a person drops in, and shares their screen displaying, ahem, questionable/disturbing-to-some content to the group (tink pr0n, violence, etc.). As someone mentioned this CAN be traumatizing.
So YES, USE THE “Embed password in meeting link for one-click join” OPTION under > profile > settings
@Brian
I think Slido’s service (https://www.sli.do/) has a similiar issue. Customers can create Q&A events without passwords. The event ID is the only information needed to join such events and the ID is specified by the user upon event creation. I’m not a security researcher, but this looks to me as if one could easily scan through a large range of possible IDs. It’s certainly easy to do a targeted scan for one company since they usually include some abbreviation of the company (or division) name in the event code, together with a sequence number or a year or a date.
Or one can merely use Google to list all sorts of “public” events. I’ll not paste the query here, but it’s fairly easy to put together without any real pentester experience.
What I am surprised by is that it is apparently not possible to associate access control lists with meetings, so I can specify a list of the people who can join the meeting. Sure I can require that people authenticate with SSO, but then anyone who authenticates is authorized to join. I can set up a waitlist and only allow in the “right” people, but if it’s a meeting of 300 people, this is not feasible.
I use password protection, the link I get includes the password as a query parameter (this is the only way the use of passwords would be acceptable to my user base), so I guess the point of the password is just to prevent war dialing. If someone puts the link, password and all, up on social media, then only some form of authorization can prevent gatecrashers. See above.
how about webex and microsoft teams?
Vincent, and others…
As noted in the Oct 2019 publication of the Prying Eye vulnerability, Webex acknowledged the same problem – users were disabling security making it easy for bots to enumerate the namespace and find a valid meeting. In the discovery below, the APIs were targeted.
https://www.cequence.ai/cequence_news/cequence-security-discovers-vulnerability-in-leading-web-conferencing-platforms/
This is not just a zoom “problem”. Every meeting service has the exact same issue.
For ease of use they are all using this method.
So for fairness Brian can you have a crack at WeBex, GoTo, Bluejeans, etc?
Agreed. Yet, FBI (!) called it “Zoombombing”, not “VC-bombing”. And Wired, Brian and Bruce Schneier are all writing about Zoom specifically on exact same day.
Some findings (both recent and past) in Zoom indeed look scary (although so do some findings in, say, Slack). But it seems to me that the underlying problem here is “Zoom sends their encryption keys to China”, but not to Langley. So there’s a Huawei-like coordinated scaremongering campaign all over again, “we don’t want China to spy on you – we want to spy on you ourselves”.
My daughter’s school is using Zoom. Fortunately, they somehow decided to password protect the Zoom meetings my daughter was asked to attend — maybe the default was in place by then.
For now, my takeaway is that password protection will do the trick . . . for now.
Thanks Brian for the great write-up. Always good to know that you are on it.
+1
For those of you looking for a secure be design web conferencing system please check out this website. GoWildix.com it will not only take care of your meetings but much much more.
Brian, side question for you. Over the years you have shown a tendency for leniency of punishments for cyber criminals, while others including myself would rather see very harsh punishments for many of the crimes.
Have the crimes against hospitals, and the fraud surrounding crimz taking advantage of this pandemic changed your mind?
I think you are a fantastic researcher, and maybe it’s that you are a parent that you offer a lot of forgiveness, understanding that some of the criminals are young – which doesn’t change the effect on the victims, often loosing their life labor/savings and being left destitute.
I’m all for password protecting zoom meetings – and this article is excellent. But we have enabled the feature to “allow” guests into the meeting room. I think zoom calls this the waiting room.
Just thinking – would this achieve the same behavior – of keeping bad actors out?
This is how we’ve managed our zoom calls, foregoing passwords and manually adding in folks we know from the waiting room.
Just curious what feedback you may have on this?
Keys Used to Encrypt Zoom Meetings Sent to China
https://www.securityweek.com/keys-used-encrypt-zoom-meetings-sent-china-researchers
During test meetings conducted by users in Canada and the United States, researchers noticed that the key used to encrypt and decrypt the video conference was sent to a server apparently located in Beijing, China.
According to Zoom CEO there was no leak from their platform. They said that Zoom cant be hacked so easily as people say. Don’t know what to do now. Is this App safe anymore?
Thanks for the support
i was able to find hundreds unprotected meeting using Burp Intruder. you can find a post about it on my blog.
This technique is not new. The software used (wardialz) is just making things easy when targeting zoom service as a vector for finding free confz. This is almost as lame as my google dork vuln article. I discovered it prolly around 2002 and had a few years of fun making prank calls across the country for free and showing girls how to make calls with landlines across the country without paying a dime (not gunna lie, in the early 00’s girls loved being able to chat with their friends who were in far away area codes without wracking up their parents phone bills.. truth.)
if you take a look at k-1ine issue 47 (titled ” SIX F*CKING YEARS ” written in Spring of 2005) the 5th article in the zine titled “The Guide to Using Google to Get Free Confz” written by myself, it explains how to use google dorks to find not only recordings of teleconferences that have already taken place, but also current ones happening right now, and future ones that havent taken place yet; sometimes letting you know months in advance!
It is also not hard to not only find the participant pin to let you in, but also find the administrator pin (essentially the teleconferences master password) that allows you to change how many participants allowed in the teleconference, when the participants entered the conf, the ANI of the participants, booting participants out of the conf, and even using the admin pin to call out to any number you want, and call someone -any number- and make them join the conference.
More often than not you’d only find participant passcodes, and when that happens the most you can do is share the 800 number and the participant passcode to all your friends irl and from far away (for me it was on IRC) or wheverver and chat.. but every once and a while an administrator passcode will come up in the google searching. When that happens, some real lulz could be had. You can outdial any number you want on the confz dime.. You had the ability to prank whomever you wanted as long as you had their phone number – and everyone on the conf could hear it in real time, and even join in on the crank call, or ruin it if they sucked.
The thing you have to remember tho, is that all of those confs are being recorded as a default setting as long as there is a participant on the conf. This is so that members who missed the conf can go back and hear what was said. I found that some systems allowed you to turn off recording if you had the admin code. If by some chance a legitimate employee from the company calls into the conf while you and your friends were abusing their teleconf, then they would likely call the telco provider who was providing the conf and get an operator to shut down the conf, change the codes and that would be the end of the lulz.
Pretty much every dial-in toll free conf number I ever found was owned by a telco… MCI, Bell, ATT, Verizon, Rodgers, Bell South, Telus , they all had multiple teleconf toll free numbers.
It looks like things have changed in 15 years – zoom has bought up many numbers or is simply leasing them out from traditional telcos and conf providers.
Example: This one, a toll number based in canada: 647-558-0588 is operated by Iristel Inc out of Toronto (according to reverse yellowpage lookup) and is registered as a landline…
… but is being leased out to or used by zoom. How do I know this? because when I google the number I find that an environmental organization is hosting a zoom conference at April 23, 2020 at 4:30 PM and have posted the access number as well on their website. They are even offering a prize to those who will be present on the conf at that time!
..Of course they mean that the prize is only for MEMBERS of their organization, of whom are the only actual ones invited to the conf – but they dont say that ANYWHERE on the website.
Based on this one phone number I am going to guess that zoom contracts out (or rents services from) traditional teleconf providers, so each of the dial-in numbers they provide their customers could be on a different system… If they need a dial-in number from nyc the participants calling in likely could be using a nynex supplied teleconf wrapped up to look like zoom is the provider. Ive never used zoom, but thats how im going to guess how they work for the actual phone in part of their service.
I am more responsible now than I was 15 years ago so I wont share the name of the company, or the passcode nor the link to the site, but it goes to show that google dorking of conf access numbers is all you need to do what is stated in this article.
That was the first number that I tried googling and sorted by date. I would much less blame on zoom, and much more blame on companies who do this sort of idiotic public disclosure of information on their very public website with no disclaimer, warning or any notice whatsoever saying that it is meant for their employees only.
I have no doubt that at least *some* of the interruptions to legit confz have been due to ignorance of some random web surfer rather than any sort of malice.
With that said, dont be an idiot and try takng over confz.
Theres no need. you can get free phone calls with textnow.com or google voice or skype or any number of other free services.
Your ANI will reveal your landline or mobile phone number and there will always be the chance of toll fraud, especially if you are dialing into a TOLL FREE number because it is not toll free to the one paying for it,
and even _moreso_ if you are using the admin code to dial out. You could be breaking the Computer Fraud and Abuse Act if you are disrupting any conf that has to do with business or whatever.. im not a lawyer but I know for sure your ass could go to jail if the conf belongs to pretty much anyone whos trying to do do business especially now that many need to work from home!
As far as my antics went in the early to mid 00’s, that never did happen to anyone I knew during my own exploits, nor did it happen to myself. Mostly because I used confs when no one else was on them. I count myself lucky..
I was young, stupid, and having a great time making dumb phone calls with IRC friends from all over the place, but I was very dumb while exploring this vuln 16+ years ago. By the time I actually wrote the article, I had a part time job that paid for my own landline with free long distance so I stopped using confz. That, and a lot of people who I shared them with on IRC were just plain embarrassing or weird to talk too.
You dont need much skill to do this. Just knowledge of the toll free phone numbers that are portals to these corporate teleconfs, access to google, and sorting results by the most recent date .. and that is pretty much it.
Specific google dorking details are linked in k-1ine issue 47 above, (btw the k-1ine issues above #45 and higher are actually pretty rare – they are not even featured in textfiles.com)
so you heard it here, on kerbs first! (except only 15+ years late!).
Anyone who shares an admin pin to a toll free conf and lets it activate a month before its needed and then shares it on the public internet where a whole bunch of idiot kids from all over the place use it deserves to be fired.
Granted, the kids need a smack for being idiots (I know I did 20 years ago when I figured this out and abused it to make prank calls and talk to girls in other area codes for free),
But it is especially stupid in times such as this where we need to work from home to keep the economy from completely collapsing. Those of you out there who are doing this – stop doing it. You are risking going to jail, and those people who are legit using the confz are keeping the system that we call society running.
Sorry for the retarded long comment – it hit a bit of nostalgia for me. (PS Spam Nation was legit unbelievably eye opening)
It gets worse.
“An app with easily-identifiable limitations in cryptography, security issues, and offshore servers located in China which handle meeting keys presents a clear target to reasonably well-resourced nation state attackers, including the People’s Republic of China,” the report says.
https://www.theregister.co.uk/2020/04/03/dont_use_zoom_if_privacy