The COVID-19 pandemic has made it harder for banks to trace the source of payment card data stolen from smaller, hacked online merchants. On the plus side, months of quarantine have massively decreased demand for account information that thieves buy and use to create physical counterfeit credit cards. But fraud experts say recent developments suggest both trends are about to change — and likely for the worse.
The economic laws of supply and demand hold just as true in the business world as they do in the cybercrime space. Global lockdowns from COVID-19 have resulted in far fewer fraudsters willing or able to visit retail stores to use their counterfeit cards, and the decreased demand has severely depressed prices in the underground for purloined card data.
That’s according to Gemini Advisory, a New York-based cyber intelligence firm that closely tracks the inventories of dark web stores trafficking in stolen payment card data.
Stas Alforov, Gemini’s director of research and development, said that since the beginning of 2020 the company has seen a steep drop in demand for compromised “card present” data — digits stolen from hacked brick-and-mortar merchants with the help of malicious software surreptitiously installed on point-of-sale (POS) devices.
Alforov said the median price for card-present data has dropped precipitously over the past few months.
“Gemini Advisory has seen over 50 percent decrease in demand for compromised card present data since the mandated COVID-19 quarantines in the United States as well as the majority of the world,” he told KrebsOnSecurity.
Meanwhile, the supply of card-present data has remained relatively steady. Gemini’s latest find — a 10-month-long card breach at dozens of Chicken Express locations throughout Texas and other southern states that the fast-food chain first publicly acknowledged today after being contacted by this author — saw an estimated 165,000 cards stolen from eatery locations recently go on sale at one of the dark web’s largest cybercrime bazaars.
“Card present data supply hasn’t wavered much during the COVID-19 period,” Alforov said. “This is likely due to the fact that most of the sold data is still coming from breaches that occurred in 2019 and early 2020.”
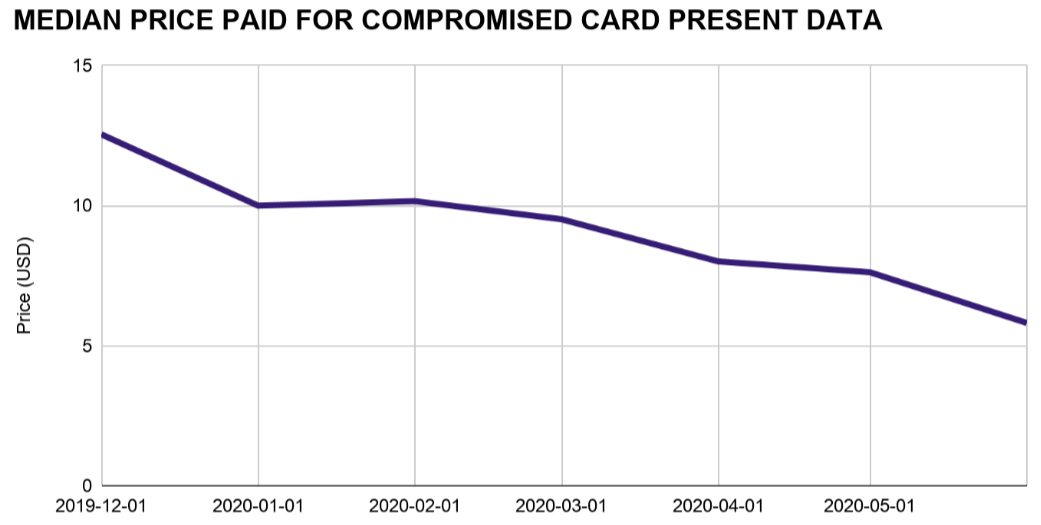
A lack of demand for and steady supply of stolen card-present data in the underground has severely depressed prices since the beginning of the COVID-19 pandemic. Image: Gemini Advisory
Naturally, crooks who ply their trade in credit card thievery also have been working from home more throughout the COVID-19 pandemic. That means demand for stolen “card-not-present” data — customer payment information extracted from hacked online merchants and typically used to defraud other e-commerce vendors — remains high. And so have prices for card-not-present data: Gemini found prices for this commodity actually increased slightly over the past few months.
Andrew Barratt is an investigator with Coalfire, the cyber forensics firm hired by Chicken Express to remediate the breach and help the company improve security going forward. Barratt said there’s another curious COVID-19 dynamic going on with e-commerce fraud recently that is making it more difficult for banks and card issuers to trace patterns in stolen card-not-present data back to hacked web merchants — particularly smaller e-commerce shops.
“One of the concerns that has been expressed to me is that we’re getting [fewer] overlapping hotspots,” Barratt said. “For a lot of the smaller, more frequently compromised merchants there has been a large drop off in transactions. Whilst big e-commerce has generally done okay during the COVID-19 pandemic, a number of more modest sized or specialty online retailers have not had the same access to their supply chain and so have had to close or drastically reduce the lines they’re selling.”
Banks routinely take groups of customer cards that have experienced fraudulent activity and try to see if some or all of them were used at the same merchant during a similar timeframe, a basic anti-fraud process known as “common point of purchase” or CPP analysis. But ironically, this analysis can become more challenging when there are fewer overall transactions going through a compromised merchant’s site, Barratt said.
“With a smaller transactional footprint means less Common Point of Purchase alerts and less data to work on to trigger a forensic investigation or fraud alert,” Barratt said. “It does also mean less fraud right now – which is a positive. But one of the big concerns that has been raised to us as investigators — literally asking if we have capacity for what’s coming — has been that merchants are getting compromised by ‘lie in wait’ type intruders.”
Barratt says there’s a suspicion that hackers may have established beachheads [breachheads?] in a number of these smaller online merchants and are simply biding their time. If and when transaction volumes for these merchants do pick up, the concern is then hackers may be in a better position to mix the sale of cards stolen from many hacked merchants and further confound CPP analysis efforts.
“These intruders may have a beachhead in a number of small and/or middle market e-commerce entities and they’re just waiting for the transaction volumes to go back up again and they’ve suddenly got the capability to have skimmers capturing lots of card data in the event of a sudden uptick in consumer spending,” he said. “They’d also have a diverse portfolio of compromise so could possibly even evade common point of purchase detection for a while too. Couple all of that with major shopping cart platforms going out of support (like Magento 1 this month) and furloughed IT and security staff, and there’s a potentially large COVID-19 breach bubble waiting to pop.”
With a majority of payment cards issued in the United States now equipped with a chip that makes the cards difficult and expensive for thieves to clone, cybercriminals have continued to focus on hacking smaller merchants that have not yet installed chip card readers and are still swiping the cards’ magnetic stripe at the register.
Barratt said his company has tied the source of the breach to malware known as “PwnPOS,” an ancient strain of point-of-sale malware that first surfaced more than seven years ago, if not earlier.
Chicken Express CEO Ricky Stuart told KrebsOnSecurity that apart from “a handful” of locations his family owns directly, most of his 250 stores are franchisees that decide on their own how to secure their payment operations. Nevertheless, the company is now forced to examine each store’s POS systems to remediate the breach.
Stuart blamed the major point-of-sale vendors for taking their time in supporting and validating chip-capable payment systems. But when asked how many of the company’s 250 stores had chip-capable readers installed, Stuart said he didn’t know. Ditto for the handful of stores he owns directly.
“I don’t know how many,” he said. “I would think it would be a majority. If not, I know they’re coming.”




I think we should coin the phrase Breachheads now 🙂
That’s Breachheads®
Seconded!
Is a breach head when I eat too much beans and I make a brown in my pants?
No, a ‘Breachhead’ is when you have ate too many beans to stop me from leaving a brown in your pants!
“But when asked how many of the company’s 250 stores had chip-capable readers installed, Stuart said he didn’t know.”
Ah, we see where the problem actually lies…
surely given the amount of card fraud in the US it would pay the providers to just push out chip-capable enabled readers to all vendors
they must have replaced cards quite a few times by now, we have had chip readers in Au for so long now I can’t remember the last time I had to swipe
just seems so backward and a lack of care for consumers
funny thing is a still see the chip slot taped over in some places in the US and told to just slide… yeah screw you ill use cash…
o wait they are banning cash too due to this election year synthetic chaos (covid/BLM)
Taped over chip slots may not be that big of a problem as it first seems. One franchised food place I frequent has their chip slot taped over, but they accept Apple / Google Pay and their phone app also accepts Apple / Google Pay. The only reason I know this is I have to use the keypad to enter my rewards number. I haven’t paid with a physical card there for at least 5 years.
Being one of the world’s leaders, its strange how in US its still widely used magnetic cards instead of the ones with chip?! Here in EU cards with chip are standard, magnetic stripes are not used.
Chip cards are quite widespread here in the U.S. by now.
All mine are, so are all in my children’s families.
All UK cards are chip and pin. Why is the USA so backwards at implementing much of the security that is developed in the USA in the first place. Most transactions are Apple Pay or Google Pay to avoid the £45 pin less transaction value. I can’t remember the last time I used my pin, maybe my fingerprint on my phone to authorise on the old odd occasion (usual transactions over £500).
From what I understand, the POS devices for Chip-n-pin are so expensive, that many merchants literally can’t afford the machine. Since the credit card companies have congress’s ear, they have allowed merchants in a class of total yearly sales to deflect using the new device, and because the credit companies want as much business as they can get, they allow them to get away with the old magnetic swipe technology.
I’m surprised many of them can even afford to give credit card service to their customers at all – because it is expensive enough as it is.
Is that true for Square also ? I’d admired their mobilizing tech but never thought to ask after costs.
Out here on the southwest coast of the US, we’re seeing a majority of the in store readers are now chip readers.
Pay at the pump is still far behind.
That said, I’ve never seen a “chip and PIN” reader around these parts.
All are either chip and go or chip, sign, and go.
The chip readers are also incredibly fragile.
Customer shoves the card in, fails to read, slams it in harder and it fails again.
Clerk reaches over the counter, gently inserts the card (maybe a couple times) and it reads.
Soon enough, the chip reader is broke and we’re back to sliding.
$20-$30 a month – for a chip reader, that can be attached via USB or serial to a vanilla windows POS. if you can’t afford that you have no business taking credit card payments.
And many of the small vendors running Magento 1 will not be able to afford the upgrade to Magento 2 because of reduced sales during this period.
That’s certainly not another failure of the free market.
Good read. Interesting comments,but…
The card reader? In a location, depends on the “security bend” of the owner of a business. How important the security is related to future sales is unknown. But, stolen numbers will create an ill will and shoppers may move on to someone else fried chicken joint. The article really disappointed me, he is really more interested in his profit, rather the the public’s safety in his store. Capitalism at its finest.
Just about a week ago my AMEX card had an attempted false charge, but AMEX flagged it.
It was a chip card and had not been used in a POS transaction in a long time.
However, I have used it for online purchases.
Being responsible for infosec at a SaaS company, I sometimes have nightmares about hearing the words “there’s a guy named Brian Krebs on the phone wants to talk to you.”
I sure hope it never happens. But, cybercreeps are smart.
Thanks for the link on the Chicken Express breach. Now I know where my card data was stolen earlier this year. Until recently, Chicken Express was still using swipe readers only, and had not enabled their chip readers. Sometime in the past 4-5 months, they moved to activate the chip readers.
The good news is the card issuer, Citi (not a favorite, but they deserve credit), flagged the second and third transactions as possibly fraudulent, locked the card and called me. I only had to contest an AT&T account payment in Los Angeles, the Sports Memorabilia purchase for ~$1,200 in New York and a $4,000 payment to an LA plastic surgeon were both rejected. All that happened within 11 minutes, at 12:50 AM EST on a Friday night…the scary bit is they probably only got flagged because of the rush of charges in widely spread locations.
Hi. I always use a memory stick in internet cafés but I do not have any security on it. Can you recommend something? thanks in advance, tom
Try a stick of chewing gum instead. Totally unhackable. Also, delicious.
The use of virtual account #s is an increasing smart decision to slow the theft of card data (I use Citi virtual card data).
I have also used pseudo names in transactions and trying to investigate how to bypass/fool address verification with stored aliases.