Companies hit by ransomware often face a dual threat: Even if they avoid paying the ransom and can restore things from scratch, about half the time the attackers also threaten to release sensitive stolen data unless the victim pays for a promise to have the data deleted. Leaving aside the notion that victims might have any real expectation the attackers will actually destroy the stolen data, new research suggests a fair number of victims who do pay up may see some or all of the stolen data published anyway.

The findings come in a report today from Coveware, a company that specializes in helping firms recover from ransomware attacks. Coveware says nearly half of all ransomware cases now include the threat to release exfiltrated data.
“Previously, when a victim of ransomware had adequate backups, they would just restore and go on with life; there was zero reason to even engage with the threat actor,” the report observes. “Now, when a threat actor steals data, a company with perfectly restorable backups is often compelled to at least engage with the threat actor to determine what data was taken.”
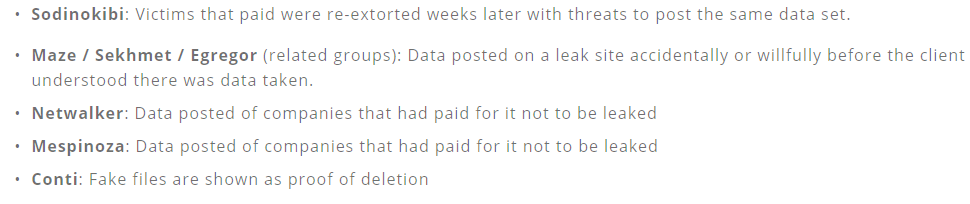
Coveware said it has seen ample evidence of victims seeing some or all of their stolen data published after paying to have it deleted; in other cases, the data gets published online before the victim is even given a chance to negotiate a data deletion agreement.
“Unlike negotiating for a decryption key, negotiating for the suppression of stolen data has no finite end,” the report continues. “Once a victim receives a decryption key, it can’t be taken away and does not degrade with time. With stolen data, a threat actor can return for a second payment at any point in the future. The track records are too short and evidence that defaults are selectively occurring is already collecting.”
The company said it advises clients never to pay a data deletion ransom, but rather to engage competent privacy attorneys, perform an investigation into what data was stolen, and notify any affected customers according to the advice of counsel and application data breach notification laws.
Fabian Wosar, chief technology officer at computer security firm Emsisoft, said ransomware victims often acquiesce to data publication extortion demands when they are trying to prevent the public from learning about the breach.
“The bottom line is, ransomware is a business of hope,” Wosar said. “The company doesn’t want the data to be dumped or sold. So they pay for it hoping the threat actor deletes the data. Technically speaking, whether they delete the data or not doesn’t matter from a legal point of view. The data was lost at the point when it was exfiltrated.”
Ransomware victims who pay for a digital key to unlock servers and desktop systems encrypted by the malware also are relying on hope, Wosar said, because it’s also not uncommon that a decryption key fails to unlock some or all of the infected machines.
“When you look at a lot of ransom notes, you can actually see groups address this very directly and have texts that say stuff along the lines of, Yeah, you are fucked now. But if you pay us, everything can go back to before we fucked you.'”




That is why there should be some legislature that makes it illegal for any US company to pay any ransom to restore their encrypted computer files. Period.
This will also be beneficial for a consumer as well. As we will not be kept unaware if some company decides to just sweep their ransomware incident under a rug by paying the ransom and not telling the users that their private data was exposed.
I agree entirely Dennis. We need to take the wind of the sails of this nefarious criminal business. By now every CEO of every company should be aware of the risks they take by inadequate security or unpracticed BCP/DR capabilities. They should have already put in place a corrective action plan so they can deal with a security incident quickly and efficiently. If not then they need to start writing their resignation letters. Failure to prepare is no excuse at all today.
Obviously in critical industries like healthcare time to restore and recover is a major concern, if patients are dying because HIT and HIoT systems are down and unable to diagnose or treat them. But paying blood money for a decryption key and running that decryption should be no faster than a well engineered and practiced backup and restore system. Furthermore, when restoring from your own backups you can trust the integrity of the data unlike data that may have been compromised by hackers.
CEOs need to spend the money when and where it makes sense – and that is NOT on a roulette wheel for those that continue to weigh the odds of attack, versus the size of their annual bonus and stock options.
Agreed. An even easier first step would be a law prohibiting insurers from paying these ransoms on behalf of their clients.
The Grugq, a respected security expert, is of the opinion that a ban on paying a ransom will only make things worse. Such a ban will only be partially effective because some victims will pay anyway. Therefore the ransomware gangs will still make money and not cease their operations.
A ban will make the gangs more aggressive and the whole process more opaque. There will be few legal companies that negotiate the ransom and in some way “manage” the gangs.
For more see: gru.gq/2020/10/18/ransomware-prohibition/
I’m interested in others thoughts on this. If paying ransom is the only way to restore your business and your livelihood, should that be allowed? What if your business is a Dr’s office, and all of your patient’s medical records are encrypted, impacting your ability to effectively treat them?
Interestingly the US Treasury Dept issued guidance last month that prosecution could occur for making ransom payments, but also provided some relief for reporting payments and cooperating with law enforcement.
I don’t think your example is a good one. Unless the patient is incapacitated, you can always recreate most of the records by talking to the patient and/or redoing some tests.
Rich, I think you underestimate the quantity of data associated with a single patient. I want my doctor to have my complete medical history available. I can’t tell you all my test results from the 20-odd years I’ve been visiting my primary care physician. And then there’s billing. I’ve had to request records two years after the fact to satisfy insurance company needs.
Jill – While I sympathize with any doctor who has been the subject of a cyber extortion attack, the fact is that that given a long history of ransomware attacks against healthcare and missive publicity all over the world, if any doctor still only has a single copy of their patients records, with no off-site backup and restore plans, then they plainly don’t intend to stay in business for long. Its not a question “if” that medical practice is attacked, but “when” today unfortunately.
Unfortunately, I’m beginning to think that the only way to stop ransomware is if no one EVER pays the ransom. And I’m afraid the only way for that to happen is some kind of government enforcement. It seems backward to punish the victim (either by potentially losing encrypted data, or by charging the victim with a crime), but under this scenario that’s the only possible choice. So ransomware will drive some businesses out of business initially, but eventually there will be no more financial incentive for the ransomware extortionists, and they will find some other way to continue their life of crime. Maybe. The worst case scenario would be law-abiding victims don’t pay, and are driven out of business, and other victims circumvent the laws and continue making ransomware profitable. Obviously not a good outcome.
If we could de-anonymize crypto currencies and then “follow the money” we could potentially stop ransomware that way, but I think the math says that isn’t going to happen.
[…livelyhood…] No. If you failed to invest in basic IT security practices, prefer to use the password of “password” because of convenience, and your company fails because of it, thats #1 entirely your gamble, and #2 a small societal price to pay for majorly disrupting the existing illegal ransomware feedback loop of >Ransom > Profit > Improve > Repeat
[…healthcare…] Yes but only AFTER involvement of proper authorities and reporting. If someone’s life is literally on the line, and this is the only way to prevent an innocent casualty, then sure life and limb is more important than money. However the process should be legislated to require the involvement of gov authorities and public reporting of the incident. Failure to report should include jail time, or else it will never happen (I know, see below).
[…to prevent public disclosure…] Never. If you have backups and dont need to pay to restore critical services, and only are interested to pay to prevent public disclosure of the incident, you’re SOL. You should have adequately secured the public’s data to begin with, now suffer the public consequences. The point you irreversibly lost control of the data, was when it was originally uploaded to systems you don’t control – not the point where you declined to pay to prevent disclosure.
(I’m an IT incident responder by day and I help private companies including healthcare conglomerates cover this sh** up all the time – I make bank doing it but even I will say what I get asked to do every day should be illegal….. but isnt at all. My companies’ BTC accounts have had 165300+ BTC flow thru them in the last 4 years, to give a sense of volume)
Full ACK!
But: “There is no glory in prevention” …
Prevention does cost money.
That must be taken from the profit of the shareholders – NoGo. 🙁
Isn’t the risk to this approach (assuming it’s effectively enforced), though, that you create an incentive for ransomware gangs to only target “life and limb” services like healthcare and critical infrastructure, because that’s where the ransom will be paid?
At this juncture in time, I would hope a small doctor’s office has: (1) its patient’s information encrypted so even if it is exfiltrated it is of little use and (2) an encrypted back up of its patients records that are not connected to any network.
My wife has a private practice and this is exactly how we protect her patient’s information. It took me five minutes to teach my wife how to use Veracrypt. Now encryption protection is just part of the daily routine.
IIRC the prosecution is only if you pay your ransom to an organization that is based in a nation on a sanction list.
I think it is pretty complicated because of things like your small example. You can even be a large company, do things right, and still get pwned.
I do think that there should be more done though in preventing ransom paying depending on loads of variables. Illegal to pay to have your exfiltrated data “deleted”. A structure of some sort might be better especially if it involves keeping a business alive vs just trying to get the last 3 days of email back. So depending on the incident you can pay and be ok legally, some cases flat out illegal, or some cases you can pay if you need too but you’ll also get a fine that insurance is not allowed to pay for you.
I know a company that got ransomwared this year because they left a Windows XP VPN open to the world. It got pwned. Whether the law would allow them to pay the ransom or not would fall into this structure of legallity on if you can pay or not, but something like this 100% needs to have a fine on it and how do we determine how large this fine is. It it needs to be large enough where action will be taken to replace that XP VPN box BEFORE it gets hacked.
While it should be illegal to pay a ransom and all data breaches should be notified (GDPR style), it should also be illegal to store personal (including health) information in an unencrypted way.
Everyone would benefit from this. I do not want my random dentist/doctor to store my information in a sloppy way and risk being hacked. If that means paying for some service, then at least that part of the bill would make sense.
It is surprisingly difficult to define in law what “encrypted” means though.
For instance all data on my hard disk is encrypted with Bitlocker, but files are decrypted on the fly transparently as they are read and any changes encrypted transparently as they are written. Any software running on my PC (or even running on other computers on my network if they have access via a shared folder) can read any of those files. A lawyer would no doubt argue that the files were stored encrypted, but that wouldn’t stop ransomware reading and exfiltrating their data.
This really is the issue. HIPAA already requires encryption at rest but there are many ways to accomplish this without providing an ounce of protection against ransomware.
Another great article !
Whenever this topic comes up, everyone talks about having good backups. Backups are critical for any company, but they pose serious problems in this scenario.
Backups take a long time to run, so they typically run once per day (or less frequent in some environments).
This means you’re likely to lose the majority of a day’s work if the restore is started *immediately*, which is never done.
Restores are also very time consuming, especially when the admins have to manually run individual restores to each system.
Desktops/laptops (the things typically hit first with ransomware) are *not* backed up in most environments.
There is a much better solution, and it’s something I’ve used at home and at work for well over a decade.
ZFS with rolling snapshots (and home dirs mounted from the server). This is such an elegant solution, it’s mindblowing that Ellison never bothered marketing ZFS appliances (which they do still make) as an answer to this problem.
The rolling snapshot retention I use is (basically the defaults):
4x “frequent” snapshots taken every 15 minutes
24x hourly snapshots
7x daily snapshots
4x weekly snapshots
12x monthly snapshots
(snapshots older than the above are automatically deleted in the config I use)
This means that I can limit my losses to *under 15 minutes* if I catch it quickly enough. Snapshots are immutable too, so can’t be deleted or overwritten by a client machine.
You can recover an entire snapshot with a one-line command on the server, or you can find the version of an individual file you want by navigating the hidden .zfs directory under the mount-point and copying the files needed from the client or the server side.
Yes, I personally run Solaris on my servers (home and work), but ZFS is also available (and stable) for Illumos (FKA:OpenSolaris), BSD Unix, and Linux, so free options are available. At least the Solaris/Illumos versions directly support SMB (at the kernel level), while Linux and BSD versions can be shared via Samba, so ZFS can be used to back a fileserver for Windows clients just as easily as an NFS server for *nix clients.
True, this doesn’t address the data exposure issue, but as the article states, there is no way to actually address that. My intent is to show there’s a significantly easier and faster way to recover files than via backups, whether corrupted, encrypted, or deleted, and the user can retrieve the files for themselves.
(I was a the backup guy for the engineering network of a Fortune 100 company back in the ’90s, so I know the pain of dealing with backups)
No way to address the exposure problem? Why not encrypt your data? Also, is there a way to scan your snapshots with anti-malware to find the original attack package. If not – you will just be pwned again.
ZFS supports on-disk encryption.
Encrypting your data only helps on-disk though, it only protects you if your drives are physically stolen. Your data has to be decrypted to be used. If you can read it, so can malware that runs on your machine as you use it.
Aside from all that, the exposure I’m referring to in my previous comment is the same that’s being discussed in the article. Once the actors have your data, they have it, it’s exposed.
If you wish to find on-disk malware, that’s actually easier with ZFS than with a normal filesystem. You can take a snapshot to preserve the infection, roll back to recover your data, then analyse the snapshot at your leisure (since there is no mad-rush to get your systems back online). Duplicating the filesystem is trivial too using zfs send and zfs receive, so you don’t even have to analyze the malware on the same machine.
Another handy feature is ZFS diffs, which will show everything that changed between snapshots. This dramatically reduces the amount of data you have to sift through.
I just realized it may not be obvious, snapshots can be accessed just like any other filesystem data, so anything that can search for malware on a filesystem can search the snapshots.
All that said, if you’re looking at the filesystem, you’re likely not finding the infection vector. Looking at the filesystem will likely (if you’re lucky) only expose the payload. I say “if you’re lucky” as more and more malware authors are moving to diskless/ram-based infections that never show up in a filesystem. To analyze those requires a memory dump and something like volatility (cross-platform memory analysis package).
The primary infection package is typically cleaned up long before the ransomware takes over. If the timing is right (and not infected then cleaned between snapshots), you still might be lucky and be able to find the initial package in an earlier snapshot. You’ll likely have to go back weeks to months to find it though.
oh I see the latest growing fields of the modern era
I’m sure developers are learning all the classic lessons and are writing increasingly bug-free code, like the good folks at Microsoft.
/s
goverment should have some good relationship with crypto excnhgers and making like 2% year contract wich goes to criminals out side of usa !
yes you think its expesnive but at the end it will be a lot more cheaper !
instead of putting danger the people lives and so just make contract with mob pay your bitcoins and everybody happy.
Yeah right lol, “pay the mob and they’ll stop stealing” – derp?
Read the article for a change. It’s dumb AF.
To suggest that… is to miss the entire point of this article.
If businesses took the proper safety precautions and trained their employees properly, and invested in backups and encryption, they’d be in a much better position. The thing is that most companies don’t want to be proactive because they think it’ll never happen to them until it does, and then they are reactive, and it costs them 10x more to fix.
I also became victim of the famous WannaCry Ransomware back in 2017 and lost a lot of Data.
Its also the Great way to hide taxes for business.
Just send yourself ransome e-mail buy Some btc.
Cash out abroad and done no taxes just claim You payed ransome lol
You may have heard, South American retail giant CENCOSUD is being hit by Egregor right now…