Authorities across Europe on Tuesday said they’d seized control over Emotet, a prolific malware strain and cybercrime-as-service operation. Investigators say the action could help quarantine more than a million Microsoft Windows systems currently compromised with malware tied to Emotet infections.
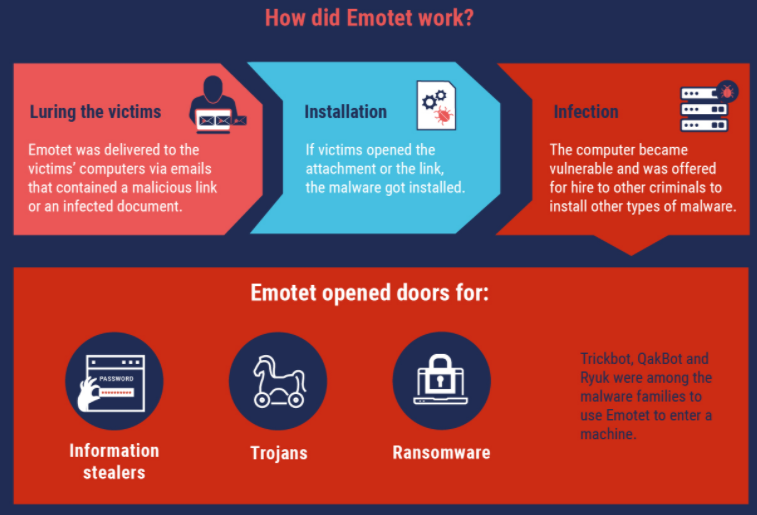
First surfacing in 2014, Emotet began as a banking trojan, but over the years it has evolved into one of the more aggressive platforms for spreading malware that lays the groundwork for ransomware attacks.
In a statement published Wednesday morning on an action dubbed “Operation Ladybird,” the European police agency Europol said the investigation involved authorities in the Netherlands, Germany, United States, the United Kingdom, France, Lithuania, Canada and Ukraine.
“The EMOTET infrastructure essentially acted as a primary door opener for computer systems on a global scale,” Europol said. “Once this unauthorised access was established, these were sold to other top-level criminal groups to deploy further illicit activities such data theft and extortion through ransomware.”
Experts say Emotet is a pay-per-install botnet that is used by several distinct cybercrime groups to deploy secondary malware — most notably the ransomware strain Ryuk and Trickbot, a powerful banking trojan. It propagates mainly via malicious links and attachments sent through compromised email accounts, blasting out tens of thousands of malware-laced missives daily.
Emotet relies on several hierarchical tiers of control servers that communicate with infected systems. Those controllers coordinate the dissemination of second-stage malware and the theft of passwords and other data, and their distributed nature is designed to make the crimeware infrastructure more difficult to dismantle or commandeer.
In a separate statement on the malware takeover, the Dutch National police said two of the three primary servers were located in the Netherlands.
“A software update is placed on the Dutch central servers for all infected computer systems,” the Dutch authorities wrote. “All infected computer systems will automatically retrieve the update there, after which the Emotet infection will be quarantined. Simultaneous action in all the countries concerned was necessary to be able to effectively dismantle the network and thwart any reconstruction.”
A statement from the German Federal Criminal Police Office about their participation in Operation Ladybird said prosecutors seized 17 servers in Germany that acted as Emotet controllers.
“As part of this investigation, various servers were initially identified in Germany with which the malicious software is distributed and the victim systems are monitored and controlled using encrypted communication,” the German police said.
Sources close to the investigation told KrebsOnSecurity the law enforcement action included the arrest of several suspects in Europe thought to be connected to the crimeware gang. The core group of criminals behind Emotet are widely considered to be operating out of Russia.
A statement by the National Police of Ukraine says two citizens of Ukraine were identified “who ensured the proper functioning of the infrastructure for the spread of the virus and maintained its smooth operation.”
A video released to YouTube by the NPU this morning shows authorities there raiding a residence, seizing cash and computer equipment, and what appear to be numerous large bars made of gold or perhaps silver. The Ukrainian policeman speaking in that video said the crooks behind Emotet have caused more than $2 billion in losses globally. That is almost certainly a very conservative number.

Police in the Netherlands seized huge volumes of data stolen by Emotet infections, including email addresses, usernames and passwords. A tool on the Dutch police website lets users learn if their email address has been compromised by Emotet.
But because Emotet is typically used to install additional malware that gets its hooks deeply into infected systems, cleaning up after it is going to be far more complicated and may require a complete rebuild of compromised computers.
The U.S. Cybersecurity & Infrastructure Security Agency has labeled Emotet “one of the most prevalent ongoing threats” that is difficult to combat because of its ‘worm-like’ features that enable network-wide infections.” Hence, a single Emotet infection can often lead to multiple systems on the same network getting compromised.
It is too soon to say how effective this operation has been in fully wresting control over Emotet, but a takedown of this size is a significant action.
In October, Microsoft used trademark law to disrupt the Trickbot botnet. Around the same time, the U.S. Cyber Command also took aim at Trickbot. However, neither of those actions completely dismantled the crimeware network, which remains in operation today.
Roman Hüssy, a Swiss information technology expert who maintains Feodotracker — a site that lists the location of major botnet controllers — told KrebsOnSecurity that prior to January 25, some 98 Emotet control servers were active. The site now lists 20 Emotet controllers online, although it is unclear if any of those remaining servers have been commandeered as part of the quarantine effort.
Further reading: Team Cymru on taking down Emotet




This is illuminati own thing
Regular person dont know anything.
This should be not be in the news let the mafia freemasons amd illuminati deal with own crooks inside the circle.
Regular person work hard and dont reach nowhere or maybe getting reqruited by agents like escobar and all those criminals.
Only top layer earn money
I see they are fans of Benjamin Franklin.
Is there a name for those containers of silver?
Quite embarrassing for Digital Ocean to be hosting the C&C.
Gary, as I noted in the story, a number of the Emotet controllers were commandeered in order to send infected systems into a quarantine effort. That effort can’t continue if all of the control servers are taken offline. That said, we don’t know yet which and/or how many of the 20 control servers still listed by Feodotracker and elsewhere are malicious vs. benign/helpful.
My mistake. My eyes naturally zoomed in on the bad IP space as soon as I saw it. I bet Hetzner is not benign. Contabo is also on my bock list. But if you read the various web hosting forums there are plenty of people that claim to be kicked off Hetzner and Contabo for terms of service violations or no reason at all.
Note I have two droplets on Digital Ocean. I block their IP space as well (excluding my own of course). I have seen posts on the Digital Ocean forums complaining about lifetime bans.
I think when the barrier to entry for a VPS is $3 to $5, you can’t police it at scale.
Digital Ocean hosts bad guys. If I complain to AWS about a bad actor (which happens about once a year), I get a reply within 24 hours, and no recurrences after that. If I complain to Digital Ocean about attacks (which happen nightly) they respond vaguely within a week or two. So I have all of the IP ranges of Digital Ocean I know about blocked.
Operating out if russia ?
T be honest real russian are drunk and drinking vodka.
The russian natural resources are stolen and locals drunk of vodka
That tool on the Dutch police site is very useful for individuals. For those of us managing large businesses, is there any way check for all email addresses belonging to an entire domain? e.g. https://haveibeenpwned.com/DomainSearch equivalent
I assume there isn’t at this point. Here is hoping this comment is noticed and someone provides this service. On the off chance there is, I hope someone lets me know.
Tried the testing at https://www.politie.nl/themas/controleer-of-mijn-inloggegevens-zijn-gestolen.html and my email looks good – use google translate ofor text ” Wij zoeken nu of uw e-mailadres voorkomt in de inbeslaggenomen data” = “We are now looking to see if your e-mail address is included in the seized data “
“It propagates mainly via malicious links and attachments sent through … email”
That is really a sad statement on the current state of email spam filtering. Infected attachment tricks have been around for years, yet spam filters are still not catching them? Millions of emails sent with the a shady domain name link and spam filters are still not catching them?
I understand the difficulty of catching phishing emails, especially spear phishing, but I thought there was decent spam filtering for malicious links and attachments. I guess not.
…a link created a minute ago has no history of being a spammer…
…polymorphic malware in an attachment has a similar issue, no signature…
…two or three layers of anit-spam a/v, etc., gets maybe 85%…
…the rest is training…
A url can be included in a new email that points to a benign landing page, so when it’s scanned by the filters it comes back as clean. A few minutes after the spam campaign is sent using that url, the attacker can modify the landing page or replace the file with a malicious file that uses the same file name / url. That is how you can create a malware threat that is weaponized post-delivery. Build some simple software to automate this, use multiple free OneDrive or Google drive stores and you can rotate quickly through the urls. This is why industry’s filters will never be 100% effective 100% of the time. Advanced capabilities like Url rewriting with click isolation, and post delivery sandbox checks can help stop these attacks. Filters using reputation and signatures only leave gaps.
…yep, that’s another way of evading filters, and stopping them, but no way is 100% so training will always be needed…
Why so many Digital Ocean entries. Though that list shows the host IP address, where is the actual VM host physically located? I bet it’s not at the geolocation of the host IP address.
Lots of stuff comes up on the logs that originates in a VM that maps to either Digital Ocean or GoDaddy. That is why we so need to be done with 47 U.S. Code § 230. If they were liable for the content of their servers, I’m sure they would police user activity better, and less spam, malware, CP, etc…
Thanks to now being compromised in multiple breaches, including one from my ISP itself, my main email account (with my ISP and which I’ve protected with 2FA), my account is now like a honey pot.
Some months I get hundreds of spoofed phishing emails, of criminally reprogrammed login pages of every company you can imagine, but mostly Amazon, Paypal, Chase and other financial institutions.
I’ve been forwarding the spoofed phish-bait to the respective companies and to reportphishing@apwg.org with the assumption that each of the source account/address is being neutralized.
Striking thing to note for me is that almost 50% of these messages are originating from funky subdomains created on wix.com
godaddy is pretty close behind.
Appears to me that these two outfits have no protections on their systems for preventing bots from creating malicious subdomains.
Seems like these companies have figured out a way to stash a few million in a bank account and just pay a parking ticket, if found liable for anything, than spending the lot more that’d be needed to prevent their systems from being attractive launch pads for criminal use.
That tool on the Dutch police site is very useful for individuals.
Hey, tracking capabilities are rated at 3.5. But enough thanks for sharing.
Avanan email platform hands down the best protection for email.
I support to Europol say “The EMOTET infrastructure essentially acted as a primary door opener for computer systems on a global scale,”. Yes, good people of the Windows world, it’s time once again to backup and patch up!