Monthly Archives: March 2021
Phish Leads to Breach at Calif. State Controller
A phishing attack last week gave attackers access to email and files at the California State Controller’s Office (SCO), an agency responsible for handling more than $100 billion in public funds each year. The phishers had access for more than 24 hours, and sources tell KrebsOnSecurity the intruders used that time to steal Social Security numbers and sensitive files on thousands of state workers, and to send targeted phishing messages to at least 9,000 other workers and their contacts.
RedTorch Formed from Ashes of Norse Corp.
Remember Norse Corp., the company behind the interactive “pew-pew” cyber attack map shown in the image blow? Norse imploded rather suddenly in 2016 following a series of managerial missteps and funding debacles. Now, the founders of Norse have launched a new company with a somewhat different vision: RedTorch, which for the past two years has marketed a mix of services to high end celebrity clients, including spying and anti-spying tools and services.
Fintech Giant Fiserv Used Unclaimed Domain
If you sell Web-based software for a living and ship code that references an unregistered domain name, you are asking for trouble. But when the same mistake is made by a Fortune 500 company, the results can range from costly to disastrous. Here’s the story of one such goof committed by Fiserv [NASDAQ:FISV], a $6 billion firm that provides online banking software and other technology solutions to thousands of financial institutions.
Can We Stop Pretending SMS Is Secure Now?
SMS text messages were already the weakest link securing just about anything online, mainly because there are tens of thousands of people (many of them low-paid mobile store employees) who can be tricked or bribed into swapping control over a mobile phone number to someone else. Now we’re learning about an entire ecosystem of companies that anyone could use to silently intercept text messages intended for other mobile users.
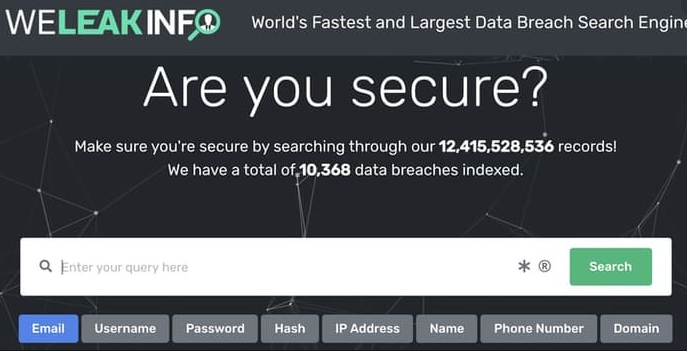
WeLeakInfo Leaked Customer Payment Info
A little over a year ago, the FBI and law enforcement partners overseas seized WeLeakInfo[.]com, a wildly popular service that sold access to more than 12 billion usernames and passwords stolen from thousands of hacked websites. In an ironic turn of events, a lapsed domain registration tied to WeLeakInfo let someone plunder and publish account data for 23,000 people who paid to access the service with a credit card.
Microsoft Patch Tuesday, March 2021 Edition
On the off chance you were looking for more security to-dos from Microsoft today…the company released software updates to plug more than 82 security flaws in Windows and other supported software. Ten of these earned Microsoft’s “critical” rating, meaning they can be exploited by malware or miscreants with little or no help from users.
Warning the World of a Ticking Time Bomb
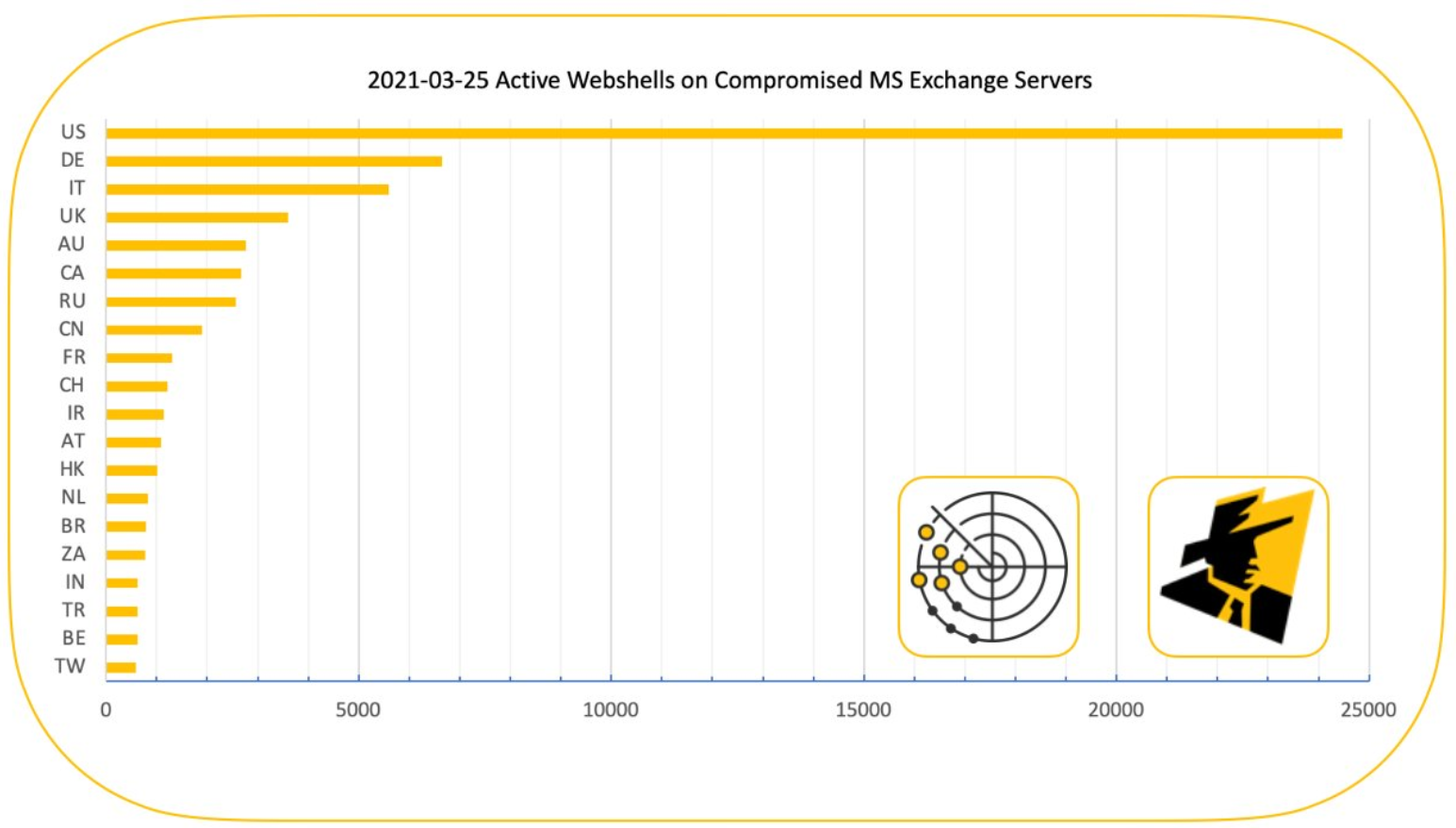
Globally, hundreds of thousand of organizations running Exchange email servers from Microsoft just got mass-hacked, including at least 30,000 victims in the United States. Each hacked server has been retrofitted with a “web shell” backdoor that gives the bad guys total, remote control, the ability to read all email, and easy access to the victim’s other computers. Researchers are now racing to identify, alert and help victims, and hopefully prevent further mayhem.
A Basic Timeline of the Exchange Mass-Hack
Sometimes when a complex story takes us by surprise or knocks us back on our heels, it pays to revisit the events in a somewhat linear fashion. Here’s a brief timeline of what we know leading up to last week’s mass-hack, when hundreds of thousands of Microsoft Exchange Server systems got compromised and seeded with a powerful backdoor Trojan horse program.
At Least 30,000 U.S. Organizations Newly Hacked Via Holes in Microsoft’s Email Software
At least 30,000 organizations across the United States — including a significant number of small businesses, towns, cities and local governments — have over the past few days been hacked by an unusually aggressive Chinese cyber espionage unit that’s focused on stealing email from victim organizations, multiple sources tell KrebsOnSecurity. The espionage group is exploiting four newly-discovered flaws in Microsoft Exchange Server email software, and has seeded hundreds of thousands of victim organizations worldwide with tools that give the attackers total, remote control over affected systems.