At least 30,000 organizations across the United States — including a significant number of small businesses, towns, cities and local governments — have over the past few days been hacked by an unusually aggressive Chinese cyber espionage unit that’s focused on stealing email from victim organizations, multiple sources tell KrebsOnSecurity. The espionage group is exploiting four newly-discovered flaws in Microsoft Exchange Server email software, and has seeded hundreds of thousands of victim organizations worldwide with tools that give the attackers total, remote control over affected systems.

On March 2, Microsoft released emergency security updates to plug four security holes in Exchange Server versions 2013 through 2019 that hackers were actively using to siphon email communications from Internet-facing systems running Exchange.
Microsoft said the Exchange flaws are being targeted by a previously unidentified Chinese hacking crew it dubbed “Hafnium,” and said the group had been conducting targeted attacks on email systems used by a range of industry sectors, including infectious disease researchers, law firms, higher education institutions, defense contractors, policy think tanks, and NGOs.
In the three days since then, security experts say the same Chinese cyber espionage group has dramatically stepped up attacks on any vulnerable, unpatched Exchange servers worldwide.
In each incident, the intruders have left behind a “web shell,” an easy-to-use, password-protected hacking tool that can be accessed over the Internet from any browser. The web shell gives the attackers administrative access to the victim’s computer servers.
Speaking on condition of anonymity, two cybersecurity experts who’ve briefed U.S. national security advisors on the attack told KrebsOnSecurity the Chinese hacking group thought to be responsible has seized control over “hundreds of thousands” of Microsoft Exchange Servers worldwide — with each victim system representing approximately one organization that uses Exchange to process email.
Microsoft’s initial advisory about the Exchange flaws credited Reston, Va. based Volexity for reporting the vulnerabilities. Volexity President Steven Adair said the company first saw attackers quietly exploiting the Exchange bugs on Jan. 6, 2021, a day when most of the world was glued to television coverage of the riot at the U.S. Capitol.
But Adair said that over the past few days the hacking group has shifted into high gear, moving quickly to scan the Internet for Exchange servers that weren’t yet protected by the security updates Microsoft released Tuesday.
“We’ve worked on dozens of cases so far where web shells were put on the victim system back on Feb. 28 [before Microsoft announced its patches], all the way up to today,” Adair said. “Even if you patched the same day Microsoft published its patches, there’s still a high chance there is a web shell on your server. The truth is, if you’re running Exchange and you haven’t patched this yet, there’s a very high chance that your organization is already compromised.”
Reached for comment, Microsoft said it is working closely with the U.S. Cybersecurity & Infrastructure Security Agency (CISA), other government agencies, and security companies, to ensure it is providing the best possible guidance and mitigation for its customers.
“The best protection is to apply updates as soon as possible across all impacted systems,” a Microsoft spokesperson said in a written statement. “We continue to help customers by providing additional investigation and mitigation guidance. Impacted customers should contact our support teams for additional help and resources.”
Meanwhile, CISA has issued an emergency directive ordering all federal civilian departments and agencies running vulnerable Microsoft Exchange servers to either update the software or disconnect the products from their networks.
Adair said he’s fielded dozens of calls today from state and local government agencies that have identified the backdoors in their Exchange servers and are pleading for help. The trouble is, patching the flaws only blocks the four different ways the hackers are using to get in. But it does nothing to undo the damage that may already have been done.
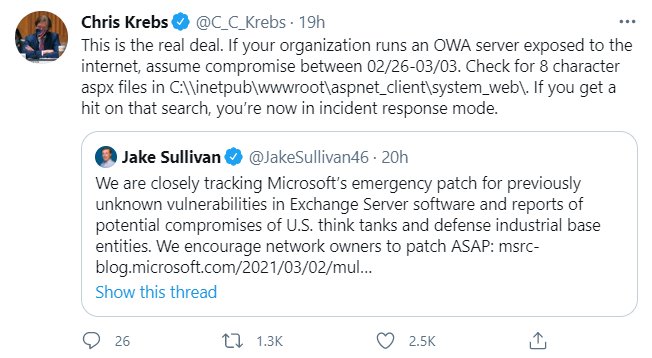
A tweet from Chris Krebs, former director of the Cybersecurity & Infrastructure Security Agency, responding to a tweet from White House National Security Advisor Jake Sullivan.
White House press secretary Jen Psaki told reporters today the vulnerabilities found in Microsoft’s widely used Exchange servers were “significant,” and “could have far-reaching impacts.”
“We’re concerned that there are a large number of victims,” Psaki said.
By all accounts, rooting out these intruders is going to require an unprecedented and urgent nationwide clean-up effort. Adair and others say they’re worried that the longer it takes for victims to remove the backdoors, the more likely it is that the intruders will follow up by installing additional backdoors, and perhaps broadening the attack to include other portions of the victim’s network infrastructure.
Security researchers have published several tools for detecting vulnerable servers. One of those tools, a script from Microsoft’s Kevin Beaumont, is available from Github.
KrebsOnSecurity has seen portions of a victim list compiled by running such a tool, and it is not a pretty picture. The backdoor web shell is verifiably present on the networks of thousands of U.S. organizations, including banks, credit unions, non-profits, telecommunications providers, public utilities and police, fire and rescue units.
“It’s police departments, hospitals, tons of city and state governments and credit unions,” said one source who’s working closely with federal officials on the matter. “Just about everyone who’s running self-hosted Outlook Web Access and wasn’t patched as of a few days ago got hit with a zero-day attack.”
Another government cybersecurity expert who participated in a recent call with multiple stakeholders impacted by this hacking spree worries the cleanup effort required is going to be Herculean.
“On the call, many questions were from school districts or local governments that all need help,” the source said, speaking on condition they were not identified by name. “If these numbers are in the tens of thousands, how does incident response get done? There are just not enough incident response teams out there to do that quickly.”
When it released patches for the four Exchange Server flaws on Tuesday, Microsoft emphasized that the vulnerability did not affect customers running its Exchange Online service (Microsoft’s cloud-hosted email for businesses). But sources say the vast majority of the organizations victimized so far are running some form of Internet-facing Microsoft Outlook Web Access (OWA) email systems in tandem with Exchange servers internally.
“It’s a question worth asking, what’s Microsoft’s recommendation going to be?,” the government cybersecurity expert said. “They’ll say ‘Patch, but it’s better to go to the cloud.’ But how are they securing their non-cloud products? Letting them wither on the vine.”
The government cybersecurity expert said this most recent round of attacks is uncharacteristic of the kinds of nation-state level hacking typically attributed to China, which tends to be fairly focused on compromising specific strategic targets.
“Its reckless,” the source said. “It seems out of character for Chinese state actors to be this indiscriminate.”
Microsoft has said the incursions by Hafnium on vulnerable Exchange servers are in no way connected to the separate SolarWinds-related attacks, in which a suspected Russian intelligence group installed backdoors in network management software used by more than 18,000 organizations.
“We continue to see no evidence that the actor behind SolarWinds discovered or exploited any vulnerability in Microsoft products and services,” the company said.
Nevertheless, the events of the past few days may well end up far eclipsing the damage done by the SolarWinds intruders.
This is a fast-moving story, and likely will be updated multiple times throughout the day. Stay tuned.
Update, 8:27 p.m. ET: Wired cybersecurity reporter Andy Greenberg has confirmed hearing the same number of victim numbers cited in this report: “It’s massive. Absolutely massive,” one former national security official with knowledge of the investigation told WIRED. “We’re talking thousands of servers compromised per hour, globally.” Read Greenberg’s account here.
Also, the first and former director of CISA, Chris Krebs (no relation) seems to be suggesting on Twitter that the victim numbers cited here are conservative (or just outdated already):
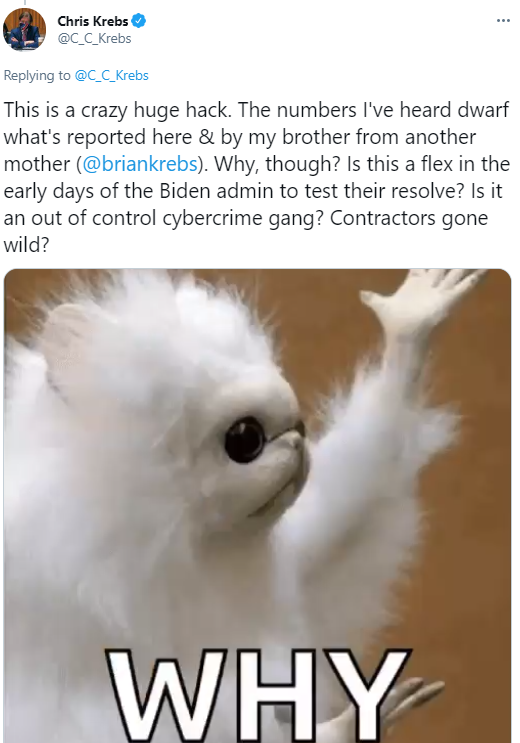
Update 8:49 p.m. ET: Included a link to one of the more recommended tools for finding systems vulnerable to this attack.
Update, 10:17 p.m. ET: Added mention from Reuters story, which said White House officials are concerned about “a large number of victims.”
Update, March 6, 10:56 a.m. ET: CISA’s Twitter account says the agency “is aware of widespread domestic and international exploitation of Microsoft Exchange Server vulnerabilities and urges scanning Exchange Server logs with Microsoft’s detection tool to help determine compromise.”
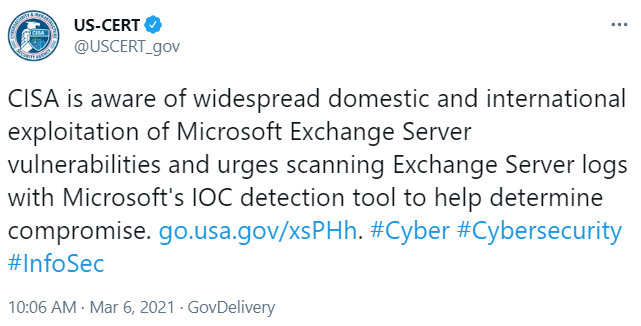
A tweet today from the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
Further Reading:




So are subscribers to Microsoft 365, formerly Office 365, affected if they use the Exchange SAS offering including OWA and/or desktop Outlook (with or without custom domain)?
Answering to my own question.
“The zero-days recently exploited include CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065. Microsoft urges customers to update their on-premises systems with the patches “immediately” and says these flaws affect Microsoft Exchange Server versions 2013, 2016, and 2019. Exchange Online is not affected.”
This is truly alarming! Thanks for your work, Brian.
Regards,
Good job sharing this with us. Now it’s time to fix those vulnerabilities.
Once compromised, how do we evict the threat actor?
I understand that installing the patches is recommended, however https://msrc-blog.microsoft.com/2021/03/05/microsoft-exchange-server-vulnerabilities-mitigations-march-2021/ clearly states “This will not evict an adversary who has already compromised a server.”
the same thing you would do any other time your server is compromised? If you’re not familiar with removing attackers from your network, your question is beyond the scope here.
The appropriate response is to wipe the hard drive, reinstall your server OS, and restore from known good backups. Then look at every other machine on your system with a very paranoid eye. This isn’t a run-of-the-mill malware campaign, it’s an actual state actor.
How do we remove the threat actor after patches are installed?
https://msrc-blog.microsoft.com/2021/03/05/microsoft-exchange-server-vulnerabilities-mitigations-march-2021/ Clearly states, “This will not evict an adversary who has already compromised a server.”
Not be a jerk or blithe, but if you’re asking this question, it’s too late. You need to hire an incident response firm. Trying to figure out how to do incident response in the middle of an incident isn’t a recipe for success.
Your best bet is to hire a company that specializes in incident response. And then once this fire is put out, devote significant resources to creating incident response capabilities in-house.
This is 100% true. IR, and DF that goes along with it, is a specialized capability. IF you don’t have a plan for IR it’s too late.
Everyone’s asking this question. It is a “0-day” attack.
Important question: Is that really only Hafnium or also ransomware gangs which will soon start their usual business model?
Why would Hafnium exploit the same server multiple times: https://twitter.com/GossiTheDog/status/1368247470761852933
Sightings of mimikatz and cobalt strike: https://twitter.com/_johnhammond/status/1368111199733374978
Microsoft is working with the Chicoms to destroy America.
Big TECH is approved by Congress.
Big Congress is OWNED>
Too bad we see all your moves.
I wish someone other than Koch funders would own Marsha Blackburn. That woman needs cybersecurity training.
No one of any reputation would support guns for hire like that.
Training money would be wasted. Mercenary talking heads will say whatever you pay them to say.
That’s quite a leap, considering that this is a global hack with no specific target and behavior uncharacteristic of a nation-state threat. You can keep your conspiracy theories – I’ll rely on hard work.
Of course. We only assume that when it appears to be Russian. Not Chinese.
Yes Ham, my Q-brother!
Big Dairy is also working to put us tasty sandwich items together on a toasted grain with EVIL CONDIMENTS. Big Mustard is surely in on the deal, to profit from us!
IT’S CRAZY
ROFL …
LOL
He may be crazy but he’s not wrong. Government can’t censor people, but Big Tech can, so big Tech has been doing things on behalf of our government. Were you awake in the months leading up to the election and after?
You can laugh at crazy people, but it’s not helpful. He’s not at all crazy, just lacking eloquence.
The New World Order is out in the open. It’s true that it was foil-hat “conspiritard” stuff up to 2019, but today I am amazed to find that they call themselves that, now, in the open. Most of it comes from Switzerland, not just Davos, but Sankt Gallen Mafia, and, of course, the Bank of International Settlements in Basel.
Maybe you should read more books instead of laughing online at people. Even chemtrails are almost vindicated in 2021, as it has come out that Bill Gates sponsors weather control. It sounds crazy, but search-engine it, and come to your own conclusions.
Honestly, in my view, you sound like the nut, not that guy, because it is clear to me that you didn’t read any good books in 2020 or 2021 for that matter. That guy you’re laughing at has a much better understanding of what’s happening in our civilization, sir.
Can someone explain why:
“Its reckless,” the source said. “It seems out of character for Chinese state actors to be this indiscriminate.”
…There are no consequences for hackers in China or Russia or ( you name a country which doesn’t respect laws and ethics.) Their governments would probably give them a bonus.
Generally they perform targeted high value attacks.
While they do that, they can claim it’s a fair spy-v-spy thing.
Attacking random civilians is the equivalent of an army switching from attacking military leaders to attacking random civilians, it’s considered a war crime and would generally result in an escalation.
While one plays spy-v-spy, the consequences are generally just to other spies.
There’s no evidence (from any organization you can trust) it was a Chinese state actor. By this time, it should be clear that attribution is a failed endeavor – many cyber state actors can spoof anything.
This was publicized by Taiwanese cyber sleuths in December 2020.
This was another Microsoft failure. They happen.
Saying that something is out of character for a certain organization isn’t definitively saying it was that organization.
In fact, it half suggests, “maybe it was some other organization that is known to behave this way”.
If you see a Swan and it Quacks, maybe it’s a Duck. And there’s certainly limited harm in considering the possibility. Just give it some space, because, if your wrong, it might bite you (Swans do this).
Something that is often underappreciated is the precision behind state sponsored APTs. They are not spraying and praying, they are clinically precise.
The more victims you have, the more likely you are to be found. A state sponsored attack would have relatively little to gain from attacking everyone and everything they can get their hands on.
Because they are acting for those governments. Same reason NSA hackers are not punished by the US Government when they hack other countries. That’s what they were told to do.
Peak navel gazing, American-style: “Volexity President Steven Adair said the company first saw attackers quietly exploiting the Exchange bugs on Jan. 6, 2021, a day when most of the world was glued to television coverage of the riot at the U.S. Capitol”.
“Volexity President Steven Adair said the company first saw attackers quietly exploiting the Exchange bugs on Jan. 6, 2021,” What did Mr. Adair DO about it though? Why is it now two months later and the world is in rubble on the ground? These are question about which we must think. If Mr Adair told Microsoft and Microsoft just sat back and let this happen, then to Microsoft we must turn for funding to fix issue. If Mr Adair did not, then must he pay?
Throw in a good gaslight with our enterprise level massive Chinese hacking report
I have as a best practice used ip address and domain restrictions in iis to lockdown the ecp folder to internal ips only on servers that publish on the internet, does this prevent the vulnerability?
Not at all. You also need to block /owa and /oab at the very least.
2 things;
I wonder when the MS Cloud/Azure is being breached big time … what is your opinion – never, soon or already?
I wonder when organisations learn not to:
… standardize and uniform their infrastructure,
… stop listening to big-tech and “how great they are”
… stop spending money for non-working pain relief
and start,
… transforming their infrastructure
… dump VPN, x.509, PIM/PAM, IAM, DLP, CASB etc. and other compromizable technologies and start implementing Sw. Def. Perimeter on layer 7, with SASE and Zero-Trust eXtended capabilities – and trunk all traffic through something like ZafePass – a solution connecting users with resources, services and applications – and the best part …. its designed with security first principles – you don’t need to add anything – just click and work. Easy and convenient.
– wonder when they to transform
This an advert then?
Not an ad . . . just someone regurgitating a bunch of buzz-words to make people think he knows what he’s talking about!!
This is by far the best comment posting i have read on that subject so far, and very true!
Thanks for the adivce!
This is by far the best comment posting i have read on that subject so far, and very true!
Thanks for the adivce!
When you design in backdoors for the alphabet organizations this is what happens when someone else finds the backdoor. More reasons for open source.
When are there going to be any kind of consequences for this or the solar winds hack? Government and private sector consequences. Right now it seems as if there are none.
Let me Google that for you:
https://www.google.com/search?client=firefox-b-1-e&q=biden+sanction+russia+solarwinds
Every story on this I’ve read states that it’s U.S. companies under attack. Since I’m not in the U.S., I am not too worried.
This is hitting Exchange servers all over the world. It doesn’t matter if you are outside of the US, you still need to respond to this urgently.
Not sure if you are trolling or not, but if I were you I would be very worried, we detected reconnaissance from one of the identified IP’s of these threat actors all the way down here in South Africa. We patched promptly but these guys were already ahead of the game before Microsoft rolled out the patch. If I were you I would jump on this as if you were already compromised and then determine if you are indeed safe….
Just checked back and saw this. Yikes. I will get onto it asap. Thanks.
Shame on Krebs to give the impression that this was only an issue for US companies. Typical US-centric-ness of narrow minded Americans…
How do you figure that? This is from the second sentence of the first paragraph of the story:
“The espionage group is exploiting four newly-discovered flaws in Microsoft Exchange Server email software, and has seeded hundreds of thousands of victim organizations worldwide with tools that give the attackers total, remote control over affected systems.”
“In the three days since then, security experts say the same Chinese cyber espionage group has dramatically stepped up attacks on any vulnerable, unpatched Exchange servers worldwide.”
“Speaking on condition of anonymity, two cybersecurity experts who’ve briefed U.S. national security advisors on the attack told KrebsOnSecurity the Chinese hacking group thought to be responsible has seized control over “hundreds of thousands” of Microsoft Exchange Servers worldwide — with each victim system representing approximately one organization that uses Exchange to process email.”
Says three times in a row that this is a global problem.
This hack must have been going on for longer.
I had a machine that got hacked with the Webshell on August 10, 2020 in a Firefox window to read mail on ms exchange.
I suspected that they had also installed a WebWorker in order to push command messages, and control all traffic to the ms exchange.
Good article except for the 8 character part. There are other files too, and they aren’t all 8 characters. Just looking for 8 characters isn’t enough, you need to look for reverse shells on Exchange. https://us-cert.cisa.gov/ncas/alerts/aa21-062a
I am sorry if this sounds stupid, I don’t know much about the field of CyberSecurity.
I fit the bill when it comes to on Device Outlook but from all the articles I have read say that there is nothing to do but download the update.
I have updated the Outlook client but can’t find anything when it comes to checking if I have been hit by the hack.
What should I do?
(P.S. I use outlook for personal reasons, not business. Does this effect anything?)
The hack was for on-prem Exchange Server. It has absolutely nothing to do with Outlook. Unless you are hosting your own email server in your garage, then this is completely irrelevant to your situation.
When making the comment
“The government cybersecurity expert said this most recent round of attacks is uncharacteristic of the kinds of nation-state level hacking typically attributed to China, which tends to be fairly focused on compromising specific strategic targets.”
Has anyone considered that this might not be the main show, that it could just as easily be a distraction from something bigger.
Microsoft SCAM to get businesses to move to a hosted solution! If they can scare 30,000+ companies and potentially hundreds of thousands of users – they stand to make a HUGE amount of money!
Not a big fan of conspiracy theories, but when will Microsoft or other big tech companies start to take responsibility for their crappy products?
This will cost businesses billions in time, resources and money to fix this!!!
MicroSHAFT is the DEVIL!!
Just wanna thank my helper SNOWHACKINGKING. I would have been homeless by now due to my bad credit score but thanks to him i now have a home. You can contact him for any issues that has to do with credit card or hacking at SNOWHACKINGKING at GMAIL dot COM Or text/call him on 2 6 7 2 0 9 0 3 6 7. Yes i can vouch for him. He is real and affordable.
Those who do not subscribe to their corporate emails etc being in the cloud are NOT withering on the vine!
My exchange server is nice and clean. I watch my router logs daily. Thank you Netgear. Even though Microsoft does not recommend blocking IPs with the firewall, which I can’t believe I read, I block by IP range or address, depends, the bad guys with both IIS and the firewall. I patch, I install the CUs, I look at my event logs etc.
I saw someone hitting my server with the script. I saw the IP and knew they were blocked.
I do not want Exchange Online. Online did not get hacked this time. There is no guarantee it won’t be vulnerable with the next one.
My 2 cents.
Why hasn’t Microsoft been on the news APOLOGIZING ON THEIR HANDS AND KNEES!
Truly unbelievable!
Starting Monday, 3/8 our Outlook (Office 365) is sending 10MB emails.
Last week they were usually KB sized.
1, 2, 3, 4. I declare a cyber war. Seriously, though. Why haven’t we declared war on China? Maybe maybe we will when they launch a virus that infects both humans AND information systems.
This is 100% true. IR, and DF that goes along with it, is a specialized capability. IF you don’t have a plan for IR it’s too late.
Please on French
Cordialement
If my bank was affected, could my money be stolen?
If Yahoo was affected, can personal computers with Yahoo accounts who do not use Exchange be impacted?
Why have we not heard from Microsoft personally.? How do we fix this?
Is anyone working on a solution? When will the company contact we the consumers!