Millions of U.S. government employees and contractors have been issued a secure smart ID card that enables physical access to buildings and controlled spaces, and provides access to government computer networks and systems at the cardholder’s appropriate security level. But many government employees aren’t issued an approved card reader device that lets them use these cards at home or remotely, and so turn to low-cost readers they find online. What could go wrong? Here’s one example.

A sample Common Access Card (CAC). Image: Cac.mil.
KrebsOnSecurity recently heard from a reader — we’ll call him “Mark” because he wasn’t authorized to speak to the press — who works in IT for a major government defense contractor and was issued a Personal Identity Verification (PIV) government smart card designed for civilian employees. Not having a smart card reader at home and lacking any obvious guidance from his co-workers on how to get one, Mark opted to purchase a $15 reader from Amazon that said it was made to handle U.S. government smart cards.
The USB-based device Mark settled on is the first result that currently comes up one when searches on Amazon.com for “PIV card reader.” The card reader Mark bought was sold by a company called Saicoo, whose sponsored Amazon listing advertises a “DOD Military USB Common Access Card (CAC) Reader” and has more than 11,700 mostly positive ratings.
The Common Access Card (CAC) is the standard identification for active duty uniformed service personnel, selected reserve, DoD civilian employees, and eligible contractor personnel. It is the principal card used to enable physical access to buildings and controlled spaces, and provides access to DoD computer networks and systems.
Mark said when he received the reader and plugged it into his Windows 10 PC, the operating system complained that the device’s hardware drivers weren’t functioning properly. Windows suggested consulting the vendor’s website for newer drivers.
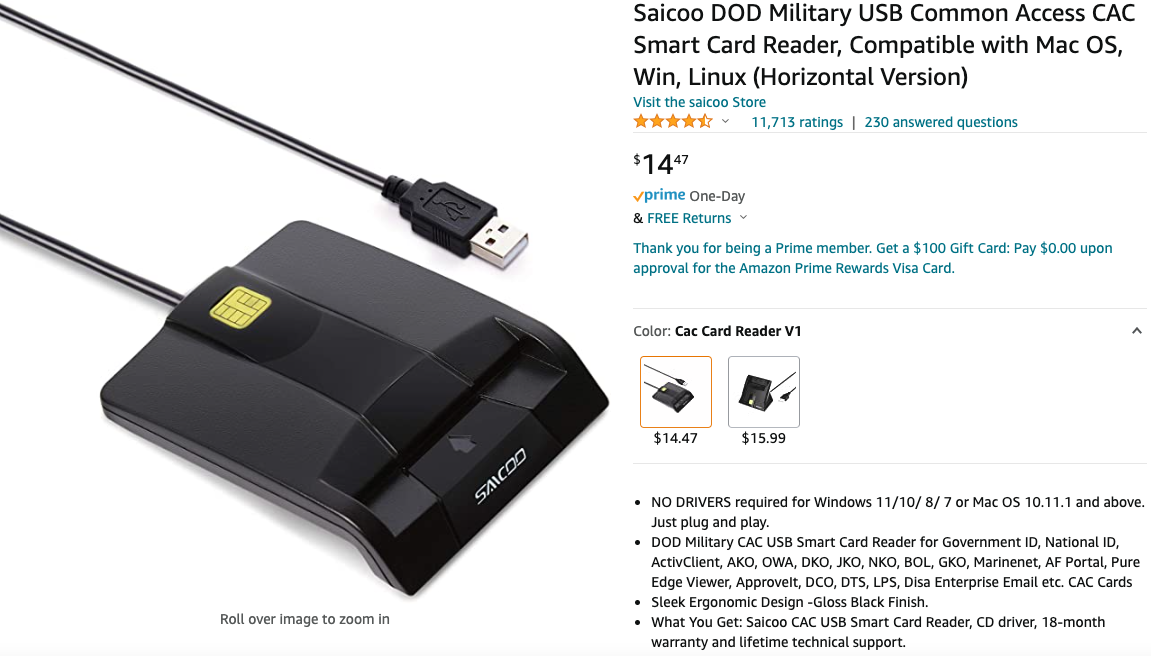
The Saicoo smart card reader that Mark purchased. Image: Amazon.com
So Mark went to the website mentioned on Saicoo’s packaging and found a ZIP file containing drivers for Linux, Mac OS and Windows:
Image: Saicoo
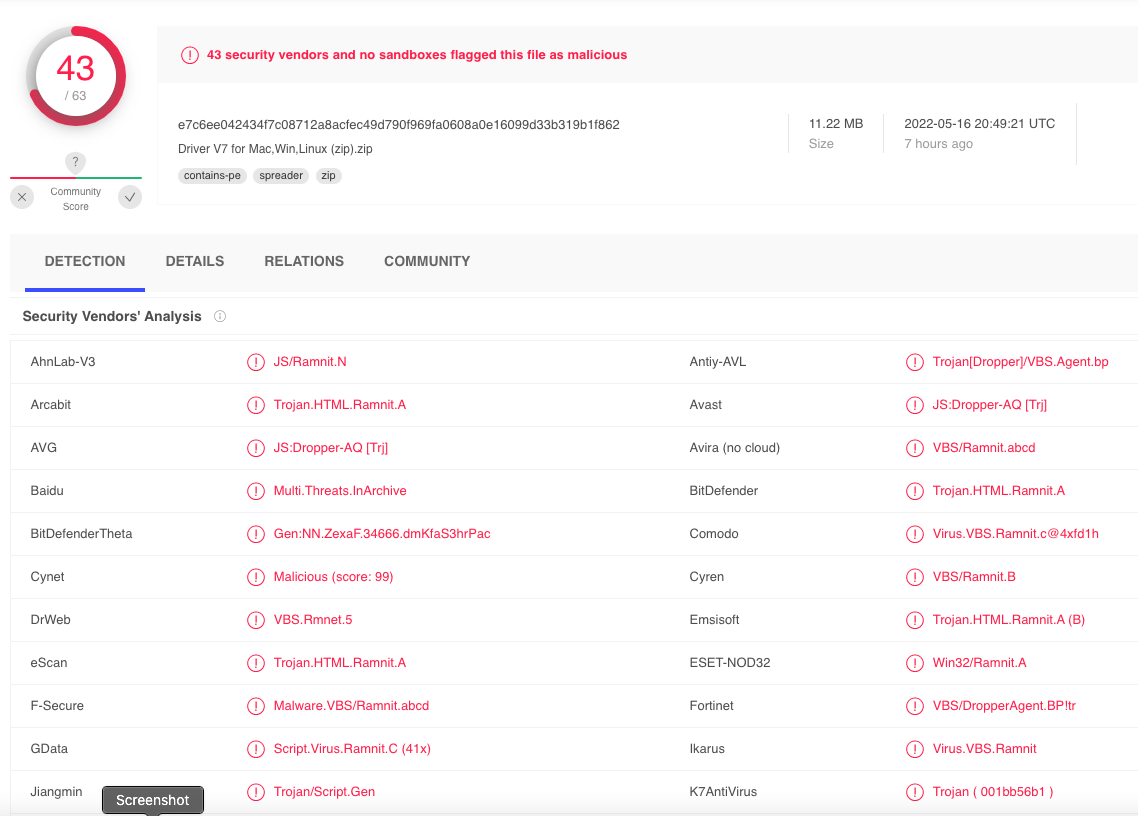
Out of an abundance of caution, Mark submitted Saicoo’s drivers file to Virustotal.com, which simultaneously scans any shared files with more than five dozen antivirus and security products. Virustotal reported that some 43 different security tools detected the Saicoo drivers as malicious. The consensus seems to be that the ZIP file currently harbors a malware threat known as Ramnit, a fairly common but dangerous trojan horse that spreads by appending itself to other files.
Ramnit is a well-known and older threat — first surfacing more than a decade ago — but it has evolved over the years and is still employed in more sophisticated data exfiltration attacks. Amazon said in a written statement that it was investigating the reports.
“Seems like a potentially significant national security risk, considering that many end users might have elevated clearance levels who are using PIV cards for secure access,” Mark said.
Mark said he contacted Saicoo about their website serving up malware, and received a response saying the company’s newest hardware did not require any additional drivers. He said Saicoo did not address his concern that the driver package on its website was bundled with malware.
In response to KrebsOnSecurity’s request for comment, Saicoo sent a somewhat less reassuring reply.
“From the details you offered, issue may probably caused by your computer security defense system as it seems not recognized our rarely used driver & detected it as malicious or a virus,” Saicoo’s support team wrote in an email.
“Actually, it’s not carrying any virus as you can trust us, if you have our reader on hand, please just ignore it and continue the installation steps,” the message continued. “When driver installed, this message will vanish out of sight. Don’t worry.”
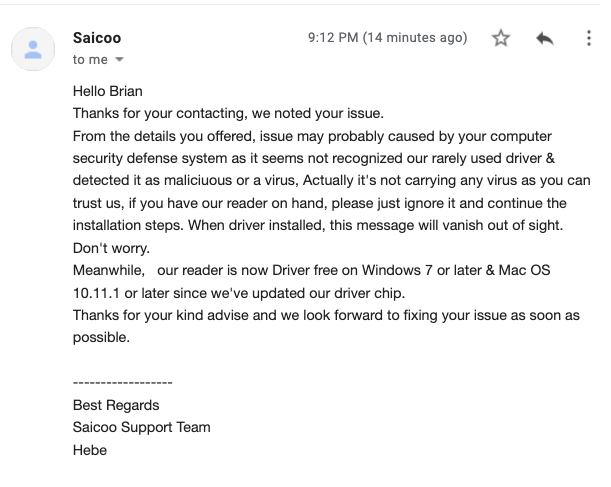
Saicoo’s response to KrebsOnSecurity.
The trouble with Saicoo’s apparently infected drivers may be little more than a case of a technology company having their site hacked and responding poorly. Will Dormann, a vulnerability analyst at CERT/CC, wrote on Twitter that the executable files (.exe) in the Saicoo drivers ZIP file were not altered by the Ramnit malware — only the included HTML files.
Dormann said it’s bad enough that searching for device drivers online is one of the riskiest activities one can undertake online.
“Doing a web search for drivers is a VERY dangerous (in terms of legit/malicious hit ratio) search to perform, based on results of any time I’ve tried to do it,” Dormann added. “Combine that with the apparent due diligence of the vendor outlined here, and well, it ain’t a pretty picture.”
But by all accounts, the potential attack surface here is enormous, as many federal employees clearly will purchase these readers from a myriad of online vendors when the need arises. Saicoo’s product listings, for example, are replete with comments from customers who self-state that they work at a federal agency (and several who reported problems installing drivers).
A thread about Mark’s experience on Twitter generated a strong response from some of my followers, many of whom apparently work for the U.S. government in some capacity and have government-issued CAC or PIV cards.
Two things emerged clearly from that conversation. The first was general confusion about whether the U.S. government has any sort of list of approved vendors. It does. The General Services Administration (GSA), the agency which handles procurement for federal civilian agencies, maintains a list of approved card reader vendors at idmanagement.gov (Saicoo is not on that list). [Thanks to @MetaBiometrics and @shugenja for the link!]
The other theme that ran through the Twitter discussion was the reality that many people find buying off-the-shelf readers more expedient than going through the GSA’s official procurement process, whether it’s because they were never issued one or the reader they were using simply no longer worked or was lost and they needed another one quickly.
“Almost every officer and NCO [non-commissioned officer] I know in the Reserve Component has a CAC reader they bought because they had to get to their DOD email at home and they’ve never been issued a laptop or a CAC reader,” said David Dixon, an Army veteran and author who lives in Northern Virginia. “When your boss tells you to check your email at home and you’re in the National Guard and you live 2 hours from the nearest [non-classified military network installation], what do you think is going to happen?”
Interestingly, anyone asking on Twitter about how to navigate purchasing the right smart card reader and getting it all to work properly is invariably steered toward militarycac.com. The website is maintained by Michael Danberry, a decorated and retired Army veteran who launched the site in 2008 (its text and link-heavy design very much takes one back to that era of the Internet and webpages in general). His site has even been officially recommended by the Army (PDF). Mark shared emails showing Saicoo itself recommends militarycac.com.

Image: Militarycac.com.
“The Army Reserve started using CAC logon in May 2006,” Danberry wrote on his “About” page. “I [once again] became the ‘Go to guy’ for my Army Reserve Center and Minnesota. I thought Why stop there? I could use my website and knowledge of CAC and share it with you.”
Danberry did not respond to requests for an interview — no doubt because he’s busy doing tech support for the federal government. The friendly message on Danberry’s voicemail instructs support-needing callers to leave detailed information about the issue they’re having with CAC/PIV card readers.
Dixon said Danberry has “done more to keep the Army running and connected than all the G6s [Army Chief Information Officers] put together.”
In many ways, Mr. Danberry is the equivalent of that little known software developer whose tiny open-sourced code project ends up becoming widely adopted and eventually folded into the fabric of the Internet. I wonder if he ever imagined 15 years ago that his website would one day become “critical infrastructure” for Uncle Sam?




Very interesting reading, as usual. Thank you for the information.
For those needing to know, you should only ever use a TAA (United States Trade Agreements Act (TAA) of 1979) compliant CAC/Smart Card Reader. This is pretty common knowledge within the Defense IT area, in which I work as a contractor.
It really should be provided by the unit/org/agency. They have cheap foldable ones i got a while ago. They are smaller than a bic lighter. I don’t think i paid for it. The cost is really much less than the actual card.
Between the incredible possibilities for security breaches described here and the Capitol Hill hearings on UFOs/UAPs
I think this is worth considering:
“After one look at this planet, any vistor from outer space would say, `I want to see the manager.'”
—- William S. Burroughs
So who’s at fault here? Seems article blames all parties involved, including the end users.
Saicoo blamed the end user in their response to his inquiry, stating that it was the end user’s antivirus that gave a false positive on the drivers. In fact, the user put it in VirusTotal and it had nothing to do with his drivers. The people at fault are Saicoo either for 1) leaving their site vulnerable enough for malware to be implanted and 2) not noticing it at any point.
Chief Danberry is a colleague of mine. Same rank and same job. It’s a small world that you are writing about him. He’s been an inspiration for the Signal Warrant cohort. Holding it all together with spit and bailing wire.
We’ve only gotten more reliant on CAC authentication since moving to milCloud SaaS services. Reserve component forces just don’t get the hardware issued like active component does.
Reserve unit admins often fail their members. They should be buying card readers in bulk (cheap).
US: Spent billions to bring on secure and smart card system for federal employees.
China: Let’s supply them with card readers so cheap they won’t refuse!
In fact any unvetted distributor is suspect. An Amazon listing for a TAA-compliant device could actually be a counterfeit device.
Most Amazon listings for most electronics are counterfeit, it’s hard for anyone to tell a legit one from a fake, except by the price – and who pays $50 when there is the same thing for $15, and they look the same. Heck, Amazon will create clones of popular products so they can bypass their sellers and profit a few cents more. Space tourism isn’t gonna pay for iteslf.
There are reliable vendors out there. Amazon is Ebay or worse. Still…
“Mark opted to purchase $15 reader from Amazon” unknown brand is big fail #1 for sure.
“that said it was made to handle U.S. government smart cards” – raises zero red flags! XD
Government perfection doesn’t exist but they do actually make vendor equip merch lists.
If you ignore that and go with unknown brand (from xyz-ia) in a government security role,
uh, at least you probably won’t be fired the first few times you blow it hugely like this.
Good to know we have top men on the job.
“unknown brand is big fail #1 for sure”
Unfortunately the current state of Amazon seems to be a coin flip if you choose a legitimate brand, whether you will actually receive a legitimate or instead a counterfeit copy of what you bought. The retail supply chain is not a viable solution for these users for the purpose of accessing secured systems.
Certainly true and if you don’t even narrow by BRAND? What IS that?
Absolutely yes secure systems procurement is a deliberate process.
Guy didn’t even get to step one. I’m squinting just thinking about it.
The readers listed on IDmanagement.gov are for physical access control systems, not for reading smart cards on computers.
GSA no longer certifies “transparent” readers.
See 10/29/16 announcement: https://www.idmanagement.gov/sell/fipsannouncements/
Help me understand, if you will. Does this mean a “SolarWinds-like” embedded malware built-in these “Saicoo-ish” cheap Common Access Card (“CAC”) readers collects the Personal Identity Verification (“PIV”) access data from the secure cards used by the array of military, government and enterprise personnel, and then transmits that identity (credentials) to China when the reader is plugged into the USB port of any Internet-connected computer? Does that data collection defeat the security of secure facilities (government and private) everywhere? This cleverly defeats perimeter security everywhere.
No. This isn’t as bad as that nightmare scenario. The private keys on the card is still protected even if the reader is malicious. And in this case, the device itself isn’t even malicious.
The threat here is that a user may “trust” the manufacturer’s website for drivers, which is malicious in this case.
If the user does install malware, then it’s possible to infect the web browser and steal a user login session and access the Unclassified networks as that user.
I’m trying to understand the proper way to remediate this issue: does DoD need to malware scan all the laptops of those that downloaded the driver package? Does it need to assess the which of its employees’ laptops has had an incoming connection to a ramnit-initated C2 beacon?
No. Personally owned devices are not managed, or the responsibility of the government.
If someone gets hacked on their personal device, and gets their session cookies stolen, they’ll have to report it to their security manager.
The only response would be resetting accounts and terminating open sessions.
Nothing on the laptop, the user is on their own for that. Although there used to be a web portal that allows military to download free antivirus software for personal systems.
ASMO. Get a new machine when retraining is successfully completed.
DoD should be issuing readers to everyone (employees, reservists, and contractors).
Heck, they could do the entire country a favor and issue readers to *everyone* (regardless of citizenship/residency status).
The ones they issue should be supported natively by the OS and thus not require ever downloading third party drivers…
Private key should be protected, so they get the public key, as well as all the other info on the employee / card.
I am not sure how old keys/algs are in operation.
But supposedly since 2013, it should be only RSA with 2048 bit and ECDSA-256.
Card authentication can use weaker algorithms:
3TDEA + AES-128, AES-192, or AES-256
But if the chinese can somehow find a weakness in the issuing software (there have been some over time), then they can replace the private key. So while not extremely critical, it all depends on the quality of the issuing CA.
I’ve been privy to way too many smart card rollouts that are run like this, “here’s your smart card, and from here you’re on your own. Oh, and nothing will work any more unless you can get this thing working”. So in terms of assigning blame I’d say it’s squarely on the DoD IT managers who rolled out a barely-supported product, as evidence by the fact that the main “support” site for it appears to be some volunteer on a private web site.
This stuff goes back at least 25 years, I remember with the Fortezza cards (sort of precursor to the CAC) we were downloading drivers from some FTP site in Texas run by God knows who which had a good chance of blue-screening your desktop when loaded and support was essentially nonexistent. I mean, when things went wrong, there was absolutely no-one you could go to for help beyond whoever your local IT people were, and they often didn’t know any more than you did.
Ha! Fortezza! Oh, the memories of testing those in early DMS builds at JITC, Ft. H. Good times!
I worked for the DoD for nearly a decade at several agencies and locations and the one commonality was that they all told you to fend for yourself in obtaining a smart card reader for home use. Now that DoD civilians can shop at the military exchanged, they can generally pick up a safe, reliable reader at the exchange for under $20. But they shouldn’t have to foot the bill for hardware necessary to do their jobs at all. And most agencies won’t reimburse these expenses, citing them as conveniences rather than necessities. I’m thankful the civilian agencies I’ve worked for outside DoD haven’t taken that approach, pretty liberally distributing smart card readers, despite having far fewer systems requiring smart card login.
This is not as troubling as buying any USB peripheral that is infected by BADUSB (https://en.wikipedia.org/wiki/BadUSB). There are no software virus scans that can detect BADUSB and it can infect your system in seconds after being plugged in.
Most of the USB kit that I buy are now made in China – which happens to have a history of computer tricks against the US and the rest of the world.
BadUSB and OMG cables are a serious risk.
That’s what they just said.
BadUSB and OMG cables are a serious risk. But it should be understood that this particular attack is more akin to a watering hole attack, rather than an actual malicious device.
Sorry, not all government employees can shop at a local exchange. They, the exchanges are few, and far between. And all exchanges carry different stock.
But, it does raise an interesting question, why is some of the government allowing other systems on their network without proper vetting? Is it the department, the local manager, local security?
How does a new employee get the equipment to do their portion of government work? How do they find a listing of approved vendors? It does seem as if the new improved hiring system sucks.
Indeed, AAFES exchanges are not a viable option for most.
To answer your questions: These personally owned devices are not allowed “on their network”. This is simply allowing authentication to unclassified websites.
Everyone who is issued a CAC, gets issued one “in person”. Must be done at approved location by approved personnel using the approved machines to print, take photo and set the PIN. That is probably the best time to give them a card reader too. If the issuing agency doesn’t want to budget for card readers, they should also be directing to approved vendors.
This isn’t a new hiring system, this is at least 20 years old.
That’s a simplistic “fix” to a much bigger problem if pers machines compromised.
Anyone who buys $15 readers off amazon for nat sec access is audit ASMO ready.
This isn’t for national security. It’s for people checking their emails at home. Most don’t even have a security clearance and don’t need one.
This simplistic fix seems like the best option.
email is, yes, national security. unfortunately that’s a standard we have still.
Anyone who has been in the military a day understands that personal computers don’t connect to any classified networks used for national security.
Not everything is a matter of national security.
National Guard and Reserves need to check payroll, unclassified administrative email, etc from home. They aren’t issued laptops or card readers.
national security email is classified and thus on classified networks that are inaccessible from personal computers. its pretty clear that this discussion is only about people trying to access unclassified email that would not process national security data.
Many have pointed out the concerns of using unapproved PIV/CAC readers on government systems or for connecting from home to VPN into Govt networks. At least there is an “approved” source for these devices. A more pernicious problem is that of businesses that supply products and services to the government, or who are entrusted with government information. What controls do these business have to prevent the next “Solargate?”
It seems they took the driver download down:
https://www.saicootech.com/show-99-6-1.html
>>Dixon said Danberry has “done more to keep the Army running and connected than all the G6s [Army Chief Information Officers] put together.”
I believe it, but uhhhhh… not an encouraging state of affairs. Not at all.
Not suprising though. Warrant Officers and NCOs are the real brains and brawn, the officers exist to take the credit and the blame. The G6 is just the executive CIO, which even in the civilian world, they aren’t the ones doing the work or coming up with the plans.
Unfortunately what happened here is common:
Equipment required for the job was not supplied, the process to get the needed equipment wasn’t properly communicated (or Mark didn’t read the memo), Mark’s manager/supervisor may have incorrectly recommended Amazon. This is not isolated to government agencies, many private businesses have the same issues.
Probably most concerning is that one guy is tech support for for all of this. Again typical in many private businesses, but still concerning.
I am curious to hear what Mark did after he found the driver had malware, and whether Krebs advised him of the correct way to get a card reader.
Blue6 – Hate to call you out on this, but you’re missing the point of all the whole article. Mark is addressing the bigger risk to anyone who potentially buys any card reader.
This is why I’m glad my company, years ago, got wise and deployed peripheral vending machines on their campuses. Need a new mouse? Just wave your employee badge at the vending machine and voila! Need speakers, keyboard, card reader, docking station? Got you covered! No need to go through the standard logistics red tape nightmare of who will fund your 20$ purchase, where you’ll be allowed to even purchase it from and you can avoid all the paperwork and labor hours which will cost 10x what the final product costs. “Keep It Simple Stupid” saves the day, some dollars and averts security risks too!
Might work for Silicon Valley, but not government. And certainly not military.
They have to account for and control who might have access to these unsupervised vending machines that unwitting service members could use to start plugging into their laptops.
It’s a common attack to sprinkle USB drives containing malware in a parking lot based on the probability someone with use it. A vending machine for government employees is the perfect target for foreign espionage.
That reminds me of the other big security violation involving vendors just outside the base, selling bootleg DVDs. Guess what, they were also rampant with early malware. We were instructed to never stick those into any computer and to only use standalone DVD players.
Many of the companies in Silicon Valley are also a target for foreign espionage. They have to account for and control who might have access just the same. Not every employee of a Silicon Valley company is security-wise, not by a long shot. In ways it’s more of a risk in Silicon Valley because you can be sure that *every* employee is for example, checking a work email.
It’s interesting that they didn’t instruct you to stop breaking the law, just to do it more carefully…
Very true. Silicon Valley or any private company could be a target. It’s a bad idea all around to use vending machines like that.
The real simple solution would be to have the same office that is issuing badges, also issue card readers. That’s how we did it.
In fairness, this was in countries that did not follow DMCA or other copyright laws. A legal gray area to be sure. Even it were breaking the law, nobody enforced such things on deployment. And even if they wanted to instruct a ban, it would be like a church instructing celibacy but still advocating the use of condoms if you do it anyway.
There are ways to get a derived PIV/CAC certificate on your personal and mobile device and use that instead of a personally owned card reader.
No. The “certificate” that can be exported to be stored on the personal or mobile device will never contain the private key. That cert is simply not capable of doing any authentication or digital signing.
The private key is essentially stored in write-only media on the chip, and cannot be read / copied (without a scanning electron microscope).
If what you say were possible, it would defeat the purpose of a smart card.
They can hijack any open session. Absolutes aren’t.
what are you talking about? there is no “session” between the card and computer that can be “hijacked”. this is basic cyber security principles
Yeah it’s basic. If you don’t know what is being referred to by “session” just keep quiet.
youre making things up. the cryptography used in smart cards / CACs don’t establish any kind of “session”. you are just trying to sound smart and hoping nobody calls you out on your bs.
Should be easy to prove, by providing one example of such a hack.
Ring up about 4 levels and try again.
If you’re looking for a cheap and trustworthy smart card reader, the classic Identiv SCR3310 is the way to go.
It’s only about $15, a name brand, and reliable
The Navy doesn’t indorse Militarycac.com, Mr. Danberry reached out to us many years ago for specific information to add to his site. We denied that request, yes he has some good information but not all are correct.
As for card readers yes DoD does have a list of approved tested readers, that doesn’t mean those are the only ones that work with the CAC or PIV (FED). Navy use to provided and may still provided readers at no cost to their reservist.
However, each service has it’s own PKI office that can advise any Member or contactor on what is recommended not required.
There is a Navy page on his site. Each service does not need to endorse militarycac specifically. 99% of the content is general and for any/all DOD.
There is actually very little service specific information on that website. Generally, consists of links to the service’s websites for more information. This is a courtesy because many of the links that would contain up-to-date information, requires a working CAC anyway.
With office hours only available from 1100-1130 on a Tuesday by appointment only, as is the way. The Army used to have a good support page on setting up your CAC too… but the page required a CAC login.
I agree that it’s much better if these resources are provided by the services themselves, but it’s very difficult for the end user to find them and even S6 shops aren’t always aware of them
“Ramnit is a well-known and older threat — first surfacing more than a decade ago”
See this is why I don’t hook my “smart TV’s” up to the internet. Vendors are so lazy about updating their firmware and software to the highest standards. If this company was doing it right, they would have modern, up-to-date malware in their drivers instead of lazily using a decade old version of malware.
Attempt at gallows humor intentional.
It should be understood that this particular attack is more akin to a watering hole attack, rather than an actual malicious device.
With a watering hole serving up malware, there’s no need for phishing, no need to actually encode malware into a physical device.
Driver errors in windows are pretty common and if the user just googles the manufacturer’s website and trusts it, they are bound to fall for a watering hole attack.
Stop making excuses.
Interesting that Reserve members are allowed/forced to read mission-critical email on privately owned hardware. Even the non-DOD agency I worked for prior to retirement required the use of a government-issued laptop for off-site email access, c. 2018.
Watch out the email snapshot has the guy’s real name
Do you mean the guy who runs the website perhaps? Brian Krebs.
Great article
I used to support a 3 letter government agency and we provided readers for home use to anyone that stopped by to ask for one. We kept a large stock, to give out to people I myself working in IT and Procurement would look for a CAC that was TAA compliant and MilitaryCAC would be my choice of where to look.
People are forgetting their could be malware in the firmware of the reader too much like a card skimmer at a gas station only built into the reader!.
Malicious firmware in any USB device would be really bad. Mostly because it could potentially act as a BadUSB keyboard and auto-type into your system to download and execute more malware.
Malicious firmware in a smart card reader can also try to steal your PIN, or cause a DOS attack by locking the card with multiple PIN failures.
But it cannot really act as a “card skimmer” that reads static data, sends to attackers, which can then replay the data.
Chip and PIN (EMV) is protects against card skimmers in a similar way, but performing the cryptography functions on the card itself, so it’s not possible to steal the keys even if the reader is fully compromised.
They can hijack an open session and do anything at all Corporal Excuses.
Thanks Mealy. I see you are learning from my previous comments to Robin about session hijacking. Good to know you are reading all my comments and still cyber stalking me.
In this case, malicious card reader firmware would not be the malware that could steal the session. That would have to inject into the browser. And it certainly does not act as a card skimmer.
I hope you keep reading about cyber security and keep learning. Maybe one day you’ll be able to contribute something to the community instead of trolling people.
Thanks Mealy. I see you are learning from my previous comments to Robin about session hijacking. Good to know you are reading all my comments and still cyber stalking me. 🙂
In this case, malicious card reader firmware would not be the malware that could steal the session. That would have to inject malicious code into the browser first. And it certainly does not act as a card skimmer.
I hope you keep reading about cyber security and keep learning. Maybe one day you’ll be able to contribute something to the community instead of being just a contrarian.
As somebody who has done this dance since it started, I am nodding my head in agreement to all of this. The sketch hardware and drivers… Having to explain to my coworkers that this not (dot)mil address is the most authoritative site on CAC issues….”trust me…I swear!”.
I really appreciate you sharing the approved list and will be sharing that information with people I know along with this story. It hits close to home.
This is the tip of the iceberg. When I was at USCIS, the SolarWinds machine was slowing our network down so much that we had to disconnect it. The Russians were looking at everything, especially email. It’s a wonder that the Russians don’t cause the US to nuke itself.