The United Kingdom’s National Crime Agency (NCA) has been busy setting up phony DDoS-for-hire websites that seek to collect information on users, remind them that launching DDoS attacks is illegal, and generally increase the level of paranoia for people looking to hire such services.
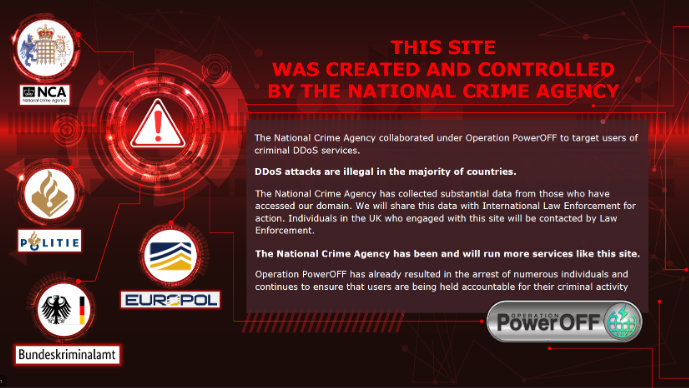
The warning displayed to users on one of the NCA’s fake booter sites. Image: NCA.
The NCA says all of its fake so-called “booter” or “stresser” sites — which have so far been accessed by several thousand people — have been created to look like they offer the tools and services that enable cyber criminals to execute these attacks.
“However, after users register, rather than being given access to cyber crime tools, their data is collated by investigators,” reads an NCA advisory on the program. “Users based in the UK will be contacted by the National Crime Agency or police and warned about engaging in cyber crime. Information relating to those based overseas is being passed to international law enforcement.”
The NCA declined to say how many phony booter sites it had set up, or for how long they have been running. The NCA says hiring or launching attacks designed to knock websites or users offline is punishable in the UK under the Computer Misuse Act 1990.
“Going forward, people who wish to use these services can’t be sure who is actually behind them, so why take the risk?” the NCA announcement continues.
The NCA campaign comes closely on the heels of an international law enforcement takedown involving four-dozen websites that made powerful DDoS attacks a point-and-click operation.
In mid-December 2022, the U.S. Department of Justice (DOJ) announced “Operation Power Off,” which seized four-dozen booter business domains responsible for more than 30 million DDoS attacks, and charged six U.S. men with computer crimes related to their alleged ownership of popular DDoS-for-hire services. In connection with that operation, the NCA also arrested an 18-year-old man suspected of running one of the sites.
According to U.S. federal prosecutors, the use of booter and stresser services to conduct attacks is punishable under both wire fraud laws and the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in arrest and prosecution, the seizure of computers or other electronics, as well as prison sentences and a penalty or fine.
The United Kingdom, which has been battling its fair share of domestic booter bosses, started running online ads in 2020 aimed at young people who search the Web for booter services.
As part of last year’s mass booter site takedown, the FBI and the Netherlands Police joined the NCA in announcing they are running targeted placement ads to steer those searching for booter services toward a website detailing the potential legal risks of hiring an online attack.




The handful of people who don’t use a throwaway email or a VPN/Proxy/TOR when signing up to these type of sites will just learn they should have and know for their next attempt.
The other 90% of users will not be contactable and will continue as always.
A lot of effort by the authorities which will achieve very little.
yeah, this seems stupid. Agreed.
I agree this won’t stop a motivated attacker. The paranoia factor though is interesting. If I put myself in the attackers shoes I might be thinking, “I’m alright if I just use fake information, VPN, proxy, etc”, but maybe there is a seed of doubt in the back of their mind. Maybe they did capture some legitimate information…the psychological element is pretty strong.
I agree that most people will use a throwaway email or whatever, but I still think this is a reasonable tactic. I suspect it’s actually _not_ a lot of effort by the authorities to set these sites up (and move them to new addresses when they become “known”), and the payoff is increased friction when it comes to buying booter services. For muddying the waters and increasing paranoia, they’re perfect. Will it solve the problem? No. But it isn’t intended to. A perfect project for a summer intern.
“A lot of effort by the authorities which will achieve very little”
Security Theater?
No it us not stupid because it gets the amatures out if hiring these dogs. Next step is to punish and ban from the Internet the use of throw away emails
By the way the Internet grew out of a US Taxpayer funded effort called ARPANET and I watched the Internet come into existence. Just like on national and international highways we have strong enforcement, the same needs to go for the Internet. I do not want to live in a world ruled by anarchy but a world ruled by responsible nation states.
I like my throw away emails, thanks. Tired of having my information leaked or sold and getting my inbox spammed with copious amounts of nonsense.
I too watched – and assisted – the current internet come into being, from the early 70’s DARPANET to the mess it is now. “Responsible nation states?” You’re more likely to find King Solomon’s mines or the Loch Ness monster. Anarchy may be chaos, but it definitely forces people to be kind to one another – because if you aren’t you get your just deserts.
I would much rather the governments of the world not interfere in the internet, however it seems that modern people are stupid and have no sense of security or self-preservation, no inkling of what technology does to them or their lives, the latest generation being the worst. Perhaps being coddled from cradle to grave by Big Brother is the only thing that will save us, God help us if that’s the case.
Curmudgeon? Luddite? Maybe, but only after seeing what has become of the good works of people like Vint Cerf and Tim Berners-Lee.
“Anarchy may be chaos, but it definitely forces people to be kind to one another – because if you aren’t you get your just deserts.”
That NRA, ‘Wild West was peaceful’, Might = Right nonsense mentally never works. It just breeds strongmen, mob bosses, gang leaders, and dictators who take over. We’ve tried self governance anarchy and then lawlessness allowed more crime, not polite behavior.
The Internet is the wild west. Where anyone can be pseudo anonymous. Draconian regulations aren’t the answer, but neither is deregulation anarchy. There must be a middle ground.
The key word here being “responsible”.
I see no responsible nation-state actor. Or any state-level actor I would name responsible.
Any serious criminal isn’t the target of this campaign and most of them wouldn’t use a DDoS 3rd party if they wanted to execute a plan that was more complicated than “irritate the blogger/politician/journalist/X I don’t like”
What the NCA have done here is maybe gotten rid of some, maybe a lot of, casuals. And to be honest, I think that’s a win.
Most of their users are probably kids wanting to impress their friends. If they’d had caught actual criminals blackmailing companies that would be the headline.
Anyways, isn’t it illegal for the police to offer a service like this? I remember that in some countries it’s illegal for police to try and trick drug-users into buying drugs from them.
“There is no defence of entrapment in English law” -LexisNexis
This is not in and of itself being used to prosecute anyone.
There will be bycatch but this is data collection based on illicit activity.
Further investigation of individual criminal activity takes place over time.
Less savvy users who are interested in this are meanwhile discouraged,
translating into less money for the operators and ecosystem shrinkage.
It will not “catch the ringleaders” but it may provide intel on future ones.
Once known to be interested in this illegal service their info is in the DB;
That has value even if you don’t understand exactly how it will be used,
or even if it will ever be publicly. It also doesn’t cost much to do this.
People who think it’s “stupid” are mostly under-thinking the point of it.
Also this is but one publicly known iteration of such a program.
My speculation: since there’s no prosecution (afaik), then nothing illegal about wasting wannabe criminals’ time.
In the EU, this way of collecting data would be against GDPR and therefore illegal
GDPR does not apply to government bodies and law enforcement when data are gathered and processed for the prevention, investigation, detection, or prosecution of criminal offenses or the execution of criminal penalties or for preventing threats to public safety
We’d all have less DDoS tools in the world if Cloudflare weren’t tolerated as a protection racket for them (look for “stresser” or “booter”, see how many start with a 104. IP address).
cloudflare.com/ips/ is a list of their IP ranges, also accessible by API.
How many actual booter services can you find that match up to CF IPs?
Further reading:
https://nakedsecurity.sophos.com/2023/03/28/cops-use-fake-ddos-services-to-take-aim-at-wannabe-cybercriminals/
https://en.wikipedia.org/wiki/Entrapment
Totally unethical to set up a trap website like this and investigate visitors, as if their click was evidence of crime, or even a lead to it.
This is probably passive enough that you could argue that they are not inciting a crime but merely muddying the waters, and thereby possibly preventing users from committing crimes by making them think twice. A bit like announcing the placement of speed cameras beforehand.
It won’t stop the diehards, but it may prevent some from dipping their toes into that particular swamp on the Web.
Signing up for such a service is a bit more than a click. People who sign up on a fake website offering DDoS-for-hire are very likely doing so in order to buy these services and as such are hardly victims of entrapment. After all entrapment is about making someone do something illegal that they otherwise would not have been “otherwise been unlikely or unwilling to commit” as the article states.
How about a journalist, internet security blogger or researcher signing up to the site to get an idea how they work.
Do they get put on a naughty list as potential person of interest in future hacking/extortion cases because they signed up to one of these law enforcements bogus sites?
If they sign up to pay an illegal service for any reason including “research” or “journalism” then yes, they could still be put on the same list as anyone else who doesn’t have legal authority to do that for a sanctioned investigation purpose. They could appeal to have themselves removed from it on same grounds, but if the service is illegal and you’re knowingly trying to use it for “reasons” it’s still 3/5ths of a crime. Motive and other factors would likely be determinant in whether they are ultimately charged, and with what. In this case they spell out that it’s for warning and data collection, not prosecution, but BK or anyone else could end up in this same list – that’s why ethical and responsible investigatory practices are essential when you’re delving firsthand into criminal services and sources.
Your definition of ‘ethics’ seems rather different to mine.
I disagree with your interpretation of “Entrapment”. From the URL you referenced: “Entrapment is a practice in which a law enforcement agent or agent of the state induces a person to commit a “crime” that the person would have otherwise been unlikely or unwilling to commit.”
[1] Not the same as an undercover police officers asking strangers at a club if they want to buy drugs. The person that signed up for a booter account actively sought out the booter service website and then signed up.
[2] Laws in UK might have a different interpretation of “Entrapment” then the one you are familiar with.
[3] No one said anything about prosecution of the UK persons that signed up for the booter service. “Users based in the UK will be contacted by the National Crime Agency or police and warned about engaging in cybercrime. Information relating to those based overseas is being passed to international law enforcement.” For all we know, the users might get an email from the UK police advising them that using a booter service is illegal.
This seems like a low cost, low effort way to “alert” potential users that using a booter service is illegal in the UK. A PSA if you will. Look at the press it has gotten. As other commenters have pointed out, it might stop the kids or first timers, others will just look elsewhere.
Just me
It’s not entrapment, the people who end up on these sites chose to do so. They searched for a booter, found a list of results and picked one. They could have chosen one that was real (and probably did so immediately after discovering they’ve been had) but they happened to click the “wrong” link. Additionally, they do not state that any prosecutorial action will be taken against anyone who did click. They get sent some “don’t do bad stuff” info that they won’t read and that’s that.
By the way, in the US at least, the police are legally allowed to lie to you. So there’s that as well.
Since when did something being illegal stop a government from doing it?
This seems about 10 years behind the times. Annoying hacker kidz have moved on to smoking Instagram accounts and extorting the account owners to get them put back up. They’ve also moved on to creating financial accounts in others’ names and using those for nefarious purposes. DDOS attacks are so 2013.
That’s like saying writing speeding tickets is so 1997.
I’ll refrain from Trump-themed examples.
bad question related to the Fake booter site.
If a person sets up a Fake booter/criminal site, accepts funds, but does not do any criminal work (pinged the server twice, just to say we hit it repeatedly) and stuff like that. Would LE come after me? the crooks I don’t care about.
(not that I have time for this crap, but a valid question, if the law can, can I?)
Thanks
I’m not a lawyer, but contracts for illegal activity are not enforced by the legal system.
I’m not a lawyer, but contracts for illegal activity are not enforced by the legal system.
The citizens of the UK can rest easier knowing their chances of getting booted off while playing Minecraft have decreased a whole 0.001%
Why….say….anything
It sends neophyte chatterboxes back to the monitored crime forums.
New actors will advertise there and a new round of intel is collected.
If the police rock up to Brian’s place to discuss why using a stresser is a bad idea, he can show them this blog. Likewise, a journalist can show them their press ID and the partially written article.
Both would likely get an interesting convo with the officers about what is helpful to report on and what is not, and make a contact.
(As an aside, I would assume Brian’s details are used to register an account on most of these going forwards, because that’s usually along the list of things people do for the lulz…)
Brian can show the police this blog if they come to his house to talk about why it’s not a good idea to use a stress reliever. Likewise, a journalist can show them their press ID and the partially written article.
Both would probably have an engaging conversation with the officers about what information is important to disclose and what is not, and they would establish communication.