Many things have changed since 2018, such as the names of the companies in the Fortune 100 list. But one aspect of that vaunted list that hasn’t shifted much since is that very few of these companies list any security professionals within their top executive ranks.

The next time you receive a breach notification letter that invariably says a company you trusted places a top priority on customer security and privacy, consider this: Only five of the Fortune 100 companies currently list a security professional in the executive leadership pages of their websites. This is largely unchanged from five of the Fortune 100 in 2018, the last time KrebsOnSecurity performed this analysis.
A review of the executives pages published by the 2022 list of Fortune 100 companies found only five — BestBuy, Cigna, Coca-Cola, Disney and Walmart — that listed a Chief Security Officer (CSO) or Chief Information Security Officer (CISO) in their highest corporate ranks.
One-third of last year’s Fortune 100 companies included a Chief Technology Officer (CTO) in their executive stables; 40 listed Chief Information Officer (CIO) roles, but just 21 included a Chief Risk Officer (CRO).
As I noted in 2018, this is not to say that 95 percent of the Fortune 100 companies don’t have a CISO or CSO in their employ: A review of LinkedIn suggests that most of them in fact do have people in those roles, and experts say some of the largest multinational companies will have multiple people in these positions.
But it is interesting to note which executive positions the top companies deem worth publishing in their executive leadership pages. For example, 88 percent listed a Director of Human Resources (or “Chief People Officer”), and 37 out of 100 included a Chief Marketing Officer.
Not that these roles are somehow more or less important than that of a CISO/CSO within the organization. Nor is the average pay hugely different among all these roles. Yet, considering how much marketing (think consumer/customer data) and human resources (think employee personal/financial data) are impacted by your average data breach, it’s somewhat remarkable that more companies don’t list their chief security personnel among their top ranks.
One likely explanation as to why a great many companies still don’t include their security leaders within their highest echelons is that these employees do not report directly to the company’s CEO, board of directors, or Chief Risk Officer.
The CSO or CISO position traditionally has reported to an executive in a technical role, such as the CTO or CIO. But workforce experts say placing the CISO/CSO on unequal footing with the organization’s top leaders makes it more likely that cybersecurity and risk concerns will take a backseat to initiatives designed to increase productivity and generally grow the business.
“Separation of duties is a fundamental concept of security, whether we’re talking about cyber threats, employee fraud, or physical theft,” said Tari Schreider, an analyst with Datos Insights. “But that critical separation is violated every day with the CISO or CSO reporting to the heads of technology.”
IANS, an organization geared toward CISOs/CSOs and their teams, surveyed more than 500 organizations last year and found roughly 65 percent of CISOs still report to a technical leader, such as the CTO or CIO: IANS found 46 percent of CISOs reported to a CIO, with 15 percent reporting directly to a CTO.
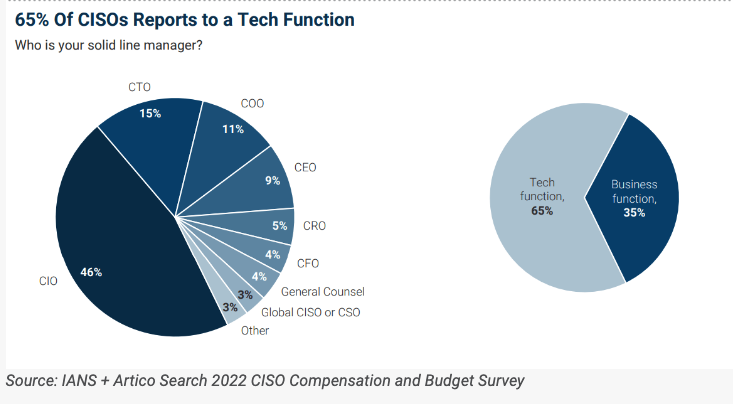
A survey last year by IANS found 65 percent of CISOs report to a tech function within organizations, such as the CTO or CIO. Image: IANS Research.
Schreider said one big reason many CISOs and CSOs aren’t listed in corporate executive biographies at major companies is that these positions often do not enjoy the same legal and insurance protections afforded to other officers within the company.
Typically, larger companies will purchase a “Directors and Officers” liability policy that covers legal expenses should one of the organization’s top executives find themselves dragged into court over some business failing on the part of their employer. But organizations that do not offer this coverage to their security leaders are unlikely to list those positions in their highest ranks, Schreider said.
“It’s frankly shocking,” Schreider said, upon hearing that only four of the Fortune 100 listed any security personnel in their top executive hierarchies. “If the company isn’t going to give them legal cover, then why give them the responsibility for security? Especially when CISOs and CSOs shouldn’t own the risk, yet the majority of them carry the mantle of responsibility and they tend to be scapegoats” when the organization eventually gets hacked, he said.
Schreider said while Datos Insights focuses mostly on the financial and insurance industries, a recent Datos survey echoes the IANS findings from last year. Datos surveyed 25 of the largest financial institutions by asset size (two of which are no longer in existence), and found just 22 percent of CSOs/CISOs reported to the CEO. A majority — 65 percent — had their CSOs/CISOs reporting to either a CTO or CIO.
“I’ve looked at these types of statistics for years and they’ve never really changed that much,” Schreider said. “The CISO or CSO is in the purview of the technical stack from a management perspective. Right, wrong or indifferent, that’s what’s happening.”
Earlier this year, IT consulting firm Accenture released results from surveying more than 3,000 respondents from 15 industries across 14 countries about their security maturity levels. Accenture found that only about one-third of the organizations they surveyed had enough security maturity under their belts to have integrated security into virtually every aspect of their businesses — and this includes having CISOs or CSOs report to someone in charge of overseeing risk for the business as a whole.
Not surprisingly, Accenture also found that only a third of respondents considered cybersecurity risk “to a great extent” when evaluating overall enterprise risk.
“This highlights there is still some way to go to make cybersecurity a proactive, strategic necessity within the business,” the report concluded.
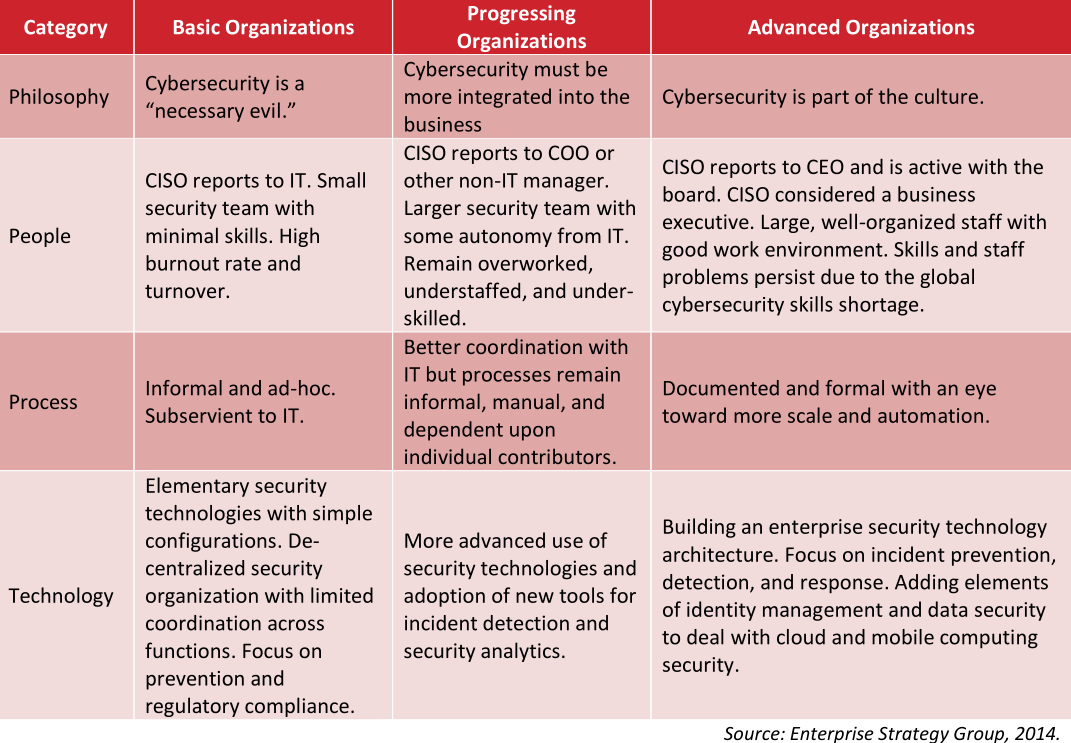
One way of depicting the different stages of security maturity.
A spreadsheet tracking the prevalence of security leaders on the executive pages of the 2022 Fortune 100 firms is available here.
Update, July 23: Somehow overlooked Disney’s CSO listed on their leadership page. The story copy above has been updated to reflect that.




Zero steps forward, one step back.
The comments included from Tari Schneider related to D&O insurance are not accurate and require fact checking. D&O insurance policies are not written to include only direct reports of the CEO. Otherwise this is a good article and agree with need for organizations to separate CISO function from CIO. They must be peers, and more importantly the CISO must have influence and build relationships with a long list of non-tech business functions. Latest Verizon DBIR shows 3 out 4 data breaches involved a human cause. CISO’s can’t make a difference when security is seen as a technology problem and the only solutions are based on technology.
Security doesn’t make money, unless that’s the business.
A sign that says, “WARNING! ELECTRIFIED FENCE!” is almost as effective as a real electric fence, and a lot cheaper. That’s why you don’t see many real electric fences in public, or many security experts in boardrooms.
True Security, isn’t a revenue generator, however a lack of Security can cost a business significantly, not limited to the potential imprisonment of Directors.
If you have something someone wants behind that fence, you can bet your house on a malicious actor testing an entry point. Controls should be commensurate to the value of the assets they protect. Whether a sign is sufficient depends on the value of what’s behind your fence….
The majority of CIOs are clueless when it comes to security but they want security under their control to elevate their status.
In my view it is good practice not provide too much information about anything security related to the public. Why should anybody know which specific person is in charge of security issues in a specific company, just makes forr example spear fishing attacks on this person more easy……
Yet the CEO and other top officers ARE disclosed – and in such cases spear-spoofing anyone at the C-level “usually” grants opportunities to move laterally and find whatever they seek… of course LinkIn/LNexus etc list who those individuals are in ~90% of cases for big companies… and to especially belabor the point, if your ‘designated top security expert’ for one of these big companies is falling on e-spears (of ANY quality level) simply due to his/her name being public, they probably/hopefully aren’t indefinitely tenured for that position.
The point of this article is that CSO’s and CISO’s are not part of the executive leadership, not that they are “less public” than the other C-levels.
Considering the LinkedIn attacks on infosec professionals of a couple of years ago, I wonder if some companies don’t list these folks as top execs to slow down script kiddies trying to do low-end social engineering attacks.
As for not including infosec people on corporate errors-and-omissions insurance policies, it means our employers don’t have our backs. See “burnout” in the maturity matrix published in the article.
Key frame here: “‘scapegoats’ when the organization eventually gets hacked, he said.” He didn’t say “if”.
I just have a feeling that companies with business in Europe (EU) or want to sell services in Eurozone are more likely than the deplorable averages seen in Krebs’s report to have more robust security protocols. Just a feeling.
Australia (234) Brazil (100) Canada (115) France (201) Germany (223) Ireland (102) Italy (200) Japan (221) Netherlands (101) Norway (100) Saudi Arabia (55) Spain (100) United Kingdom (360) United States (888)
EU makes up nearly half of the companies polled for this result.
“Our top priority is X”, where X is whatever corporate tit is presently stuck in a PR ringer.
Seems like any CFO would have a fiduciary reponsibility that extends to securing corporate financial information from both internal misappropriation and external threats. Not doing so is irresponsible or negligent. I don’t know what the national accounting standards say about protecting financial records and data.
Most of these CSOs have no idea what Cybersecurity is. Zero hands-on experience. Just got there due to good connections and not merit.
We know CISSP is just useless.
So, it really doesn’t matter whether you advertise these greenhorns on your executive profile.
May be rest of the executives may feel insulted!
The majority of CIOs are clueless when it comes to security but they want security under their control to elevate their status.
CISO’s and their teams have to constantly educate IT on Information Security.
Your comment about the CISOs is innacurate.
Might want to rephrase that sentence after the update?
“Only five of the Fortune 100 companies currently list a security professional in the executive leadership pages of their websites. This is actually down from five of the Fortune 100 in 2018, the last time KrebsOnSecurity performed this analysis.”
Down from five to five sounds weird… 😉
Otherwise, keep up the good work! 🙂
Datos surveyed 25 of the largest financial institutions by asset size (two of which are no longer in existence), and found just 22 percent of CSOs/CISOs reported to the CEO. A majority — 65 percent — had their CSOs/CISOs reporting to either a CTO or CIO.
The FFIEC Examination Handbook, Information Security, published regulatory guidance for financial institutions to segregate the CIO and CISO roles and reporting structure. However, guidance is not a regulation and does not have the effect of law.
“Information security officers should report directly to the board or senior management and have sufficient authority, stature within the organization, knowledge, background, training, and independence to perform their assigned tasks. To ensure appropriate segregation of duties, the information security officers should be independent of the IT operations staff and should not report to IT operations management.”
I hope that this report serves as a wake-up call for other companies to reevaluate their approach to cybersecurity. Let’s encourage more businesses to prioritize security, not only for their own benefit but for the greater good of the digital ecosystem we all operate within. Together, we can build a safer and more resilient online landscape for everyone.
Why are the spreadsheet percentage denominators hard-coded value of 94 rather than the total number of companies on the sheet (100)?
Interesting that there are no banks on the list. JP Morgan Chase, Bank of America, Wells Fargo, Morgan Stanley, Goldman Sachs, and USAA (!) don’t value their customer’s data that much apparently. Meta and Amazon are also in the bottom 95.
Having the CISO listed on the executive team on a web page does not mean they have been given a seat at the Board of Directors Table, even though it is a C-level position. If 65% of CISOs in the referenced survey report to CIO or CTO, the remaining, although reporting elsewhere, there are very few, if any, that sit on the Board.