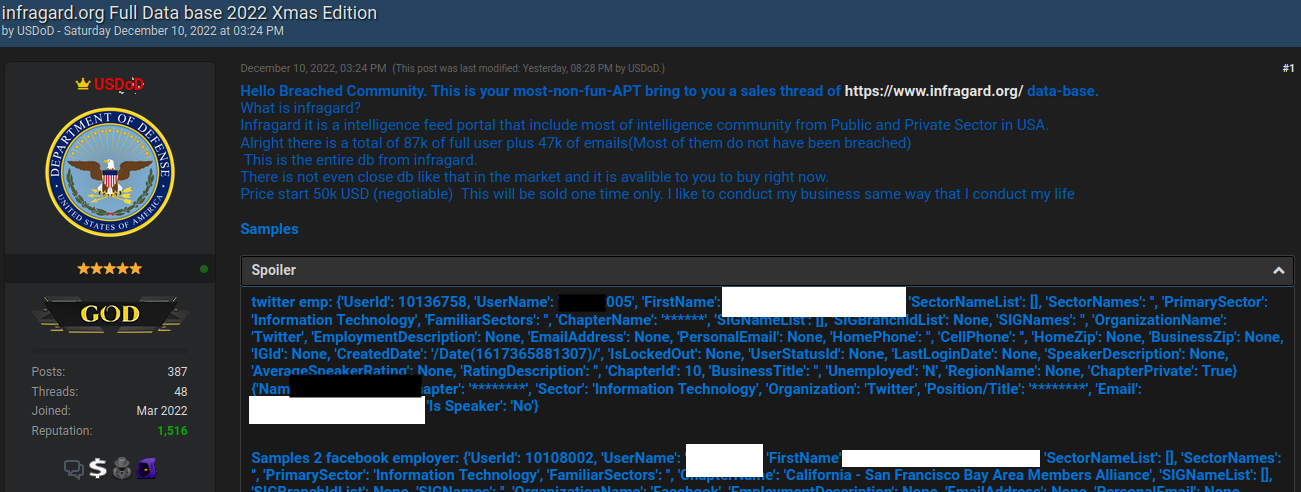
In December 2022, KrebsOnSecurity broke the news that a cybercriminal using the handle “USDoD” had infiltrated the FBI‘s vetted information sharing network InfraGard, and was selling the contact information for all 80,000 members. The FBI responded by reverifying InfraGard members and by seizing the cybercrime forum where the data was being sold. But on Sept. 11, 2023, USDoD resurfaced after a lengthy absence to leak sensitive employee data stolen from the aerospace giant Airbus, while promising to visit the same treatment on top U.S. defense contractors.
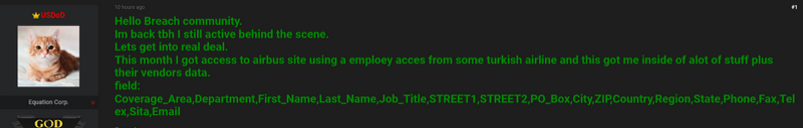
In a post on the English language cybercrime forum BreachForums, USDoD leaked information on roughly 3,200 Airbus vendors, including names, addresses, phone numbers, and email addresses. USDoD claimed they grabbed the data by using passwords stolen from a Turkish airline employee who had third-party access to Airbus’ systems.
USDoD didn’t say why they decided to leak the data on the 22nd anniversary of the 9/11 attacks, but there was definitely an aircraft theme to the message that accompanied the leak, which concluded with the words, “Lockheed martin, Raytheon and the entire defense contractos [sic], I’m coming for you [expletive].”
Airbus has apparently confirmed the cybercriminal’s account to the threat intelligence firm Hudson Rock, which determined that the Airbus credentials were stolen after a Turkish airline employee infected their computer with a prevalent and powerful info-stealing trojan called RedLine.
Info-stealers like RedLine typically are deployed via opportunistic email malware campaigns, and by secretly bundling the trojans with cracked versions of popular software titles made available online. Credentials stolen by info-stealers often end up for sale on cybercrime shops that peddle purloined passwords and authentication cookies (these logs also often show up in the malware scanning service VirusTotal).
Hudson Rock said it recovered the log files created by a RedLine infection on the Turkish airline employee’s system, and found the employee likely infected their machine after downloading pirated and secretly backdoored software for Microsoft Windows.
Hudson Rock says info-stealer infections from RedLine and a host of similar trojans have surged in recent years, and that they remain “a primary initial attack vector used by threat actors to infiltrate organizations and execute cyberattacks, including ransomware, data breaches, account overtakes, and corporate espionage.”
The prevalence of RedLine and other info-stealers means that a great many consequential security breaches begin with cybercriminals abusing stolen employee credentials. In this scenario, the attacker temporarily assumes the identity and online privileges assigned to a hacked employee, and the onus is on the employer to tell the difference.
In addition to snarfing any passwords stored on or transmitted through an infected system, info-stealers also siphon authentication cookies or tokens that allow one to remain signed-in to online services for long periods of time without having to resupply one’s password and multi-factor authentication code. By stealing these tokens, attackers can often reuse them in their own web browser, and bypass any authentication normally required for that account.
Microsoft Corp. this week acknowledged that a China-backed hacking group was able to steal one of the keys to its email kingdom that granted near-unfettered access to U.S. government inboxes. Microsoft’s detailed post-mortem cum mea culpa explained that a secret signing key was stolen from an employee in an unlucky series of unfortunate events, and thanks to TechCrunch we now know that the culprit once again was “token-stealing malware” on the employee’s system.
In April 2023, the FBI seized Genesis Market, a bustling, fully automated cybercrime store that was continuously restocked with freshly hacked passwords and authentication tokens stolen by a network of contractors who deployed RedLine and other info-stealer malware.
In March 2023, the FBI arrested and charged the alleged administrator of BreachForums (aka Breached), the same cybercrime community where USDoD leaked the Airbus data. In June 2023, the FBI seized the BreachForums domain name, but the forum has since migrated to a new domain.
Unsolicited email continues to be a huge vector for info-stealing malware, but lately the crooks behind these schemes have been gaming the search engines so that their malicious sites impersonating popular software vendors actually appear before the legitimate vendor’s website. So take special care when downloading software to ensure that you are in fact getting the program from the original, legitimate source whenever possible.
Also, unless you really know what you’re doing, please don’t download and install pirated software. Sure, the cracked program might do exactly what you expect it to do, but the chances are good that it is also laced with something nasty. And when all of your passwords are stolen and your important accounts have been hijacked or sold, you will wish you had simply paid for the real thing.




I highly doubt that is USDoD. I have talked to him on several occasions and this guy can’t spell “employee” or “access”. I know they were working on something and I highly doubt it was airbus.
They always type like that, look at breached.vc archives.
> likely infected their machine after downloading pirated and secretly backdoored software
yeah they said he downloaded pirated .NET… which is free….. that path only showed up like that because the malware or crypter is written in c# damnit
You must not know much about how process injection works if you’re confusing string and pub lib obfuscation with stub crypting.
maybe i don’t, but there is no such thing as “pirated .NET” and your comment does not invalidate my point
That’s true, it is free. The current version is 4.8.1 I believe, not 4.0…
(Or “.net 7” if you go by their alternate, confusing version numbering.)
So it’s an open question why/how this user infected themselves, if it
was actually the .net being “pirated” initially or some hijacker malware
took over .net to compile bad bins on the fly using .net or that route,
which apparently lokibot can do for one example…
(www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/analysis-abuse-of-net-features-for-compiling-malicious-programs)
Airbus wouldn’t have their information spread on the Internet if they followed best practices for authentication (2FA, reauthenticate often)
Cookies bypass 2FA. Just like how you login to certain websites, ticking “Remember Me”, after you login + provide 2FA, your account stays logged in for X period of time (sometimes 30 days, sometimes longer, sometimes infinite until cookie expiry). For example my Cloudflare and Private Email accounts stay logged in for months before, someone with my cookies could access that without any 2FA and I wouldn’t know.
There’s a lot more than just the cookie though, any modern environment you’re going to have to send the cookie, they’re going to check your IP and if you aren’t bouncing your session off of their actual IP, its likely not going to work. You also have to make sure you’ve fingerprinted them enough to where you have all of the info to send the exact user agent. Even then, the sessions might be done in such a way that its super temporary until it renews using the actual client.
You’re right. BUT Just relying on authentication isn’t sufficient in situations like that. Jonathan Care from Gartner recently put out a guide and some worksheets tailored for CISOs focusing on building effective insider threat programs. You can find it here: https://www.ekransystem.com/en/resources/white-papers/guide-n-worksheets-for-insider-threat-program. This resource comes right after his webinar, co-hosted with Ekran System, where Jonathan discussed strategies for minimizing data exfiltration. He strongly emphasizes the need for a comprehensive approach to preventing and mitigating data breaches, as opposed to just implementing scattered best practices. I’m completely on board with his perspective.
Very cool. Love to see this happening to American babykillers and their european stooges.
In Putin’s America, this would never happen. Reporting on inconvenient truths is western weakness.
In other news, two Russian warships decided to catch fire yesterday due to lack of patriotism…
Note that gross generalizations like American Baby Killers lump together large numbers of innocent people with those offenders and reflect your personal hatred.
Totally agree with Natalie. But how often and how well do our news media or even our own government nuance Russia or Iran or China? Not very?
What nuance are you seeking in reporting on those totalitarian governments without real elections? Should free media / governments just ignore the fact that all three nations are demonstrably complicit in state-backed cybercrime groups, actual terrorist groups essentially as well, or should we play the whataboutism game instead? Did you consider that none of the three you mentioned even HAVE a free press, to make such a “nuanced” ad hoc comparison? Not very indeed.
Projection much like the compromised former us president. It’s such an obvious and dumb technique but still seems to work on 30% of the USA population.
Puhleeze. The only compromised former US president is Obama. And the current US president is in the same leaky boat.
Just a thought… I reported breaches 3 years ago. They continued to refuse to investigate and I lost my house and got put in jail and everything over a thief and a liar changing my records and using my email. I would have preferred to have my money instead of someone else. FYI, I’m not in Louisiana and DOJ needs to stay off my phone and accounts SALESFORCE DO YOU HEAR ME!! I caught you on my phone and accounts. I hate Kentucky and which ever DOJ and FBI agency is responsible for participating in organized crime should have been stopped long ago. Go set someone else up for fraud and alter legal documents and steal their identity. I got my copies and they don’t match your lies.
FYI, altered legal documents to obtain someone’s property and judges and attorney’s shouldn’t participate in fraud. Torture me again in a hospital where the DOJ and KY FBI agencies give exc6auch as I can’t investigate unless the law reports it, I must allow intentional harm to continue and I’m sorry for the loss of your dad’s life but I can’t step on any toes because I’m getting my kickback from the government for the illegal placements at the hospital so that’s why we cannot afford to stop this from happening to people. The fraudulent legal documents will be acknowledged because they don’t have anyone who cares. The state makes money if you cannot pay and the Hospital makes it either way. You talk about a organized crime ring.
FYI, altered legal documents to obtain someone’s property and judges and attorney’s shouldn’t participate in fraud. Torture me again in a hospital where the DOJ and KY FBI agencies give exc6auch as I can’t investigate unless the law reports it, I must allow intentional harm to continue and I’m sorry for the loss of your dad’s life but I can’t step on any toes because I’m getting my kickback from the government for the illegal placements at the hospital so that’s why we cannot afford to stop this from happening to people. The fraudulent legal documents will be acknowledged because they don’t have anyone who cares. The state makes money if you cannot pay and the Hospital makes it either way. You talk about a organized crime ring.
“And when all of your passwords are stolen and your important accounts have been hijacked or sold, you will wish you had simply paid for the real thing.”
-Turkish Airlines
“You mean security can be layered? Explain how.”
Remember Solarwinds? That’s the type of catastrophic hack which leads into an Airbus breach. or a Microsoft breach. As far as we can tell that breach still has a long road ahead.
They’re only as strong as their weakest link. Men are known best for their errors. Even Google knows and is willing to help.
“Authentication” sounds like a straightforward exercise-to determine, to some level of assurance, that a party is entitled to a specific set of credentials (i.e., a procedure or mechanism to test an entitlement claim)-but in practice, especially for financial transactions, it is anything but.
‘https://www.interisle.net/sub/Authentication.pdf