The Chinese company in charge of handing out domain names ending in “.top” has been given until mid-August 2024 to show that it has put in place systems for managing phishing reports and suspending abusive domains, or else forfeit its license to sell domains. The warning comes amid the release of new findings that .top was the most common suffix in phishing websites over the past year, second only to domains ending in “.com.”

Image: Shutterstock.
On July 16, the Internet Corporation for Assigned Names and Numbers (ICANN) sent a letter to the owners of the .top domain registry. ICANN has filed hundreds of enforcement actions against domain registrars over the years, but in this case ICANN singled out a domain registry responsible for maintaining an entire top-level domain (TLD).
Among other reasons, the missive chided the registry for failing to respond to reports about phishing attacks involving .top domains.
“Based on the information and records gathered through several weeks, it was determined that .TOP Registry does not have a process in place to promptly, comprehensively, and reasonably investigate and act on reports of DNS Abuse,” the ICANN letter reads (PDF).
ICANN’s warning redacted the name of the recipient, but records show the .top registry is operated by a Chinese entity called Jiangsu Bangning Science & Technology Co. Ltd. Representatives for the company have not responded to requests for comment.
Domains ending in .top were represented prominently in a new phishing report released today by the Interisle Consulting Group, which sources phishing data from several places, including the Anti-Phishing Working Group (APWG), OpenPhish, PhishTank, and Spamhaus.
Interisle’s newest study examined nearly two million phishing attacks in the last year, and found that phishing sites accounted for more than four percent of all new .top domains between May 2023 and April 2024. Interisle said .top has roughly 2.76 million domains in its stable, and that more than 117,000 of those were phishing sites in the past year.
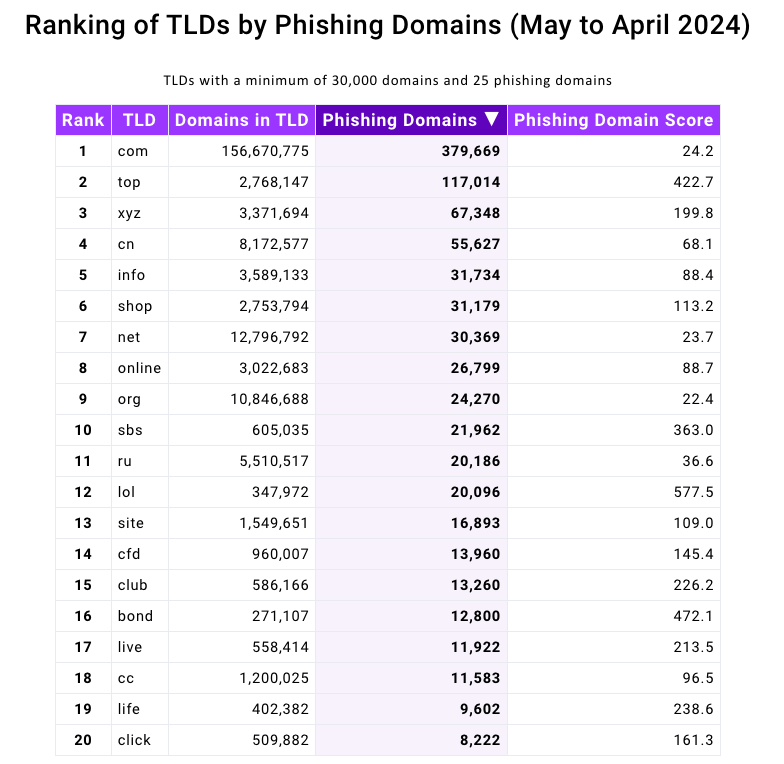
Source: Interisle Consulting Group.
ICANN said its review was based on information collected and studied about .top domains over the past few weeks. But the fact that high volumes of phishing sites are being registered through Jiangsu Bangning Science & Technology Co Ltd. is hardly a new trend.
For example, more than 10 years ago the same Chinese registrar was the fourth most common source of phishing websites, as tracked by the APWG. Bear in mind that the APWG report excerpted below was published more than a year before Jiangsu Bangning received ICANN approval to introduce and administer the new .top registry.
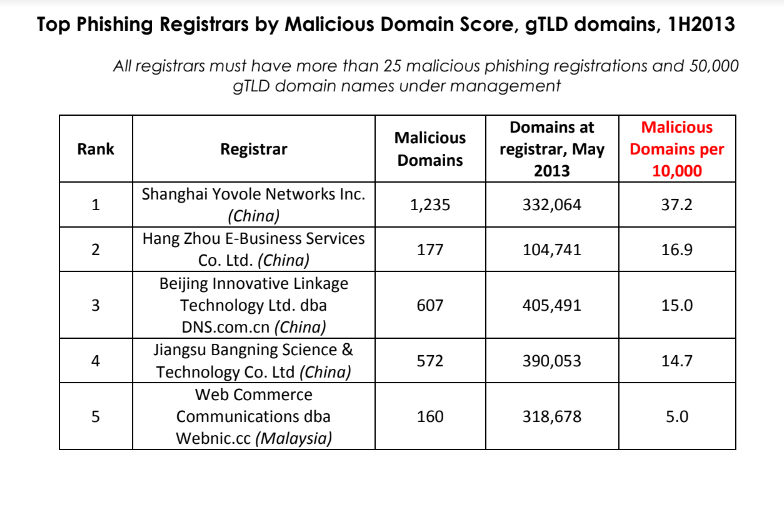
Source: APWG phishing report from 2013, two years before .top came into being.
A fascinating new wrinkle in the phishing landscape is the growth in scam pages hosted via the InterPlanetary File System (IPFS), a decentralized data storage and delivery network that is based on peer-to-peer networking. According to Interisle, the use of IPFS to host and launch phishing attacks — which can make phishing sites more difficult to take down — increased a staggering 1,300 percent, to roughly 19,000 phishing sites reported in the last year.
Last year’s report from Interisle found that domain names ending in “.us” — the top-level domain for the United States — were among the most prevalent in phishing scams. While .us domains are not even on the Top 20 list of this year’s study, “.com” maintained its perennial #1 spot as the largest source of phishing domains overall.
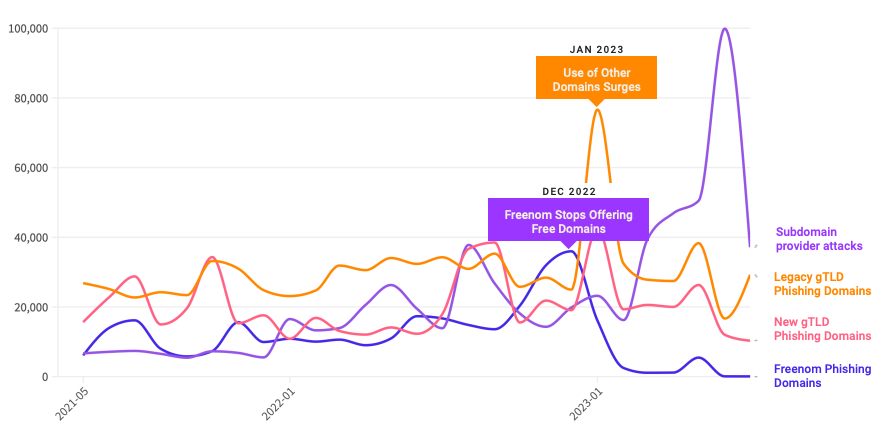
A year ago, the phishiest domain registrar by far was Freenom, a now-defunct registrar that handed out free domains in several country-code TLDs, including .tk, .ml, .ga and .cf. Freenom went out of business after being sued by Meta, which alleged Freenom ignored abuse complaints while monetizing traffic to abusive domains.
Following Freenom’s demise, phishers quickly migrated to other new low-cost TLDs and to services that allow anonymous, free domain registrations — particularly subdomain services. For example, Interisle found phishing attacks involving websites created on Google’s blogspot.com skyrocketed last year more than 230 percent. Other subdomain services that saw a substantial growth in domains registered by phishers include weebly.com, github.io, wix.com, and ChangeIP, the report notes.
Interisle Consulting partner Dave Piscitello said ICANN could easily send similar warning letters to at least a half-dozen other top-level domain registries, noting that spammers and phishers tend to cycle through the same TLDs periodically — including .xyz, .info, .support and .lol, all of which saw considerably more business from phishers after Freenom’s implosion.
Piscitello said domain registrars and registries could significantly reduce the number of phishing sites registered through their services just by flagging customers who try to register huge volumes of domains at once. Their study found that at least 27% of the domains used for phishing were registered in bulk — i.e. the same registrant paid for hundreds or thousands of domains in quick succession.
The report includes a case study in which a phisher this year registered 17,562 domains over the course of an eight-hour period — roughly 38 domains per minute — using .lol domains that were all composed of random letters.
ICANN tries to resolve contract disputes privately with the registry and registrar community, and experts say the nonprofit organization usually only publishes enforcement letters when the recipient is ignoring its private notices. Indeed, ICANN’s letter notes Jiangsu Bangning didn’t even open its emailed notifications. It also cited the registry for falling behind in its ICANN membership fees.
With that in mind, a review of ICANN’s public enforcement activity suggests two trends: One is that there have been far fewer public compliance and enforcement actions in recent years — even as the number of new TLDs has expanded dramatically.
The second is that in a majority of cases, the failure of a registry or registrar to pay its annual ICANN membership fees was cited as a reason for a warning letter. A review of nearly two dozen enforcement letters ICANN has sent to domain registrars since 2022 shows that failure to pay dues was cited as a reason (or the reason) for the violation at least 75 percent of the time.
Piscitello, a former vice president of security at ICANN, said nearly all breach notices sent out while he was at ICANN were because the registrar owed money.
“I think the rest is just lipstick to suggest that ICANN’s on top of DNS Abuse,” Piscitello said.
KrebsOnSecurity has sought comment from ICANN and will update this story if they respond.
ICANN said most of its investigations are resolved and closed through the initial informal resolution stage, and that hundreds of enforcement cases are initiated during this stage with the contracted parties who are required to demonstrate compliance, become compliant, and/or present and implement remediation plans to prevent the recurrence of those enforcement issues.
“It is important to take into account that, prior to issuing any notice of breach to a registrar or registry operator, ICANN Compliance conducts an overall contractual compliance ‘health check’ of the relevant contracted party,” ICANN said in a written response to questions. “During this check, ICANN Compliance proactively reviews the contracted party’s compliance with obligations across the agreements and policies. Any additional contractual violation found during these checks is added to the Notice of Breach. It is not uncommon for parties who failed to comply with contractual obligations (whether they are related to DNS Abuse, RDDS, or others) to also be in arrears with ICANN fees.”
Update, 11:49 p.m. ET: Added statement from ICANN. Clarified Piscitello’s former role at ICANN.




.top has been a cesspool for as long as I can remember and always the first thing I block on a network
One of many TLD’s that should be on the block list already. The entire TLD system needs a do over.
Why? It seems to work well, and it’s good we have more top level domains.
Thanks for the microthought.
you seem like an insufferable jerk
Well, you seem plainly a simpleton contrarian trolling for attention. Maybe we’re both right, but neither *(troll) answered the basic question related to assertions that it’s working great and doesn’t need attention. Start by reading the article and go from there – or just run along.
Ugh. Why is it “good” that we have more unsecured and ill-attended tld’s used by malactors?
“It seems to work well” is based on what exactly?
Interesting. I have an .xyz domain consisting of six numbers (my childhood phone number) that I use where I suspect I might be spammed or defrauded, so that I can relinquish it any time I need to. I bought it because it only costs me about 1 euro a year. I remember when I bought it that numbered .xyz domains where being marketed as suitable for buying in bulk “for testing purposes”.
@ Punk Gift: how do you use it if you are suspecting that you are being spammed or defrauded?
Interesting. I’d like to see statistics on domain names as well as someone actually shutting down some of those domains. Each day I receive nearly 50 spam e-mails from the same domains but with random sender names. Blocking a sender in E-Mail on my IPhone is worthless. But blocking the entire domain would be a godsent. Apple? Anyone listening?
Okay, Time to get some coffee before posting an ignorant comment like this. I appologize.
urlabuse.com says it was the party that reported the attacks to .TOP, which according to ICANN happened in mid April.
https://news.urlabuse.com/ICANN-Issued-Breach-Notice-to-TOP-Registry-After-URLAbuse-Complaint
https://domainincite.com/30036-we-grassed-up-top-says-free-abuse-outfit
Here is the source of the original story and the part that is missed if you are interested:
https://news.urlabuse.com/ICANN-Issued-Breach-Notice-to-TOP-Registry-After-URLAbuse-Complaint
Here is similar abuse happening to GitHub, Microsoft and Google owned domains by spammers.
https://www.oopspam.com/blog/abused-by-spammers
I think .top is abused only because he is the cheapest of all the options. I also own a .top domain, which I purchased during my student years when I didn’t have much money.
This is not news to anyone with a firewall and security logs. Most of the failed login attempts come from China, and not just from the .top domain. Since China regulates its businesses so closely.and owns many of them, one concludes that the Chinese government is complicit. And they don’t respond because they don’t care.
***
Random example from the log: “Failed password for invalid user root from 180.101.88.218 port 48317 ssh2”
$ whois 180.101.88.218
….
Chinanet Jiangsu Province Network
….
***
These are probably bots. Trying to block them all is futile.
You will be assimilated.
You can effectively, IMHO, but not by IP address other than CIDR. You can also do so by regular expression filtering of get and put requests, triggering .htaccess rules in Apache. I send visitors, depending on how naughty they are, to interesting places. You’re looking for .env? There are stock warnings. For visitors who do other things, there are other outcomes. As an Apache administrator you can mask, redirect, and do whatever based on URI, User Agent, CIDR IP address, and several other criteria. Read the mod_rewrite documentation. Each test can redirect miscreants to wherever you want, or give them any file you want. Admins using EC2 will find the AWS firewall allows for fine grained control of access to the whole port range.
If you want to see how this works, click on “Catwhisperer” with a python or go tool that you haven’t sanitized. Homey don’t play with snakes(all safe, you just get a text file), and loves the game Go(Wikimedia page on Go)… It won’t work with any browser, because the rule-set detects python and go based clients only, which have been PT’s. Some visitors get to enjoy an MC Hammer video, which is the outcome of a persistent probe for a CVE from certain areas of Sol 3.
At scale, the same techniques apply, with common sense modification as necessary. Some things are threats and others aren’t and at scale processing shouldn’t be spent on those that aren’t.
Block entire TLD’s at the perimeter and forget it.
China is a kleptocracy. It has nothing to offer but unavoidable risk. Black hole & done.
China, Russia, NK, etc. Heck, maybe a whitelist makes more sense than a blacklist.
The article states “Indeed, ICANN’s letter notes Jiangsu Bangning didn’t even open its emailed notifications”. I gather this is a reference to the first Attachment paragraph. It would be more accurate to say there was no timely response to the emailed notifications.
Properly configured [ahem, Outlook and Gmail] email clients should not allow senders to determine whether their messages have been opened. I am hoping ICANN is not trying to use tracking pixels on its registrars.
Tracking beacons/pixels and related technologies are not uncommon in legal communications IMPE.
I definitely read the headline too quickly and read an article I’m not interested in (but finished out of respect for the work put in for the sake or journalism). I had high hopes of places to stay overnight when following a band
The top domain is cheap, which may be one reason why it is maliciously exploited
Is there anyone more corrupt than the Chinese at this point?
At least the Russian cybercriminals are principled: they just want money. The Chinese seem to just want to create disorder — or at the very least, don’t mind disorder.