Residents across the United States are being inundated with text messages purporting to come from toll road operators like E-ZPass, warning that recipients face fines if a delinquent toll fee remains unpaid. Researchers say the surge in SMS spam coincides with new features added to a popular commercial phishing kit sold in China that makes it simple to set up convincing lures spoofing toll road operators in multiple U.S. states.
Last week, the Massachusetts Department of Transportation (MassDOT) warned residents to be on the lookout for a new SMS phishing or “smishing” scam targeting users of EZDriveMA, MassDOT’s all electronic tolling program. Those who fall for the scam are asked to provide payment card data, and eventually will be asked to supply a one-time password sent via SMS or a mobile authentication app.
Reports of similar SMS phishing attacks against customers of other U.S. state-run toll facilities surfaced around the same time as the MassDOT alert. People in Florida reported receiving SMS phishing that spoofed Sunpass, Florida’s prepaid toll program.

This phishing module for spoofing MassDOT’s EZDrive toll system was offered on Jan. 10, 2025 by a China-based SMS phishing service called “Lighthouse.”
In Texas, residents said they received text messages about unpaid tolls with the North Texas Toll Authority. Similar reports came from readers in California, Colorado, Connecticut, Minnesota, and Washington. This is by no means a comprehensive list.
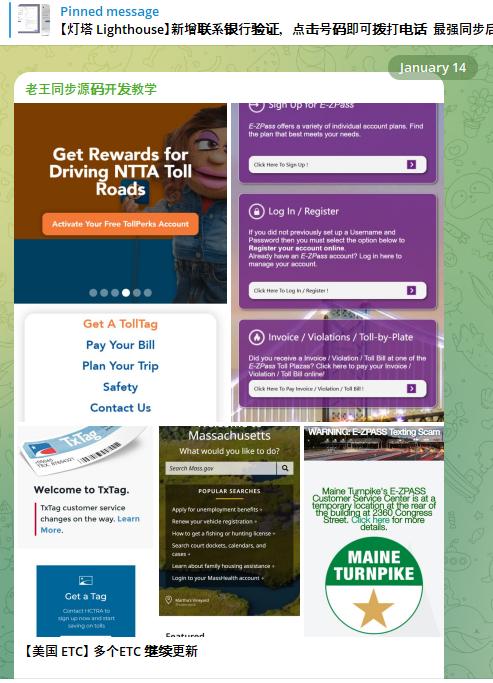
A new module from the Lighthouse SMS phishing kit released Jan. 14 targets customers of the North Texas Toll Authority (NTTA).
In each case, the emergence of these SMS phishing attacks coincided with the release of new phishing kit capabilities that closely mimic these toll operator websites as they appear on mobile devices. Notably, none of the phishing pages will even load unless the website detects that the visitor is coming from a mobile device.
Ford Merrill works in security research at SecAlliance, a CSIS Security Group company. Merrill said the volume of SMS phishing attacks spoofing toll road operators skyrocketed after the New Year, when at least one Chinese cybercriminal group known for selling sophisticated SMS phishing kits began offering new phishing pages designed to spoof toll operators in various U.S. states.
According to Merrill, multiple China-based cybercriminals are selling distinct SMS-based phishing kits that each have hundreds or thousands of customers. The ultimate goal of these kits, he said, is to phish enough information from victims that their payment cards can be added to mobile wallets and used to buy goods at physical stores, online, or to launder money through shell companies.
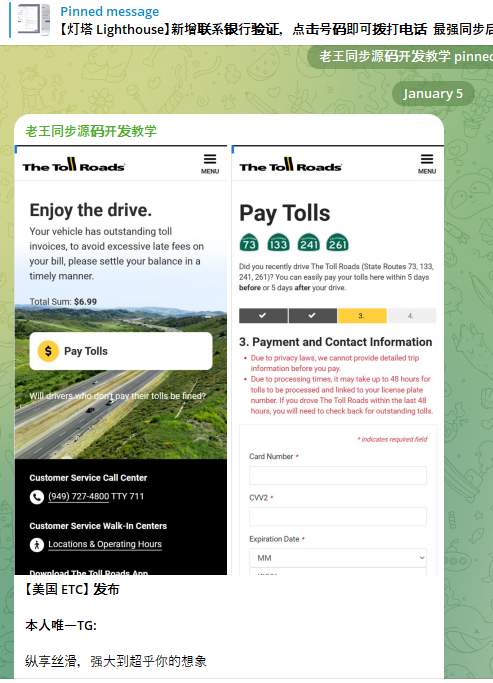
A component of the Chinese SMS phishing kit Lighthouse made to target customers of The Toll Roads, which refers to several state routes through Orange County, Calif.
Merrill said the different purveyors of these SMS phishing tools traditionally have impersonated shipping companies, customs authorities, and even governments with tax refund lures and visa or immigration renewal scams targeting people who may be living abroad or new to a country.
“What we’re seeing with these tolls scams is just a continuation of the Chinese smishing groups rotating from package redelivery schemes to toll road scams,” Merrill said. “Every one of us by now is sick and tired of receiving these package smishing attacks, so now it’s a new twist on an existing scam.”
In October 2023, KrebsOnSecurity wrote about a massive uptick in SMS phishing scams targeting U.S. Postal Service customers. That story revealed the surge was tied to innovations introduced by “Chenlun,” a mainland China-based proprietor of a popular phishing kit and service. At the time, Chenlun had just introduced new phishing pages made to impersonate postal services in the United States and at least a dozen other countries.
SMS phishing kits are hardly new, but Merrill said Chinese smishing groups recently have introduced innovations in deliverability, by more seamlessly integrating their spam messages with Apple’s iMessage technology, and with RCS, the equivalent “rich text” messaging capability built into Android devices.
“While traditional smishing kits relied heavily on SMS for delivery, nowadays the actors make heavy use of iMessage and RCS because telecom operators can’t filter them and they likely have a higher success rate with these delivery channels,” he said.
It remains unclear how the phishers have selected their targets, or from where their data may be sourced. A notice from MassDOT cautions that “the targeted phone numbers seem to be chosen at random and are not uniquely associated with an account or usage of toll roads.”
Indeed, one reader shared on Mastodon yesterday that they’d received one of these SMS phishing attacks spoofing a local toll operator, when they didn’t even own a vehicle.
Targeted or not, these phishing websites are dangerous because they are operated dynamically in real-time by criminals. If you receive one of these messages, just ignore it or delete it, but please do not visit the phishing site. The FBI asks that before you bin the missives, consider filing a complaint with the agency’s Internet Crime Complaint Center (IC3), including the phone number where the text originated, and the website listed within the text.




I’ve had at least 10 or so of these. I don’t own a car. They allege there’s a problem even from other states from where I live. I think for many who received these, it’s an easy and expensive trap to fall into.
Yup. I live in Texas but have had a 508 area code for years. The messages came from the Philippines but I guess I wasn’t supposed to notice that. Massachusetts has always been a pretty long drive from here, like the Philippines is kind of a long swim from China.
This type of scam has been seen in Australia for many years. If fact it is now so well known that most people are fully aware and delete the SMS immediately.
I’ve gotten several of these for Georgia’s PeachPass. A couple of months ago PeachPass actually put up a warning on their website about them.
I received one shortly after opening a snail mail from EZPass. Was “easy” to spot the scam.
This happened to one of my residents at work last week and because she is older she was worried but i helped point out the obvious reasons why it was a scam. First i reminded her that she was in rehab and had not driven her car in Massachusetts for several of months. Secondly i had to remind her that if she had not been out of the state than this is most likely a scam because Connecticut does not have tolls at least to my knowledge. I work in healthcare so phishing is something we are trained and tested on quite often.
I received several such text messages about three months ago here in Maryland. I told my wife (who also got these texts) not to act on it. I logged in to the regular web site without clicking on anything in the message. And Behold! there was an announcement from EZ Pass MD that there were impostor text messages and we should look out.
I received one of these SMS attacks last week. It was not too shabby, as far as phishing attacks go. I could see those attacks being good enough to lure several victims, unfortunately.
I got 4 of these, 2 on 1 day, 2 more on another day.
But…here’s what’s strange: they only showed up in messages on my Apple Watch Ultra 2 with cellular; they didn’t show up in messages on my iPad, or iPhone.
Apple Watch has a separate phone number
Further to my earlier comment he is a link to the Linkt Toll Scam in Melbourne, Australia that has been ongoing for at least two years now.. https://www.linkt.com.au/help/security/latest-scams/melbourne
It shows several SMS messages, some purporting to be from the Toll Provider and some from a Debt Collection House.
Delete and do not open!
Further to my earlier comment here is a link to the Linkt Toll Scam in Melbourne, Australia that has been ongoing for at least two years now.. https://www.linkt.com.au/help/security/latest-scams/melbourne
It shows several SMS messages, some purporting to be from the Toll Provider and some from a Debt Collection House.
Delete and do not open! Be aware!
Does the Chinese government support these phishers?
Yes and no. By proxy they do but if it hurts their image they don’t.
Phishing is not a top tier cybercrime like say stealing corporate or state secrets, so fighting or defending against it only receives the attention/funding relative to the public interest. If Chinese society starts getting vocal about it, only then will the authorities act. They recently cracked down hard on activities operating out of Myanmar for this very reason and the message was; don’t target Chinese citizens.
Phishing and lower tier crimes of opportunity are generally only performed by organised crime groups or script kiddies, but groups operating out of Russia and China have been known for years to have support from state backed APT operatives, moonlighting for extra cash on the side. Unfortunately, like Russia, corruption exists and they are lowly paid, so their supervisors turn a blind eye. This is also why Western agencies have been able to identify and sanction so many individual operatives, simply because they get lazy and use the same tools and techniques regardless of who they are working for; an MO is like a fingerprint and leaves you vulnerable to discovery.
By comparison Western agencies, Five Eyes operatives especially, are bound by very strict rules of engagement for the very reasons stated above. They are highly educated and highly paid. Therefore moonlighting is not only frowned upon, but would be career ending and ostracised from the community forever.
I’ve talked one of them and they don’t even know this type of fraud may cause jail time in world. No fraud is illegal in china that’s why every fraud site is operator by chinese.
There is companies in china that sends scam messages with spoofed caller / sender IDs and there is not only one, same company owns 500 more subcompany. They have real office, real address, real support contacts.
LOL.. nice joke.
I don’t trust text messages because there is no real way to authenticate them.
My rate of text messages went up in 2024 because of doctors. It seems that doctors really love them for contacting patients.
I thought that I had found a good use for text messages when I found out that I could send e-mail to the telephone number ([cellnumber]@vtext.com for Verizon and [cellnumber]@txt.att.net for AT&T). So the logical thing was to have my servers send text messages for various events to my cell phone so that I could keep up with what was happening even at times when I don’t have internet access.
I started with logins to the servers. Even that was too much. After about twenty minutes, the cell phone company stopped accepting messages. I had figured realistically that I would be happy with maybe 40,000 messages a month to cover startups, shutdowns, logins, logouts, and some significant attempts to break in, but when it couldn’t barely handle five messages per hour, that was out of the question.
So I’m back to hating text messages.
Drag a few anchors over the middling kingdon’s cables. “Chinese cybercriminal group” is redundant.
IN MN and have received a couple of these. Here you need to have a balance and CC on file to use the system so their story doesn’t wash with this process.
Here in Seattle area I got one of these from Good-To-Go, deleted, and several from US Post office-deleted, and yesterday one from Pay Pal, also ignored and deleted. Also two from bogus Amazon purchases. They got nothing but I did get my credit card re-issued. ( They were happy to do it after I explained all of the above)
I have taught my wife,kids,dog,cat, and pet canary that if they get an SMS, Email, or any other type of comms that say you need to click this link to look up the sender’s phone number not the number in the message and ring them to verify the message. If verified then to proceed to the senders web site and check there as well.
I am not convinced that criminals do not have a list of numbers associated with toll accounts (at least in MA). I received a smish along with several people with area codes in other states. Oddly, the area code that sent me the text coincides with my wife’s area code which is across the county. Maybe a mere coincidence, I just don’t know.
What’s the repair if someone did open the link?
(Asking for a friend)
If your are asking specifically about the scam Brian described in the article above ie; toll phishing via SMS, it all depends on what your friend did DIRECTLY AFTER clicking on the link.
1. If they found themselves on a toll operators page they weren’t familiar with, asking for payment card data and this spooked them into closing the page without going any further, they are probably going to be okay. Just block, report and delete the message.
2. If, however they continued to enter their payment card data AND supplied the one-time pass-code sent to them via SMS or their authenticator app, there will be problems and you need to act quickly. The toll operators page they visited is FAKE and controlled by the scammers, so any payment card data you have provided them, including the one-time pass-code, has given them access to the bank account attached to that payment card. That card has been compromised and needs to be cancelled by their financial institution ASAP as the malicious actors will waste no time abusing it.
As this is only a data harvesting attack the physical device ie; phone, should be fine. If in doubt back up all their data and perform a factory reset, however as there is no suspicious download of files present here, I don’t think this is necessary.
As Brian points out; “It remains unclear how the phishers have selected their targets” it is important to remember that these scammers have access to millions of compromised phone numbers and you are not being individually targeted. They are performing a “Spray and Pray” offensive in the hopes of catching that less than 1% off guard. Please remain vigilant as these campaigns will continue into the foreseeable future.
Yeah, I’ll go into this more in a follow-up, but basically their phishing pages are live, which means anything you type they will capture, whether or not you actually hit submit. So let’s say you enter all your credit card details and address etc, and then go “nah, this is a scam” and close the page, they still have your info. This is one of the reasons why I urge people not to even visit these links.
Cheers for that Brian. I look forward to the follow-up.
In India, I received a traffic violation fine with a link to pay for riding without a helmet at 9 pm in a neighbouring district – on my tractor.
We’ve had these in Ireland for a couple of years now. They spoof the eFlow toll company, as they are responsible for the only barrierless toll bridge in the country.
A colleague’s son got caught with this in the early days. It was pure coincidence that they had just come off the motorway having gone over the toll bridge when the message came in. Since they didn’t have a tag or an account with eFlow, they presumed it was the company offering them a quick and easy way to pay, so they went to the website and paid the “toll”. They had €2,500 taken, which they eventually managed to get back from the bank.
https://www.rte.ie/news/business/2023/0214/1356635-eflow-warns-motorists-not-to-respond-to-scam-texts/
https://www.eflow.ie/news/eflow-fraudulent-text-messages/
China deserves all type of hate, all of those SMS/VOIP/CARD scams are based on there. Visit any fraud site, you will see chinese language option lol. I don’t think it’s illegal in China that’s why they are able to do it freely without any pressure.
Literally just got this spam SMS this afternoon. WA state, though the spam is referencing a toll vendor that does not exist in WA.
That’s only the tip of the iceberg, like one of the many schemes they have, there are e-commerce stores, there are PayPal copies. They steal your cards, tie them on google pay or apple pay and use them on POS machines or payment links built for them to “cash-out” stolen cards. Even FBI won’t care, I even wrote to krebson and never got a reply. What is shown in this article is already old when it gets sold to the “public” chinese profit first between themself selling those “packages”.
I’ve been digging for a year now and I realized that no one cares in any country, I’ve found similar structures for any country in the world and contacted them. Didn’t recieved a single answer. I guess for the big guys is cheaper to just write a warning on top of the real websites, nobody cares of your money so be careful and always double check even the link that looks the real one. If you want to shop in your favorite store be sure to bookmark it and open just from there even if you see some ads with incredible discounts is better to close and reach a website just from your bookmarks, not even searching on Google is safe nowadays.
Just delete any SMS message with Chinese characters in it.
I’m the the SF Bay Area where we use FastPASS. They’ve tried purporting to be FastPASS too.
But I can’t count how many I’ve received for EZpass.
After reading your article yesterday “Chinese Innovations Spawn Wave of Toll Phishing Via SMS” I thought you and your readers should know that the above group is sending out notices in the mail to individuals. One of my family members received two notices in the mail. The initial one notifying there was an outstanding toll and then a 2nd a few days later which included late charges. This was in NH for the EZ-PassMA. Both of the invoices included a wrong license plate number, wrong state (MA) – (NH resident). Same telephone number on both. However, this family member tried to called the number to see what this was about. No answer. I just happened to advise them in conversation, about your article and the one the FBI had published. I advised my family member to block the number on their phone and I told them I would fill out the IC3.gov form to advise them that not only are these individuals sending the SMS messages, they are using the US postal service too.
I sincerely thank you again for helping keep your readers informed.