A security architect with the National Labor Relations Board (NLRB) alleges that employees from Elon Musk‘s Department of Government Efficiency (DOGE) transferred gigabytes of sensitive data from agency case files in early March, using short-lived accounts configured to leave few traces of network activity. The NLRB whistleblower said the unusual large data outflows coincided with multiple blocked login attempts from an Internet address in Russia that tried to use valid credentials for a newly-created DOGE user account.

The cover letter from Berulis’s whistleblower statement, sent to the leaders of the Senate Select Committee on Intelligence.
The allegations came in an April 14 letter to the Senate Select Committee on Intelligence, signed by Daniel J. Berulis, a 38-year-old security architect at the NLRB.
NPR, which was the first to report on Berulis’s whistleblower complaint, says NLRB is a small, independent federal agency that investigates and adjudicates complaints about unfair labor practices, and stores “reams of potentially sensitive data, from confidential information about employees who want to form unions to proprietary business information.”
The complaint documents a one-month period beginning March 3, during which DOGE officials reportedly demanded the creation of all-powerful “tenant admin” accounts in NLRB systems that were to be exempted from network logging activity that would otherwise keep a detailed record of all actions taken by those accounts.
Berulis said the new DOGE accounts had unrestricted permission to read, copy, and alter information contained in NLRB databases. The new accounts also could restrict log visibility, delay retention, route logs elsewhere, or even remove them entirely — top-tier user privileges that neither Berulis nor his boss possessed.
Berulis writes that on March 3, a black SUV accompanied by a police escort arrived at his building — the NLRB headquarters in Southeast Washington, D.C. The DOGE staffers did not speak with Berulis or anyone else in NLRB’s IT staff, but instead met with the agency leadership.
“Our acting chief information officer told us not to adhere to standard operating procedure with the DOGE account creation, and there was to be no logs or records made of the accounts created for DOGE employees, who required the highest level of access,” Berulis wrote of their instructions after that meeting.
“We have built in roles that auditors can use and have used extensively in the past but would not give the ability to make changes or access subsystems without approval,” he continued. “The suggestion that they use these accounts was not open to discussion.”
Berulis found that on March 3 one of the DOGE accounts created an opaque, virtual environment known as a “container,” which can be used to build and run programs or scripts without revealing its activities to the rest of the world. Berulis said the container caught his attention because he polled his colleagues and found none of them had ever used containers within the NLRB network.
Berulis said he also noticed that early the next morning — between approximately 3 a.m. and 4 a.m. EST on Tuesday, March 4 — there was a large increase in outgoing traffic from the agency. He said it took several days of investigating with his colleagues to determine that one of the new accounts had transferred approximately 10 gigabytes worth of data from the NLRB’s NxGen case management system.
Berulis said neither he nor his co-workers had the necessary network access rights to review which files were touched or transferred — or even where they went. But his complaint notes the NxGen database contains sensitive information on unions, ongoing legal cases, and corporate secrets.
“I also don’t know if the data was only 10gb in total or whether or not they were consolidated and compressed prior,” Berulis told the senators. “This opens up the possibility that even more data was exfiltrated. Regardless, that kind of spike is extremely unusual because data almost never directly leaves NLRB’s databases.”
Berulis said he and his colleagues grew even more alarmed when they noticed nearly two dozen login attempts from a Russian Internet address (83.149.30,186) that presented valid login credentials for a DOGE employee account — one that had been created just minutes earlier. Berulis said those attempts were all blocked thanks to rules in place that prohibit logins from non-U.S. locations.
“Whoever was attempting to log in was using one of the newly created accounts that were used in the other DOGE related activities and it appeared they had the correct username and password due to the authentication flow only stopping them due to our no-out-of-country logins policy activating,” Berulis wrote. “There were more than 20 such attempts, and what is particularly concerning is that many of these login attempts occurred within 15 minutes of the accounts being created by DOGE engineers.”
According to Berulis, the naming structure of one Microsoft user account connected to the suspicious activity suggested it had been created and later deleted for DOGE use in the NLRB’s cloud systems: “DogeSA_2d5c3e0446f9@nlrb.microsoft.com.” He also found other new Microsoft cloud administrator accounts with nonstandard usernames, including “Whitesox, Chicago M.” and “Dancehall, Jamaica R.”
On March 5, Berulis documented that a large section of logs for recently created network resources were missing, and a network watcher in Microsoft Azure was set to the “off” state, meaning it was no longer collecting and recording data like it should have.
Berulis said he discovered someone had downloaded three external code libraries from GitHub that neither NLRB nor its contractors ever use. A “readme” file in one of the code bundles explained it was created to rotate connections through a large pool of cloud Internet addresses that serve “as a proxy to generate pseudo-infinite IPs for web scraping and brute forcing.” Brute force attacks involve automated login attempts that try many credential combinations in rapid sequence.
The complaint alleges that by March 17 it became clear the NLRB no longer had the resources or network access needed to fully investigate the odd activity from the DOGE accounts, and that on March 24, the agency’s associate chief information officer had agreed the matter should be reported to US-CERT. Operated by the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA), US-CERT provides on-site cyber incident response capabilities to federal and state agencies.
But Berulis said that between April 3 and 4, he and the associate CIO were informed that “instructions had come down to drop the US-CERT reporting and investigation and we were directed not to move forward or create an official report.” Berulis said it was at this point he decided to go public with his findings.
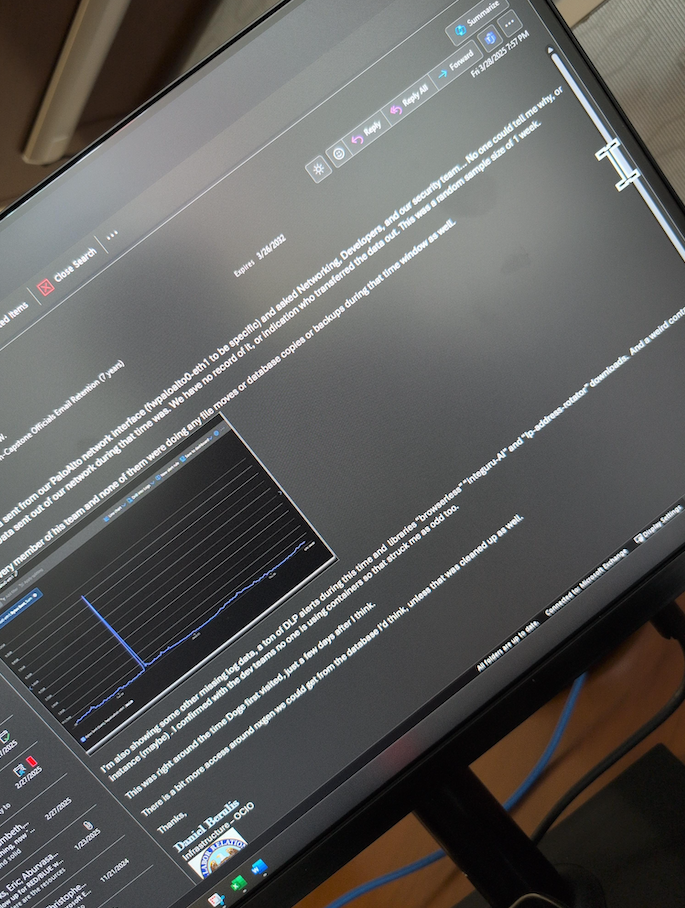
An email from Daniel Berulis to his colleagues dated March 28, referencing the unexplained traffic spike earlier in the month and the unauthorized changing of security controls for user accounts.
Tim Bearese, the NLRB’s acting press secretary, told NPR that DOGE neither requested nor received access to its systems, and that “the agency conducted an investigation after Berulis raised his concerns but ‘determined that no breach of agency systems occurred.'” The NLRB did not respond to questions from KrebsOnSecurity.
Nevertheless, Berulis has shared a number of supporting screenshots showing agency email discussions about the unexplained account activity attributed to the DOGE accounts, as well as NLRB security alerts from Microsoft about network anomalies observed during the timeframes described.
As CNN reported last month, the NLRB has been effectively hobbled since President Trump fired three board members, leaving the agency without the quorum it needs to function.
“Despite its limitations, the agency had become a thorn in the side of some of the richest and most powerful people in the nation — notably Elon Musk, Trump’s key supporter both financially and arguably politically,” CNN wrote.
Both Amazon and Musk’s SpaceX have been suing the NLRB over complaints the agency filed in disputes about workers’ rights and union organizing, arguing that the NLRB’s very existence is unconstitutional. On March 5, a U.S. appeals court unanimously rejected Musk’s claim that the NLRB’s structure somehow violates the Constitution.
Berulis shared screenshots with KrebsOnSecurity showing that on the day the NPR published its story about his claims (April 14), the deputy CIO at NLRB sent an email stating that administrative control had been removed from all employee accounts. Meaning, suddenly none of the IT employees at the agency could do their jobs properly anymore, Berulis said.
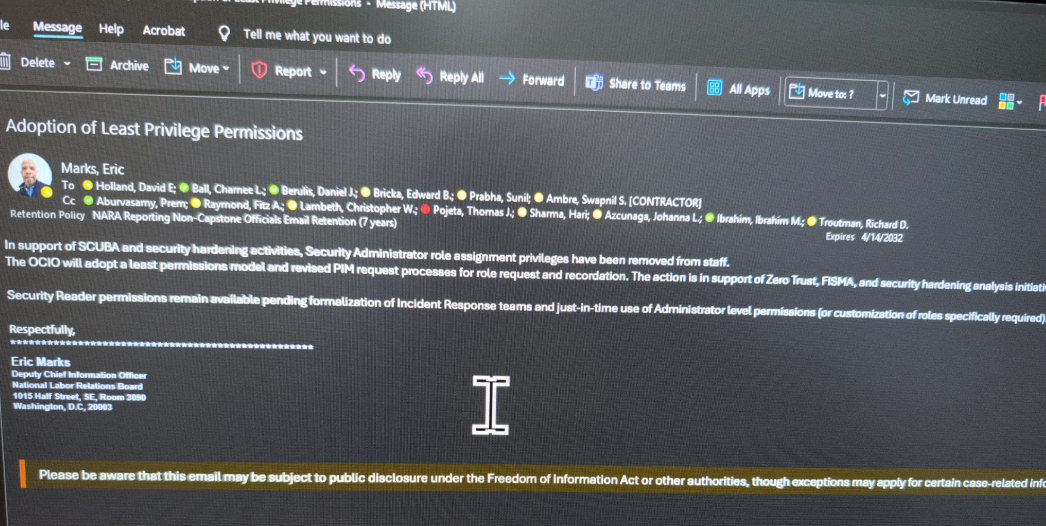
An email from the NLRB’s associate chief information officer Eric Marks, notifying employees they will lose security administrator privileges.
Berulis shared a screenshot of an agency-wide email dated April 16 from NLRB director Lasharn Hamilton saying DOGE officials had requested a meeting, and reiterating claims that the agency had no prior “official” contact with any DOGE personnel. The message informed NLRB employees that two DOGE representatives would be detailed to the agency part-time for several months.

An email from the NLRB Director Lasharn Hamilton on April 16, stating that the agency previously had no contact with DOGE personnel.
Berulis told KrebsOnSecurity he was in the process of filing a support ticket with Microsoft to request more information about the DOGE accounts when his network administrator access was restricted. Now, he’s hoping lawmakers will ask Microsoft to provide more information about what really happened with the accounts.
“That would give us way more insight,” he said. “Microsoft has to be able to see the picture better than we can. That’s my goal, anyway.”
Berulis’s attorney told lawmakers that on April 7, while his client and legal team were preparing the whistleblower complaint, someone physically taped a threatening note to Mr. Berulis’s home door with photographs — taken via drone — of him walking in his neighborhood.
“The threatening note made clear reference to this very disclosure he was preparing for you, as the proper oversight authority,” reads a preface by Berulis’s attorney Andrew P. Bakaj. “While we do not know specifically who did this, we can only speculate that it involved someone with the ability to access NLRB systems.”
Berulis said the response from friends, colleagues and even the public has been largely supportive, and that he doesn’t regret his decision to come forward.
“I didn’t expect the letter on my door or the pushback from [agency] leaders,” he said. “If I had to do it over, would I do it again? Yes, because it wasn’t really even a choice the first time.”
For now, Mr. Berulis is taking some paid family leave from the NLRB. Which is just as well, he said, considering he was stripped of the tools needed to do his job at the agency.
“They came in and took full administrative control and locked everyone out, and said limited permission will be assigned on a need basis going forward” Berulis said of the DOGE employees. “We can’t really do anything, so we’re literally getting paid to count ceiling tiles.”
Further reading: Berulis’s complaint (PDF).




RIPPope
My initial thought was that DOGE was conducting penetration testing using a VPN or Tor routed through a Russian IP address. However, it turns out this IP is actually associated with a mobile device – likely a cellphone or a modem…
The multiple login attempts from a Russian IP sounds too amateurish to believe. If 1 or 2 login attempts fail, wouldn’t they immediately drop to a US proxy or VPN? Or just use a US proxy/VPN from the first login?
OTOH maybe they used a VPN intentionally to blame Russia…
Or DOGE forgot to turn off their Russian VPN they were using before logging in.
The credentials had just been created within 15 minutes or so. A small group obtains those hot JIT credentials and tries to login a few times each? Assuming they have centralized operation infrastructure w/ distributed access. Maybe it gave some obscure error code and they were trying different setups? I wouldn’t say that’s the least believable part, it’s all pretty unbelievable isn’t it?
But absolutely everything DOGE does sounds too amateurish to believe. That’s why I have no doubt it’s them. (Also it was clear years before: this government would sell every single American asset to Russia for an apple.)
How do you know they didn’t use a VPN. The same day this they figured out the report was to be published, 3 top people at NSA were fired. It sounds like they contacted the NSA and they tracked it. That would be classified information and not released publicly. Why was he threatened multiple times not to release the report? Why would they worry if it was not true. He signed a sworn affidavit and it a felony to do what he did and lie. But you think it is made up makes sense. They lied about doge being granted access. They said they were never given access but subsequently the Whitehouse confirmed they were given access to the systems. Someone is lying. Either trumps people at the NLRB or the Whitehouse. Either way they are lying about what happened. But your simplistic explanation is supposed to refute it. It nonsense.
Thank God for whistleblowers and thank journalists for covering it.
and you’re mentally ill ..
Musk is far more corrupt that I thought! DODGE is far more suspicious and crooked, especially under Musk. Then there is the Russian connection. What is that all about? I fear what is coming.
They want to rewrite millions of lines of code used by the Social Security Administration. If you wanted to siphon off billions of dollars yearly from Social Security, that would be the way to go.
wowo you’re some high level moron, seek help
This is just evil, and stupid. Forgot firewalls and IPSs, they can just be circumvented by the lackey of a billionaire in a black SUV. Next time, physical security should just shoot.
I cannot imagine any legitimate reason to create accounts with logging disabled. Why would that capability even exist?
Thank you Mr Daniel, you did the right thing at great cost.
The Trusted News Initiative is hard at work.
It would probably be the top news in a normal administration. With this one, it would barely make the headlines. The problem with the U.S. system is that there’s absolutely nothing that we can do now since the congress is just looking the other way and the executive branch is the Russian asset.
This would either be the birth of the United States of Fascist America, or the end of the republican party, that after this election will never be able to elect another candidate. We shall see.
So…Russia is involved because they ran…a docker container?
How’s that boot taste?
DOGE is saying it never happened.
https://x.com/amuse/status/1913665346281656394
BTW, quoting NPR doesn’t help the case as they are hardly an unbiased source.
NPR is far more unbiased than DOGE, themselves.
Another spinless lacky. The sad part is, even if we do get past this regime people like you get to carry on like nothing happened.
“…quoting NPR doesn’t help the case as they are hardly an unbiased source.” Now, that is an understatement if there ever was one.
These DOGE invasions are unrecoverable. We are literally watching the end of America as we know it.
DOGE destroying the government and Tesla getting super-contracts. Just wrap it all up and throw it away at this point.
I wish to God that Anonymous would get on the job of hacking the Doge idiots and all of Musk’s businesses. They’ve destroyed the US State Dept., the EPA, and will probably destroy the Social Security system using Musk’s half-*ssed AI, Grok. The only thing that will stop the Trumpists is technology, not some sad little demonstrations w/ppl holding signs fgs! If I had the skills I’d do it myself!
YOU CAN GET THESE TYPES OF SIGNINS ON ANY FKING ACCOUNT IN O365, these are typical botnet attempts they can show up from any country. AND DO NOTHING IF YOU HAVE MFA. But you really proved that you’re some dumb sH***t mf and you call yourself cyber security expert.. you’re fking propaganda spreading leftist woke mf.
Nurse! He needs another dose of Ivermectin!
How does a botnet get the correct password for a brand new account? That’s an incident in its own right.
Kerbs and the whistleblower are framing this as a sophisticated nation-state attack leveraging DOGE to exploit the NLRB. But that doesn’t add up. Nation-state actors don’t blow their cover because they proxy with clean IPs from within the target country. The IP address in question (83.149.30[.]186) has had a bad reputation in open-source intelligence for over a year, linked to credential stuffing and scanning activity. Using an IP like that in a high-level operation is like flying a spy plane into enemy airspace with inflatable tube men and disco balls strapped to the wings. Attacks of this complexity require significant time and resources—no serious actor would risk burning their investment by using an IP already flagged and based in Russia. What is more likely- the DOGE employee’s creds were leaked, he’s reusing passwords, or using a weak password and they got password sprayed.
CISA and US-CERT are not a bunch for scrubs. If their official statement is that it’s not a security incident then I trust them.
I see no official statement from CISA and/or US-CERT that it’s not a security incident. Where are you reading that or did you just make it up?
“instructions had come down to drop the US-CERT reporting and investigation and we were directed not to move forward or create an official report.” That means it was not incident read between the lines dude. Also google the guy’s name you’ll find articles stating National Labor Relations Board saying it wasn’t an incident.
Ah, so because the higher-ups at NLRB denied everything, it never happened? Newsflash: You can always find “articles” offering almost any kind of take on any big story, but a lot of those publications offer conclusions without supporting them with facts. And if you’re asking AI to tell you the truth, their LLM crawlers are getting fed a ton of real fake news to create a ton of a “stories” that offer unsubstantiated explanations but which are not made for human consumption.
I will wait for more information. There are a ton of false naratives being pushed to try and discredit any meaningful and necessary reduction in fraud, waste, and abuse in the government. As an example of the kind if thing taking place, there was a widespread story being pushed recently that an American citizen was wrongly being held by immigration officials for ten days. As it turned out, the likes of NPR and other Leftists media didn’t have the real story. On its face, this seemed like a pretty big flub by federal officials. After all, no one should want a government that can mistakenly arrest you and hold you for ten days without any evidence that you’re an illegal alien. There’s just one problem, though. Hermosillo not only told immigration officials he crossed the border illegally, but he also signed a statement swearing that as well. So, just take a seat and stop gaslighting us about “the world coming to an end”.
Must have been a chinese hacker using a russian vpn… many such cases
nice how you framed a docker container, a ubiquitous tool for this kind of work for at least the last 10 years, as super super scary.
Krebs, the tech-bro who cried wolf.