Security researchers recently revealed that the personal information of millions of people who applied for jobs at McDonald’s was exposed after they guessed the password (“123456”) for the fast food chain’s account at Paradox.ai, a company that makes artificial intelligence based hiring chatbots used by many Fortune 500 firms. Paradox.ai said the security oversight was an isolated incident that did not affect its other customers, but recent security breaches involving its employees in Vietnam tell a more nuanced story.
A screenshot of the paradox.ai homepage showing its AI hiring chatbot “Olivia” interacting with potential hires.
Earlier this month, security researchers Ian Carroll and Sam Curry wrote about simple methods they found to access the backend of the AI chatbot platform on McHire.com, the McDonald’s website that many of its franchisees use to screen job applicants. As first reported by Wired, the researchers discovered that the weak password used by Paradox exposed 64 million records, including applicants’ names, email addresses and phone numbers.
Paradox.ai acknowledged the researchers’ findings but said the company’s other client instances were not affected, and that no sensitive information — such as Social Security numbers — was exposed.
“We are confident, based on our records, this test account was not accessed by any third party other than the security researchers,” the company wrote in a July 9 blog post. “It had not been logged into since 2019 and frankly, should have been decommissioned. We want to be very clear that while the researchers may have briefly had access to the system containing all chat interactions (NOT job applications), they only viewed and downloaded five chats in total that had candidate information within. Again, at no point was any data leaked online or made public.”
However, a review of stolen password data gathered by multiple breach-tracking services shows that at the end of June 2025, a Paradox.ai administrator in Vietnam suffered a malware compromise on their device that stole usernames and passwords for a variety of internal and third-party online services. The results were not pretty.
The password data from the Paradox.ai developer was stolen by a malware strain known as “Nexus Stealer,” a form grabber and password stealer that is sold on cybercrime forums. The information snarfed by stealers like Nexus is often recovered and indexed by data leak aggregator services like Intelligence X, which reports that the malware on the Paradox.ai developer’s device exposed hundreds of mostly poor and recycled passwords (using the same base password but slightly different characters at the end).
Those purloined credentials show the developer in question at one point used the same seven-digit password to log in to Paradox.ai accounts for a number of Fortune 500 firms listed as customers on the company’s website, including Aramark, Lockheed Martin, Lowes, and Pepsi.
Seven-character passwords, particularly those consisting entirely of numerals, are highly vulnerable to “brute-force” attacks that can try a large number of possible password combinations in quick succession. According to a much-referenced password strength guide maintained by Hive Systems, modern password-cracking systems can work out a seven number password more or less instantly.
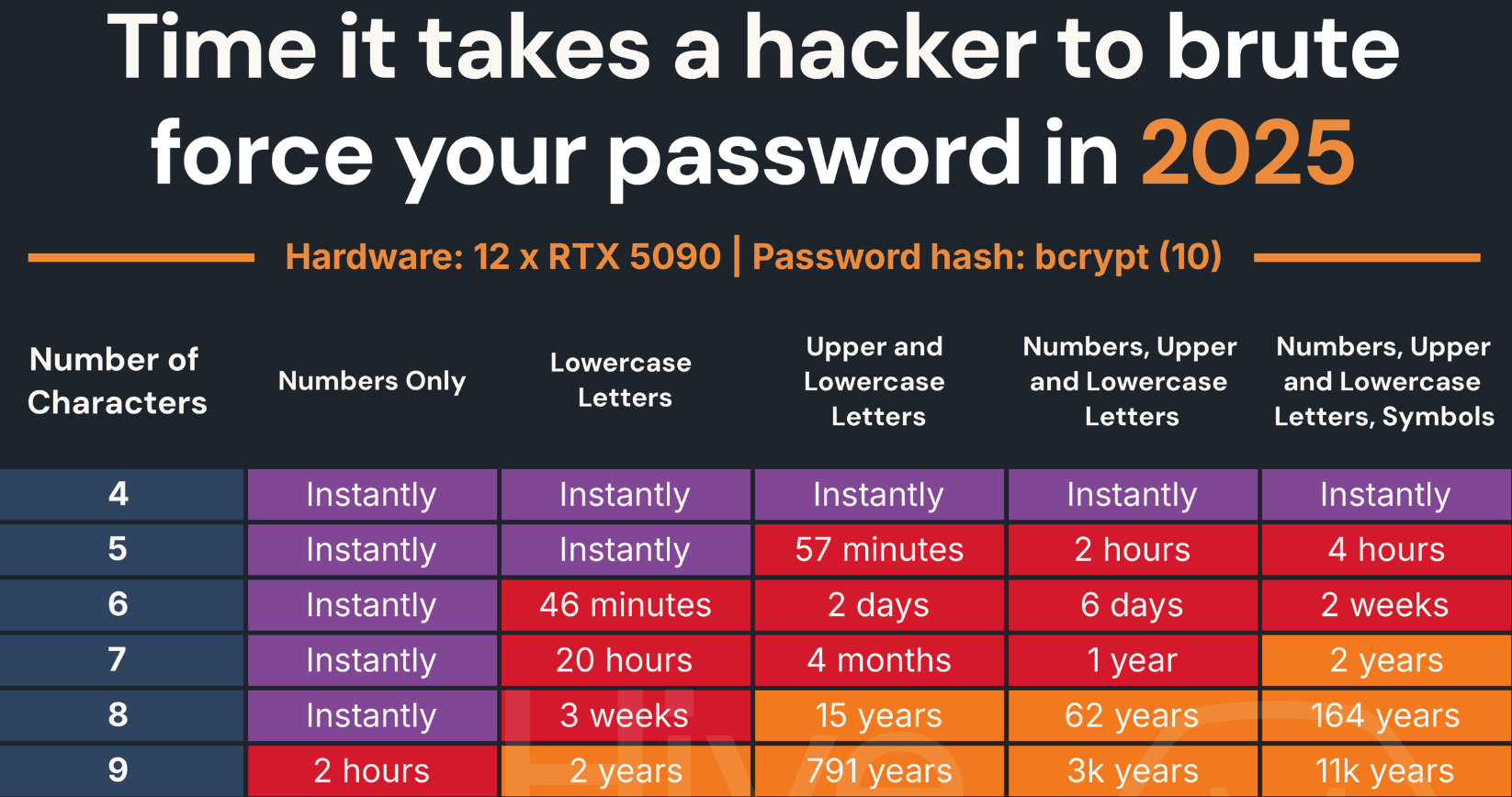
Image: hivesystems.com.
In response to questions from KrebsOnSecurity, Paradox.ai confirmed that the password data was recently stolen by a malware infection on the personal device of a longtime Paradox developer based in Vietnam, and said the company was made aware of the compromise shortly after it happened. Paradox maintains that few of the exposed passwords were still valid, and that a majority of them were present on the employee’s personal device only because he had migrated the contents of a password manager from an old computer.
Paradox also pointed out that it has been requiring single sign-on (SSO) authentication since 2020 that enforces multi-factor authentication for its partners. Still, a review of the exposed passwords shows they included the Vietnamese administrator’s credentials to the company’s SSO platform — paradoxai.okta.com. The password for that account ended in 202506 — possibly a reference to the month of June 2025 — and the digital cookie left behind after a successful Okta login with those credentials says it was valid until December 2025.
Also exposed were the administrator’s credentials and authentication cookies for an account at Atlassian, a platform made for software development and project management. The expiration date for that authentication token likewise was December 2025.
Infostealer infections are among the leading causes of data breaches and ransomware attacks today, and they result in the theft of stored passwords and any credentials the victim types into a browser. Most infostealer malware also will siphon authentication cookies stored on the victim’s device, and depending on how those tokens are configured thieves may be able to use them to bypass login prompts and/or multi-factor authentication.
Quite often these infostealer infections will open a backdoor on the victim’s device that allows attackers to access the infected machine remotely. Indeed, it appears that remote access to the Paradox administrator’s compromised device was offered for sale recently.
In February 2019, Paradox.ai announced it had successfully completed audits for two fairly comprehensive security standards (ISO 27001 and SOC 2 Type II). Meanwhile, the company’s security disclosure this month says the test account with the atrocious 123456 username and password was last accessed in 2019, but somehow missed in their annual penetration tests. So how did it manage to pass such stringent security audits with these practices in place?
Paradox.ai told KrebsOnSecurity that at the time of the 2019 audit, the company’s various contractors were not held to the same security standards the company practices internally. Paradox emphasized that this has changed, and that it has updated its security and password requirements multiple times since then.
It is unclear how the Paradox developer in Vietnam infected his computer with malware, but a closer review finds a Windows device for another Paradox.ai employee from Vietnam was compromised by similar data-stealing malware at the end of 2024 (that compromise included the victim’s GitHub credentials). In the case of both employees, the stolen credential data includes Web browser logs that indicate the victims repeatedly downloaded pirated movies and television shows, which are often bundled with malware disguised as a video codec needed to view the pirated content.




“A developer”, so someone who should know better?
But plural its developers developers developers. There’s no accountability when you’re just a hivemind.
Someone shocked me in a casual conversation on Wednesday when he argued that all wifi access points should have the password “12345678” (without the quotes) and he couldn’t understand why I thought that was a terrible idea. In the past he has said that no person, no business, and no government should be permitted to have any secrets.
On the surface, he’s one of the most intelligent people I know, but he doesn’t seem to have much in the way of common sense to guide his use of that intelligence.
Why don’t these systems adopt a delay and lockout after failed login attempts?
Even my phone does this, requiring a ten minute rest after three failures; it completely locks up after a hundred (or something like that).
Wouldn’t this policy protect all but the most feeble passwords?
This is not that type of attack. The attack you are referring to is simply trying to guess a password, then entering that password to an online service at a login prompt. That type of attack is typically easily thwarted by the measures you mentioned… timeout, lockout, and rate limiting.
The attack the article is referring to is when a hacker breaks into a service and steals their encrypted user password database, then attempts to decrypt the passwords stored in the database. In this scenario the hacker gets an unlimited number of tries to decrypt the passwords.
Too often also the timeout restrictions and MFA requirements for trying passwords can be bypassed by trying to log into an API (a programming interface rather than a user one) and trying user names and passwords there. If the developer codes the timeout into the mobile app or web interface only and not the actual API that those communicate with on the backend. And those API transactions may either not be logged the same way as the intended end user interactions, or those logs may not be analyzed for abuse.
“the digital cookie left behind after a successful Okta login with those credentials says it was valid until December 2025”
But bear in mind this does not ipso facto mean that an Okta login is valid for six months. Okta could use all manner of logic on the server side to decide to reject a cookie that hasn’t expired. A shorter expiration, an unexpected IP address, or manual action by an administrator, to name a few. I don’t know which of this Okta has implemented; hopefully all of them and more.
All I could do after the first sentence of this article was laugh. They used 123456 as a password, and this year’s winner
of the Darwin award is… Come on, use your pet’s name, it would be more secure.
I’m gonna have to change the combination to my luggage.
Why in this day and age are they not using an API to prevent the use of passwords like this?
> “123456”
> seven character password
Did you use an LLM to count the characters?
There’s nothing wrong with the story. I guess at some point they improved their passwords by adding a digit.
“Paradox.ai told KrebsOnSecurity that at the time of the 2019 audit, the company’s various contractors were not held to the same security standards the company practices internally. Paradox emphasized that this has changed, and that it has updated its security and password requirements multiple times since then.”
Does this mean that Paradox took on jobs from customers to build something for them and then outsourced the implementation to contractors and never even bothered to verify whether the end result actually matches any product requirements (like features, quality and security)? 😮 If they did such checks, how could it escape them that a significant number of the delivered solutions (built by their contractors for Paradox customers, e.g. McDonalds, Aramark, Lockheed Martin, Lowes and Pepsi) allowed a password like “123456”? I mean checking password complexity requirements should be on the top of every kind of security reviews/audits. Paradox’s reasoning sounds very weak to say the least.