Visa Drops Support for Breached Processor, Acknowledges Weekend Outage
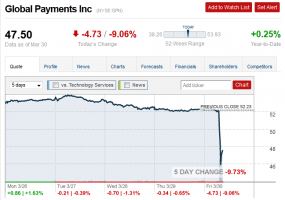
Global Payments, the credit and debit card processor that disclosed a breach of its systems late Friday, said in a statement Sunday that the incident involved at least 1.5 million accounts. The news comes hours ahead of a planned conference call with investors, and after Visa said it had pulled its seal of approval for the company.
In a press release issued 9:30 p.m. ET Sunday, Atlanta based Global Payments Inc. said it believes “the affected portion of its processing system is confined to North America and less than 1,500,000 card numbers may have been exported…Based on the forensic analysis to date, network monitoring and additional security measures, the company believes that this incident is contained. ”
It remains unclear whether there are additional accounts beyond these 1.5 million that were exposed by the breach; the company’s statement seems to be focusing on the number of cards it can confirm that thieves offloaded from its systems.
It’s also unclear how Global Payments’ timeline of the incident meshes with that of MasterCard and Visa. In an alert sent to card-issuing banks that was first reported early Friday by KrebsOnSecurity.com, the card associations said the window of vulnerability for the breached processor (at that time unnamed) was between Jan. 21, 2012 and Feb. 25, 2012. The alert also said that full Track 1 and Track 2 data was exposed, meaning thieves could use the stolen information to counterfeit new cards.
Yet, in a statement Friday, Global Payments said its own security systems identified and self-reported the breach, which it said was detected in early March 2012: “It is reassuring that our security processes detected an intrusion,” the company said.
In its follow-up statement Sunday, the company mentioned only that “Track 2 card data may have been stolen, but that cardholder names, addresses and social security numbers were not obtained by the criminals.” (For more info on the data contained on Track 1 and Track 2, see this explainer).
In any event, The Wall Street Journal is reporting that Visa took the step over the weekend of distancing itself from Global Payments, by removing the company from its list of those it considers to be compliant service providers. That list is huge, and is available here (PDF).
At the same time, a technical glitch affecting the Visa network barred some people around the United States from using their credit and debit cards for about 45 minutes on Sunday. Visa told The Associated Press that the outage was caused by an update it made to its system, but that the problem was unrelated to the Global Payments breach.
The apparent discrepancy over the timeline of the Global Payments breach and the means by which it was discovered and reported leaves several unanswered questions: Was the initial alert by Visa and MasterCard that prompted this story related to a separate breach? If so, was Global Payments involved?
Stay tuned; Global Payments holds a public conference call at 8:00 a.m. ET Monday to discuss the incident, and to hopefully shed more light on these questions.




Here we go again. Contained?? These people have no shame.
Anyone that thinks breaches are preventable will hold all organizations to unachievable expectations and those people should put their cards away and revert to cash.
We need to migrate to a mindset that measures companies based on their response process and hold the court of public opinion at bay until the facts come to light.
Keeping data safe from vanilla hackers isn’t an unreasonable or unachievable expectation. There’s been organizations doing that for some time now. Apple is an example of good internal security. Furthermore, there are organizations using OpenBSD, hardened Linux desktops and secure thin client devices to reduce infection risks.
Far as data goes, there are designs for provably secure databases, file systems, and inline crypto. Companies use Windows, SQL server, unencrypted storage and insecure network configurations instead. Same with credit card systems. There’s a ton of designs that outright prevent many common attack vectors cheaply. Banks use mag stripes instead. $10 USB-type devices for more secure logins and stuff. Companies just use username/password instead.
The reason is all about marketing. Time to market, productivity & profit margins are the most important things to them. People rarely pay extra for safer, less convenient solutions. Hence, companies rarely build or deploy them. They’ve also conditioned people to think that breaches & hacks are totally inevitable. That it’s impossible to design an OS or app that can prevent a 14 year old from totally controlling your system via a web page load. (There’s quite a few OS products that can prevent that by design, but you don’t need to know that.)
There’s nothing impossible about greatly reducing the risk of a breach or exploit. Just look at Microsoft’s improvements after introducing SDL. Look at methodologies like SQUARE requirements and Cleanroom software. Companies can do way better than they’re doing. They’re just making excuses. Americans need to stop letting them get away with it. I can understand if they’re playing it smart, trying really hard, and get breached by sophisticated attackers. Right now, though, they spend more money on security theater than security. That’s the problem.
Nick P
schneier.com
You said that Global Payments, “said in a statement Sunday that the incident involved at least 1.5 million ACCOUNTS.” Unless that is a statement they whispered into your ear, you have your facts wrong again. Their published statement said, “less than 1,500,000 CARD NUMBERS may have been exported. The
investigation to date has revealed that Track 2 card data may have been stolen, but that cardholder names, addresses and social security numbers were not obtained.” (Capitalization added by me.)
The inaccurate reporting from your blog is not helping.
The changing scope of the breach comes from the way in which Global Payments has been handling its information sharing with Visa and MasterCard. I appreciate getting your updates since it allows me to stay current and vigilant. It’s obvious that the full impact is still being assessed.
Responsible journalists need to understand the facts and need to understand breach identification and investigation processes.
There is no mysterious discrepancy in the breach timeline. The breach occurred during Jan and Feb but wasn’t discovered by GP until March.
The so-called ‘discrepancy’ is the difference between when it occurred and when it was discovered. Duh.
The discrepancy IS significant.
What kind of monitoring systems and/or incident response process alerts you of incidents a month AFTER?
I think the discrepancy can mean one of two things:
1. It was an extended breach, meaning the attackers didn’t just get in and get out, but maintained access over a long period of time. Eventually GP caught wind of it and shut them out.
2. The breach was discovered by a third party, and GP is trying to sound more responsive and capable than they actually were.
“What kind of monitoring systems and/or incident response process alerts you of incidents a month AFTER?”
The problem is linked to weak operational processes to ensure trained staff SEE the alerts and know how to respond.
Sadly, there is a mountain of research that shows the response time for many breaches is often much longer than this– 3 to 6 MONTHS in many cases.
I agree with the issue being having the necessary staff trained to discover and respond to incidents. As for the 3 to 6 month response time, you’re now talking about 3rd parties tracing fraudulent card use BACK to the point of the breach.
As for internal monitoring, either you catch it right away, or not at all. Few companies have the resources to spend more than one day to look at one day’s worth of logs and alerts.
This is due in large part to the delay in fraudulent use of this information. It is very difficult for someone to know a third party is siphoning off your data until that data is utilized in a fraudulent manner. The creation of counterfeit cards takes time… once it was done, the company took notice and issued a release through the proper channels (PULSE, MasterCard Online, VISA, etc) through their security bulletins and CAMs notices to the banks… which is likely how this situation was leaked to the public (something that virtually never occurs). These situations are not rare… it’s the public disclosure is uncommon in this case.
“It is very difficult for someone to know a third party is siphoning off your data…”
That’s the whole point of almost a third of the PCI requirements. To identify incidents like a third party siphoning off your data. Being compliant is no guarantee you’ll catch them, but to be compliant you have to at least demonstrate you have the ability to detect and stop intrusions…
PCI-DSS is a flat out joke. Being certified compliant means you got a QSA to believe that you were compliant. PCI-DSS provides very little real world protection for these organizations, but it does significantly increase costs for them. Processors and institutions waste security budgets to become compliant instead of being able to spend the money on real security initiatives. PCI-DSS was designed to allow Visa/Mastercard/Discover/AMEX to shift all liability onto processors and issuing institutions. That being said, institutions and processors are generally where the majority of liability lies.
I knew something major was going on when I had two cards cloned within days of each other! This is just hitting the news yet I was a victim the first week of March!
Brian – the so-called “window of vulnerable transactions” is Visa’s technical term for the period of time when the attacker who did the breach was in the system and could take track data. It’s related to the date of discovery by the fact that a breach was discovered after the breach occurred. Most consumers won’t even see the fraudulent transactions until the billing cycle closes on those transactions that were funded by their Issuing bank. The big no-no’s here are that full track data could be exfiltrated and the attacker could breach them in the first place.
But full track data was not “exfiltrated” — GPN is stating that only the card numbers were exported. I think you can only read the statement one way, that Track 2 data was stolen, but the only data on that track that was stolen was the card number, not the name, address, etc.
Tim: You’re arguing semantics. Credit card “Accounts”, “Numbers” and Track 1/Track 2 data imply slightly different things, but would all be counted the same. Swap any of those terms and the breach is still affecting 1.5 million credit cards.
To all: Note that PCI forbids the storage of ANY track data. The fact that they say the data was “extracted” implies that Global was actually storing Track data. CardSystems Services was effectively shut down by VISA and AMEX seven years ago for less.
Adrian – I agree with your main point but have a question about your note: is it not possible that if the attackers had prolonged access to GP’s systems (as seems to be the case from what they have said so far) that they may have been capturing live track data as payment transactions were processed? If this is possible then they may not have been storing track data surely.
I ask as an interested IT professional who is not a specialist in either security or card payment systems.
Ian: Absolutely, the track data could have been captured on the wire, and that would help explain how they were able to capture it in the first place. PCI forbids storing such data, but does not require it to be encrypted in transmission, as long as it isn’t crossing public networks (i.e. the Internet).
Adrian, my main objective was to point out that the author said more than 1.5 million were involved in the breach when in fact fewer than 1.5 million is what GPN stated. I should also have capitalized “more” and “fewer,” so my bad.
Second, they did not say “extracted,” they said “exported.” Although I agree that is semantics, it does not prove they were storing numbers (see Ian’s comment).
Third, I disagree with your comment that the distinction between an account and a credit card number is semantics. Crooks can do a lot with an account’s data because it would include name, address, card number, expiration date, etc. A credit card number is just that: a number. There is not much a crook can do with just a number, and that’s why we haven’t been hearing of fraudulent transactions.
Tim: I said nothing about proof. What I’m trying to do here is read between the lines, in liu of details. I could be completely wrong, but you usually don’t say data was “exported” when someone captures it in real time as it crosses the network. The fact that GP chose the term “export” makes it very likely that data was exfiltrated from a database.
Again, this is just my interpretation. An effort to read between the lines, based on my experience working for a credit card processor of a similar size and doing incident response on similar (though MUCH smaller) incidents.
Yes, I agree — very likely but not in fact.
If only Track 2 data was taken, doesn’t that indicate that the thieves got into this big customer’s accounts, seized what was going out, and were unable to take what was coming back, which would have included Track 1 and was encrypted?
Good question. I’m going by what the company said, i.e., that only card numbers were stolen.
Here is what the CEO said, “The company believes that fewer than 1.5 million card numbers may have been stolen and that this theft is confined to our North American processing system.
Importantly, investigating to-date has revealed that the theft involved Track 2 card data only. We do not believe that Track 1 card data was taken or that cardholder names, addresses, Social Security numbers or consumer banking information was obtained by the criminals.”
Penalties are pretty stiff for public company executives who lie, so I don’t think he is lying. Also, I’ve followed the career of this CEO for many years, from when he was at First Financial Management in the 1990s to when he joined National Data Corp., which later spun out GPN. I don’t think his intergrity can be questioned.
I wonder if they are improperly using the term “track data”, and they actually mean “data stored in track 2”. Storing track data (which is the raw data off the magnetic stripe, and includes more than just payment information) is a big PCI violation. Storing allowed elements from either track is NOT a violation.
I’m not sure it matters though, as there has been no mention of encryption, and if they were storing unencrypted data, that’s nearly as blatant a violation. In other breaches, like Sony’s, the press releases were very quick to point out that credit card data accessed by attackers was properly encrypted.
After reading the WSJ article that just came out that maintains expiration date and security code data was stolen, I’m afraid I was taking Garcia too literally when he said that “card numbers” were stolen. It looks like Garcia defines a “card number” as not only the number but also the expiration date and the security code. Is that how most people in the industry define it? Brian, is that how you define it?
No, it is definitely not standard for the term “card numbers” to refer to, or include other sensitive data elements.
When card numbers are stolen, other elements typically do not get mentioned if they do not increase the severity of the breach. Therefore, you can assume “card numbers” might also include the amount, the expiration date, the batch number, and other fields related to the transaction. However, if the cardholder’s name can be connected to the credit card number in the breached data set, the combination of the two are now considered “personal information” under breach law in many states.
This is an important distinction. Now you not only have an issue with PCI compliance and the card brands, but with state breach laws.
The security code and track data should never be stored, so again, if the bad guys got their hands on this kind of sensitive data, either Global was storing it and never should have been PCI compliant, or as suggested earlier, the attackers were able to capture authorization traffic off the wire as they came in from merchants.
If not the latter, this will be quite the scandal, as:
Storing Track Data = Not PCI Compliant
Storing Security Codes = Not PCI Compliant
Storing Unencrypted CCN = Not PCI Compliant
These are the first things you look for as a QSA when assessing a service provider, and yet… they were certified PCI compliant.
There is no basis to jump to the conclusion that Global is trying to hide or misrepresent anything. From all accounts they self reported the incident and were working with law enforcement to identify the hackers.
The quaestionable activity in my opinion was Krebs reporting that up to 10 million accounts were compromised based on a small sampling of one credit union report.
It is interesting how this story has played out. When I ran my piece on Friday, I still did not know for sure if Global Payments was involved. In fact, I never mentioned them in my story. That was dug up by the Wall Street Journal.
I continue to be nagged by the possibility that the breach I was chasing may be unrelated to the GPN incident. Hence, your calling my reporting what I was hearing from sources about an unnamed merchant breach “questionable” is itself questionable. Thanks for your comment, all the same.
They ARE hiding something. Quite a lot of something. All the details.
As long as they leave us in the dark, we’ll analyze every shred they give us. We want to know what’s going on with our money and personal data. I personally think they owe us the full details the moment they lose our information and decide to issue a press release.
Either have all the info ready for the press release, or don’t complain when rumors start flying around.
It took Heartland a few weeks to come to this conclusion, if I recall.
They may be mostly hiding ignorance. It’s more likely they don’t know what they don’t know than that they’re lying about what they do know.
ABC News online quotes and refers to Brian at length (put online about five hours ago) in connection with this security breach :
http://abcnews.go.com/Business/questions-answers-security-breach-acknowledged/story?id=16054236#.T3n819mqlcA
They are selling these pretty cheap on carder.pro. You can make an account there if you can get a few vouches. Nice way to get some early christmas gifts for your family, courtesy of Visa.