The recent hacker break-in at Sony Pictures Entertainment appears to have involved the theft of far more than unreleased motion pictures: According to multiple sources, the intruders also stole more than 25 gigabytes of sensitive data on tens of thousands of Sony employees, including Social Security numbers, medical and salary information. What’s more, it’s beginning to look like the attackers may have destroyed data on an unknown number of internal Sony systems.
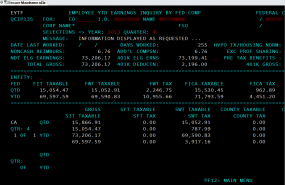
Screen shot from an internal audit report allegedly stolen from Sony and circulating on file-trading networks.
Several files being traded on torrent networks seen by this author include a global Sony employee list, a Microsoft Excel file that includes the name, location, employee ID, network username, base salary and date of birth for more than 6,800 individuals.
Sony officials could not be immediately reached for comment; a press hotline for the company rang for several minutes without answer, and email requests to the company went unanswered. But a comprehensive search on LinkedIn for dozens of the names in the list indicate virtually all correspond to current or former Sony employees.
Another file being traded online appears to be a status report from April 2014 listing the names, dates of birth, SSNs and health savings account data on more than 700 Sony employees. Yet another apparently purloined file’s name suggests it was the product of an internal audit from accounting firm Pricewaterhouse Coopers, and includes screen shots of dozens of employee federal tax records and other compensation data.
The latest revelations come more than a week after a cyberattack on Sony Pictures Entertainment brought down the company’s corporate email systems. A Sony spokesperson told Reuters that the company has since “restored a number of important services” and was “working closely with law enforcement officials to investigate the matter.”
Several media outlets reported at the time that Sony employees had been warned not to connect to the company’s corporate network or to check email, and noted that Sony’s IT departments had instructed employees to turn off their computers as well as disable Wi-Fi on all mobile devices.” Other reports cited unnamed investigators pointing to North Korean hackers as the source of the attack, although those reports could not be independently confirmed.
Such extreme precautions would make sense if the company’s network was faced with a cyber threat designed to methodically destroy files on corporate computers. Indeed, the FBI this week released a restricted “Flash Alert” warning of just such a threat, about an unnamed attack group that has been using malware designed to wipe computer hard drives — and the underlying “master boot record” (MBR) on the affected systems — of all data.
KrebsOnSecurity obtained a copy of the alert, which includes several file names and hashes (long strings of letters and numbers that uniquely identify files) corresponding to the file-wiping malware. The FBI does not specify where the malware was found or against whom it might have been used, noting only that “the FBI has high confidence that these indicators are being used by CNE [computer network exploitation] operators for further network exploitation.” The report also says the language pack referenced by the malicious files is Korean.
The FBI alert references several network traffic “signatures” that organizations can use to detect the traffic seen in previous attacks from this malware — traffic that appears to beacon back to (most likely compromised) systems in Thailand, Poland and Italy. But the alert also says this type of vigilance may only serve to let organizations know that their files are currently in the process of being deleted.
“The following Snort signature can be used to detect the beacon traffic, though by the time the beacons occur, the destructive process of wiping the files has begun,” the alert warned.
Here’s the Snort signature, in case this is useful for any readers who didn’t get this memo:
Alert tcp any any – > [88.53.215.64, 217.96.33.164, 203.131.222.102] [8080, 8000] (msg: “wiper_callout”;
dsize:42; content: “|ff ff ff ff|”; offset: 26; depth: 4; sid: 314;
Update: 1:58 p.m. ET: Multiple sources are reporting that the links to the torrents for the stolen Sony internal data were posted on Pastebin late Monday morning. Less than an hour after that post went live, the individual hosts that were sharing copies of the Sony data came under sustained denial-of-service attacks apparently aimed at keeping the files from being shared with other torrent users.
Also, the security guys over at Packetninjas have posted a useful write-up on a malware sample they spotted from early July 2014 that matches the file name of the malware described in the FBI’s Flash alert about the file-wiping malware. Packetninjas notes that the file also was calling home to the same control server in Thailand that was documented in this week’s FBI alert.
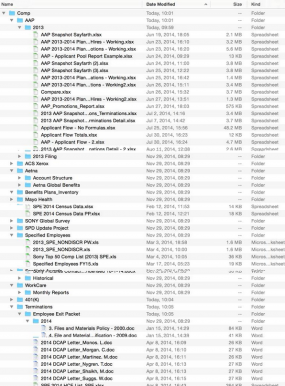
This file directory tree, included in the leaked data, offers a glimpse into the sheer volume of files apparently compromised in this breach.
This is a developing story. More to come. Stay tuned.




Pure curiosity: what’s up with the DDOSing of the distributors of the file? Are you saying that someone who runs a botnet decided to be altruistic and save the victims’ bacon – or that Sony’s got its own pet botnet? Either strikes me as weird…
So, here’s a *7 year old* article wherein Sony Pictures’ director of information security justifies his company’s lax infosec practices:
http://www.cio.com/article/2439324/risk-management/your-guide-to-good-enough-compliance.html
Seems this guy was paid $300k a year mainly to justify why Sony didn’t protect a damned thing – and yes, he’s still in the same position now.
The Snort rule needs some work see below–
alert tcp $HOME_NET any -> [88.53.215.64/32,217.96.33.164/32,203.131.222.102/32] [8080,8000] (msg: “FLASH-A-000044-MW-wiper-callout”; flow:established; dsize:42; content: “|ff ff ff ff|”; offset: 26; depth: 4; classtype:malware-cnc; sid: 1,000,001; rev:2;)
No spaces between IP lists, add /32 for specific IP, add flow, add classtype, change sid to standard local convention > 1,000,000, add revision.
So, uh Jason, Mr. Spaltro. Can I call you Jason? ah good. I just got one more question for you and I’ll get outta your way, because it looks like you’ve got your hands full at the moment. Now about this hack and all these missing data files you say were deleted by someone from North Korea? I have to tell you that, if you had better internal security practices mandated, you know that this sort of thing wouldn’t have happened right?, and also since you’re the only one with the keys to the kingdom and the fact that you’ve seemed frustrated that you didn’t get the needed security items through out the years you’ve been asking for from the heads of the studio, so it would be logical, bear with me here. wouldn’t it make scene to perpetuate a hack internally and blame it on an external party all the while in your passive aggressive nature, you also get back at those whom have held you back in your position here as executive director of information security at Sony Pictures Entertainment.
Officer Arrest this man!
I seem to have found the correlation of the email sent from dfrank1973.david@gmail.com, it’s something to do with beer, i like beer, seems these sony hackers like beer too. that was probably their demand, they wanted beer.
https://www.google.com/search?q=%22frank1973.david%40%22
now if you don’t mind chief, Joe and I are going to go back to work and fix this protestor problem we got goin on here in the city.
Brian – any information regarding your upcoming movie deal part of the take? Any chance this is in retaliation for that deal?
Would anyone be able to share a copy of the FBI’s flash alert?
http://krebsonsecurity.com/2014/12/sony-breach-may-have-exposed-employee-healthcare-salary-data/comment-page-1/#comment-337635
Looks like there will be some amusing press reports and more bad days in the office when the mainstream press catches up…
Always wondered what senior movie exec’s Amex cards would look like.
2013
│ │ │ │ ├── Amex\ -\ October\ 2013.pdf
│ │ │ │ ├── Amex\ 12-25-13.pdf
│ │ │ │ ├── Amex\ 3-27-13.pdf
Also this
CBS.QueenLatifah.fullyexedcontract.tif
│ │ ├── CBS.Seinfeld5thcycle.revisedcontracts.tif
│ │ ├── CBS.Seinfeld5thcycle.revisedsignedcontract.pdf
Will no doubt make fun reading…
any updates on this? they apparently released a 500 gb file dump. not that anyone could have possibly downloaded that yet but I’m very curious about what’s inside.