It seems nearly every day we’re reading about Internet attacks aimed at knocking sites offline and breaking into networks, but it’s often difficult to visualize this type of activity. In this post, we’ll take a look at multiple ways of tracking online attacks and attackers around the globe and in real-time.
A couple of notes about these graphics. Much of the data that powers these live maps is drawn from a mix of actual targets and “honeypots,” decoy systems that security firms deploy to gather data about the sources, methods and frequency of online attacks. Also, the organizations referenced in some of these maps as “attackers” typically are compromised systems within those organizations that are being used to relay attacks launched from someplace else.
The Cyber Threat Map from FireEye recently became famous in a 60 Minutes story on cyberattacks against retailers and their credit card systems. This graphic reminds me of the ICBM monitors from NORAD, as featured in the 1984 movie War Games (I’m guessing that association is intentional). Not a lot of raw data included in this map, but it’s fun to watch.
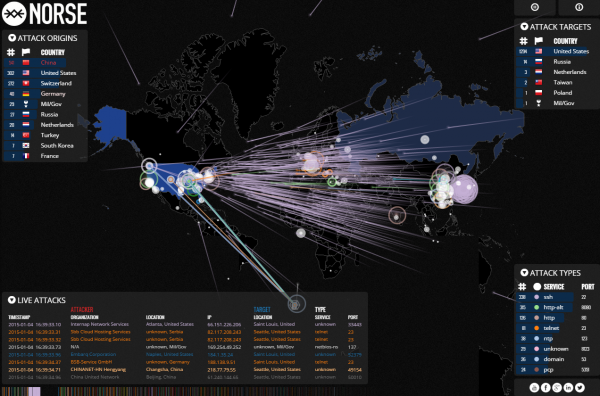
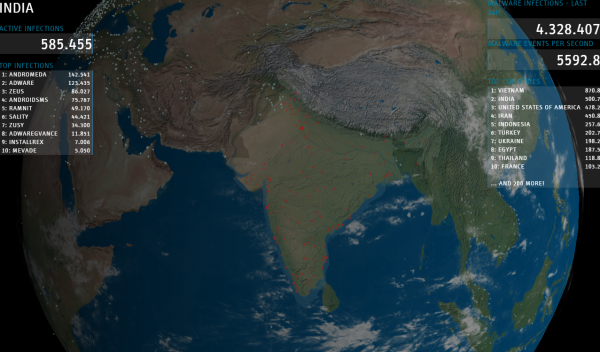
My favorite — and perhaps the easiest way to lose track of half your workday (and bandwidth) comes from the folks at Norse Corp. Their map — IPViking — includes a wealth of data about each attack, such as the attacking organization name and Internet address, the target’s city and service being attacked, as well as the most popular target countries and origin countries.
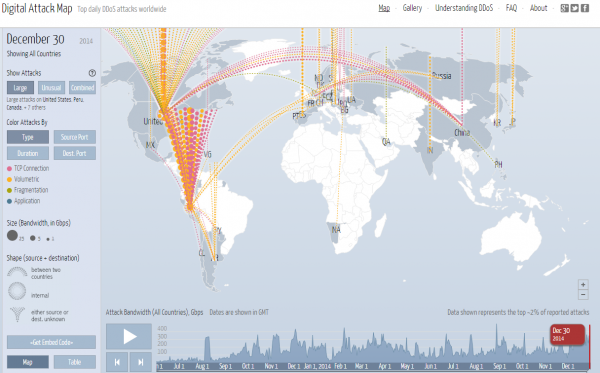
Another live service with oodles of information about each attack comes from Arbor Networks‘ Digital Attack map. Arbor says the map is powered by data fed from 270+ ISP customers worldwide who have agreed to share anonymous network traffic and attack statistics. This is a truly useful service because it lets you step back in time to attacks on previous dates going all the way back to June 2013.
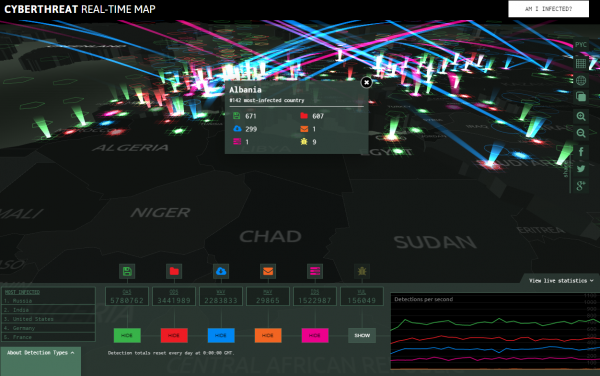
Kaspersky‘s Cyberthreat Real-time Map is a lot of fun to play with, and probably looks the most like an interactive video game. Beneath the 3-D eye candy and kaleidoscopic map is anonymized data from Kaspersky’s various scanning services. As such, this fairly interactive map lets you customize its layout by filtering certain types of malicious threats, such as email malware, Web site attacks, vulnerability scans, etc.
The Cyberfeed, from Anubis Networks, takes the visitor on an automated tour of the world, using something akin to Google Earth and map data based on infections from the top known malware families. It’s a neat idea, but more of a malware infection map than an attack map, and not terribly interactive either. In this respect, it’s a lot like the threat map from Finnish security firm F-Secure, the Global Botnet Threat Activity Map from Trend Micro, and Team Cymru‘s Internet Malicious Activity Map.
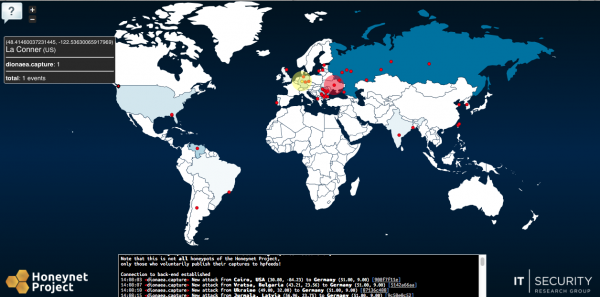
The Honeynet Project‘s Honey Map is not super sexy but it does include a fair amount of useful information about real-time threats on honeypot systems, including links to malware analysis from Virustotal for each threat or attack.
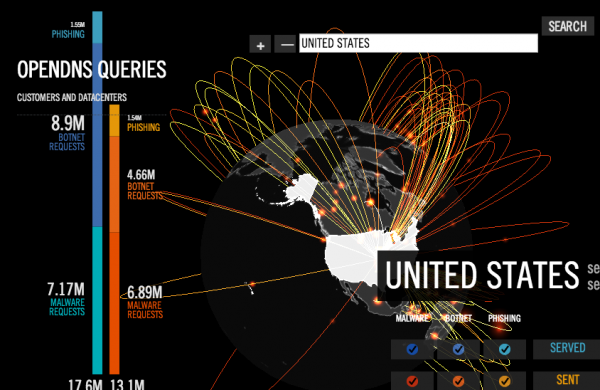
Additionally, the guys at OpenDNS Labs have a decent attack tracker that includes some nifty data and graphics.
If all these maps are a bit too Hollywood for you, then you’ll love the simplicity and humor behind PewPew, which derives its name from the added sound effects. Might want to turn the volume down on your computer’s speakers before visiting this map (especially if you’re at work while viewing it).
Speaking of attacks, some of you may have noticed that this site was unreachable for several hours over the last few days. That’s because it has been under fairly constant assault by the same criminals who attacked Sony and Microsoft’s gaming networks on Christmas Day. We are moving a few things around to prevent further such disruptions, so you may notice that some of the site’s features are a tad flaky or slow for a few days. Thanks for your patience as we sort this out. And Happy New Year, dear readers!
Update, 1:25 p.m. ET: An earlier version of this post incorrectly stated that the PewPew service was fed with data supplied by Mandiant. The story above has been changed to reflect that.




interesting infographics!
Hi, Brian! Thanks for the mention on PewPew.
However, it is not based on Mandiant data. If you use it without the location flags (like china_mode, for instance) it uses aggregated data from scanning and probing attacks from Arbor Networks as a weight for the randomness. Here is a link for it (with all the sound effects on): http://ocularwarfare.com/ipew/?allfx=1
Since it uses the same aggregated distributions as the actual attacks seen in real life, it can be a pretty accurate simulation, without all this pesky data gathering. 🙂
Also, please try dprk_mode. Very fashionable these last few weeks.
I’d only ever heard of the IPViking one before, will definitely check out the others.
Also, Happy New Year, Brian.
Nice job Anonymous. Always great to receive un-credited Happy New Year wishes from somone. durp!
Thanks for the link, Brian.
As always, you are a wealth of valuable information.
Russian czar Peter the Great influenced the content of the Norse Corp. graphic. Look at the attack targets in the upper right hand corner. Russia and the Kingdom of the Netherlands hold positions number two and three. Peter so admired the Dutch that he used their flag as a model for the Russian flag. He merely changed the order of the colors. As for the flags in the graphic, the colors blue, red and white had a bad day.
When your site timed out over the past few days, the first thing I thought was that those Lizard Brain Kids were at it again.
It seems you hit a nerve. Keep up the good work!
and the us gov still thinks NorKorz did the hack on sony. meh! i know who it was. n-e-wayz. happy new yearz tuz ebrybodies. keeps ups the goodz werkz brian. youz iz almost there, but do not forgets how you gets tharz.
‘the ending is just the beginning
Nothing like a deep throat who is soooo underground they go out of their way to mispell every single word.
Wait you did do that on purpose right. I hope.
Oooh, that’s deep. ‘The ending is just the beginning’ The hair is standing up on the back of my neck. Did you just take that from the netflix movie you watched last night?
Ah, the price of success! Seems you hit a nerve, Brian. Hang in there, the service and information you provide are invaluable!
I think Sony themselves are the ones who took North Korea offline. I think if you look really hard at the Norse map, you will still see Sony popup in the attackers column every now and then.. They need to hire lizard scrubs….haha
Steve Gibson suggests that ISP’s are being irresponsible for not blocking ip addressses going out from their network, that aren’t in their actual address range, as a simple way to stop most of these ddos attacks.
I find it interesting Kapersky has Russia as the #1 infected country in the world and not USA.
LizardSquat is the GoP. they are not the NorKors, nor did they ever communicate with them on this hack. it was an inside job and LizSquat haz more friends in the sony as well as other production companies it the hollywood area. it’s not my place to judge here, just to report.
Excellent factual and timely reporting! Jack! I just breathed a sigh of relief knowing that Jack is on top of the ‘truth’.
head meet palm, palm meet head.
That’s interesting enough, but realistically what can one do when one is under such an attack?
If you have a lot of money, there are solutions. If you don’t, then there aren’t many except disconnect your service and wait for it to stop. Even if you do have a lot of money, that still doesn’t mean you’re safe.
The idiots from Lizard Squad like to pretend that DDoS is incredibly easy to avoid and deal with, but it isn’t, really. In theory, it is simple, but the practicality of solutions in the real world isn’t simple at all.
…no link for the OpenDNS map…
http://labs.opendns.com/security-graph/
Requires limited beta access:
http://labs.opendns.com/security-graph-contextual-search-application/
Happy New Year, Brian! Thanks for all the great information.
It helps to be aware.
Don’t know if you’ve addressed the walk-by scanners or not. They can get your credit/debit card info without you knowing it just by walking by you. It happened to my son.
The thieves immediately went to a McDonald’s & a couple of other local stores, bought something & got cash back. Why would McDonald’s give you $250 in cash back. mmmmhh…
The bank could immediately tell what happened, canceled the card & made the account good. In fact, the bank rep had had the same thing happen to him.
Wouldn’t you think the bank would want to report this to the police? No! The answer to whether to report it was a very casual, “You can if you want to…”
We now all use metal wallets. ;^)
We check your site daily just to see what’s threatening. ;^)
Take care & stay safe!
Sounds like a very poor implementation of NFC all round:
– all card information bar the PAN and expiry should be encrypted, and useless even if acquired. This does not expose enough information for counterfeit or CNP fraud.
– the merchant’s POS system should expect a chip card and refuse any transaction where the card is not genuine (but I’ll assume you’re in the US and they can still fallback to mag stripe).
– as soon as a transaction occurs on the card that is out-of-sync with the transaction counter in either the MVP/EPAL or NFC chip (ie. on a counterfeit card) that card should be restricted until the cardholder can be contacted.
Reading an NFC card through someone’s pocket cannot obtain either a PIN or signature. Small transactions might go through without these (under Visa small-ticket conditions for example) but not the $250+ you describe, nor should any merchant be refunding a purchase in cash – it should be reversed to the card. It sounds highly suspicious that a merchant would be that compliant in processing such a request. In any case, in the coincidence of scenarios above NFC security is the least of your worries.
No mention of AlienVault?
http://www.alienvault.com/open-threat-exchange/dashboard#/threats/top
^signup wall^ :/
There is a very interesting bit of code in fireeye’s map.js:
n=Math.round(1200*Math.random())+200;randSeconds=n/1e3,setTimeout(function(){t+=e*randSeconds,$(“#totalAttacksToday” …
😉
Thanks so much for combining these cool maps. Norse is also my fav!!
The Norse maps show constant bombardment of attacks against the United States, from China and Russia
Completely useless junk.
OpenDNS map:
http://labs.opendns.com/global-network/
How soon before the hackers have contests on who can light up these threat maps the most?
They will try and make them dance like the Christmas lights youtube videos.
And don’t forget, china_mode=1!
Don’t miss the hilarious help string trashing this whole concept at IPew:
I second that notion. I am always a bit skeptical when I see data viz pages like these and wonder about the statistical methods used AND the data sources they are pulling from. Graphics like statistics can portray anything you want it to.
That being said from a purely aesthetic POV most are pretty cool looking.
My $0.02.
Keep up the good work, Krebs!
Any particular reason why so many attacks are focused on St Louis?
Mike, there is a large hosting/ISP company there, Savvis, and when they register their IP addresses, they give their headquarters address in St. Louis. However the IP addresses are probably in use at data centers all over the country, and these “eye candy” attack mapping sites don’t know the precise locations.
St. Louis metro area has a notably large census of Department of Defense contractors: Geospatial Intelligence Agency (formerly Rand Corporation/”Defense Mapping Agency,”) Lockheed-Martin, McDonnell-Douglas, Boeing, Graybar, military apparel and munitions manufacturers, actual military bases (army, air force), etc.
It ain’t all beer and pet food.
And btw those two are related–brewers have been selling their spent grains to owners of livestock for many decades.
Perhaps these industries attract more than average interest…
One day I hope launch attack big enough to watch with IPviking
I has to learn for my exams but I assume I will be starring on my screen and watch IPViking the whole night….
Thank you in advance I think I will be able to have some fun with it.
…and for a site that belongs on no list of “cool” sites for attack graphics is this gem:
http://www.securitywizardry.com/radar.htm
If wondering why Australia is not listed as attackers, it’s because the Cricket is on 🙂
Hi Brian,
I have been following the Charlie Hebdo French language news online, and ran across this-
http://mobile.lemonde.fr/societe/live/2015/01/07/en-direct-des-coups-de-feu-au-siege-de-charlie-hebdo_4550635_3224.html
Agence Presse France says that several readers alerted them to hacked pages in the city Val d’Oise. They say their reporters are working on it.
Interested in your take on this.