The online attack service launched late last year by the same criminals who knocked Sony and Microsoft’s gaming networks offline over the holidays is powered mostly by thousands of hacked home Internet routers, KrebsOnSecurity.com has discovered.
Just days after the attacks on Sony and Microsoft, a group of young hoodlums calling themselves the Lizard Squad took responsibility for the attack and announced the whole thing was merely an elaborate commercial for their new “booter” or “stresser” site — a service designed to help paying customers knock virtually any site or person offline for hours or days at a time. As it turns out, that service draws on Internet bandwidth from hacked home Internet routers around the globe that are protected by little more than factory-default usernames and passwords.

The Lizard Stresser’s add-on plans. Despite this site’s claims, it is *not* sponsored by this author.
In the first few days of 2015, KrebsOnSecurity was taken offline by a series of large and sustained denial-of-service attacks apparently orchestrated by the Lizard Squad. As I noted in a previous story, the booter service — lizardstresser[dot]su — is hosted at an Internet provider in Bosnia that is home to a large number of malicious and hostile sites.
That provider happens to be on the same “bulletproof” hosting network advertised by “sp3c1alist,” the administrator of the cybercrime forum Darkode. Until a few days ago, Darkode and LizardStresser shared the same Internet address. Interestingly, one of the core members of the Lizard Squad is an individual who goes by the nickname “Sp3c.”
On Jan. 4, KrebsOnSecurity discovered the location of the malware that powers the botnet. Hard-coded inside of that malware was the location of the LizardStresser botnet controller, which happens to be situated in the same small swath Internet address space occupied by the LizardStresser Web site (217.71.50.x)
The malicious code that converts vulnerable systems into stresser bots is a variation on a piece of rather crude malware first documented in November by Russian security firm Dr. Web, but the malware itself appears to date back to early 2014 (Google’s Chrome browser should auto-translate that page; for others, a Google-translated copy of the Dr. Web writeup is here).
As we can see in that writeup, in addition to turning the infected host into attack zombies, the malicious code uses the infected system to scan the Internet for additional devices that also allow access via factory default credentials, such as “admin/admin,” or “root/12345”. In this way, each infected host is constantly trying to spread the infection to new home routers and other devices accepting incoming connections (via telnet) with default credentials.
The botnet is not made entirely of home routers; some of the infected hosts appear to be commercial routers at universities and companies, and there are undoubtedly other devices involved. The preponderance of routers represented in the botnet probably has to do with the way that the botnet spreads and scans for new potential hosts. But there is no reason the malware couldn’t spread to a wide range of devices powered by the Linux operating system, including desktop servers and Internet-connected cameras.
KrebsOnSecurity had extensive help on this project from a team of security researchers who have been working closely with law enforcement officials investigating the LizardSquad. Those researchers, however, asked to remain anonymous in this story. The researchers who assisted on this project are working with law enforcement officials and ISPs to get the infected systems taken offline.
This is not the first time members of LizardSquad have built a botnet. Shortly after their attack on Sony and Microsoft, the group’s members came up with the brilliant idea to mess with the Tor network, an anonymity system that bounces users’ connections between multiple networks around the world, encrypting the communications at every step of the way. Their plan was to set up many hundreds of servers to act as Tor relays, and somehow use that access to undermine the integrity of the Tor network.
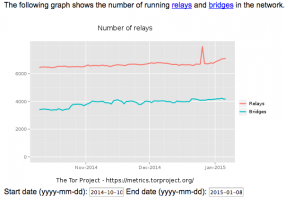
This graphic reflects a sharp uptick in Tor relays stood up at the end of 2014 in a failed bid by the Lizard Squad to mess with Tor.
According to sources close to the LizardSquad investigation, the group’s members used stolen credit cards to purchase thousands of instances of Google’s cloud computing service — virtual computing resources that can be rented by the day or longer. That scheme failed shortly after the bots were stood up, as Google quickly became aware of the activity and shut down the computing resources that were purchased with stolen cards.
A Google spokesperson said he was not able to discuss specific incidents, noting only that, “We’re aware of these reports, and have taken the appropriate actions.” Nevertheless, the incident was documented in several places, including this Pastebin post listing the Google bots that were used in the failed scheme, as well as a discussion thread on the Tor Project mailing list.
ROUTER SECURITY 101
Wireless and wired Internet routers are very popular consumer devices, but few users take the time to make sure these integral systems are locked down tightly. Don’t make that same mistake. Take a few minutes to review these tips for hardening your hardware.
 For starters, make sure you change the default credentials on the router. This is the username and password that were factory installed by the router maker. The administrative page of most commercial routers can be accessed by typing 192.168.1.1, or 192.168.0.1 into a Web browser address bar. If neither of those work, try looking up the documentation at the router maker’s site, or checking to see if the address is listed here. If you still can’t find it, open the command prompt (Start > Run/or Search for “cmd”) and then enter ipconfig. The address you need should be next to Default Gateway under your Local Area Connection.
For starters, make sure you change the default credentials on the router. This is the username and password that were factory installed by the router maker. The administrative page of most commercial routers can be accessed by typing 192.168.1.1, or 192.168.0.1 into a Web browser address bar. If neither of those work, try looking up the documentation at the router maker’s site, or checking to see if the address is listed here. If you still can’t find it, open the command prompt (Start > Run/or Search for “cmd”) and then enter ipconfig. The address you need should be next to Default Gateway under your Local Area Connection.
If you don’t know your router’s default username and password, you can look it up here. Leaving these as-is out-of-the-box is a very bad idea. Most modern routers will let you change both the default user name and password, so do both if you can. But it’s most important to pick a strong password.
When you’ve changed the default password, you’ll want to encrypt your connection if you’re using a wireless router (one that broadcasts your modem’s Internet connection so that it can be accessed via wireless devices, like tablets and smart phones). Onguardonline.gov has published some video how-tos on enabling wireless encryption on your router. WPA2 is the strongest encryption technology available in most modern routers, followed by WPA and WEP (the latter is fairly trivial to crack with open source tools, so don’t use it unless it’s your only option).
 But even users who have a strong router password and have protected their wireless Internet connection with a strong WPA2 passphrase may have the security of their routers undermined by security flaws built into these routers. At issue is a technology called “Wi-Fi Protected Setup” (WPS) that ships with many routers marketed to consumers and small businesses. According to the Wi-Fi Alliance, an industry group, WPS is “designed to ease the task of setting up and configuring security on wireless local area networks. WPS enables typical users who possess little understanding of traditional Wi-Fi configuration and security settings to automatically configure new wireless networks, add new devices and enable security.”
But even users who have a strong router password and have protected their wireless Internet connection with a strong WPA2 passphrase may have the security of their routers undermined by security flaws built into these routers. At issue is a technology called “Wi-Fi Protected Setup” (WPS) that ships with many routers marketed to consumers and small businesses. According to the Wi-Fi Alliance, an industry group, WPS is “designed to ease the task of setting up and configuring security on wireless local area networks. WPS enables typical users who possess little understanding of traditional Wi-Fi configuration and security settings to automatically configure new wireless networks, add new devices and enable security.”
But WPS also may expose routers to easy compromise. Read more about this vulnerability here. If your router is among those listed as vulnerable, see if you can disable WPS from the router’s administration page. If you’re not sure whether it can be, or if you’d like to see whether your router maker has shipped an update to fix the WPS problem on their hardware, check this spreadsheet. If your router maker doesn’t offer a firmware fix, consider installing an open source alternative, such as DD-WRT (my favorite) or Tomato.
 While you’re monkeying around with your router setting, consider changing the router’s default DNS servers to those maintained by OpenDNS. The company’s free service filters out malicious Web page requests at the domain name system (DNS) level. DNS is responsible for translating human-friendly Web site names like “example.com” into numeric, machine-readable Internet addresses. Anytime you send an e-mail or browse a Web site, your machine is sending a DNS look-up request to your Internet service provider to help route the traffic.
While you’re monkeying around with your router setting, consider changing the router’s default DNS servers to those maintained by OpenDNS. The company’s free service filters out malicious Web page requests at the domain name system (DNS) level. DNS is responsible for translating human-friendly Web site names like “example.com” into numeric, machine-readable Internet addresses. Anytime you send an e-mail or browse a Web site, your machine is sending a DNS look-up request to your Internet service provider to help route the traffic.
Most Internet users use their ISP’s DNS servers for this task, either explicitly because the information was entered when signing up for service, or by default because the user hasn’t specified any external DNS servers. By creating a free account at OpenDNS.com, changing the DNS settings on your machine, and registering your Internet address with OpenDNS, the company will block your computer from communicating with known malware and phishing sites. OpenDNS also offers a fairly effective adult content filtering service that can be used to block porn sites on an entire household’s network.
The above advice on router security was taken from a broader tutorial on how to stay safe online, called “Tools for a Safer PC.”




So – I don’t use the router part of the FIOS-interface box my ISP gave me, but I need to stop it from being botted – how to disable the functionality that botnets would use?
@patti: You shouldn’t have to worry about much more than making sure your router’s firmware is up to date, and that you changed the default password.
1) Ensure that the username and password is changed on the router
2) Ensure that remote administration is turned off (stops someone loading the GUI from outside the network)
3) Ensure the firmware is upto date on the router (or flash it to be 1 of the open firmwares if your router is supported)
To improve security by all means
1) Disable WPS
2) Ensure the wireless uses wpa2 (if your hardware supports it)
3) change the wireless encryption key
4) Avoid using power line adapters (sometimes sockets for neighbours run on the same circuit)
5) Disable guest logins on wireless (if your router has them) any traffic the guests use will show from your IP.
6) Change DNS to a trusted 3rd party DNS that will help protect such as opendns that Brian mentions.
There are probably plenty of other things that I have forgotten but worth doing the above
If your router support MAC filtering function, You should use that.
MAC address filtering is not an effective means of securing a wireless network. It doesn’t even keep out the novices. It only makes it more complicated for you when you want to add another device to the network. It is trivial to change your computer’s MAC address to match an already-authenticated user.
Also note that some of these cheap home routers will actually report connected MAC addresses. I bought a Pineapple and scanned the local air space. After seeing these devices fail so many penetration tests, I dumped mine and purchased a Watchguard XTM26W. That was the only device that was dark to the pineapple.
As noted, MAC address filtering is useless. Secure your password. Upgrade your firmware. Be vigilant.
You need to go to http://192.168.1.1/(this is your default gateway and this makes a connection from your local computers 0.0.0.0 address), use the default password and change it as soon as you can. I don’t know about the FIOS router’s, but let’s assume that it’s running a variant of ARM Linux; in which case it would be vulnerable to exploitation. Unfortunately unless your using commercial grade networking appliances updates are hard to find and the firmware is usually very buggy. Nevertheless, searching for a firm ware update would be in your best interest.
Change the default Admin passwords and usernames for the management interface , being this is a FIOS box it probably
uses Verizon’s Cloud Servers for authentication etc. So it
ain’t too much to worry about.
Regularly scan your registry and make sure to delete any suspicious folders. Do NOT delete any important or stock folders.
Mucking about in the Registry is not recommended for most users, as it is very easy to remove something that is actually legit and break something on your computer.
This has nothing to do with Wireless Security.
Hackers will infect a device that is connected to your WiFi, and take advantage of your connection to flood other networks with packets. Your actual router is not at risk here. Also, virus detection softwares will not help you with finding every infection. Hackers are able to create undetectable files that will run on your device as soon as you boot it. Check your start up folders daily and delete anything suspicious.
Hey Brian, nice article. Check out my new logs collector, probably would be interesting for you – irclogs.ftp.sh
Here is a Computerworld article on finding the IP address of a router that covers Windows, OS X, iOS, Android and Chrome OS
http://www.computerworld.com/article/2474776/network-security/find-the-ip-address-of-your-home-router.html
Thank you Brian! I’d not heard of WPS. WiFi is turned off in my router, but I don’t know if that means WPS is not remotely accessible. Research. Thanks!
OpenDNS is a great idea too.
If your WiFi is off, then you dont need to worry about WPS.
Brain….I used to be a blackhat hacker. Those ways have gotten me in a lot of trouble. Ive been affiliated with Anonymous, LulzSec, ADT, and LizardKids haha. Ive talked and operated with them before. Your blog has been a part inspiration of mine to do the right thing. I have recently changed to the ethical side of hacking and i will be able to continue on once i build my trust up with my parents and after i figure out what my consequences are in court. I can explain more to you if you wish by email. I would love to talk to you. I would love to get some tips for staying on the ethical path and what others things i should learn. I would also love to tell you what i know. If you guys would like to hit me up my email is isaacowen@outlook.com
Brian you probably didnt need that cuz you probably got everything logged anyway XD
Well thanks guys and mostly thank you Brian.
I would have sent him a private message, rather than post your email in public. If there are bots scanning these wordpress sites, they are going to see your post and email address and potentially start serving you up some spam. =\
I know what you mean isaac, been there done that. parental and self discipline is a virtue. don’t dishonor your families name for the sake of trouble-making. you reap what you sow, and the current landscape of troublemakers will soon find this out.
‘There is an unequal amount of good and bad in most things, The trick is to work out the ratio and act accordingly.’
‘vive la France’
Testing 1234 social engin 101
Plus my last attempt to post here a no-go & I don’t know why 🙂
Not sure if this is a troll or not… Not worth taking seriously either way.
– Uses real name (in full)
– Posts unobfuscated email address
– Associated with LizardSquad
– “Parents”
Pr0 hacker confirmed.
One option is if you have an old router or feel that your existing router doesn’t have that many security functions is to use an open source firm ware like DD-WRT. Essentially flashing your existing router will make it almost brand new again and in most cases faster. The only problem is that when you install the new firm ware you have to make sure that you are doing it correctly and don’t loose power during the process or you will brick your router. Also of your you can use old routers as “repeaters” to extend the range of your router. There are alot of youtube videos on this and I suggest trying it with an old router first. Also if your using WEP you are definitely getting hacked or going to get hacked by a simple program called BackTrack. This is noob stuff…..hope this helps.
I have discovered my NetGear WAP won’t allow the named “admin” account to be renamed?? Is this common in modern routers? Seems to me it would be a security hole to allow in dictionary style attacks even for the less lazy home router user that actually spends the extra 10 seconds to change it.
Yes, most routers do not allow you to change the logon userid, only the password. I have seen a high end Asus router that allowed you to change the userid while cheaper Asus models do not.
Stock firmware for most routers won’t allow you to change the username but flashing third party firmwares such as DD-WRT, OpenWRT, or tomato can give you this functionality and more. DD-WRT in particular has built-in security policies that force you to change the username/password when you first install it and can stop brute-forcing attempts or prevent remote users from logging into your router entirely.
How effective do you think these cleanup efforts will be?
Depends on the shelf life of the products, and the sheer amount of advertisements that are out there.
Simply put, even though it probably wouldn’t happen, put up propaganda posters, something in the theme of the vintage Dragnet series, where the badge flashing, FBI coat wearing detectives say – Hello Ma’am, were here to arrest and confiscate your miscreant router.
The sick side of all that would be, that their immediate thought would probably be, Geesh- now what do I do for internet access? Oh, well, I’ll go buy another and slap in on the network and all will be fine.
People need a super historical event just to move enough to view it on TV. But Geeesh, post something like this on a social media/ profile site, and people will put more effort in proving they are right than it would take to change a username & password.
If these devices once plugged in were to offer a nag popup via a broadcast message saying “security alert – router default router username and password in place”, then it would get changed to about 90% of the issues.
The only real way is for people to hand in their old router for a new or updated router which will not let them connect unless the username/password is changed. Maybe offer a new router at 30-50% off. Who knows. Obviously corporations would go broke, so they will look for the governments to foot the bill to correct.
Congratulations on another honor! You certainly deserve it, and I hope it will encourage some media people/organizations to check their facts, emphasize being correct instead of being first, and revert to reporting the news instead of providing a platform for would-be newsmakers.
Regards,
Well deserved. Keep up the good work.
I have a wifi base station connected (through a wire connection) to a DSL modem provided by my phone company. Which one of these is the router — the wifi base station or the DSL modem?
The manufacturer of the base station is listed in the site that Brian cites, with a model name that’s similar to mine, but not an exact match. (I think the list on that site may be a bit dated.) And the manufacturer of the DSL modem is not listed in that site.
But when I use the utility software provided by the base station manufacturer, it says that the base station is my “network” and the DSL modem is the “router”.
When I set up the system I changed the name and password of the wifi base station. But I have no idea what the name and password for the DSL modem are, or how to change them.
Any thoughts? Thanks!
Find a knowledgeable techie. It doesn’t sound like you need to be mucking about in your network settings.
I’d strongly caution most internet users from using OpenDNS or similar services. While they may function as a lightly effectively security measure they often come with a significant performance hit when accessing CDN served content like most streaming video services due to their relative distance (as opposed to those maintained by ISPs).
A more elegant (but complicated) solution is to sinkhole malicious or compromised addresses on a machine by machine basis using a hosts file, or throughout the network if the router allows it.
MAC locking is worthless and not even worth the time it takes to configure
I’d like to see a white hat produce a ‘crude’ malware that searches for vulnerable routers and then changes the default password to a random one. the same folks who leave the default password will probably never notice. most routers have a physical reset anyway, so they wouldn’t be permanently locked out. shut down the lizards
Wonderful paintings! This is the kind of information that are meant to be shared across the web. Shame on search engines|Google} for not positioning this put up upper! Come on over and consult with my site . Thanks =)
I would say it is extremely funny that now they feel safe because there using cloudflare business.
First of all I would like to say fantastic blog!
I had a quick question which I’d like to ask if you don’t
mind. I was interested to find out how you center yourself and clear
your thoughts prior to writing. I’ve had trouble clearing
my thoughts in getting my ideas out. I truly do enjoy writing however it just seems like the
first 10 to 15 minutes are lost just trying to figure out how to
begin. Any recommendations or hints? Thank you!
site (Sherman)