Skimming attacks on ATMs increased at an alarming rate last year for both American and European banks and their customers, according to recent stats collected by fraud trackers. The trend appears to be continuing into 2016, with outbreaks of skimming activity visiting a much broader swath of the United States than in years past.
In a series of recent alerts, the FICO Card Alert Service warned of large and sudden spikes in ATM skimming attacks. On April 8, FICO noted that its fraud-tracking service recorded a 546 percent increase in ATM skimming attacks from 2014 to 2015.
“The number of ATM compromises in 2015 was the highest ever recorded by the FICO Card Alert Service, which monitors hundreds of thousands of ATMs in the US,” the company said. “Criminal activity was highest at non-bank ATMs, such as those in convenience stores, where 10 times as many machines were compromised as in 2014.”
While 2014 saw skimming attacks targeting mainly banks in big cities on the east and west coasts of the United States, last year’s skimming attacks were far more spread out across the country, the FICO report noted.
Earlier this year, I published a post about skimming attacks targeting non-bank ATMs using hidden cameras and skimming devices plugged into the ATM network cables to intercept customer card data. The skimmer pictured in that story was at a 7-Eleven convenience store.
Since that story ran I’ve heard from multiple banking industry sources who said they have seen a spike in ATM fraud targeting cash machines in 7-Elevens and other convenience stores, and that the commonality among the machines is that they are all operated by ATM giant Cardtronics (machines in 7-Eleven locations made up for 17.5 percent of Cardtronics’ revenue last year, according to this report at ATM Marketplace).
Some financial institutions are taking dramatic steps to head off skimming activity. Trailhead Credit Union in Portland, Ore., for example, has posted a notice to customers atop its Web site, stating:
“ALERT: Until further notice, we have turned off ATM capabilities at all 7-11 ATMs due to recent fraudulent activity. Please use our ATM locator for other locations. We are sorry for the inconvenience.”
7-Eleven did not respond to requests for comment. Cardtronics said it wasn’t aware of any banks blocking withdrawals across the board at 7-11 stores or at Cardtronics machines.
“While Cardtronics is aware that a single financial institution [Xceed Financial Credit Union] temporarily restricted ATM access late in 2015, it soon thereafter restored full ATM access to its account holders,” the company said in a statement. “As the largest ATM services provider, Cardtronics has a long history of executing a layered security strategy and implementing innovative security enhancements at our ATMs. As criminals modify their attack, Cardtronics always has and always will aggressively respond, reactively and proactively, with innovation to address these instances.”
DRAMA IN DC
A bit closer to home for this author, on April 22 FICO pushed an alert to its customers and partners warning about “a recent and dramatic increase in skimming fraud perpetrated at a chain of discount supercenters point-of-sale (POS) terminals,” in an around the Washington, D.C. area, including Frederick, Ellicott City and Mt. Airy in Maryland, and in Fredricksburg, Va.
“As this fraud activity has appeared and progressed suddenly, it is likely that sites in other cities and other geographic areas will be targeted by organized criminal groups,” the organization cautioned.
EUROPE
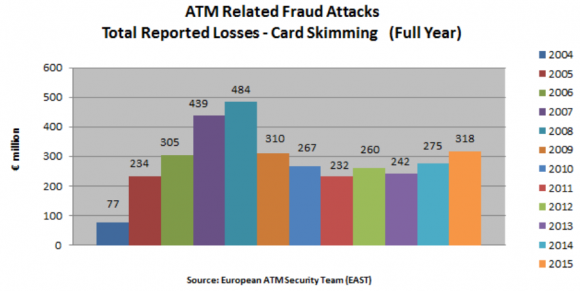
Banks in Europe also enjoyed an increase in skimming attacks of all kinds last year. According to statistics shared by the European ATM Security Team (EAST), during 2015 there were 18,738 skimming attacks reported against European ATMs. That’s a 19% increase from the previous year and equates to 51 attacks per 1000 ATMs over the period.
“During 2015 total losses of 327.48 million euros were reported,” EAST wrote. “This is a 17% increase when compared to the total losses of 279.86 million euros reported for 2014 and equates to losses of 884,069 euros per 1000 ATMs over the period.”
EAST’s report further breaks down the skimming activity by specialization. For example, there were at least 2,657 cases in which a thief tried to blow up or otherwise physically force his way into the cash machine. “This total also includes data from solid explosive and explosive gas attacks. This is a 34% increase from 2014 and equates to 7.2 attacks per 1000 ATMs over the period.”
EAST also tracked 15 malware incidents reported against European ATMs in 2015. All of them were ‘cash out’ or ‘jackpotting’ attacks. According to EAST, this is a 71% decrease from 2014.
PROTECT YOURSELF
As I’ve noted in countless skimmer stories here, the simplest way to protect yourself from ATM skimming is to cover your hand when entering your PIN. That’s because most skimmers rely on hidden cameras to steal the victim’s PIN.
Interestingly, a stat in Verizon‘s new Data Breach Investigations Report released this week bears this out: According to Verizon, in over 90 percent of the breaches in the report last year involving skimmers used a tiny hidden camera to steal the PIN.
The Verizon report also offers this advice about ATM safety: Trust your gut. “If you think that something looks odd or out of place, don’t use it. While it is increasingly difficult to find signs of tampering, it is not impossible. If you think a device may have been tampered with, move on to another location, after reporting to the merchant or bank staff.”
For more on ATM skimmers and other skimming devices, check out my series All About Skimmers.






On the 7/11 ATM–you mean their data traffic isn’t encrypted???
My husband got hit at a gas station pump. We live in a small town north of Seattle and I was really surprised to find skimmer’s had made it to our small town. I am not surprised now after reading this article.
If you ever stop by a gas station and see the red inspection tape around the pumps this is a clear sign that station has had trouble in the past and you may want to use your card inside or not at all.
http://krebsonsecurity.com/2015/02/fuel-station-skimmers-primed-at-the-pump/
P.S. The “security” tape is a joke, you can pull it off and put it back with ease.
Not sure where the idea that if a pump has red tape it means they have had a recent issue. Some states (TX being one) require these stickers as a matter of consumer protection, generally regarding the certification of the weights and measures for the pump. Many national c-store brands also use these on all pumps, regardless of local regulations.
I would agree that they are mostly worthless anti-tampering devices, but just because they have them has no relation to having had a recent issue, in most cases.
This all comes down to convenience really….My job is to keep credit card data safe, yet when I recently saw an atm almost identical to the picture here, exposed phone line and all, I paused for a second and then laughed as I inserted my card. There wasnt another ATM for at least a 10 minute drive, and I needed cash to get into my son’s basketball tournament. I knew better (luckily nothing bad has happened as a result, at least to this point) and I still did it, because I wasnt driving 20 minutes round trip to another ATM.
Using my banks ATM today, I thought of an evilly genius skimming idea – my bank has a plastic shield over the keypad to protect you when entering your PIN. Add you skimmer to an ATM, and then add one of these shields with a camera on the underside and I bet you would have near 100% capture of PIN numbers! As soon as someone feels safe, they will let down their guard, almost every time!
A large number of the gas stations I go to here in the DFW area do NOT have that security tape on them. Not sure that its actually a state requirement. If so there are dozens of service stations out of compliance.
How does capturing data off the network help the bad guys? I’d assume network traffic is encrypted, no?
Nope. No encryption. Read Kreb’s previous article about that hack. Because its a dedicated connection to the financial institution’s data center they didn’t believe that encryption was necessary. Only the pin was encrypted, everything else in plain text. So with a camera and the intercept device you’ve got some credit cards to spend money on.
My local Tesco (I live in the UK, for clarity) has a bank of three ATMs built into the wall next to the entrance. Access to the internals is via a secure door behind the customer services desk, and well monitored.
The frontage is under a camera. I’ve seen at least one incident of a skimmer being attached to the card insertion point of one of these three, and the damage (facia pushed back into the machine) was still there 6 months later. Store security staff and store management both didn’t understand what I was talking about when reporting it, and it took a call to the operating bank (a tesco subsidiary) to resolve it.
I’m assuming this isn’t isolated, and this is the UK’s biggest convenience store chain. Lucky we’re all on Chip-and-pin over here, I guess.
PIN data transmitted from the PED (PIN Pad) is encrypted at the device. Card Data is not encrypted until it hits the router sending it to the ATM network/VPN. Any distance between the ATM and the router is at risk of being exploited. For card data. The PIN is still necessary via video-capture.
Most reliable banks & ATM operators will incorporate the router into (inside) the ATM body and any data sent/connected to a network port (Cat5 to Switch56 or T1 connection) would be encrypted.
Cellular-connected ATMs are generally the best for protecting data. When the router is incorporated into the ATM, that is. Many (but not all by any means) C-Store ATMs using a POTS line (dialup or ISDN) may not be protected until it hits the ATM operator’s network.
GOOD RULE OF THUMB: Look for a branded-ATM (Wells Fargo, PNC, Chase, BB&T, Regions, etc.) versus a “generic” ATM. These branded ATMs are not actually operated by the bank – they are very often a Cardtronic ATM (or ATM USA, Carolina ATM, etc.) operated ATM. However, bank branded (have a top-hate or signage as-if they belonged to a bank) ATMs have to meet rigorous standards versus the private-label ATMs.
Those 7-11 ATM machines are Citi branded.
Prevent skimming by “turning off” suspected ATMs? On its face it seems like a good idea, until it is given a little thought. The only aspect the issuer controls is the authorization. At that point, the card has been swiped or dipped, and skimmed if the ATM is breached, then you’re left with a pissed off customer that doesn’t have their cash.
Probably not getting happier when that skimmed card is then cloned and they see Russian ATM use.
When will we get 2FA for debit cards? ATMs are hooked up, how tough would it be to insert card, input PIN, and then have an additional random generated 4-6 digit number texted from my bank to my cellphone. Believe me this is not foolproof, but would likely reduce fraud. Many bank websites have something like in place now for online banking, how do we extend that to ATM trans
Aren’t debit cards technically already 2FA? I mean – you need the card (possession – 1 factor) and the PIN (knowledge – 2nd factor).
The issue is that the possession factor can be easily duped – need to get rid of mag cards.
Read up on 2FA or multi-factor authentication. Simply having a card is not any form of authentication, that is simply authorization.
The card is essentially something you know – that is, data on the magstrip.
There really is no such thing as multifactor, if you breach the device. Something you are (fingerprint, retinal scan) is distilled to something known that can be captured.
Only something you have which is time-based is worth much, and only if the something you have is kept isolated from something which might capture the seed stored within it (a physically isolated fob).
Revolut look like they’re starting to head in that direction – you can get a physical card (Chip&Pin) linked to an app-based account. Using the app you can disable (or selectively reenable) magstripe transactions, and make the card unuseable if in a different location than the phone (GPS located), and even put an immediate temporary block on the account.
It’s an interesting area
In the Europe section of the article the total for skimming attacks also includes over 2600 instances where the ATM was damaged or destroyed by an explosion. I would have expected to see those attacks in some other category – blowing up an ATM to get at the (often very large amounts of) cash inside is not the same as using snooping techniques to copy and then clone card details. Do you have any figures for the United States for this more direct approach to getting money out of the cash machine?
It’s not really widespread enough until you find a skimmer installed on top of other skimmer 🙂
Brian, I wouldn´t exactly class gas attacks, where the ATM and sometimes the surrounding building is blown to pieces to get at the safe inside, as skimming attacks?
Sad truth is we have seen quite an uptick, which varying collateral damage, of those in Germany.
I don´t quite get the rationale behing the on bank blocking theier cards at 7-11 ATMs? When the auth reaches the bank to decline, the damage is already done? Data is compromised, all the crooks are missing is the 00 auth to confirm PIN was correct and funds available?
Of the 5 people who shielded the keypad while entering their PIN in the video, I could still observe the PIN just by concentrating on relative finger movement in 4 of them.
Only the first person is able to hide the PIN from the camera, because he/she makes it very hard to see which number is pressed first, and also which fingers are used to enter the PIN.
Advising people to conceal the keypad while entering a PIN is like telling teenagers to only practice safe sex. You need to educate the user of the CORRECT way of hiding the PIN. Just advising the user to “hide the PIN” isn’t going to do much.
Fake extra keystrokes without actually depressing the buttons. I do this each time, and rest my fingers on 2-3 extra digits before I withdraw my hand so even if someone had an infrared camera to detect heat they’d be fooled.
Is anyone awakened to the fact, about Nickie’s son having worked for a major money distribution firm servicing atm’s yet. Notice any kind of connection yet?
So the tampering isn’t noticeable. Security tapes are in place, what does that suggest. After the machine is installed, who gets to get into the machine?
Another two factor, by phone? I thought that was busted years ago, the data when stolen, goes to a crib company, surely they verify the data, which includes a minor credit check, which pulls your mobile phone number, anyone ever heard of cloned cards? That’s so 90’sish. If I was the typical buyer of the info, I’d be looking for the better service company for my hard earned cash.
Oh, and hitting Europe also. Well so much for the new style card.
“Oh, and hitting Europe also. Well so much for the new style card.”
Correct. EMV cards are technically more secure, but criminals just adapt and will now target human weaknesses. One tactic they now use in Europe is to queue next to you at a grocery store, watch you enter your PIN (distracting you when you see you cover the keypad), watch where you put your wallet, and then steal your wallet. Your checking account is already emptied by the time you realize your wallet is gone. Oh, and since your wallet is gone, so are your creditcards, your ID and any cash money you had. If you used the same PIN for your creditcards, then gone is the money on those as well. If you used the same PIN for your European ID, then your digital government identity will be sold on the black market too.
I never understood why people advocate for EMV. With magstripe, there was no need to desperately steal your wallet and the victim, while having to deal with an inconvenience, at least still had his cards/cash/ID’s. The EMV scheme makes victims more helpless, and was – of course – only designed to benefit the banks. Because suddenly, it’s no longer the consumer who can blame the bank/institution for not securing an ATM. It’s the bank who blames the consumer for not securing his wallet and protecting his PIN. In the EU, legislation already punishes the consumer for this by not requiring banks to refund the first $150 of stolen money. You will still be able to get the rest of your money back, but your position will be vulnerable in court or when communicating with the bank (who always assumes that you’re trying to pull some trick on them, because who else would have your “secure” chip AND know your PIN?).
Crazy ideas – keep two IDs; don’t put your walled in the back pocket and have a spare card or two elsewhere.
I have had to do IT work at American Native casinos a number of times which make you check in by turning in your ID to get a security badge. I did two things (as I don’t trust them): I had left my ID in the car and told them I’d be right back. Then, I used my expired ID (non-drivers license) I keep tucked away in my car and second I destroyed the magstrip on the back so they couldn’t mass-dump the info.
I can’t imagine that you are referring to 2FA that sends a PIN to one’s mobile phone. If the crook doesn’t have your phone, they don’t get the PIN regardless of knowing your mobile number. (Or am I ignorant on this topic?). So what’s the attack vector?
I am very much looking forward to the day that I can use Pay or NFC and TouchID as the authentication method for ATM access.
Such an approach would seem to eliminate the costs of issuing/replacing ATM cards as well as risks of carrying one around in ones wallet and replace cards with a robustly safe alternative.
Don’t post when your misinformed. The security stickers you see on gas dispensers are there as part of a stations PA-DSS. If pulled from dispenser it will leave part of the sticker showing “tamper”. If not then sticker was not properly installed. Each has a unique number that is recorded and checked several times daily. I know this because I am a Petroleum Technician with over 25 yrs experience. This is just one of the many preventive measures that have been implemented to keep criminals at bay. This is not a sign that a site has had issues in the past ..actually it is a great sign that the business takes your security to heart to avoid skimming issues. So please do your homework before posting false information. Thx, The Lemon
My practice had been to go to a local Credit Union, which had a sharing arrangement with a number of other CUs (including my own CU) so I could use the ATMs there. But a month or two ago, they took those machines out of service for everyone – and directed people to the ATMs outdoors instead (they had even gone so far as to place a ficus in front of each machine to make it even more obvious that the machines were now out of service). Using the outdoor machine to me defeats the purpose. I still don’t know why it is that this CU disconnected the machines.
There is another CU nearby which I believe has a sharing arrangement. I need to find it, find the hours, and verify that it really works.
There is an office for my own CU a bit further off. I always have the option of going there and going inside.
I do have the option of using the 7-11 machines, of course, but generally I don’t want anything to do with them unless I can’t avoid it.
This won’t be possible for everyone, but a some options: leave minimum balances in debit accounts; turn off overdraft protection; set up withdraw alerts, if you bank offers it.
My grocery store has a rubber shield around the POS pinpad. It hides my fingers while I enter the PIN. Why don’t most ATM’s have this? Are they ineffective?
They are mostly effective. However, an infrared camera can still detect which buttons you pressed, and approximately what order.
You can thwart this by purposely lightly pressing your fingers over extra digits not part of your pin before you withdraw your hand (without actually dressing the other digits).
I stopped at a 7-11 last month to get cash from a BofA ATM, and the screens were completely unlike the screens presented at the bank’s drive-up atm, even though it looked exactly the same on the outside. I left before entering my pin.
I stopped at 7-11 in Bowie, across from Chick-file near walmart supercenter.
I stopped at 7-11 near walmart supercenter in Bowie MD
Card issuers need to start declining transactions from EMV cards where they fallabck to magstripe at an EMV capable ATM.
This is blatant non compliance from ATM providers who can’t employ basic financial standards that have been around for years.
The saddest part about this scenario, inline network or modem tap would only work if the connection between the ATM and the remote party is not encrypted with strong encryption. Are there not standards in the US that dictate high levels of security used between the ATMs and banks? If not, why????? This is the same frustration I have about so many of the PoS systems out there today. It seems everywhere I go stores are still lacking behind on chip-reader PoS and no one other than me seems to be ticked off about it. And I am sorry, gas pumps are PoS. Why in the world should PoS devices outside of a store, where it is harder to monitor the installation of skimmers, be exempted.
Just to note, I find it hard to hide the keypad with my hand, but then I started using my wallet to hide the keypad, which was much easier for me. My wallet is available as this tool once I take out my ATM card so might as well use it.
I like to use my .45 to hide the pad, plus it keeps the guy behind in line for the duration of my transaction.