Last week, LifeLock and several other identity theft protection firms erroneously alerted their customers to a breach at cloud storage giant Dropbox.com — an incident that reportedly exposed some 73 million usernames and passwords. The only problem with that notification was that Dropbox didn’t have a breach; the data appears instead to have come from another breach revealed this week at social network Tumblr.
Today’s post examines some of the missteps that preceded this embarrassing and potentially brand-damaging “oops.” We’ll also explore the limits of automated threat intelligence gathering in an era of megabreaches like the ones revealed over the past week that exposed more than a half billion usernames and passwords stolen from Tumblr, MySpace and LinkedIn.
The credentials leaked in connection with breaches at those social networking sites were stolen years ago, but the full extent of the intrusions only became clear recently — when several huge archives of email addresses and hashed passwords from each service were posted to the dark web and to file-sharing sites.
Last week, a reader referred me to a post by a guy named Andrew on the dropbox.com help forum. Andrew said he’d just received alerts blasted out by two different credit monitoring firms that his dropbox credentials had been compromised and were found online (see screenshot below).
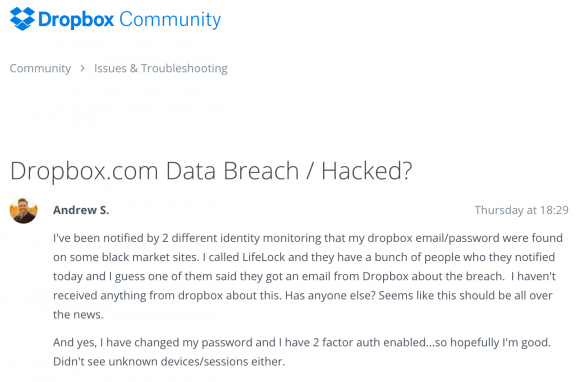
A user on the dropbox forum complains of receiving alerts from separate companies warning of a huge password breach at dropbox.com.
Here’s what LifeLock sent out on May 23, 2016 to many customers who pay for the company’s credential recovery services:
Alert Date: 05-23-2016
Alert Type: Monitoring
Alert Category: Internet-Black Market Website
**Member has received a File Sharing Network alert Email: *****
Password: ****************************************
Where your data was found: social media
Type of Compromise: breach
Breached Sector: business
Breached Site: www.dropbox.com
Breached Record Count: 73361477
Password Status: hashed
Severity: red|email,password
Site: www.dropbox.com
LifeLock said it got the alert data via an information sharing agreement with a third party threat intelligence service, but it declined to name the service that sent the false positive alert.
“We can confirm that we recently notified a small segment of LifeLock members that a version of their dropbox.com credentials were detected on the internet,” LifeLock said in a written statement provided to KrebsOnSecurity. “When we are notified about this type of information from a partner, it is usually a “list” that is being given away, traded or sold on the dark web. The safety and security of our members’ data is our highest priority. We are continuing to monitor for any activity within our source network. At this time, we recommend that these LifeLock members change their Dropbox password(s) as a precautionary measure.”
Dropbox says it didn’t have a breach, and if it had the company would be seeing huge amounts of account checking activity and other oddities going on right now. And that’s just not happening, they say.
“We have learned that LifeLock and MyIdCare.com are reporting that Dropbox account details of some of their customers are potentially compromised,” said Patrick Heim, head of trust and security at Dropbox. “An initial investigation into these reports has found no evidence of Dropbox accounts being impacted. We’re continuing to look into this issue and will update our users if we find evidence that Dropbox accounts have been impacted.”
FALSE POSITIVES?
After some digging, I learned that the bogus attribution of the Tumblr breach to Dropbox came from CSID, an identity monitoring firm that is in the midst of being acquired by credit bureau giant Experian.
Fascinated by anything related to security and false positives, I phoned Bryan Hjelm, vice president of product and marketing for CSID. Hjelm took issue with my classifying this as a threat intel false positive, since from CSID’s perspective the affected individual customers were in fact alerted that their credentials were compromised (just not their Dropbox credentials).
“Our mandate is to alert our client subscribers when we find their information on the darkweb,” Hjelm said. “Regardless of the source, this is compromised data that belongs to them.”
Hjelm acknowledged that CSID was “experiencing some reputational concerns” from Dropbox and others as a result of its breach mis-attribution, but he said the incident was the first time this kind of snafu has occurred for CSID.
I wanted to know exactly how this could have happened, so I asked Hjelm to describe what transpired in more detail. He told me that CSID relies on a number of sources online who have been accurate, early indicators of breaches past. One such actor — a sort of cyber gadfly best known by his hacker alias “w0rm” — had proven correct in previous posts on Twitter about new data breaches, Hjelm said.
In this case, w0rm posted to Twitter a link to download a file containing what he claimed were 100M records stolen from Dropbox. Perhaps one early sign that something didn’t quite add up is that the download he linked to as the Dropbox user file actually only included 73 million usernames and passwords.
In any case, CSID analysts couldn’t determine one way or the other whether it actually was Dropbox’s data. Nonetheless, they sent it out as such anyway, based on little more than w0rm’s say-so.
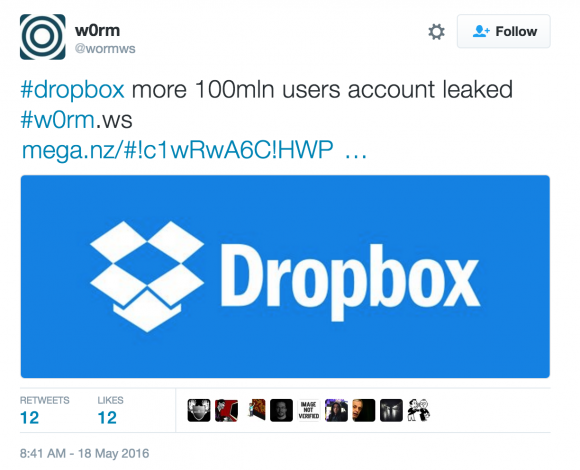
w0rm’s advertisement of the claimed dropbox credentials.
Hjelm said his analysts never test the validity of stolen credentials they’re harvesting from the dark web (i.e. they don’t try to log in using those credentials to see if they’re valid). But he said CSID may take steps such as attempting to crack some of the hashed passwords to see whether a preponderance of them point to a certain online merchant or social network.
In the LinkedIn breach involving more than 100 million stolen usernames and passwords, for example, investigators were able to connect a corpus of hashed passwords posted on a password cracking form to LinkedIn because a large number of users in the hashed password list had a password with some form of “linkedin” in it.
I asked CSID whether its researchers took the basic step of attempting to register accounts at the suspected breached service using the email addresses included in the supposed user data dump. As I discussed in the post How to Tell Data Leaks from Publicity Stunts, most online services do not allow two different user accounts to have the same email address, so attempting to sign up for an account using an email address in the claimed leak data is an effective way to test leak claims. If a large number of email addresses in the claimed leak list do not already have accounts associated with them at the allegedly breached Web site, the claim is almost certainly bogus.
Hjelm said CSID doesn’t currently use this rather manual technique, but that the company is open to suggestions about how to improve the accuracy of their breach victim attribution. He said CSID only started providing attribution information about a year ago because clients were demanding it.
Allison Nixon, a cybercrime researcher and director of security research at dark web monitoring firm Flashpoint, was the genesis of that aforementioned story about data leaks vs. publicity stunts. She’s done more research than anyone I know to date on ways to quickly tell whether a claimed breach is real, and how to source it. Nixon said automating threat intel only goes so far.
“In general, the skill of human skepticism performed today by threat intelligence experts is extremely difficult to automate,” Nixon said. “Even with advancements in cognitive and artificial intelligence technologies, humans will still and always be needed to validate the nuances associated with accurate intelligence. Security experts must be intimately involved in the fact checking process of threat intelligence, or otherwise, will run the risk of losing valuable time, resources and possibly even more, by validating false information perceived as accurate by automated technologies.”
Flashpoint found closer examination of the file that w0rm leaked maps back to a 2013 recycled breach at Tumblr.
There is no question w0rm has a history of sharing real dumps. But according to Flashpoint that reputation must be taken with a grain of salt because even though the dumps are real, they are usually publicly available yet are portrayed by w0rm as evidence of his hacking proficiency.
In short: The intended victim of guys like w0rm is probably other cybercriminals, but threat intel companies can get caught up in this as well.
Many readers have asked me to weigh in on reports of a possible breach at Teamviewer, a service that lets users share their desktops, audio chat and other applications with friends and contacts online. Teamviewer has so far denied experiencing a breach.
My guess is that a large number of Teamviewer users either re-used passwords at some of the social networking services whose usernames and hashed passwords were posted online this week, or they are Teamviewer users who unfortunately were caught up in the day-to-day churn of systems compromised through other malware. In any case, there is a lengthy thread on Reddit populated by Teamviewer users who mostly claim they didn’t re-use their Teamviewer password anywhere else.
It’s interesting to note that early versions of remote access Trojans like Zeus contained a Teamviewer-like component called “backconnect” that let the attackers use the systems much like Teamviewer enables its users. These days, however, cybercriminals often forgo that homegrown backconnect feature and rely instead on either equipping the victim with a Teamviewer account and/or hijacking the victim’s existing Teamviewer account credentials, and then exfiltrating stolen credentials and other data through a Teamviewer installation. Hence, a compromise of one’s Teamviewer account may indicate that the victim’s system already is compromised by sophisticated Windows-based malware.
For its part, Dropbox is using this opportunity to encourage users to beef up the security of their accounts. According to Dropbox’s Patrick Heim, less than one percent of the Dropbox user base is taking advantage of the company’s two-factor authentication feature, which makes it much harder for thieves and other ne’er-do-wells to use stolen passwords.
“In matters of security, we always suggest users take an abundance of caution and reset their passwords if they receive any notification of a potential compromise,” Heim said. “Dropbox strongly encourages individuals use strong and unique passwords for each service. We also encourage Dropbox users to enable two-factor authentication to further protect their account.”
I hope it goes without saying that re-using passwords across multiple sites that may hold personal information about you is an extremely bad idea. If you’re guilty of this apparently common practice, please change that. If you need some inspiration on this front, check out this post.




Not concerned. I use two-factor auth on Dropbox, have a unique and complex password and have all of my most confidential files stored in a Veracrypt container. Plus, being a paying customer I’m confident that Dropbox would notify me if my account had been compromised in any way.
I think there’s a boo-boo here:
“…more than 100,000 million stolen…”
Too many zeroes? Or does the word ‘million’ not belong there?
It only feels like 100 billion!
It always astounds me about how few people take the now trivial and affordable step of using a password manager to create complex passwords and auto fill the credential set into login pages.
I have an all Apple set up do I am well served by the iCloud Keychain incorporated into all Apple products since about 2013; and it’s free.
There are plenty of paid apps that run across various platforms ranging from password manager companies to anti virus and browser vendors.
The fact that folks don’t invest a bit of time to migrate all their login credentials into such a system never fails to surprise as doing this is fairly trivial and relative cheap both time and money wise.
“100,000 million” would be a common way of expressing that number in the UK. But I don’t think there are that many Dropbox or Tumblr accounts there.
Rest of the Europe maybe but not the UK. And in a few months the UK maybe no more belongs to Europe. So long.
For years, I have considered–in varying degrees of seriousness–subscribing to LifeLock. This matter proves it to be just another insurance hustle: very similar to USCCA . My now-negative decision is hereby irrevocable.
Well, given the Co-founder of Lifelock publicly posted his social security number and was a victim of 13 cases of identity theft in 2007/2008… that says a lot about this company.
Oh, and don’t forget about their TV commercials which looks like they’re selling a cheap & crappy product.
That says enough about this company for me.
Let’s not forget Lifelock’s settlement with the FTC last year. Largest ever (at least as of that date):
https://www.ftc.gov/news-events/press-releases/2015/12/lifelock-pay-100-million-consumers-settle-ftc-charges-it-violated
I would never sign up with a “security” company that gives you a free strip shredder when you sign up, making people think that shredding your data in a strip shredder is secure. It may be more secure than not shredding your documents at all, but it would not be that difficult to put it back together. If they are serious about security, they should be using a cross-cut shredder.
cross cut shredder? how cute, I would only trust a security company who sends me a complementary matchbook
There are plenty of reputable companies out there like IDT911 to protect your identity. You can’t buy from them directly but chances are you may have their coverage through your work benefits, bank or your insurance carrier. Just do a quick inquiry with them.
Your concerns are warranted. Due diligence is your greatest tool in helping protect yourself. One of the most reputable companies in the cyber security industry is Kroll. They administer IDShield for LegalShield members. If you are interested in finding protection from such a company, I’d like to invite you to visit my site for details.
Michael
By all means. Just give me the url.
Kroll reported my email compromised as well, ‘potential site’ – Dropbox. Haveibeenpwnd.com reported my account details leaked through Tumblr, which makes sense.
Correlating multiple sources is how ‘good’ intelligence is derived. Basing a threat report on a single source, especially one of ‘dubious’ allegience, is unprofessional at least.
Nixon said. “Even with advancements in cognitive and artificial intelligence technologies, humans will still and always be needed to validate…”
She should specify: humans with some logic and a brain.
We are facing the same problem with news networks: “Let’s skip the facts check, we gotta be the first to publish it, no matter if we’re right or wrong.”
Thankfully, people like Brian Krebs, Troy Hunt and others can do their job properly.
Interesting info – especially your interaction with CSID, Brian, particularly given the fact CSID happens to be the entity the Fed’s Office of Personnel Management contracted with to provide monitoring services to the some 18 million current/former Federal employees – whose employment info was compromised not that long back by hackers.
I think the lesson for end users is that we must always assume breach; do not share passwords between services, use complex passwords which are resistant to dictionary attacks, and the use of 2FA where you are able.
The problem arises when services don’t have controls which enforce these simple rules. Account breaches can then be expected as end users will violate these rules as we have repeatedly seen in past breaches.
Hopefully Azure’s response to the LinkedIn breach indicates that more services will be moving from ease of use to greater security!
I can only hope that Dropbox sues Lifelock for this major “false positive” as it has to be detrimental to Dropbox’s business.
After seeing the ads for Lifelock, where the president puts his Social Security number on ads, daring hackers to steal his identity, I knew it was going to be far less than the service promised. I have better things to do with my hard earned money than give it to some service that will “protect” my identity. I can do a better job and save the $$$.
I’m not surprised that some said SUE! So, why don’t you go ahead and do so. Sue them for having commercials on TV. Sue them for having so many subscribers. Sue them for using a service (CSID) that provided incorrect information. Sue them for being in the United States. Sue them for even existing. Have at it. I want to watch the show.
CSID is also the company that was awarded the contract to protect GOV employees in the OPM breach of all gov employees
This fits my experience with CSID. The OPM contacted them after their breach and it really feels like a rip-off — they don’t offer any way to filter alerts and they refuse to share any useful information with customers so you get urgent alerts telling you that your email address was found on the “dark web”. No explanation of whether that means more than “on a spam list”, whether anything else was included, etc. If you waste time talking to their support people you’ll get a response a couple days later telling you that they can’t share anything more.
Just sign up with “have i been pwned dot com”… it’s free and gives you a lot better service than that!
Been watching the Teamviewer stuff closely. I don’t believe that everyone who claimed 2FA had it set up, or if they did, they enabled another convenience option that bypassed it. But the TeamViewer issues look to be more than one attack going on at the same time. Teamviewer, as your probably know, connects on one of two sets of credentials: the persistent account, or a machine-unique ID and password. Some of the attack descriptions and logs provided point to machine credentials being compromised rather than account credentials.
For what it’s worth, I had two accounts up and running with entirely unique account credentials/unused anywhere else that weren’t touched, and I’ve got two more virgin accounts running sandboxed for the hell of it right now that haven’t been touched either. Leaves me wondering if the cases in which machine creds were used were a case of those machine creds being foolishly shared in a compromised email.
Thanks, at least this article reminded me Dropbox had 2FA and made me activate it 😉
Not that I would store anything remotely sensitive there, but even stuff like syncing your photos from device to device is nobody ele´s busines.
I think we’ll see many more of these. As end users, we need to proactively use solutions that are easy to implement, use, and can afford. 2FA auth continues to advance with software based tokens, integrated browser tokens, hard tokens. Even tools such as PassSafe, works if one changes their passwords frequently and keep browser cache cleared on exit. I would like to see a new blog about this.
Got this this morning after uninstalling TV on my personal PCs and leaving a concern about account security.
Timely ….
————————-
David Gjertsen Fri, Jun 3, 2016 at 6:44 AM
Reply-To: support@teamviewer.com
To: …………gmail.com
Dear TeamViewer Users,
Protecting your personal data is at the very core of everything we do.
We highly appreciate the trust you place in us and respect the responsibility we have to ensure your privacy. This is why we always feel a strong need to take all necessary steps to safeguard your personal data.
As you have probably heard, there have been unprecedented large scale data thefts on popular social media platforms and other web service providers. Unfortunately, credentials stolen in these external breaches have been used to access TeamViewer accounts, as well as other services.
We are appalled by the behaviour of cyber criminals, and are disgusted by their actions towards TeamViewer users. They have taken advantage of common use of the same account information across multiple services to cause damage.
Therefore, to help you – our users – and to further strengthen the protection of your data against these attacks of cyber criminals, we are globally rolling out improved security measures today in a two-fold approach:
Trusted Devices
With the first measure we give you even more protection, by catching suspicious behavior before it goes any further, and to help prevent anyone else from accessing your account.
The Trusted Devices feature ensures that whenever your TeamViewer account attempts to sign in on any given device for the first time, we will ask for your authorization of the new device before access is granted.
An in-app notification will ask you to approve the device via an email that we will send to your account email address.
That device is then added as a Trusted Device, and you will be able to sign in as usual.
Protecting Your Data Integrity
The second measure is designed to improve your security against individuals, such as cyber criminals, who steal account credentials and cause damage by taking advantage of common use of the same account information across multiple services.
We identify if your TeamViewer account shows evidence of unusual behavior (e.g. access from a new location) that might suggest it has been compromised.
To safeguard your data integrity, your TeamViewer account will be marked for an enforced password reset. You will then receive an email from us with instructions to reset your password.
We strongly recommend
We are determined to continue extending our security measures for you. We do not take your trust lightly, nor do we accept any compromise on data security. Please take the following recommendations to heart:
• Protect any user account you own – whether it is with TeamViewer or any another service – by using unique and secure passwords(link to password day blog article) that are frequently changed.
• Ensure you have reliable anti-malware and security solutions in place at all times.
• Enable two-factor authentication whenever possible, such as with TeamViewer.
For further security information, please visit the FAQ page on TeamViewer account security.
Our support team is happy to answer any of your potential queries at: https://www.teamviewer.com/en/support/contact/submit-a-ticket/
We recommend that if you suspect that you have been the victim of criminal activities to get in touch with your local police department, in order to report your case. This is particularly important because TeamViewer is subject to very strict data protection and privacy regulations, and can release sensitive data only to authorized individuals and authorities.
Kind regards,
David Gjertsen
Team Manager Customer Care
It seems like neither CSID or Life Lock really know their business well enough to validate the information they receive. Perhaps their customers aren’t getting their money’s worth.
Regards,
I suspect one of the reasons why some users are reluctant to use two factor auth is that they have been burned so many times by companies selling their phone number. I get several calls each week by spammers calling from phone numbers no longer in service.
+1
The possibilities for long-term abuse related to two-factor authentication as currently implemented far outweigh any perceived short-term benefit.
Maybe there are other lower-risk ways to implement 2FA, but what’s on offer today is, IMHO, a non-starter.
Using 2-factor authentication and Dropbox (and many other sites) doesn’t require that you give out your phone number. They support TOTP one-time codes, which can be generated by smartphone apps such as Google Authenticator.
And if you prefer open source software, there’s FreeOTP availible at https://fedorahosted.org/freeotp/
Supports TOTP & HOTP,
Also the google PAM module is super easy to set up if you want to keep away attackers from the local network
This sort of bears out my personal observation that if a company is engaged in high-volume (particularly late-night) marketing campaigns on 2nd- or 3rd-tier TV channels, their “service” is far more likely to be an expensive, less-than-worthwhile scheme and quite possibly little more than a near-fraudulent scam that hasn’t yet gotten buy-in from quite enough people who got outraged at being fleeced to have triggered an investigation by some state’s Attorney-General.
“In any case, CSID analysts couldn’t determine one way or the other whether it actually was Dropbox’s data. Nonetheless, they sent it out as such anyway, based on little more than w0rm’s say-so.”
Well they read in on the internet, so it must be true! Idiots.
This is the tumblr data leak it’s pretty obvious when you see the domain davidville.com it says this “Davidville is now Tumblr, Inc.”
And the one most didn’t see experience listed? They had a big breach also. The only thing I haven’t heard, is when were the penetrated? The longer I don’t hear about that, the further back it must have been.
Durn Google on tablet, Experian
Its in these Internet protection businesses best interests that the Internet be sen as the Wild Wild West with breaches occurring all over the place. That may seem to be the case, but to go out with alerts that are inaccurate destroys their credibility. The should preface all such announcements with a indication of just how reliable the information is that they have used. If this continues their value to customers will become diminished.
On the one hand, storing your data in the onlie databases like dropbox is dangerous. On the other, there are things like ransomware that can come and encrypt your data. So, where is the beef?
On one hand, you have absolutely no real control over your data (although a pretense of control if offered). On the other, you have as much control over your data as you wish to have (depending on how much you are willing to learn and implement). All the beef is in the choices you make.
“If you choose not to decide, you still have made a choice”
Frankly, the best choice is to keep your vital data on an off-line storage updating as often as needed
I might be paranoid but I don’t trust anybody promising me anything I can’t see. I don’t have any sensitive info on the net. It’s not on my computer or the cloud – all of it’s on thumb drives. Ok, there are mega-corps that need the net to stay in touch with all the outliers and I sse a need for cloud staorge -what ever. I’m an individual.
I get spear phishing messages that are supposedly from Dropbox all the time. Constant threats that my account will be closed unless I “verify” my credentials. I used the site once a few years ago. The emails keep coming. I send them to spam now.
Chances are that any penetration of Dropbox accounts came from phishing attacks.
adobe got hacked too ,not good